一、实验环境:CA:192.168.199.141、Apache:192.168.199.143
二、实验步骤
1、CA证书服务器的配置
1.1.安装openssl工具(默认使安装完成的)
[root@CA ~]# yum install -y openssl
1.2.查看配置文件
[root@CA /]# vim /etc/pki/tls/openssl.cnf
相关证书的存放目录
42 dir = /etc/pki/CA
存储签发的数字证书
43 certs = $dir/certs
记录颁发证书得到信息
45 database = $dir/index.txt
记录证书编号
51 serial = $dir/serial
1.3.存放证书存放相关文件位置
[root@CA ~]# cd /etc/pki/CA/
1.4.CA证书服务私钥存放位置
[root@CA CA]# cd private
1.5.CA证书服务器创建自签名证书并设置权限为600
[root@CA private]# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
......................................+++
...............+++
e is 65537 (0x10001)
1.6.CA证书服务器签发本地自签名证书(需要输入一些信息)
[root@CA private]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
---
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:zhuhai
Locality Name (eg, city) [Default City]:zhuhai
Organization Name (eg, company) [Default Company Ltd]:skills
Organizational Unit Name (eg, section) []:skills
Common Name (eg, your name or your server's hostname) []:CA
Email Address []:
1.7.创建CA证书服务申请文件
[root@CA private]# cd ../
创建记录申请证书的文件
[[root@CA CA]# touch index.txt
写入证书编号
[root@CA CA]# echo 01 > serial
[root@CA CA]# cat serial
01
2、Apache服务器的配置
2.1.安装服务
[root@www1 /]# yum install -y httpd mod_ssl
2.2.写入一个页面,暂不启动服务
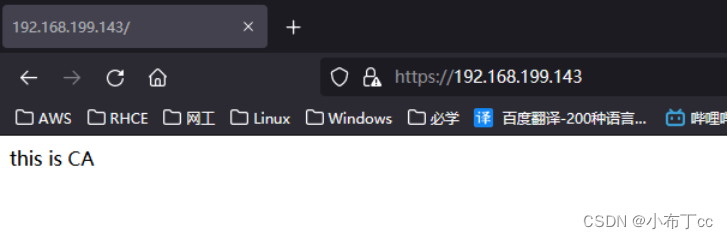
[root@www1 /]# echo "this is CA " >> /var/www/html/index.html
2.3.本地生成私钥
[root@www1 ~]# mkdir ssl
[root@www1 ~]# cd ssl/
[root@www1 ssl]# (umask 077;openssl genrsa -out /root/ssl/httpd.key 2048)
Generating RSA private key, 2048 bit long modulus
.........................................................+++
..........................+++
e is 65537 (0x10001)
2.4.使用私钥生成证书申请文件
[root@www1 ssl]# openssl req -new -key httpd.key -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
---
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:zhuhai
Locality Name (eg, city) [Default City]:zhuhai
Organization Name (eg, company) [Default Company Ltd]:skills
Organizational Unit Name (eg, section) []:skills
Common Name (eg, your name or your server's hostname) []:www1
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
2.5.将生成的证书申请文件发送到CA证书服务器进行授权操作
[root@www1 ssl]# scp httpd.csr root@192.168.199.141:/
3、CA证书服务器配置
3.1.将发送过来的申请文件进行授权
[root@CA /]# openssl ca -in httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Sep 22 02:58:58 2021 GMT
Not After : Sep 22 02:58:58 2022 GMT
Subject:
countryName = cn
stateOrProvinceName = zhuhai
organizationName = skills
organizationalUnitName = skills
commonName = www1
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
57:3E:51:FD:DE:00:B6:0D:6B:09:37:CF:F7:D2:BD:F3:F5:81:54:E1
X509v3 Authority Key Identifier:
keyid:B3:DD:A6:9D:11:39:AE:30:D6:0C:8B:D3:72:D7:5F:24:BE:E1:DD:F0
Certificate is to be certified until Sep 22 02:58:58 2022 GMT (365 days)
Sign the certificate? [y/n]:y #输入y是否要进行签署操作
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
3.2.将生成的证书文件传送会Apache服务器
[root@CA /]# scp /etc/pki/CA/certs/httpd.crt [root@192.168.199.143](mailto:root@192.168.199.143):/root/ssl
4、Apache服务器的配置
4.1.查看文件是已传输到目录中
[root@www1 ssl]# ls
httpd.crt httpd.csr httpd.key
4.2.将申请下来的证书文件目录写入到ssl配置文件中
[root@www1 ssl]# vim /etc/httpd/conf.d/ssl.conf
100 SSLCertificateFile /root/ssl/httpd.crt
107 SSLCertificateKeyFile /root/ssl/httpd.key
4.3.关闭防火墙与selinux和启动http服务(不关闭会出现启动失败的问题)
[root@www1 ssl]# systemctl stop firewalld
[root@www1 ssl]# setenforce 0
[root@www1 ssl]# systemctl start httpd
[root@www1 ssl]# ss -tan |grep 80
LISTEN 0 128 :::80 :::*
[root@www1 ssl]# ss -tan |grep 443
LISTEN 0 128 :::443 :::*
4.4.使用浏览器访问测试






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








