目录
一、简介
1.1、概述:
为了确保有一个成功的渗透测试 , 必须需要知道目标系统中服务的指纹信息。 服务指 纹信息包括服务端口 、 服务名和版本等
二、工具
2.1、Nmap(识别服务指纹信息)
使用:
【端口扫描工具】nmap核心使用方法
https://blog.csdn.net/qq_53079406/article/details/125263917?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522165932934416781432923359%2522%252C%2522scm%2522%253A%252220140713.130102334.pc%255Fblog.%2522%257D&request_id=165932934416781432923359&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2~blog~first_rank_ecpm_v1~rank_v31_ecpm-1-125263917-null-null.nonecase&utm_term=nmap&spm=1018.2226.3001.4450nmap“扫描基础”“端口扫描技术”“服务和版本探测”“操作系统探测”“时间和性能”“防火墙/IDS躲避和哄骗”相关参考指南
https://blog.csdn.net/qq_53079406/article/details/122759253?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522165932934416781432923359%2522%252C%2522scm%2522%253A%252220140713.130102334.pc%255Fblog.%2522%257D&request_id=165932934416781432923359&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2~blog~first_rank_ecpm_v1~rank_v31_ecpm-4-122759253-null-null.nonecase&utm_term=nmap&spm=1018.2226.3001.4450
测试:
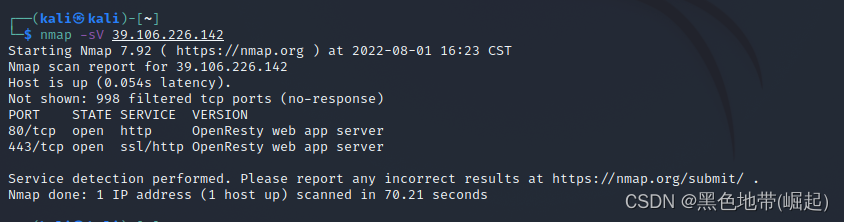
用Nmap工具查看39.106.226.142服务上正在运行的端口
nmap -sV 39.106.226.142
可以查看到目标服务器上运行的端口号、各个端口对应的服务及版本信息
2.2、Amap(服务枚举工具)
简介:
Amap是一个服务枚举工具。 使用该工具能识别正运行在 一 ·个指定端口或一个范围端
口上的应用程序
安装:
sudo apt install amap
命令:
Syntax: amap [-A|-B|-P|-W] [-1buSRHUdqv] [[-m] -o <file>] [-D <file>] [-t/-T sec] [-c cons] [-C retries] [-p proto] [-i <file>] [target port [port] ...] Modes: -A Map applications: send triggers and analyse responses (default) -B Just grab banners, do not send triggers -P No banner or application stuff - be a (full connect) port scanner Options: -1 Only send triggers to a port until 1st identification. Speeeeed! -6 Use IPv6 instead of IPv4 -b Print ascii banner of responses -i FILE Nmap machine readable outputfile to read ports from -u Ports specified on commandline are UDP (default is TCP) -R Do NOT identify RPC service -H Do NOT send application triggers marked as potentially harmful -U Do NOT dump unrecognised responses (better for scripting) -d Dump all responses -v Verbose mode, use twice (or more!) for debug (not recommended :-) -q Do not report closed ports, and do not print them as unidentified -o FILE [-m] Write output to file FILE, -m creates machine readable output -c CONS Amount of parallel connections to make (default 32, max 256) -C RETRIES Number of reconnects on connect timeouts (see -T) (default 3) -T SEC Connect timeout on connection attempts in seconds (default 5) -t SEC Response wait timeout in seconds (default 5) -p PROTO Only send triggers for this protocol (e.g. ftp) TARGET PORT The target address and port(s) to scan (additional to -i) amap is a tool to identify application protocols on target ports. Note: this version was NOT compiled with SSL support! Usage hint: Options "-bqv" are recommended, add "-1" for fast/rush checks.
使用:
用Amap 工具在指定的端口(或一段范围), 测试目标主机39.106.226.142上正在运行的应用程序
amap -bqv 39.106.226.142 80

























 844
844











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










