数据分析
Packet
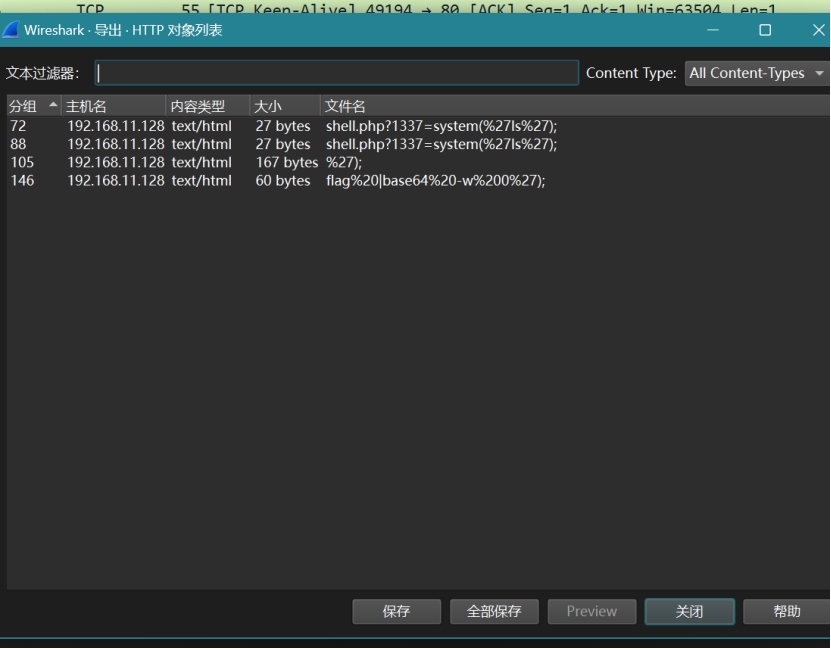
导出flag%20|base64%20-w%200%27);文件
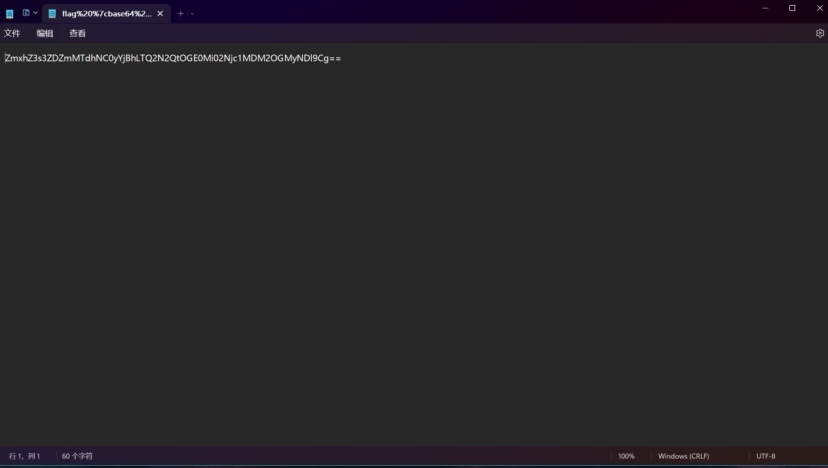
Base64
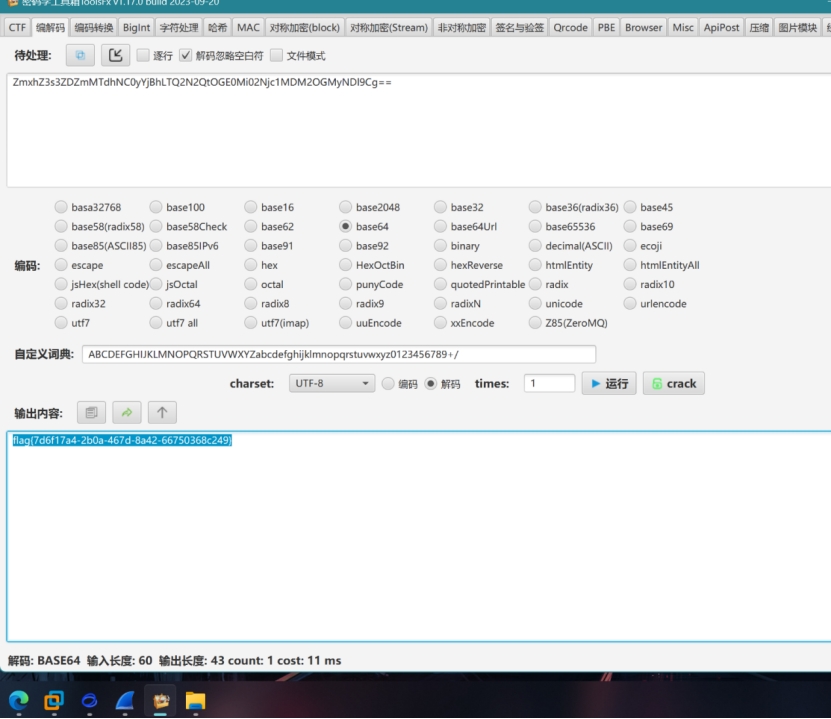
flag{7d6f17a4-2b0a-467d-8a42-66750368c249}
缺失的数据
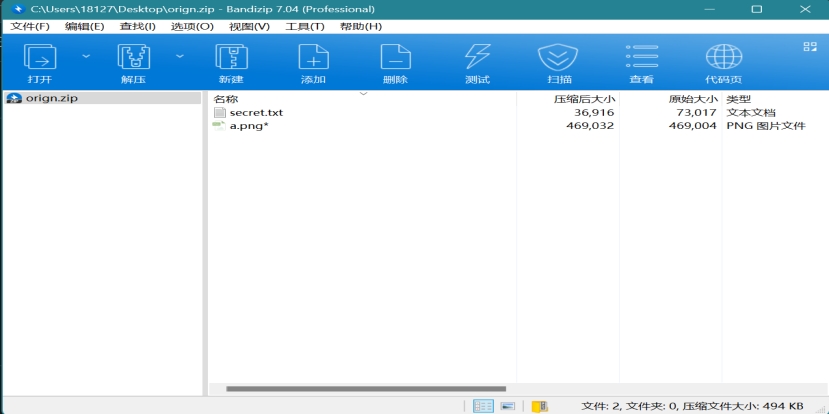
爆破密码 pavilion
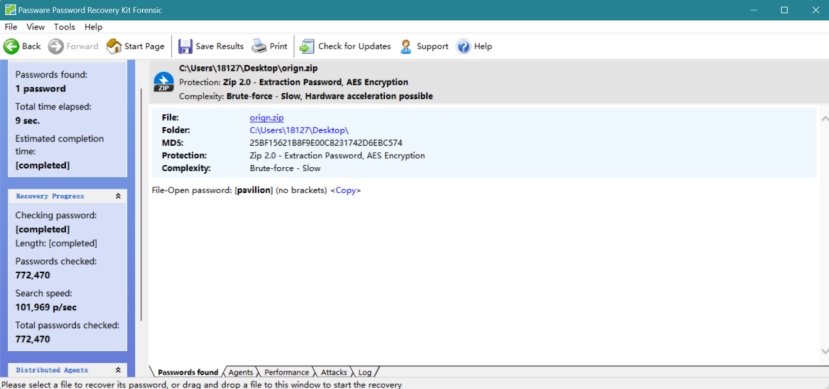
修改脚本
import cv2
import numpy as np
import pywt
class WaterMarkDWT:
def __init__(self, origin: str, watermark: str, key: int, weight: list):
self.key = key
self.img = cv2.imread(origin)
self.mark = cv2.imread(watermark)
self.coef = weight
def arnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for _ in range(self.key):
for i in range(r):
for j in range(c):
x = (i + b * j) % r
y = (a * i + (a * b + 1) * j) % c
p[x, y] = img[i, j]
return p
def deArnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for _ in range(self.key):
for i in range(r):
for j in range(c):
x = ((a * b + 1) * i - b * j) % r
y = (-a * i + j) % c
p[x, y] = img[i, j]
return p
def get(self, size: tuple = (1200, 1200), flag: int = None):
img = cv2.resize(self.img, size)
img1 = cv2.cvtColor(img, cv2.COLOR_RGB2GRAY)
img2 = cv2.cvtColor(self.mark, cv2.COLOR_RGB2GRAY)
# Apply Discrete Wavelet Transform (DWT)
c = pywt.wavedec2(img2, 'db2', level=3)
cl, (cH3, cV3, cD3), (cH2, cV2, cD2), (cH1, cV1, cD1) = c
d = pywt.wavedec2(img1, 'db2', level=3)
dl, (dH3, dV3, dD3), (dH2, cV2, dD2), (cH1, cV1, dD1) = d
a1, a2, a3, a4 = self.coef
# Calculate watermarked coefficients
ca1 = (cl - dl) * a1
ch1 = (cH3 - dH3) * a2
cv1 = (cV3 - dV3) * a3
cd1 = (cD3 - dD3) * a4
# Reconstruct the watermarked image
waterImg = pywt.waverec2([ca1, (ch1, cv1, cd1)], 'db2')
waterImg = np.array(waterImg, np.uint8)
# Apply deArnold transformation
waterImg = self.deArnold(waterImg)
# Optional morphological operations
kernel = np.ones((3, 3), np.uint8)
if flag == 0:
waterImg = cv2.erode(waterImg, kernel)
elif flag == 1:
waterImg = cv2.dilate(waterImg, kernel)
cv2.imwrite('newImg.png', waterImg)
return waterImg
if __name__ == '__main__':
img = 'a.png'
watermark = 'newImg.png' # 这是水印图像的路径
k = 20 # Arnold变换的键
xs = [0.2, 0.2, 0.5, 0.4] # DWT系数权重
W1 = WaterMarkDWT(img, watermark, k, xs) # 初始化WaterMarkDWT
W1.get() # 生成水印图像
跑出结果
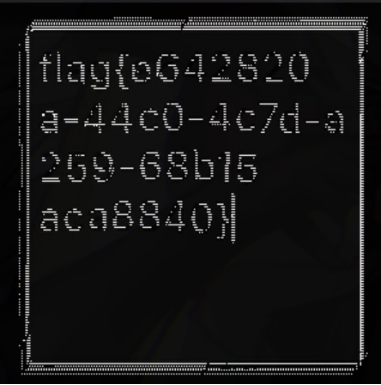
flag{e642820a-44c0-4c7d-a259-68b15aca8840}
密码破解
cc
根据给出,直接厨子解密即可

flag{6500e76e-15fb-42e8-8f29-a309ab73ba38}
Theorem
from Crypto.Util.number import *
from gmpy2 import *
flag = b'xxx'
m = bytes_to_long(flag)
p = getPrime(512)
q = next_prime(p)
e = 65537
n = p * q
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
d1 = d % q
d2 = d % p
c = pow(m, e, n)
print(n)
print(d1)
print(d2)
print(c)
# 94581028682900113123648734937784634645486813867065294159875516514520556881461611966096883566806571691879115766917833117123695776131443081658364855087575006641022211136751071900710589699171982563753011439999297865781908255529833932820965169382130385236359802696280004495552191520878864368741633686036192501791
# 4218387668018915625720266396593862419917073471510522718205354605765842130260156168132376152403329034145938741283222306099114824746204800218811277063324566
# 9600627113582853774131075212313403348273644858279673841760714353580493485117716382652419880115319186763984899736188607228846934836782353387850747253170850
# 36423517465893675519815622861961872192784685202298519340922692662559402449554596309518386263035128551037586034375613936036935256444185038640625700728791201299960866688949056632874866621825012134973285965672502404517179243752689740766636653543223559495428281042737266438408338914031484466542505299050233075829

填上,费马分解(N)

d1.d2然后计算私钥(D)

计算明文

明文(M)转字符
flag{5f00e1b9-2933-42ad-b4e1-069f6aa98e9a}
signature
import hashlib
from Crypto.Util.number import *
from gmpy2 import *
r1,s1,s2=(4690192503304946823926998585663150874421527890534303129755098666293734606680, 111157363347893999914897601390136910031659525525419989250638426589503279490788, 74486305819584508240056247318325239805160339288252987178597122489325719901254)
n= 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
e1=bytes_to_long(hashlib.sha1(b'Hi.').digest())
e2=bytes_to_long(hashlib.sha1(b'hello.').digest())
k=invert(s1-s2,n)*(e1-e2)%n
a=(s1*k-e1)*invert(r1,n)%n
print('flag{' + str(a) + "}")
脚本跑flag
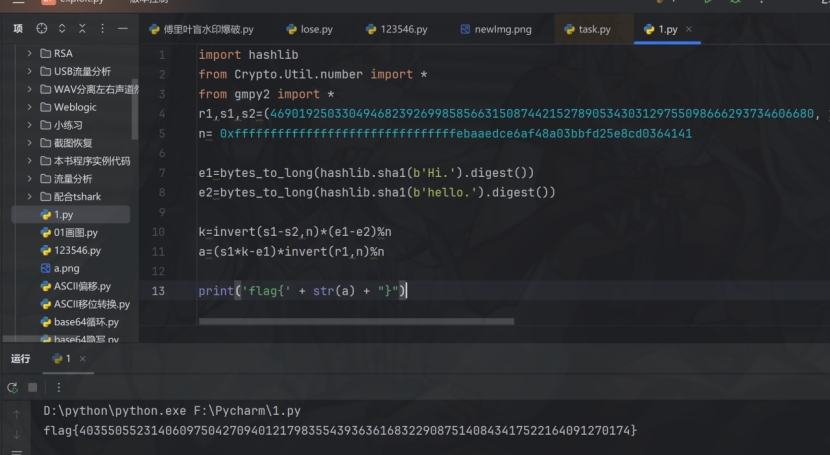
flag{40355055231406097504270940121798355439363616832290875140843417522164091270174}
情报收集
爬虫协议
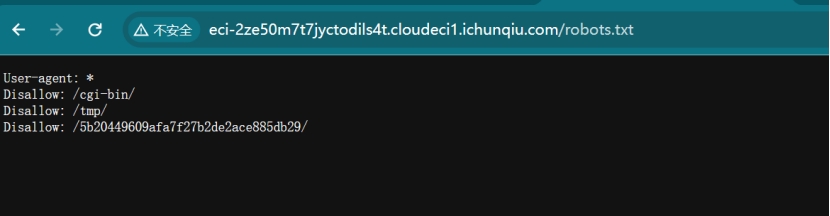
后面加上robots.txt
复制5b20449609afa7f27b2de2ace885db29/,删掉robots.txt,替换
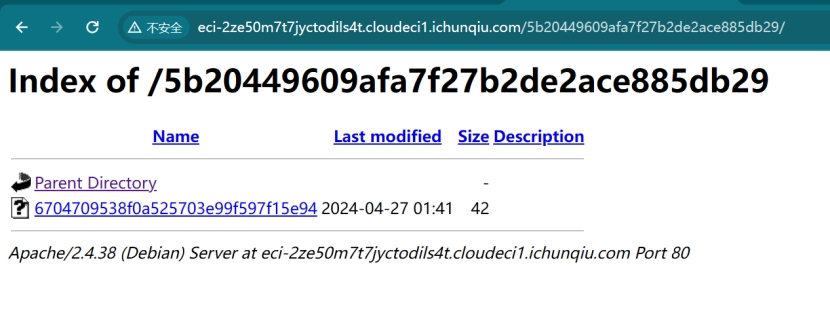
点击6704709538f0a525703e99f597f15e94
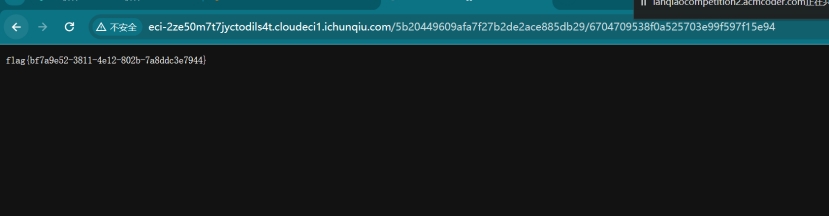
flag{bf7a9e52-3811-4e12-802b-7a8ddc3e7944}
逆向分析
rc4
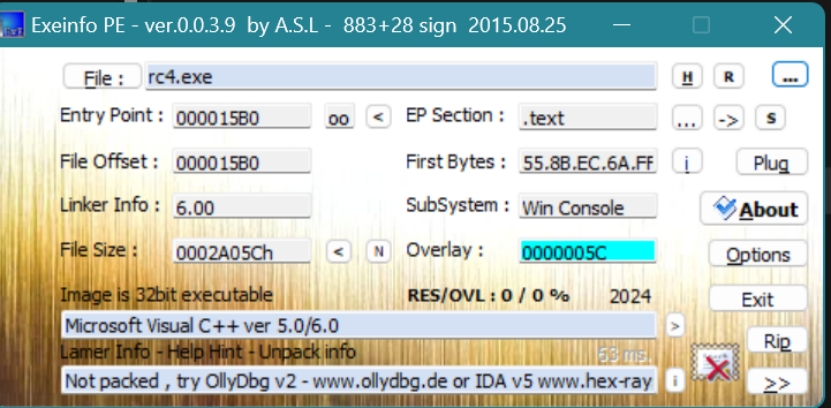
把exe拖到Exeinfo PE里面
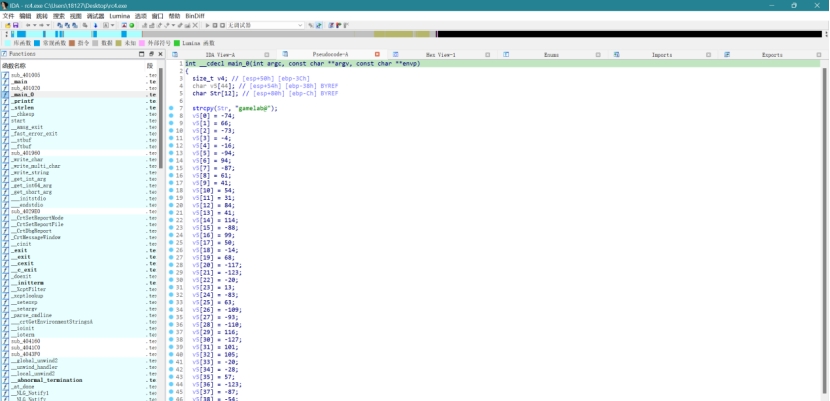
IDA打开文件,找到_main_0函数
把两个C6之间的、数据都复制到记事本里
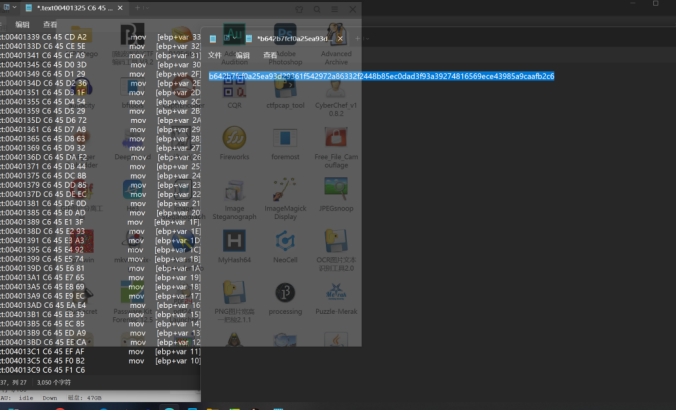
手动敲出A25EA9那一列
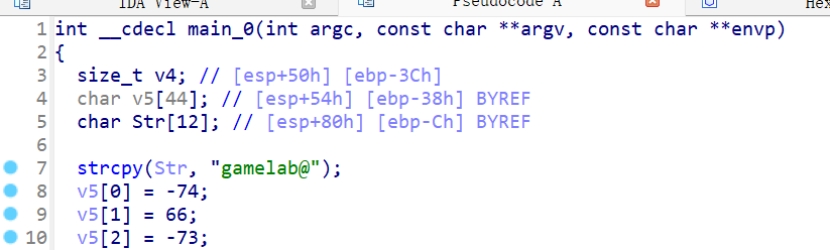
找到密码gamelab@
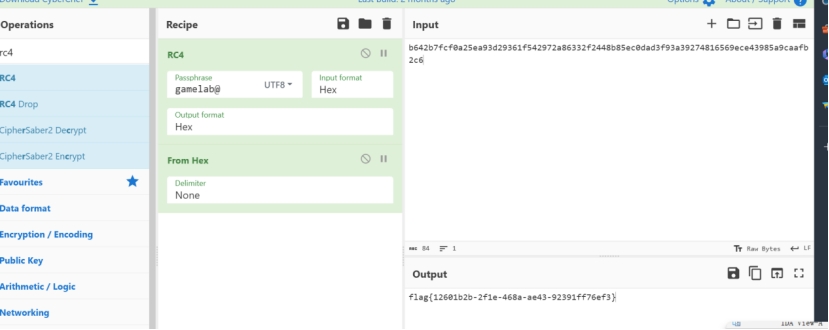
厨子rc4嗦了
flag{12601b2b-2f1e-468a-ae43-92391ff76ef3}






















 750
750











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








