本测试中网关sun与网关moon之间建立安全连接,连通两个子网,认证使用包含在PKCS12格式的文件中的X.509证书和RSA私钥。连接成功建立之后,在moon网关之后的主机alice上ping网关sun之后的bob主机,以验证连通性。
以下启动botan/net2net-pkcs12测试用例,注意在启动之前需要执行start-testing脚本开启测试环境。
$ cd strongswan-5.8.1/testing
$
$ sudo ./do-tests botan/net2net-pkcs12
Guest kernel : 5.2.11
strongSwan : 5.8.1
Date : 20191029-0605-58
[ ok ] 1 botan/net2net-pkcs12: pre..test..post
Passed : 1
Failed : 0
The results are available in /srv/strongswan-testing/testresults/20191029-0605-58
or via the link http://192.168.0.150/testresults/20191029-0605-58
Finished : 20191029-0606-06
以下为测试用例botan/net2net-pkcs12的测试结果记录文件。
$ ls /srv/strongswan-testing/testresults/20191029-0605-58/botan/net2net-pkcs12/
console.log moon.ipsec.sql moon.swanctl.conf sun.daemon.log sun.strongswan.conf sun.swanctl.pools
index.html moon.iptables moon.swanctl.conns sun.ip.policy sun.swanctl.algs sun.swanctl.sas
moon.auth.log moon.iptables-save moon.swanctl.pols sun.ip.route sun.swanctl.authorities sun.swanctl.stats
moon.daemon.log moon.strongswan.conf moon.swanctl.pools sun.ip.state sun.swanctl.certs sun.tcpdump.log
moon.ip.policy moon.swanctl.algs moon.swanctl.sas sun.ipsec.sql sun.swanctl.conf
moon.ip.route moon.swanctl.authorities moon.swanctl.stats sun.iptables sun.swanctl.conns
moon.ip.state moon.swanctl.certs sun.auth.log sun.iptables-save sun.swanctl.pols
以上测试结果文件记录了测试过程中虚拟网关sun以及网关moon的各种状态信息和运行日志。测试拓扑如下:

测试配置文件
配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/test.conf,内容如下。VIRTHOSTS变量定义了本测试用来需要使用的的虚拟主机列表。DIAGRAM指定了测试报告中使用的测试拓扑图,如上所示。变量IPSECHOSTS定义了测试中参与IPSec隧道建立的虚拟主机名称。SWANCTL为1表明使用命令行工具swanctl与主进程charon通信,而不是ipsec命令。
VIRTHOSTS="alice moon winnetou sun bob"
# Corresponding block diagram
#
DIAGRAM="a-m-w-s-b.png"
# Guest instances on which tcpdump is to be started
#
TCPDUMPHOSTS="sun"
# Guest instances on which IPsec is started
# Used for IPsec logging purposes
#
IPSECHOSTS="moon sun"
# charon controlled by swanctl
#
SWANCTL=1
网关sun配置
连接配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/hosts/sun/etc/swanctl/swanctl.conf,内容如下。虚拟网关sun的IP地址为192.168.0.2,而远端moon网关的IP地址为192.168.0.1。
另外,此连接(名称gw-gw)使用的proposals指定为:aes128-sha256-modp3072。子连接net-net使用的esp_proposals指定为:aes128gcm128-modp3072。version等于2表明使用IKEv2版本。
secrets部分指定PKCS12格式的证书文件:sunCert.p12,其中包含有证书和秘钥,此证书由secret字段指定的密码保护。
connections {
gw-gw {
local_addrs = 192.168.0.2
remote_addrs = 192.168.0.1
local {
auth = pubkey
id = sun.strongswan.org
}
remote {
auth = pubkey
id = moon.strongswan.org
}
children {
net-net {
local_ts = 10.2.0.0/16
remote_ts = 10.1.0.0/16
updown = /usr/local/libexec/ipsec/_updown iptables
esp_proposals = aes128gcm128-modp3072
}
}
version = 2
mobike = no
proposals = aes128-sha256-modp3072
}
}
secrets {
pkcs12-sun {
file = sunCert.p12
secret = "IxjQVCF3JGI+MoPi"
}
}
StrongSwan配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/hosts/sun/etc/strongswan.conf ,内容如下,指定需要加载的模块。注意这里的botan模块为本次需要测试的功能模块。
# /etc/strongswan.conf - strongSwan configuration file
charon {
load = pem nonce revocation botan x509 curl vici kernel-netlink socket-default updown
multiple_authentication = no
}
由于默认的证书文件使用PEM格式,在此次测试中不能使用,所以提供了如下的PKCS12证书文件。
$ ls strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/hosts/sun/etc/swanctl/pkcs12/
sunCert.p12
如下为证书sunCert.p12的部分内容,使用openssl命令显示时提示Import密码,需要输入以上swanctl.conf文件中定义的密码。此p12证书由三个部分组成:2个证书包和一个私钥。其中第一个证书包为CA签发给sun主机的证书;第二个证书包为根证书。
strongswan-5.8.1/testing/tests/botan/net2net-pkcs12$ openssl pkcs12 -in hosts/sun/etc/swanctl/pkcs12/sunCert.p12 -info
Enter Import Password:
MAC: sha1, Iteration 2048
MAC length: 20, salt length: 8
PKCS7 Encrypted data: pbeWithSHA1And40BitRC2-CBC, Iteration 2048
Certificate bag
Bag Attributes
friendlyName: sun
localKeyID: BC E2 76 C8 87 E4 15 46 CA 94 4E 44 28 8F 64 DC 29 01 2C 95
subject=C = CH, O = strongSwan Project, CN = sun.strongswan.org
issuer=C = CH, O = strongSwan Project, CN = strongSwan Root CA
-----BEGIN CERTIFICATE-----
MIIEhjCCAu6gAwIBAgIBBDANBgkqhkiG9w0BAQsFADBHMQswCQYDVQQGEwJDSDEb
...
g3abN2hCuoXcDw==
-----END CERTIFICATE-----
Certificate bag
Bag Attributes
friendlyName: strongSwan Root CA
subject=C = CH, O = strongSwan Project, CN = strongSwan Root CA
issuer=C = CH, O = strongSwan Project, CN = strongSwan Root CA
-----BEGIN CERTIFICATE-----
MIIEVTCCAr2gAwIBAgIIHfCCbsYXyOIwDQYJKoZIhvcNAQELBQAwRzELMAkGA1UE
...
Y6HfnUnG7HND
-----END CERTIFICATE-----
PKCS7 Data
Shrouded Keybag: pbeWithSHA1And3-KeyTripleDES-CBC, Iteration 2048
Bag Attributes
friendlyName: sun
localKeyID: BC E2 76 C8 87 E4 15 46 CA 94 4E 44 28 8F 64 DC 29 01 2C 95
Key Attributes: <No Attributes>
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIHXDBOBgkqhkiG9w0BBQ0wQTApBgkqhkiG9w0BBQwwHAQInIZn6oIFPasCAggA
...
82Sf+yuqO/huWw4ixlR8sg==
-----END ENCRYPTED PRIVATE KEY-----
moon网关配置
配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/hosts/moon/etc/swanctl/swanctl.conf,内容如下。连接gw-gw的proposals使用:aes128-sha256-modp3072,子连net-net的esp_proposals使用:aes128gcm128-modp3072。IKE使用IKEv2版。
gw-gw连接的本地IP地址为:192.168.0.1,对端的IP地址为:192.168.0.2,即sun网关的IP地址。
secrets部分指定PKCS12格式的证书文件:moonCert.p12,其中包含有证书和秘钥,此证书由secret字段指定的密码保护。
connections {
gw-gw {
local_addrs = 192.168.0.1
remote_addrs = 192.168.0.2
local {
auth = pubkey
id = moon.strongswan.org
}
remote {
auth = pubkey
id = sun.strongswan.org
}
children {
net-net {
local_ts = 10.1.0.0/16
remote_ts = 10.2.0.0/16
updown = /usr/local/libexec/ipsec/_updown iptables
esp_proposals = aes128gcm128-modp3072
}
}
version = 2
mobike = no
proposals = aes128-sha256-modp3072
}
}
secrets {
pkcs12-moon {
file = moonCert.p12
secret = "kUqd8O7mzbjXNJKQ"
}
}
StrongSwan配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/hosts/moon/etc/strongswan.conf,内容如下,指定要加载的模块。这里指定加载botan模块,其正是我们要测试的模块。
# /etc/strongswan.conf - strongSwan configuration file
charon {
load = pem nonce revocation botan x509 curl vici kernel-netlink socket-default updown
multiple_authentication = no
}
由于默认的证书文件使用PEM格式,在此次测试中不能使用,所以提供了如下的证书文件。
$ ls strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/hosts/moon/etc/swanctl/pkcs12/
moonCert.p12
如下为证书moonCert.p12的部分内容,使用openssl命令显示时提示Import密码,需要输入以上swanctl.conf文件中定义的密码。此p12证书由三个部分组成:2个证书包和一个私钥。其中第一个证书包为CA签发给moon主机的证书(CN = moon.strongswan.org);第二个证书包为根证书(CN = strongSwan Root CA)。
strongswan-5.8.1/testing/tests/botan/net2net-pkcs12$ openssl pkcs12 -in hosts/moon/etc/swanctl/pkcs12/moonCert.p12 -info
Enter Import Password:
MAC: sha1, Iteration 2048
MAC length: 20, salt length: 8
PKCS7 Encrypted data: pbeWithSHA1And40BitRC2-CBC, Iteration 2048
Certificate bag
Bag Attributes
friendlyName: moon
localKeyID: 34 46 34 B9 5A A6 28 33 B2 C1 EC FE 29 09 ED 36 78 5D 10 EA
subject=C = CH, O = strongSwan Project, CN = moon.strongswan.org
issuer=C = CH, O = strongSwan Project, CN = strongSwan Root CA
-----BEGIN CERTIFICATE-----
MIIEiDCCAvCgAwIBAgIBAzANBgkqhkiG9w0BAQsFADBHMQswCQYDVQQGEwJDSDEb
...
cbvYQ0LdGFckRIK1
-----END CERTIFICATE-----
Certificate bag
Bag Attributes
friendlyName: strongSwan Root CA
subject=C = CH, O = strongSwan Project, CN = strongSwan Root CA
issuer=C = CH, O = strongSwan Project, CN = strongSwan Root CA
-----BEGIN CERTIFICATE-----
MIIEVTCCAr2gAwIBAgIIHfCCbsYXyOIwDQYJKoZIhvcNAQELBQAwRzELMAkGA1UE
...
Y6HfnUnG7HND
-----END CERTIFICATE-----
PKCS7 Data
Shrouded Keybag: pbeWithSHA1And3-KeyTripleDES-CBC, Iteration 2048
Bag Attributes
friendlyName: moon
localKeyID: 34 46 34 B9 5A A6 28 33 B2 C1 EC FE 29 09 ED 36 78 5D 10 EA
Key Attributes: <No Attributes>
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIHXDBOBgkqhkiG9w0BBQ0wQTApBgkqhkiG9w0BBQwwHAQILqHYzwhGnWECAggA
...
uYyOMQoeY77LeaxEWMpBrw==
-----END ENCRYPTED PRIVATE KEY-----
准备阶段
配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/pretest.dat,内容如下。在预测试pre-test阶段,首先删除moon和sun系统中默认的PEM格式的证书和密钥文件,接着备份moon和sun主机的iptables配置。启动strongswan。使用脚本expect-connection检测名称为gw-gw的连接是否建立,超过5秒钟检测不到,打印失败信息。swanctl在moon网关上初始化一个名称为net-net的子连接。
通过之前的介绍已经在sun和moon网关的各自配置文件(/etc/swanctl/swanctl.conf)中看到了gw-gw和net-net连接的配置信息。
moon::cd /etc/swanctl; rm rsa/moonKey.pem x509/moonCert.pem x509ca/strongswanCert.pem
sun::cd /etc/swanctl; rm rsa/sunKey.pem x509/sunCert.pem x509ca/strongswanCert.pem
moon::iptables-restore < /etc/iptables.rules
sun::iptables-restore < /etc/iptables.rules
moon::systemctl start strongswan
sun::systemctl start strongswan
moon::expect-connection gw-gw
sun::expect-connection gw-gw
moon::swanctl --initiate --child net-net 2> /dev/null
测试阶段
配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/evaltest.dat,内容如下。在第一行测试语句中,在alice主机上ping主机bob的地址:PH_IP_BOB,并检查ping返回信息。
alice::ping -c 1 PH_IP_BOB::64 bytes from PH_IP_BOB: icmp_.eq=1::YES
moon::swanctl --list-sas --raw 2> /dev/null::gw-gw.*version=2 state=ESTABLISHED local-host=192.168.0.1 local-port=500 local-id=moon.strongswan.org remote-host=192.168.0.2 remote-port=500 remote-id=sun.strongswan.org initiator=yes.*encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128 prf-alg=PRF_HMAC_SHA2_256 dh-group=MODP_3072.*child-sas.*net-net.*state=INSTALLED mode=TUNNEL.*ESP.*encr-alg=AES_GCM_16 encr-keysize=128.*local-ts=\[10.1.0.0/16] remote-ts=\[10.2.0.0/16]::YES
sun:: swanctl --list-sas --raw 2> /dev/null::gw-gw.*version=2 state=ESTABLISHED local-host=192.168.0.2 local-port=500 local-id=sun.strongswan.org remote-host=192.168.0.1 remote-port=500 remote-id=moon.strongswan.org.*encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128 prf-alg=PRF_HMAC_SHA2_256 dh-group=MODP_3072.*child-sas.*net-net.*state=INSTALLED mode=TUNNEL.*ESP.*encr-alg=AES_GCM_16 encr-keysize=128.*local-ts=\[10.2.0.0/16] remote-ts=\[10.1.0.0/16]::YES
sun::tcpdump::IP moon.strongswan.org > sun.strongswan.org: ESP::YES
sun::tcpdump::IP sun.strongswan.org > moon.strongswan.org: ESP::YES
第二行测试语句登录到moon网关中,使用命令swanctl --list-sas --raw显示安全关联SA的信息,在其中匹配随后的模式pattern字段,可见与以上hosts/moon/etc/swanctl/swanctl.conf中的配置相符。以下为swanctl的输出信息。
gw-gw: #1, ESTABLISHED, IKEv2, 03176e9bd33240b6_i* 4d7c1f300c747012_r
local 'moon.strongswan.org' @ 192.168.0.1[500]
remote 'sun.strongswan.org' @ 192.168.0.2[500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_3072
established 1s ago, rekeying in 13999s
net-net: #1, reqid 1, INSTALLED, TUNNEL, ESP:AES_GCM_16-128
installed 1s ago, rekeying in 3286s, expires in 3959s
in c33b9296, 84 bytes, 1 packets, 1s ago
out ca1517a2, 84 bytes, 1 packets, 1s ago
local 10.1.0.0/16
remote 10.2.0.0/16
第三行测试语句与第二行类似,此处登录的sun网关上执行swanctl --list-sas --raw命令检查输出结果,进行匹配操作。以下为sun虚拟网关上执行swanctl命令的输出:
gw-gw: #1, ESTABLISHED, IKEv2, 03176e9bd33240b6_i 4d7c1f300c747012_r*
local 'sun.strongswan.org' @ 192.168.0.2[500]
remote 'moon.strongswan.org' @ 192.168.0.1[500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_3072
established 3s ago, rekeying in 13271s
net-net: #1, reqid 1, INSTALLED, TUNNEL, ESP:AES_GCM_16-128
installed 3s ago, rekeying in 3529s, expires in 3957s
in ca1517a2, 84 bytes, 1 packets, 2s ago
out c33b9296, 84 bytes, 1 packets, 2s ago
local 10.2.0.0/16
remote 10.1.0.0/16
最后两行都在sun网关上执行,这里的tcpdump命令并不执行,而是检查在以上的测试过程中后台tcpdump命令输出到文件/tmp/tcpdump.log中的日志信息,确认sun与moon之间的ESP加密的ping报文是否正常。
06:06:05.059470 IP moon.strongswan.org > sun.strongswan.org: ESP(spi=0xca1517a2,seq=0x1), length 120
06:06:05.059561 IP alice.strongswan.org > bob.strongswan.org: ICMP echo request, id 4996, seq 1, length 64
06:06:05.064523 IP sun.strongswan.org > moon.strongswan.org: ESP(spi=0xc33b9296,seq=0x1), length 120
以下为sun网关上的日志文件/var/log/daemon.log的部分内容,可见其中加载的PKCS12格式的证书文件sunCert.p12,由其加载了sun的客户证书,以及CA根证书和RSA私钥。
Oct 29 06:06:04 sun charon-systemd: 13[CFG] loaded certificate 'C=CH, O=strongSwan Project, CN=strongSwan Root CA'
Oct 29 06:06:04 sun swanctl[4963]: C=CH, O=strongSwan Project, CN=strongSwan Root CA
Oct 29 06:06:04 sun charon-systemd: 13[CFG] loaded certificate 'C=CH, O=strongSwan Project, CN=sun.strongswan.org'
Oct 29 06:06:04 sun swanctl[4963]: C=CH, O=strongSwan Project, CN=sun.strongswan.org
Oct 29 06:06:04 sun charon-systemd: 13[CFG] loaded RSA private key
Oct 29 06:06:04 sun charon-systemd: 13[CFG] added vici connection: gw-gw
Oct 29 06:06:04 sun swanctl[4963]: loaded certificate from '/etc/swanctl/pkcs12/sunCert.p12'
Oct 29 06:06:04 sun swanctl[4963]: loaded certificate from '/etc/swanctl/pkcs12/sunCert.p12'
Oct 29 06:06:04 sun swanctl[4963]: loaded rsa key from '/etc/swanctl/pkcs12/sunCert.p12'
Oct 29 06:06:04 sun swanctl[4963]: loaded connection 'gw-gw'
Oct 29 06:06:04 sun swanctl[4963]: successfully loaded 1 connections, 0 unloaded
Oct 29 06:06:04 sun charon-systemd: 11[CFG] selected peer config 'gw-gw'
Oct 29 06:06:04 sun charon-systemd: 11[CFG] using certificate "C=CH, O=strongSwan Project, CN=moon.strongswan.org"
Oct 29 06:06:04 sun charon-systemd: 11[CFG] using trusted ca certificate "C=CH, O=strongSwan Project, CN=strongSwan Root CA"
Oct 29 06:06:04 sun charon-systemd: 11[CFG] checking certificate status of "C=CH, O=strongSwan Project, CN=moon.strongswan.org"
Oct 29 06:06:04 sun charon-systemd: 11[CFG] fetching crl from 'http://crl.strongswan.org/strongswan.crl' ...
Oct 29 06:06:04 sun charon-systemd: 11[IKE] authentication of 'moon.strongswan.org' with RSA_EMSA_PKCS1_SHA2_256 successful
Oct 29 06:06:04 sun charon-systemd: 11[IKE] authentication of 'sun.strongswan.org' (myself) with RSA_EMSA_PKCS1_SHA2_256 successful
防火墙规则
以下为测试过程中,在虚拟网关sun的filter表中加入的规则(省略了OUTPUT hook点),规则的配置由swanctl.conf文件中指定的updown脚本完成(/usr/local/libexec/ipsec/_updown iptables)。在hook点INPUT上,允许UDP源和目的端口同时为500或者4500的报文,前者为IKE协议端口,后者为NAT-T使用的端口号,另外允许ESP和AH协议的报文通过,由于此测试使用ESP协议,以下AH规则的计数为空。
在FORWARD点上,源IP为10.1.0.0/16,目的IP为10.2.0.0/16的报文匹配入方向(in)的IPSEC策略,reqid为1,协议号为50(ESP)。源IP地址为10.2.0.0/16目的IP为10.1.0.0/16之间的报文分别匹配出方向(out)的IPSEC策略,reqid为1,协议号为50(ESP)。
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1 140 ACCEPT esp -- eth0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT ah -- eth0 * 0.0.0.0/0 0.0.0.0/0
3 2588 ACCEPT udp -- eth0 * 0.0.0.0/0 0.0.0.0/0 udp spt:500 dpt:500
0 0 ACCEPT udp -- eth0 * 0.0.0.0/0 0.0.0.0/0 udp spt:4500 dpt:4500
132 14748 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
1 40 ACCEPT tcp -- eth0 * 192.168.0.150 0.0.0.0/0 tcp spt:80
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1 84 ACCEPT all -- eth0 * 10.1.0.0/16 10.2.0.0/16 policy match dir in pol ipsec reqid 1 proto 50
1 84 ACCEPT all -- * eth0 10.2.0.0/16 10.1.0.0/16 policy match dir out pol ipsec reqid 1 proto 50
收尾阶段
配置文件:strongswan-5.8.1/testing/tests/botan/net2net-pkcs12/posttest.dat,内容如下。其中第一行终止moon和sun网关上的StrongSwan进程。第二、三行恢复moon和sun网关上的iptables规则。最后两行删除moon和sun网关上本次测试使用的PKCS12格式的证书文件。
moon::systemctl stop strongswan
sun::systemctl stop strongswan
moon::iptables-restore < /etc/iptables.flush
sun::iptables-restore < /etc/iptables.flush
moon::rm /etc/swanctl/pkcs12/moonCert.p12
sun::rm /etc/swanctl/pkcs12/sunCert.p12
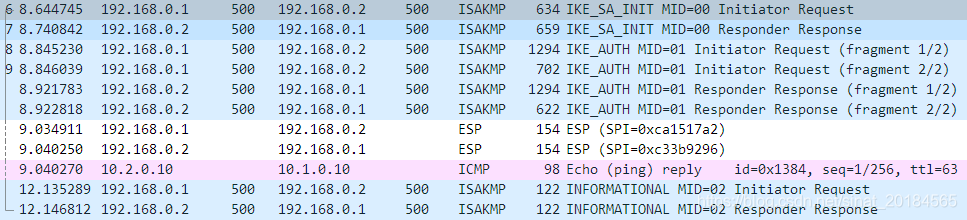
测试结果文件默认都保存在目录:/srv/strongswan-testing/testresults/20191029-0605-58/botan/net2net-pkcs12/下,其中文件console.log 记录了整个的测试过程。文件sun.daemon.log和moon.daemon.log文件记录了各自主机上charon-systemd主进程的日志。完整的测试结果文件列表见本文开始部分。下图为IKEv2报文的交互报文。
END





















 1220
1220











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








