试卷

What is the "hidden terminal"' problem?
什么是“隐藏终端”问题?

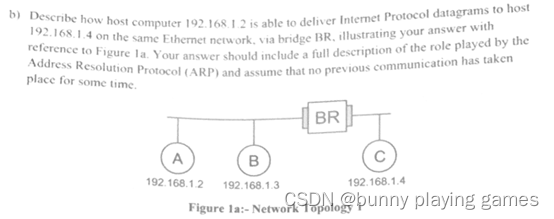
Describe how host computer 192.168.1.2 is able to deliver Internet Protocol datagrams to host 192.168.1.4 on the same Ethernet network, via bridge BR, illustrating your answer with reference to Figure la. Your answer should include a full description of the role played by the Address Resolution Protocol (ARP) and assume that no previous communication has taken place for some time.
描述主机192.168.1.2如何能够通过网桥BR向同一以太网上的主机192.168.1.4发送互联网协议数据报,并参考图a说明你的答案。你的回答应该包括地址解析协议(ARP)所扮演的角色的完整描述,并假设之前的通信已经有一段时间没有发生了。

c) The bridge is now replaced with a router RT as shown in Figure 1b. Explain any differences that would arise in the process of how host 192.168.1.2 delivers data to host 192.168.2.4.Once again, assume that no previous communication has taken place for some time
c)桥接器现在被路由器RT取代,如图1b所示。解释主机192.168.1.2向主机192.168.2.4传递数据的过程中可能出现的任何差异。再一次,假设之前有一段时间没有通信了
这里搁置一下
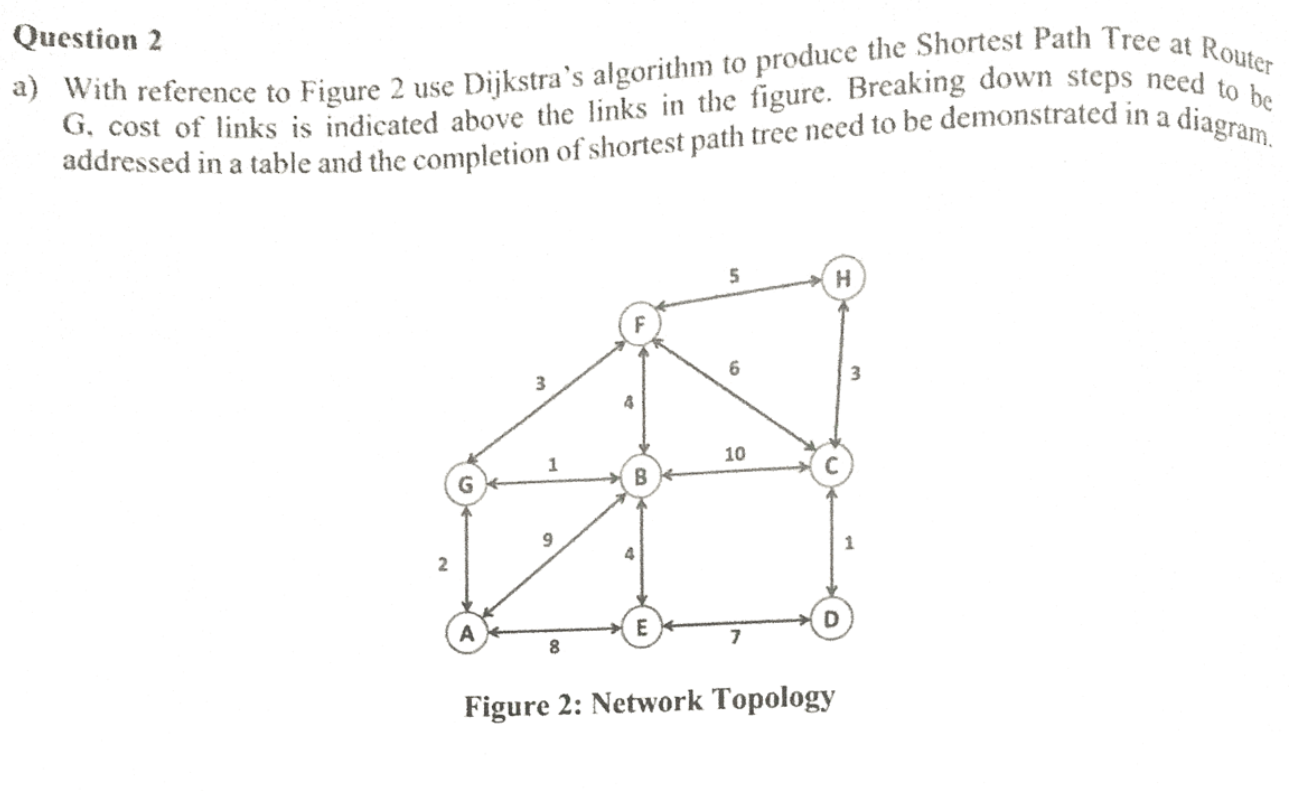
a) With reference to Figure 2 use Dijkstra's algorithm to produce the Shortest Path Tree at Router
G, cost of links is indicated above the links in the figure. Breaking down steps need toaddressed in a table and the completion of shortest path tree need to be demonstrated in a diagram.

b) Explain the ABR route maintenance when
i)DEST moves;
ii) IN moves.

c) Name three proposed multicast routing protocols in mobile ad-hoc networks.

a) Considering the traditional TCP in wired lP network,
i) What are the advantages and disadvantages of the fact that TCP acknowledgements are
cumulative?

) Whatu ionl ihe reception of duplicate acknowledgements?

ii) How is this information used in TCP Reno to maintain channcl utilisation?

b) Explain in details two reasons why current TCP does not nerform well in ad hoc wireless
networks.

c) Considering the TCP in Mobile Ad Hoc Networks,
i) Explain which state is introduced in TCP-F and how it works.
ii) What arc the problcms of TCP-F?

Question 4
a) Several applications for MANETs have been proposed but, currently, none have been realised
commercially. Describe three possible applications. In each case, comment on one potentialadvantage and one reason why the application has not been a commercial success.

b) TCP congestion control uses 4 basic mechanisms known as Additive Increase (AI),
Multiplicative Decrease (MD),Slow Start and Fast Recovery.
i) Briefly explain each of those 4 basic mechanisms.
ii) Describe the commons and differences in the design of TCP Tahoe and TCP Reno.
Show how those 4 basic mechanisms were applied in the designs.

c)Describe how stable routes are identified in Associativity-Based Routing,(ABR).
三次PRE
1
Assume you are responsible for managing IP address distribution. You have millions of IP addresses to assign to various organizations. Their applications are based on the companies’ operational scale, which varies from tens to thousands. The scenarios also include the companies asking for IP address usage expansion or reduction in later phase. If you have full freedom to design the IP address management structure. How would you like to do it? Explain in depth as much as you can.
假设您负责管理IP地址分配。您有数百万个IP地址可以分配给不同的组织。他们的应用是基于公司的运营规模,从数万到数千不等。该场景还包括企业在后期要求扩大或减少IP地址的使用。如果你有充分的自由设计IP地址管理结构。你想怎么做?尽可能深入地解释。
If the network is not very complex, the number of computers is not too many, and the network administrator can devote a lot of time and effort to the management of switch ports, there is the possibility of good management. In addition, you can also give up the management of the access layer switches, IP/MAC binding to the core switch to reduce the workload of maintenance, however, this approach may not meet the requirements of security access, because illegal access to the access layer may also affect the security of the entire network.
Therefore, small and medium-sized enterprises are best to use the static IP method, switch ports on the binding MAC to achieve two-way binding, to achieve access control of the computer.
If the network is too complex, and the number of many, this time on the switch port binding IP/MAC is a very tedious thing, it is difficult to stick to the end. With the increase of laptops, the demand of mobile office is getting more and more prosperous, it is impossible to imagine the situation of binding MAC addresses of multiple laptops to multiple ports of multiple switches, how to manage the network ports in public office area is also a bigger problem, and the cleanup of guest computers and obsolete computers is also a more tedious work.
Therefore, it is better for large and medium-sized enterprises to use DHCP method, using the enhanced function of DHCP server to dynamically assign specified IP addresses to network users, thus achieving the binding of users, IPs and MACs, realizing the security of access in the enterprise network and ensuring the safe operation of the enterprise network. It also limits the IP addresses that computers can obtain for management purposes. Router configuration IP/MAC binding function, that is, according to the configuration of network management, identify the MAC address of the computer issued a specific IP, so that the IP can be managed.
如果网络不是很复杂,计算机数量不是太多,网络管理员可以投入大量的时间和精力对交换机端口进行管理,就有可能管理好。此外,还可以放弃对接入层交换机的管理,将IP/MAC绑定到核心交换机上,减少维护工作量,但这种方式可能无法满足安全接入的要求,因为非法接入接入层也可能影响整个网络的安全。
因此,中小企业最好采用静态IP方式,在交换机端口上绑定MAC实现双向绑定,实现对计算机的访问控制。
如果网络太复杂,而且数量很多,这个时候在交换机端口上绑定IP/MAC是一件很繁琐的事情,很难坚持到底。随着笔记本电脑的增加,移动办公的需求越来越旺盛,无法想象多台笔记本电脑的MAC地址绑定到多台交换机的多个端口的情况,如何管理公共办公区的网口也是一个更大的问题,客用电脑和废弃电脑的清理也是一项更加繁琐的工作。
因此,大中型企业最好采用DHCP方式,利用DHCP服务器的增强功能,为网络用户动态分配指定的IP地址,从而实现用户、IP和mac的绑定,实现企业网络的安全接入,保证企业网络的安全运行。它还限制了计算机为管理目的而获取的IP地址。路由器配置IP/MAC绑定功能,即根据网管的配置,识别计算机的MAC地址发放特定的IP,使该IP能够被管理。
2
Assume you are going to design a routing protocol for Mobile Ad Hoc networks, what kind of route would you like to establish? To achieve your route selection goal, what is the necessary information and how do you think that information is gathered in your protocol design? Explain as much detailed as you can.
假设您要为移动Ad Hoc网络设计一个路由协议,您希望建立什么样的路由?为了达到你的路由选择目标,什么是必要的信息,你认为在你的协议设计中如何收集这些信息?尽可能详细地解释。
3
What do you think are the technical features of reliable transmission? List all you can think of and give explanation in details.
你认为可靠传输的技术特征是什么?列出所有你能想到的,并详细解释。
Transmission technology is a technology that makes full use of the transmission capabilities of different channels to form a complete transmission system that enables the reliable transmission of information. The transmission system is an important part of the communication system, and the transmission technology depends mainly on the transmission characteristics of specific channels. The technology that makes full use of the transmission capabilities of different channels to enable reliable transmission of information. Validity and reliability are the two main indicators of channel transmission performance.
Reliable transmission: that is, what is sent at the sender is what is received at the receiver. It also means that there are no transmission errors in the process of data transmission. It is the use of a series of techniques to ensure the accurate and precise transmission of information at the sender and receiver. Actual transmission systems are subject to interference such as noise and dispersion, which affect the reliability of information transmission.
The ideal transmission has two characteristics.
(1) The transmission channel is error-free.
(2) No matter how fast the sender sends data, the receiver always has time to process the received data.
Problems that can occur during data transmission: bit errors, packet loss. Methods of reliable transmission: stop-wait protocol, sliding window protocol.
No actual network has the two ideal characteristics mentioned above. But we can use some reliable transmission protocols that allow the sender to retransmit the erroneous data in case of errors, and at the same time inform the sender to reduce the speed of data transmission in time when the receiver has too much time to process the received data - flow control. In this way an otherwise unreliable channel can achieve reliable transmission.
传输技术是充分利用不同信道的传输能力,形成一个完整的传输系统,使信息能够可靠传输的技术。传输系统是通信系统的重要组成部分,而传输技术主要取决于特定信道的传输特性。充分利用不同信道的传输能力,实现信息可靠传输的技术。有效性和信度是信道传输性能的两个主要指标。
可靠传输:即发送方发送的内容就是接收方接收的内容。也就是说数据传输过程中不存在传输错误。它是使用一系列技术来确保信息在发送方和接收方的准确和精确传输。实际传输系统会受到噪声、色散等干扰,影响信息传输的可靠性。
理想的变速器有两个特点。
(1)传输通道无差错。
(2)无论发送方发送数据的速度有多快,接收方总是有时间处理接收到的数据。
数据传输过程中可能出现的问题:误码、丢包。可靠传输方法:停止等待协议、滑动窗口协议。
没有一个实际的网络具有上述两个理想的特征。但我们可以使用一些可靠的传输协议,允许发送方在错误发生时重新传输错误数据,同时在接收方有太多时间处理接收数据时及时通知发送方降低数据传输速度-流控制。通过这种方式,原本不可靠的信道可以实现可靠的传输。
三次TEST(前半节课)
1(答案不确定)
What are the difference between neighbours and adjacencies in OSPF?
OSPF中邻居和邻接的区别是什么?
Routers running OSPF need to exchange link state information and routing information with each other, and before exchanging these information routers need to establish neighbor relationship first.
OSPF-speaking routers send Hello packets out all OSPF enabled interfaces. If two routers sharing a common data link agree on certain parameters specified in their respective Hello packets, they will become neighbours – discovery mechanism
Neighbor: Once an OSPF router starts up, it sends a Hello message out through the OSPF interface to discover its neighbors. The OSPF router that receives the Hello message will check some parameters defined in the message and if both parties agree, a neighbor relationship will be formed.
Adjacency: Adjacencies, which may be thought of as virtual point-to-point links, are formed between some neighbours. OSPF defines several network types and several router types. The establishment of an adjacency is determined by the types of routers exchanging Hellos and the type of network over which the Hellos are exchanged
Both parties forming a neighbor relationship may not always form an adjacency relationship, depending on the network type. Only after both parties successfully exchange DD messages and are able to exchange LSAs, an adjacency relationship is formed in the true sense.
The router must discover the neighbor and establish the neighbor relationship before sending LSAs.
运行OSPF协议的路由器之间需要交换链路状态信息和路由信息,在交换这些信息之前,需要先建立邻居关系。
使用OSPF协议的路由器会向所有使能OSPF协议的接口发送Hello报文。如果共用一条数据链路的两台路由器对各自Hello报文中的某些参数达成一致,它们就会成为邻居——发现机制
邻居:OSPF路由器一旦启动,就会通过OSPF接口向外发送Hello报文来发现邻居。收到Hello报文的OSPF路由器会检查Hello报文中定义的一些参数,如果双方都同意,就会建立邻居关系。
邻接:邻接可以被认为是虚拟的点对点连接,是在一些邻居之间形成的。OSPF定义了几种网络类型和路由器类型。邻接关系的建立取决于交换hello的路由器类型和交换hello的网络类型
形成邻居关系的双方不一定总是形成邻接关系,这取决于网络类型。只有双方成功交换DD消息并能够交换lsa,才能形成真正意义上的邻接关系。
路由器在发送lsa之前必须发现邻居并建立邻居关系。
2
What the node will do without receiving the RREP message in AODV?
如果在AODV中没有接收到RREP消息,节点将会做什么?
According to the PPT
Route Requests (RREQ) : When a node re-broadcasts a Route Request, it sets up a reverse path pointing towards the source – AODV assumes symmetric (bi-directional) links. When the intended destination receives a Route Request, it replies by sending a Route Reply (RREP).
The RREP message is used for unicast replies to RREQ messages for the purpose of informing the source node that sent the RREQ message about the route to the destination node. The RREP message allows establishing a forward route from the node that received the RREP message to the destination node in the RREP message for sending data to the destination node later.
The RERR message is sent when one or more destination nodes are unreachable due to a link failure and is designed to be able to notify other nodes in the network which destination nodes are unreachable due to failure
The RREQ message is sent by the source node to seek a route to the destination node from the network. If a legitimate route to the destination node exists, the process is completed. When there is no legal route, the source node turns on the timer and after constructing the RREQ message, sends an RREQ message to IP address 255.255.255.255, and after sending the RREQ message, waits for the relevant node to reply to the RREP message within the specified waiting time NET_TRAVERSAL_TIME milliseconds, and if the reply is received in time, the process ends, and if the timeout is still If the reply is not received, the waiting time is updated using the binary exponential fallback method, and the timer timing is turned on again and the RREQ message is sent until the number of times sent exceeds RREQ_RETRIES or the RREP reply is received, then the process ends and the data is discarded and the upper layer protocol is notified that a route to the destination node cannot be established.
So if no RREP message is received in AODV, the node will end the process and discard the data.
路由请求(RREQ):当一个节点重新广播一个路由请求时,它会建立一个指向源的反向路径——AODV假设对称(双向)链路。当预定目的地收到路由请求时,它通过发送路由应答(RREP)进行应答。
RREP消息用于对RREQ消息的单播应答,目的是通知发送RREQ消息的源节点到目的节点的路由。RREP消息允许从接收到RREP消息的节点建立到RREP消息中的目的节点的转发路由,以便稍后将数据发送到目的节点。
当一个或多个目标节点由于链路故障而不可达时,将发送RERR消息,它的设计目的是能够通知网络中的其他节点哪些目标节点由于故障而不可达
RREQ消息由源节点发送,用于从网络中寻找到目标节点的路由。如果存在到目的节点的合法路由,则该过程结束。当没有合法路由时,源节点打开定时器,构造完RREQ消息后,向IP地址255.255.255.255发送RREQ消息,发送完RREQ消息后,等待相关节点在指定的等待时间NET_TRAVERSAL_TIME毫秒内回复RREQ消息,如果及时收到回复则结束,如果超时仍未收到回复,使用二进制指数回退方法更新等待时间,并再次打开定时器计时并发送RREQ消息,直到发送次数超过RREQ_RETRIES或收到RREP应答,则进程结束,数据被丢弃,并通知上层协议到目的节点的路由无法建立。
因此,如果在AODV中没有接收到RREP消息,节点将结束进程并丢弃数据。
3(无答案)
In TCP, how does the byte stream in cooperate with acknowledge number in TCP header?
在TCP中,字节流如何配合TCP报头中的确认数?
三次TEST(后半节课,不含答案,因为不知道我的分数)

>What is the SPF Tree for RG under the network topology?
>Both Distance Vector Algorithm and Dijkstra's Algorithm are Next-hop routing algorithms. Protocols based on these two algorithms are majority in use. Discuss what do you think are the main reasons as Source routing is not popular in wired TCP/IP networks.
网络拓扑下RG的SPF树是什么?
距离矢量算法和Dijkstra算法都是下一跳路由算法。基于这两种算法的协议是目前使用最多的。讨论你认为源路由在有线TCP/IP网络中不流行的主要原因是什么。

>Explain what are the Local Repair procedures in ABR if node E moves out of the route with source node X and destination node Y?
Design one routing algorithm which can be used in ABR to select the best stable route from all possible routes collected at Des. Brief explain the pros. and cons of this algorithm.
解释如果节点E与源节点X和目的节点Y一起移出路由,ABR中的局部修复程序是什么?
设计一种可用于ABR的路由算法,从Des收集的所有可能路由中选择最稳定的路由,并简要说明优点。这个算法的缺点。

1.In Selective Re-transmission scheme, show the potential errors in diagrams when m = 2w - 1 (w is the window size and m is the modulus sequence number)
2.Does Karn's algorithm have any drawback? If so, what scheme you can propose to improve it?
1.在选择性重传方案中, 在图中显示m = 2w - 1时的潜在误差(w为窗口大小,m为模数列)
2。卡恩的算法有缺点吗?如果是,你能提出什么方案来改善它?






















 5353
5353











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








