实验环境
本篇记录 IPSec 的 net2net 的组网, 身份认证方式 基于 预共享密钥 (PSK) 模式, 主机采用自定义编译 openwrt-x86 虚拟主机,IPSec 使用 StrongSwan 组件。
测试环境:
- (1)x86-OpenWRT-19.09 镜像
- (2)PVE ( proxmox-6.3.2 )
网络架构
net2net-psk的组网图,我们可以看到我们至少需要两个客户机Alice和Bob,两个网关Moon和Sun。
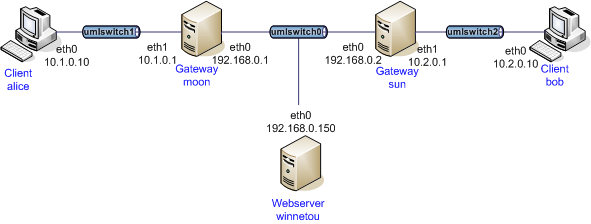
第一步 创建 4台 openwrt 的虚机
如何把 openwrt 的镜像制作制作成 PVE 格式的虚机,请查看 《OpenWrt X86 image 导入到 ProxMox 虚拟机》 文章。
- 配置 alice 网络参数
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'eth0'
option ifname 'eth0'
option proto 'dhcp'
config interface 'eth1'
option ifname 'eth1'
option proto 'static'
option ipaddr '10.1.0.10'
option netmask '255.255.255.0'
- 配置 moon 网络参数
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd87:e822:78d1::/48'
config interface 'eth0'
option ifname 'eth0'
option proto 'dhcp'
config interface 'eth1'
option ifname 'eth1'
option proto 'static'
option ipaddr '10.1.0.1'
option netmask '255.255.255.0'
- 配置 sun 网络参数
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd87:47a2:3306::/48'
config interface 'lan'
option type 'bridge'
option ifname 'lo'
option proto 'static'
option address '192.168.5.1'
option netmask '255.255.255.0'
config interface 'eth0'
option ifname 'eth0'
option proto 'dhcp'
option ip6assign '60'
config interface 'eth1'
option ifname 'eth1'
option proto 'static'
option ipaddr '10.2.0.2'
option netmask '255.255.255.0'
- 配置 bob 网络参数
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'eth0'
option ifname 'eth0'
option proto 'dhcp'
config interface 'eth1'
option ifname 'eth1'
option proto 'static'
option ipaddr '10.2.0.10'
option netmask '255.255.255.0'
第二步 配置 moon 和 sun 虚主机网关
MOON 网关 IPSec 参数配置
- 配置 moon 的 ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
# strictcrlpolicy=yes
# uniqueids = no
# Add connections here.
conn %default
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=1
authby=secret
keyexchange=ikev2
mobike=no
conn net-net
left=192.168.40.80
leftsubnet=10.1.0.0/16
leftid=@moon.strongswan.org
leftfirewall=yes
right=192.168.40.79
rightsubnet=10.2.0.0/16
rightid=@sun.strongswan.org
auto=add
- 配置 ipsec.secrets
# /etc/ipsec.secrets - strongSwan IPsec secrets file
@moon.strongswan.org @sun.strongswan.org : PSK 0sv+NkxY9LLZvwj4qCC2o/gGrWDF2d21jL
@moon.strongswan.org %any : PSK 0x45a30759df97dc26a15b88ff
@sun.strongswan.org : PSK "This is a strong password"
: PSK 'My "home" is my "castle"!'
192.168.40.80 : PSK "Andi's home"
- 配置 strongswan.conf
# strongswan.conf - strongSwan configuration file
#
# Refer to the strongswan.conf(5) manpage for details
#
# Configuration changes should be made in the included files
charon {
load_modular = yes
plugins {
include strongswan.d/charon/*.conf
}
load = random nonce aes sha1 sha2 curve25519 hmac stroke kernel-netlink socket-default updown
multiple_authentication = no
}
include strongswan.d/*.conf
SUN 网关参数配置
- 配置 ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
# strictcrlpolicy=yes
# uniqueids = no
# Add connections here.
conn %default
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=1
authby=secret
keyexchange=ikev2
mobike=no
conn net-net
left=192.168.40.79
leftsubnet=10.2.0.0/16
leftid=@sun.strongswan.org
leftfirewall=yes
right=192.168.40.80
rightsubnet=10.1.0.0/16
rightid=@moon.strongswan.org
auto=add
- 配置 ipsec.secrets
# /etc/ipsec.secrets - strongSwan IPsec secrets file
@moon.strongswan.org @sun.strongswan.org : PSK 0sv+NkxY9LLZvwj4qCC2o/gGrWDF2d21jL
- 配置strongswan.conf
# strongswan.conf - strongSwan configuration file
# Refer to the strongswan.conf(5) manpage for details
# Configuration changes should be made in the included files
charon {
load_modular = yes
plugins {
include strongswan.d/charon/*.conf
}
load = random nonce aes sha1 sha2 curve25519 hmac stroke kernel-netlink socket-default updown
multiple_authentication = no
}
include strongswan.d/*.conf
第三步 配置 alice & bob 客户端虚拟主机路由
alice 的路由配置
route add -net 10.2.0.0/24 gw 10.1.0.1
bob 的路由配置
route add -net 10.1.0.0/24 gw 10.2.0.2
第四步 启动 IPSec
在 moon 虚拟网关上启动 IPSec
ipsec restart
ipsec up net-net
第五步 验证 alice & bob 打流测试
iperf3 -c 10.1.0.10 -t 60
Connecting to host 10.1.0.10, port 5201
[ 5] local 10.2.0.10 port 52260 connected to 10.1.0.10 port 5201
[ ID] Interval Transfer Bitrate Retr Cwnd
[ 5] 0.00-1.00 sec 52.2 MBytes 438 Mbits/sec 0 1.88 MBytes
[ 5] 1.00-2.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 2.00-3.00 sec 50.0 MBytes 419 Mbits/sec 0 1.88 MBytes
[ 5] 3.00-4.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 4.00-5.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 5.00-6.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 6.00-7.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 7.00-8.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 8.00-9.00 sec 48.8 MBytes 409 Mbits/sec 0 1.88 MBytes
[ 5] 9.00-10.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 10.00-11.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 11.00-12.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 12.00-13.00 sec 50.0 MBytes 419 Mbits/sec 0 1.88 MBytes
[ 5] 13.00-14.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 14.00-15.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 15.00-16.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 16.00-17.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 17.00-18.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 18.00-19.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 19.00-20.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 20.00-21.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 21.00-22.00 sec 50.0 MBytes 419 Mbits/sec 0 1.88 MBytes
[ 5] 22.00-23.00 sec 48.8 MBytes 409 Mbits/sec 0 1.88 MBytes
[ 5] 23.00-24.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 24.00-25.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 25.00-26.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 26.00-27.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 27.00-28.00 sec 50.0 MBytes 419 Mbits/sec 0 1.88 MBytes
[ 5] 28.00-29.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 29.00-30.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 30.00-31.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 31.00-32.00 sec 55.0 MBytes 461 Mbits/sec 0 1.88 MBytes
[ 5] 32.00-33.00 sec 48.7 MBytes 409 Mbits/sec 0 1.88 MBytes
[ 5] 33.00-34.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 34.00-35.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 35.00-36.00 sec 53.8 MBytes 451 Mbits/sec 0 1.88 MBytes
[ 5] 36.00-37.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 37.00-38.00 sec 47.5 MBytes 398 Mbits/sec 154 1.39 MBytes
[ 5] 38.00-39.00 sec 51.2 MBytes 430 Mbits/sec 0 1.52 MBytes
[ 5] 39.00-40.00 sec 53.8 MBytes 451 Mbits/sec 0 1.63 MBytes
[ 5] 40.00-41.00 sec 50.0 MBytes 419 Mbits/sec 0 1.71 MBytes
[ 5] 41.00-42.00 sec 51.2 MBytes 430 Mbits/sec 0 1.78 MBytes
[ 5] 42.00-43.00 sec 51.2 MBytes 430 Mbits/sec 0 1.82 MBytes
[ 5] 43.00-44.00 sec 50.0 MBytes 419 Mbits/sec 0 1.85 MBytes
[ 5] 44.00-45.00 sec 51.2 MBytes 430 Mbits/sec 0 1.87 MBytes
[ 5] 45.00-46.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 46.00-47.00 sec 53.8 MBytes 451 Mbits/sec 0 1.88 MBytes
[ 5] 47.00-48.00 sec 50.0 MBytes 419 Mbits/sec 0 1.88 MBytes
[ 5] 48.00-49.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 49.00-50.00 sec 48.8 MBytes 409 Mbits/sec 0 1.88 MBytes
[ 5] 50.00-51.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 51.00-52.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 52.00-53.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 53.00-54.00 sec 47.5 MBytes 398 Mbits/sec 0 1.88 MBytes
[ 5] 54.00-55.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 55.00-56.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 56.00-57.00 sec 52.5 MBytes 440 Mbits/sec 0 1.88 MBytes
[ 5] 57.00-58.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 58.00-59.00 sec 51.2 MBytes 430 Mbits/sec 0 1.88 MBytes
[ 5] 59.00-60.00 sec 50.0 MBytes 419 Mbits/sec 0 1.88 MBytes
- - - - - - - - - - - - - - - - - - - - - - - - -
[ ID] Interval Transfer Bitrate Retr
[ 5] 0.00-60.00 sec 3.00 GBytes 430 Mbits/sec 154 sender
[ 5] 0.00-60.07 sec 3.00 GBytes 429 Mbits/sec receiver
net2net 适用场景
网点到网点场景,多个客户端都可用通过网关接入 IPSec 的 tunnel 。






















 7011
7011











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








