Blue Fox Arm Assembly Internals and Reverse Engineering读书笔记
01-Blue Fox 读书笔记-01-Introduction
02-Blue Fox 读书笔记-02-Part 1_Chapter 1_Introduction to ReverseEngineering
前言
- This book was originally supposed to contain an overview of the Arm instruction set, chapters on reverse engineering, and chapters on exploit miti- gation internals and bypass techniques. The publisher and I soon realized that covering these topics to a satisfactory extent would make this book about 1,000 pages long. For this reason, we decided to split it into two books: Blue Fox and Red Fox.
这本书原先打算包含对Arm指令集的概述,关于逆向工程的章节以及关于漏洞利用缓解机制和绕过技巧的章节。我和出版商很快意识到,如果要把这些主题涵盖到令人满意的程度,这本书将有大约1000页长。因此,我们决定将它分为两本书:《蓝狐》和《红狐》。
- note
Red Fox: Vulnerability Analysis and Exploit Mitigation Internals for Mobile and IoT
Expected publication May 29, 2024
- The Blue Fox edition covers the analyst view; teaching you everything you need to know to get started in reverse engineering. Without a solid under- standing of the fundamentals, you can’t move to more advanced topics such as vulnerability analysis and exploit development. The Red Fox edition will cover the offensive security view: understanding exploit mitigation internals, bypass techniques, and common vulnerability patterns.
1 《蓝狐》版涵盖了分析师的视角;教授你开始逆向工程所需的一切知识。如果没有扎实的基础知识,你无法进入更高级的主题,如漏洞分析和漏洞开发。
2《红狐》版将涵盖攻击性安全的视角:理解漏洞利用的内部机制、绕过技巧和常见的漏洞模式。
- Security researchers who are used to reverse engineering x86/64 binaries but want to adopt to the new era of Arm-powered devices are having a hard time finding digestible resources on the Arm instruction set, especially in the context of reverse engineering or binary analysis. Arm’s architecture reference manual can be both overwhelming and discouraging. In this day and age, nobody has time to read a 12,000-page deeply technical document, let alone identify the most relevant or most commonly used instructions and memorize them. The truth is that you don’t need to know every single Arm instruction to be able to reverse engineer an Arm binary. Many instructions have very specific use cases that you may or may not ever encounter during your analysis.
事实是,你不需要知道每一个Arm指令就能逆向工程一个Arm二进制文件。许多指令有非常特定的使用场景,你在分析过程中可能会或可能不会遇到。
- If you’re a beginner in reverse engineering, it is important to understand the binary’s file format, its sections, how it compiles from source code into machine code, and the environment it depends on. Because of limited space and time, this book cannot cover every file format and operating system. It instead focuses on Linux environments and the ELF file format. The good news is, regardless of platform or file format, Arm instructions are Arm instructions. Even if you reverse engineer an Arm binary compiled for macOS or Windows, the meaning of the instructions themselves remains the same.
如果你是逆向工程的初学者,理解二进制文件的格式、其各个部分、它如何从源代码编译成机器码,以及它所依赖的环境是非常重要的。由于空间和时间的限制,这本书不能涵盖每一个文件格式和操作系统。它主要关注Linux环境和ELF文件格式。好消息是,无论哪个平台或文件格式,Arm指令就是Arm指令。即使你逆向工程一个为macOS或Windows编译的Arm二进制文件,指令本身的含义仍然保持不变。
章节说明
- This book begins with an introduction explaining what instructions are and where they come from. In the second chapter, you will learn about the ELF file format and its sections, along with a basic overview of the compilation process. Since binary analysis would be incomplete without understanding the context they are executed in, the third chapter provides an overview of operating system fundamentals.
这本书从介绍开始,解释了指令是什么以及它们从哪里来。在第二章中,您将学习关于ELF文件格式及其部分的内容,以及编译过程的基本概述。因为没有理解它们执行的上下文,二进制分析是不完整的,所以第三章提供了操作系统基础的概述
- With this background knowledge, you are well prepared to delve into the Arm architecture in Chapter 4. You can find the most common data processing instructions in Chapter 5, followed by an overview of memory access instructions in Chapter 6. These instructions are a significant part of the Arm architecture, which is also referred to as a Load/Store architecture. Chapters 7 and 8 discuss conditional execution and control flow, which are crucial components of reverse engineering.
拥有这些背景知识后,你将为深入探讨第四章的Arm架构做好准备。在第五章中,你可以找到最常见的数据处理指令,其后是第六章关于内存访问指令的概述。这些指令是Arm架构的重要部分,也被称为加载/存储架构。第七章和第八章讨论条件执行和控制流,这是逆向工程的关键组件。
- Chapter 9 is where it starts to get particularly interesting for reverse engineers. Knowing the different types of Arm environments is crucial, especially when you perform dynamic analysis and need to analyze binaries during execution.
第九章对于逆向工程师来说开始变得特别有趣。了解不同类型的Arm环境是至关重要的,尤其是当你执行动态分析并需要在执行过程中分析二进制文件时。
- With the information provided so far, you are already well equipped for your next reverse engineering adventure. To get you started, Chapter 10 includes an overview of the most common static analysis tools, followed by small practical static analysis examples you can follow step-by-step.
根据到目前为止提供的信息,您已经为下一次的逆向工程冒险做好了充分的准备。为了帮助您开始,第十章包括了最常用的静态分析工具的概述,其后是一些您可以逐步遵循的小型实际静态分析示例。
- Reverse engineering would be boring without dynamic analysis to observe how a program behaves during execution. In Chapter 11, you will learn about the most common dynamic analysis tools as well as examples of useful commands you can use during your analysis. This chapter concludes with two practical debugging examples: debugging a memory corruption vulnerability and debugging a process in GDB.
如果没有动态分析来观察程序在执行过程中的行为,逆向工程将会很无趣。在第十一章中,你将学习关于最常用的动态分析工具,以及在分析过程中可以使用的有用命令的示例。这一章以两个实际的调试示例结束:调试一个内存损坏的漏洞和在GDB中调试一个进程。
- Reverse engineering is an invaluable skill for malware analysts, but they also need to be familiar with the environment a given malware sample was compiled for. To get you started in this area, this book includes a chapter on analyzing arm64 macOS malware (Chapter 12) written by Patrick Wardle, who is also the author of The Art of Mac Malware.3 Unlike previous chapters, this chapter does not focus on Arm assembly. Instead, it introduces you to common anti-analysis techniques that macOS malware uses to avoid being analyzed. The purpose of this chapter is to provide an introduction to macOS malware compatible with Apple Silicon (M1/M2) so that anyone interested in hunting and analyzing Arm-based macOS malware can get a head start.
逆向工程对于恶意软件分析师是一项宝贵的技能,但他们还需要熟悉给定的恶意软件样本所编译的环境。为了帮助您在这个领域入门,这本书包括了一个关于分析arm64 macOS恶意软件的章节(第十二章),由Patrick Wardle编写,他也是《Mac恶意软件的艺术》的作者。与前面的章节不同,这一章并不集中于Arm汇编。相反,它向你介绍了macOS恶意软件常用的反分析技巧,用于避免被分析。这一章的目的是为了提供一个与Apple Silicon(M1/M2)兼容的macOS恶意软件的介绍,这样任何对追踪和分析基于Arm的macOS恶意软件感兴趣的人都可以有一个良好的开端。
本书目录

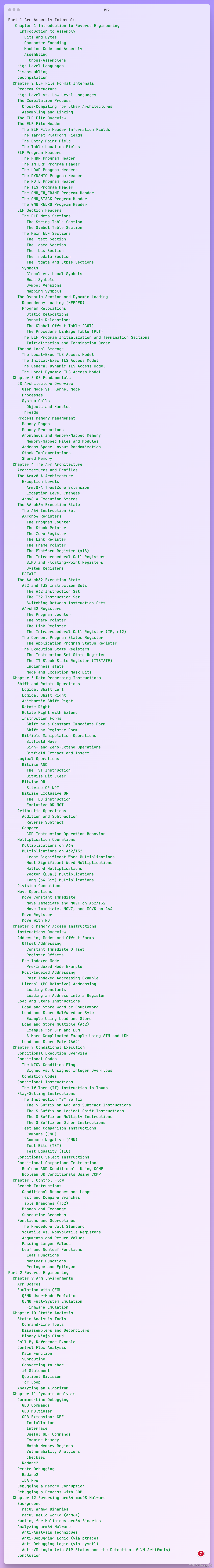
需要书籍电子版请私信我。- 尊重作者的知识产权,请大家购买正版阅读吧!
参考文献
[1]: https://leg-assembly.com/
[2]: https://www.amazon.com/Blue-Fox-Assembly-Internals-Engineering-ebook/dp/B0C2B5SLYM

























 818
818











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








