鼠标流量
基础知识
USB协议鼠标数据部分在Leftover Capture Data域中,数据长度为四个字节
第一个字节,代表按键
当取0×00时,代表没有按键
当取0×01时,代表按左键
当取0×02时,代表当前按键为右键
第二个字节,可看作为signed byte类型,其最高位为符号位,
当值为正时,代表鼠标右移像素位;
值为负时,代表鼠标左移像素位。
第三个字节,代表垂直上下移动的偏移。
当值为正时,代表鼠标上移像素位;
值为负时,代表鼠标下移像素位。
实战练习
flag隐藏在usb流量中,通过USB协议数据中的鼠标移动轨迹转换成flag
题目
方法1:
基于python2的UsbMiceHacker.py脚本
#!/usr/bin/env python
# coding:utf-8
import sys
import os
import numpy as np
import matplotlib.pyplot as plt
mousePositionX = 0
mousePositionY = 0
X = []
Y = []
DataFileName = "usb.dat"
data = []
def main():
global mousePositionX
global mousePositionY
# check argv
if len(sys.argv) != 3:
print "Usage : "
print " python UsbMiceHacker.py data.pcap [LEFT|RIGHT|MOVE|ALL]"
print "Tips : "
print " To use this python script , you must install the numpy,matplotlib first."
print " You can use `sudo pip install matplotlib numpy` to install it"
print "Author : "
print " WangYihang <wangyihanger@gmail.com>"
print " If you have any questions , please contact me by email."
print " Thank you for using."
exit(1)
# get argv
pcapFilePath = sys.argv[1]
action = sys.argv[2]
if action != "LEFT" and action != "ALL" and action != "RIGHT" and action != "MOVE":
action = "LEFT"
# get data of pcap
command = "tshark -r '%s' -T fields -e usb.capdata > %s" % (
pcapFilePath, DataFileName)
print command
os.system(command)
# read data
with open(DataFileName, "r") as f:
for line in f:
data.append(line[0:-1])
# handle move
for i in data:
Bytes = i.split(":")
if len(Bytes) == 8:
horizontal = 2 # -
vertical = 4 # |
elif len(Bytes) == 4:
horizontal = 1 # -
vertical = 2 # |
else:
continue
offsetX = int(Bytes[horizontal], 16)
offsetY = int(Bytes[vertical], 16)
if offsetX > 127:
offsetX -= 256
if offsetY > 127:
offsetY -= 256
mousePositionX += offsetX
mousePositionY += offsetY
if Bytes[0] == "01":
# print "[+] Left butten."
if action == "LEFT":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
elif Bytes[0] == "02":
# print "[+] Right Butten."
if action == "RIGHT":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
elif Bytes[0] == "00":
# print "[+] Move."
if action == "MOVE":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
else:
# print "[-] Known operate."
pass
if action == "ALL":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
fig = plt.figure()
ax1 = fig.add_subplot(111)
ax1.set_title('[%s]-[%s] Author : WangYihang' % (pcapFilePath, action))
ax1.scatter(X, Y, c='r', marker='o')
plt.show()
# clean temp data
os.system("rm ./%s" % (DataFileName))
if __name__ == "__main__":
main()
还有基于python3的UsbMiceDataHacker.py脚本
python3 UsbMiceDataHacker.py usb2.pcap RIGHT
#RIGHT代表右键
我这里什么也没有

贴上其他人成功的结果

方法2:
提取鼠标流量数据
tshark -r usb2.pcap -T fields -e usb.capdata > usbdata.txt
查看usbdata.txt

剔除空行,亲身经历,这步很重要,包含空行会得到错误结果
tshark -r usb2.pcap -T fields -e usb.capdata | sed '/^\s*$/d' > usbdata.txt
没有冒号,使用脚本添加冒号
f=open('usbdata.txt','r')
fi=open('out.txt','w')
while 1:
a=f.readline().strip()
if a:
if len(a)==8: # 键盘流量len=16,鼠标流量len=8
out=''
for i in range(0,len(a),2):
if i+2 != len(a):
out+=a[i]+a[i+1]+":"
else:
out+=a[i]+a[i+1]
fi.write(out)
fi.write('\n')
else:
break
fi.close()
运行脚本,得到out.txt

使用mouse.py脚本,通过更改btn_flag的值来测试鼠标左右键
nums = []
keys = open('out.txt','r')
f = open('xy.txt','w')
posx = 0
posy = 0
for line in keys:
if len(line) != 12 :
continue
x = int(line[3:5],16)
y = int(line[6:8],16)
if x > 127 :
x -= 256
if y > 127 :
y -= 256
posx += x
posy += y
btn_flag = int(line[0:2],16) # 1 for left , 2 for right , 0 for nothing
if btn_flag == 2 : # 1 代表左键
f.write(str(posx))
f.write(' ')
f.write(str(posy))
f.write('\n')
f.close()
经过测试是鼠标右键流量,在生成的xy.txt中可以得到坐标:

看了大师傅的wp,发现我们添加冒号得到的内容不一样

大师傅直接提取鼠标流量,含有冒号,而我提取出来的不含冒号,是Wireshark版本不同的缘故,在网上找到老版本的Wireshark
Wireshark-win64-2.4.3
https://pan.baidu.com/s/1nvIIKpr
密码:5uao
提取流量得到usbdata.txt,包含冒号:
直接使用上面的mouse.py脚本,即可得到xy.txt。

进入gnuplot工具,把xy.txt文本里的坐标转化为图片
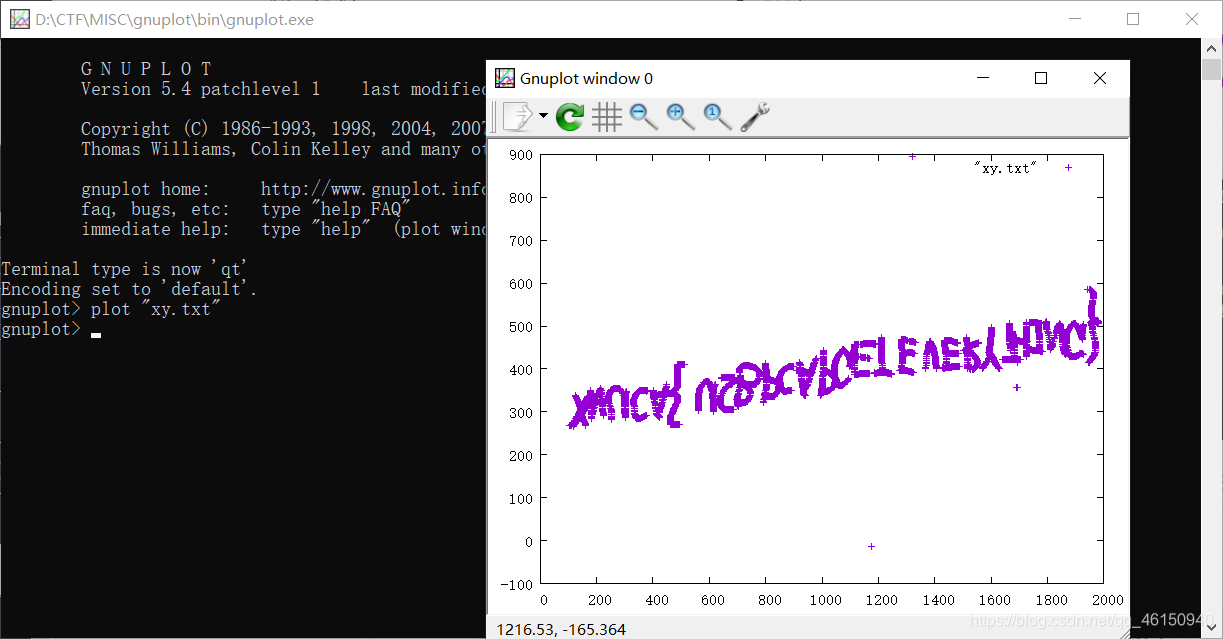
翻转一下图片
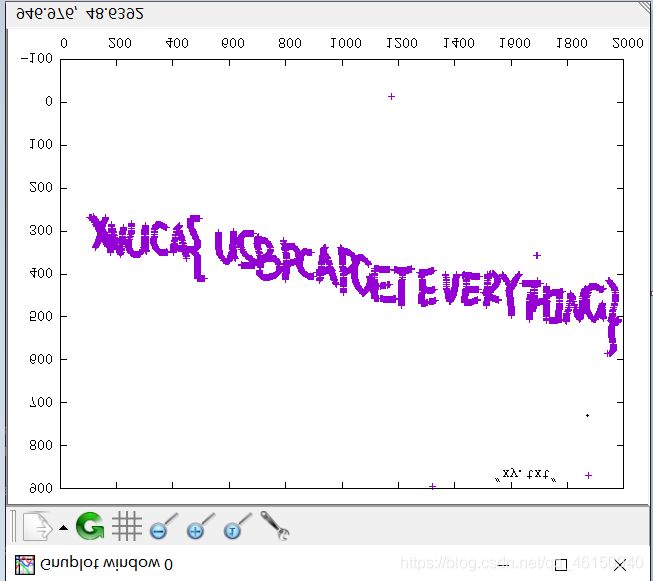
得到flag
XNCA{U2BPCAPCETEVERYTHING}
也可以利用python脚本画图
import matplotlib.pyplot as plt
import numpy as np
x, y = np.loadtxt('xy.txt', delimiter=' ', unpack=True)
plt.plot(x, y, '.')
plt.show()
得到

键盘流量
基础知识
USB协议数据部分在Leftover Capture Data域中,数据长度为八个字节。
击键信息集中在第3个字节,每次击键都会产生一个数据包。
参考文档:USB keyboard映射表
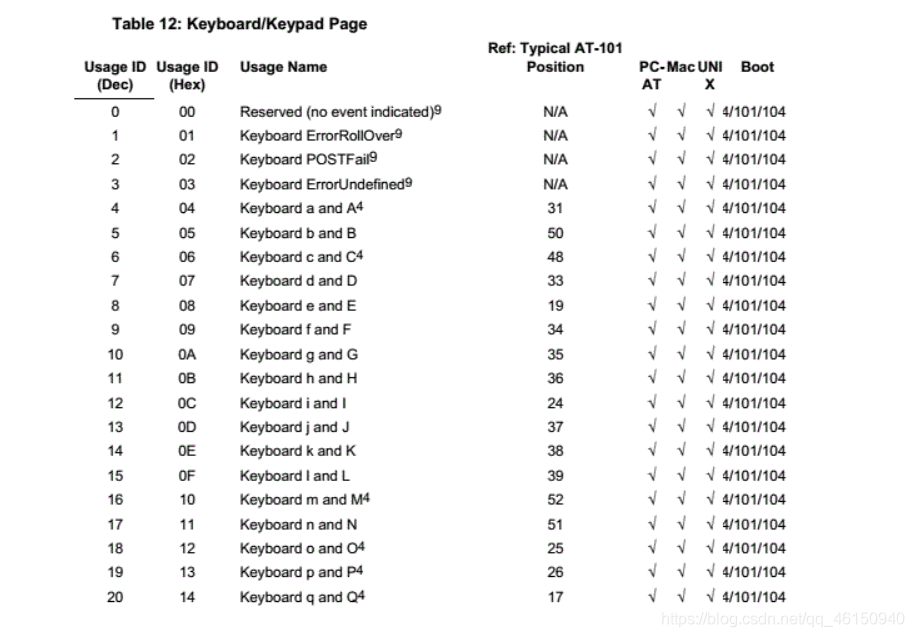
实战练习
flag信息一般隐藏在USB流量中,通过USB协议数据中的键盘键码转换成键位。
题目1:
分析流量包,发现数据是16位,所以是USB键盘流量

tshark提取USB流量
tshark -r bingbing.pcapng -T fields -e usb.capdata > usbdata.txt
usbdata.txt文件内容

发现提取出来包含空行,使用命令剔除空行
tshark -r bingbing.pcapng -T fields -e usb.capdata | sed '/^\s*$/d' > usbdata.txt
查看usbdata.txt空余行消失

提取出来的数据可能会带冒号,也可能不带,但是一般的脚本都会按照有冒号的数据来识别。有冒号时提取数据的[6:8],无冒号时数据在[4:6]
可以利用脚本加上冒号
f=open('usbdata.txt','r')
fi=open('out.txt','w')
while 1:
a=f.readline().strip()
if a:
if len(a)==16: # 键盘流量len=16,鼠标流量len=8
out=''
for i in range(0,len(a),2):
if i+2 != len(a):
out+=a[i]+a[i+1]+":"
else:
out+=a[i]+a[i+1]
fi.write(out)
fi.write('\n')
else:
break
fi.close()

在网上找到两个键盘流量脚本
keyboard1.py
mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." }
nums = []
keys = open('out.txt')
for line in keys:
if line[0]!='0' or line[1]!='0' or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0':
continue
nums.append(int(line[6:8],16))
keys.close()
output = ""
for n in nums:
if n == 0 :
continue
if n in mappings:
output += mappings[n]
else:
output += '[unknown]'
print 'output :\n' + output
运行脚本得到:
┌──(kali㉿kali)-[~/桌面/Python/USB]
└─$ python keyboard.py
output :
666C61677B3866396564326639333365662[DEL]31346138643035323364303334396531323939637D
因为[DEL]是删除键,所以
666C61677B38663965643266393333656631346138643035323364303334396531323939637D
keyboard2.py
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t",
"2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\",
"32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".",
"38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>",
"3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>",
"44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>",
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"",
"34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>",
"3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>",
"41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('out.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))
运行脚本得到
┌──(kali㉿kali)-[~/桌面/Python/USB]
└─$ python keyboard2.py bingbing.pcapng
666c61677b3866396564326639333365662<DEL>31346138643035323364303334396531323939637d
output :666c61677b38663965643266393333656631346138643035323364303334396531323939637d
使用脚本将十六进制转换为字符串
m="666C61677B38663965643266393333656631346138643035323364303334396531323939637D"
s=bytes.fromhex(m)
print(s)
得到
b'flag{8f9ed2f933ef14a8d0523d0349e1299c}'
题目2:

提取流量
tshark -r key.pcap -T fields -e usb.capdata > usbdata.txt
查看usbdata.txt内容

这是找到的第三个脚本UsbKeyboardDataHacker.py
#!/usr/bin/env python3
import sys
import os
DataFileName = "usb.dat"
presses = []
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
def main():
# check argv
if len(sys.argv) != 2:
print("Usage : ")
print(" python UsbKeyboardHacker.py data.pcap")
print("Tips : ")
print(" To use this python script , you must install the tshark first.")
print(" You can use `sudo apt-get install tshark` to install it")
print("Author : ")
print(" WangYihang <wangyihanger@gmail.com>")
print(" If you have any questions , please contact me by email.")
print(" Thank you for using.")
exit(1)
# get argv
pcapFilePath = sys.argv[1]
# get data of pcap
os.system("tshark -r %s -T fields -e usb.capdata 'usb.data_len == 8' > %s" % (pcapFilePath, DataFileName))
# read data
with open(DataFileName, "r") as f:
for line in f:
presses.append(line[0:-1])
# handle
result = ""
for press in presses:
if press == '':
continue
if ':' in press:
Bytes = press.split(":")
else:
Bytes = [press[i:i+2] for i in range(0, len(press), 2)]
if Bytes[0] == "00":
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += normalKeys[Bytes[2]]
elif int(Bytes[0],16) & 0b10 or int(Bytes[0],16) & 0b100000: # shift key is pressed.
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += shiftKeys[Bytes[2]]
else:
print("[-] Unknow Key : %s" % (Bytes[0]))
print("[+] Found : %s" % (result))
# clean the temp data
os.system("rm ./%s" % (DataFileName))
if __name__ == "__main__":
main()
运行脚本
└─$ python3 UsbKeyboardDataHacker.py key.pcap 1 ⨯
[-] Unknow Key : 01
[-] Unknow Key : 01
[+] Found : aababacbbdbdccccdcdcdbbcccbcbbcbbaababaaaaaaaaaaaaaaaaaakey{xinan}
参考文章:
https://blog.csdn.net/qq_45555226/article/details/102810474
https://github.com/WangYihang/UsbMiceDataHacker
https://blog.csdn.net/qq_43431158/article/details/108717829
CTF流量分析总结题目:
https://pan.baidu.com/s/1bGEIPeXDCbhybmWOyGr8Og#list/path=%2F
提取码:q6ro








 本文详细介绍了如何解析USB鼠标和键盘流量数据,用于CTF竞赛中的信息隐藏。通过Python脚本,从Wireshark捕获的流量包中提取鼠标和键盘的移动轨迹及按键信息,并转换为坐标或字符。实战练习中,展示了不同脚本的使用,以及如何将流量数据转化为可读的字符串,最终揭示隐藏的flag。
本文详细介绍了如何解析USB鼠标和键盘流量数据,用于CTF竞赛中的信息隐藏。通过Python脚本,从Wireshark捕获的流量包中提取鼠标和键盘的移动轨迹及按键信息,并转换为坐标或字符。实战练习中,展示了不同脚本的使用,以及如何将流量数据转化为可读的字符串,最终揭示隐藏的flag。

















 875
875

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










