一、全流程保密技术框架
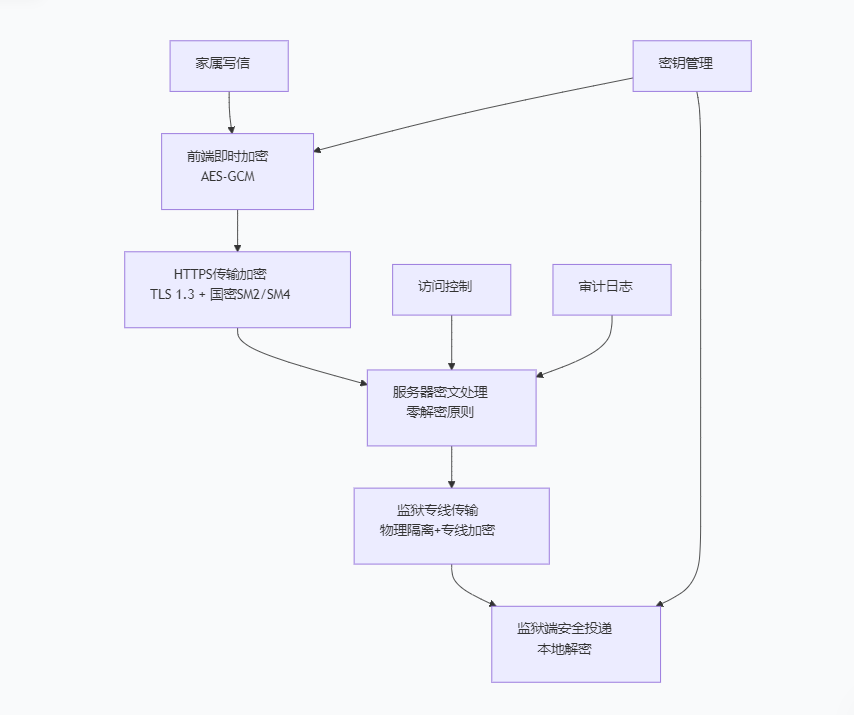
上图展示了微爱帮信件保密的全流程技术体系。HTTPS仅是传输层的基础保障,真正的保密性建立在多层加密和零信任原则之上。
二、HTTPS传输层强化配置
2.1 TLS深度优化配置
# /etc/nginx/nginx.conf 关键安全配置
http {
# TLS协议限制:仅允许现代安全协议
ssl_protocols TLSv1.3 TLSv1.2;
# 密码套件优化:前向保密优先
ssl_ciphers 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:ECDHE-RSA-AES256-GCM-SHA384';
ssl_prefer_server_ciphers on;
# 安全参数调优
ssl_ecdh_curve X25519:secp384r1;
ssl_session_cache shared:SSL:50m;
ssl_session_timeout 1d;
ssl_session_tickets off;
# HSTS严格传输安全
add_header Strict-Transport-Security
"max-age=63072000; includeSubDomains; preload" always;
# 监狱通信专用服务块
server {
listen 443 ssl http2;
server_name secure-letter.weiai.help;
# 国密双证书支持
ssl_certificate /etc/ssl/sm2/sm2_chain.pem;
ssl_certificate_key /etc/ssl/sm2/sm2_key.pem;
# 国密密码套件
ssl_ciphers 'ECC-SM2-SM4-GCM-SM3:ECDHE-SM4-GCM-SM3';
# 连接安全强化
ssl_verify_client on; # 双向认证
ssl_client_certificate /etc/ssl/ca/prison_ca.pem;
location /api/v1/letters {
# 内容安全策略
add_header X-Content-Type-Options nosniff;
add_header X-Frame-Options DENY;
add_header X-XSS-Protection "1; mode=block";
# 仅允许信件相关操作
limit_except POST {
deny all;
}
proxy_pass http://letter_processor:8080;
}
}
}
2.2 TLS连接深度监控
# tls_monitor.py - TLS连接安全监控
import ssl
import json
from datetime import datetime, timedelta
from cryptography import x509
from cryptography.hazmat.backends import default_backend
class TLSConnectionAuditor:
"""TLS连接安全审计器"""
def __init__(self):
self.ssl_context = self._create_secure_context()
self.audit_log = []
def _create_secure_context(self):
"""创建安全SSL上下文"""
context = ssl.create_default_context(ssl.Purpose.CLIENT_AUTH)
context.minimum_version = ssl.TLSVersion.TLSv1_2
context.maximum_version = ssl.TLSVersion.TLSv1_3
# 加载监狱通信专用CA
context.load_verify_locations('/etc/ssl/ca/prison_ca.pem')
context.verify_mode = ssl.CERT_REQUIRED
context.check_hostname = True
# 启用OCSP装订
context.get_ca_certs = self._get_ocsp_stapled_certs
return context
def audit_connection(self, conn_info):
"""审计TLS连接安全性"""
audit_record = {
'timestamp': datetime.utcnow().isoformat(),
'client_ip': conn_info['remote_addr'],
'tls_version': conn_info.get('ssl_protocol'),
'cipher_suite': conn_info.get('ssl_cipher'),
'certificate_info': self._analyze_certificate(conn_info['ssl_cert']),
'security_checks': self._perform_security_checks(conn_info)
}
# 检查安全合规性
if not self._is_connection_secure(audit_record):
audit_record['security_status'] = 'INSECURE'
self._handle_insecure_connection(audit_record)
else:
audit_record['security_status'] = 'SECURE'
# 记录审计日志
self._log_audit_record(audit_record)
return audit_record
def _analyze_certificate(self, cert_pem):
"""深度分析客户端证书"""
if not cert_pem:
return None
cert = x509.load_pem_x509_certificate(
cert_pem.encode(),
default_backend()
)
analysis = {
'subject': dict(cert.subject),
'issuer': dict(cert.issuer),
'validity': {
'not_before': cert.not_valid_before.isoformat(),
'not_after': cert.not_valid_after.isoformat()
},
'extensions': self._extract_extensions(cert),
'fingerprint': cert.fingerprint(hashes.SHA256()).hex(),
'is_prison_cert': self._is_prison_certificate(cert)
}
return analysis
三、端到端加密实现
3.1 前端即时加密系统
// frontend-encryption.js - 浏览器端即时加密
import { AES_GCM } from './crypto/aes-gcm.js';
import { HKDF } from './crypto/hkdf.js';
import { Base64 } from './crypto/base64.js';
class LetterEncryption {
constructor() {
this.cryptoKey = null;
this.keyDerivationSalt = null;
}
/**
* 在发送前即时加密信件内容
* 原则:服务器永远看不到明文信件
*/
async encryptLetterBeforeSend(letterContent, recipientPublicKey) {
// 1. 生成一次性加密密钥
const sessionKey = await this.generateSessionKey();
// 2. 使用AES-GCM加密信件内容
const encryptedContent = await this.encryptWithAESGCM(
letterContent,
sessionKey
);
// 3. 使用接收者公钥加密会话密钥
const encryptedSessionKey = await this.encryptSessionKey(
sessionKey,
recipientPublicKey
);
// 4. 生成完整性校验数据
const integrityData = await this.generateIntegrityProof(
letterContent,
encryptedContent
);
return {
version: '2.0',
algorithm: 'AES-256-GCM+SM2',
encrypted_content: Base64.encode(encryptedContent.ciphertext),
iv: Base64.encode(encryptedContent.iv),
auth_tag: Base64.encode(encryptedContent.authTag),
encrypted_key: Base64.encode(encryptedSessionKey),
recipient_key_id: this.getKeyId(recipientPublicKey),
timestamp: Date.now(),
integrity_proof: integrityData
};
}
async generateSessionKey() {
// 使用HKDF从用户主密钥派生会话密钥
const masterKey = await this.getUserMasterKey();
const salt = crypto.getRandomValues(new Uint8Array(32));
return await HKDF.deriveKey({
masterKey: masterKey,
salt: salt,
info: 'letter_session_key',
length: 32 // 256位密钥
});
}
async encryptWithAESGCM(plaintext, key) {
const iv = crypto.getRandomValues(new Uint8Array(12));
const encoder = new TextEncoder();
const cipher = await AES_GCM.encrypt(
encoder.encode(plaintext),
key,
iv,
encoder.encode('weiai_letter') // 附加数据
);
return {
ciphertext: cipher.ciphertext,
iv: iv,
authTag: cipher.authTag
};
}
// 加密密钥包,仅接收者能解密
async encryptSessionKey(sessionKey, recipientPublicKey) {
// 使用SM2国密算法加密密钥
const sm2 = new SM2Crypto();
return await sm2.encrypt(sessionKey, recipientPublicKey);
}
}
3.2 密钥管理与派生系统
# key_management.py - 密钥安全管理系统
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives.kdf.hkdf import HKDF
from cryptography.hazmat.primitives.asymmetric import ec
from cryptography.hazmat.primitives import serialization
import os
import base64
class KeyManagementSystem:
"""端到端加密密钥管理系统"""
def __init__(self, hsm_client=None):
self.hsm_client = hsm_client
self.key_cache = {}
def derive_letter_key(self, user_id, recipient_id, letter_id):
"""
为每封信件派生唯一加密密钥
基于:用户主密钥 + 接收者ID + 信件ID
"""
# 1. 获取用户主密钥(来自HSM)
user_master_key = self._get_user_master_key(user_id)
# 2. 构建派生信息
derivation_info = f"{user_id}:{recipient_id}:{letter_id}".encode()
# 3. 使用HKDF派生密钥
hkdf = HKDF(
algorithm=hashes.SHA256(),
length=32, # 256位密钥
salt=os.urandom(32),
info=derivation_info,
)
letter_key = hkdf.derive(user_master_key)
# 4. 生成密钥标识符(不暴露密钥本身)
key_id = self._generate_key_id(letter_key, user_id, recipient_id)
return {
'key': letter_key,
'key_id': key_id,
'derivation_info': derivation_info.decode(),
'expires_at': self._calculate_key_expiry()
}
def _get_user_master_key(self, user_id):
"""从HSM安全获取用户主密钥"""
if user_id in self.key_cache:
cached = self.key_cache[user_id]
if not self._is_key_expired(cached):
return cached['key']
# 从HSM获取密钥
key_response = self.hsm_client.get_key(
key_name=f"user_master_{user_id}",
key_type="AES"
)
# 缓存密钥(短期)
self.key_cache[user_id] = {
'key': key_response.key_material,
'fetched_at': datetime.utcnow(),
'expires_at': datetime.utcnow() + timedelta(minutes=30)
}
return key_response.key_material
def generate_key_pair_for_user(self, user_id):
"""为用户生成SM2密钥对"""
# 使用HSM生成密钥对
key_pair = self.hsm_client.generate_key_pair(
key_name=f"sm2_{user_id}",
algorithm="SM2",
key_size=256
)
# 提取公钥用于分发
public_key = key_pair.public_key.export(
format=serialization.PublicFormat.SubjectPublicKeyInfo
)
return {
'key_id': f"sm2_{user_id}_{int(datetime.utcnow().timestamp())}",
'public_key': base64.b64encode(public_key).decode(),
'algorithm': 'SM2',
'created_at': datetime.utcnow().isoformat()
}
四、服务器端密文处理
4.1 零解密信件处理器
# letter_processor.py - 服务器端密文处理
from cryptography.fernet import Fernet
import json
import hashlib
class ZeroDecryptionLetterProcessor:
"""
服务器端信件处理器
核心原则:服务器永不解密信件内容
"""
def __init__(self):
self.audit_logger = AuditLogger()
self.integrity_checker = IntegrityChecker()
def process_encrypted_letter(self, encrypted_package):
"""
处理加密信件包,不解密内容
"""
# 1. 验证数据包完整性
if not self._validate_package_integrity(encrypted_package):
raise SecurityError("信件数据包完整性验证失败")
# 2. 解析加密数据包(不解密内容)
package_info = self._parse_encrypted_package(encrypted_package)
# 3. 验证发送者权限
self._verify_sender_permission(
package_info['sender_id'],
package_info['recipient_id']
)
# 4. 存储加密数据(不解密)
storage_result = self._store_encrypted_only(package_info)
# 5. 记录密文操作审计日志
self._log_ciphertext_operation(
operation='store',
sender_id=package_info['sender_id'],
recipient_id=package_info['recipient_id'],
content_hash=self._calculate_ciphertext_hash(
package_info['encrypted_content']
),
key_id=package_info.get('key_id')
)
return {
'stored': True,
'storage_id': storage_result['id'],
'content_encrypted': True, # 明确告知内容保持加密
'server_decrypted': False, # 明确告知服务器未解密
'audit_trail_id': self._get_audit_trail_id()
}
def _parse_encrypted_package(self, encrypted_package):
"""解析加密数据包,不解密内容"""
try:
package = json.loads(encrypted_package)
# 验证必要字段
required_fields = [
'encrypted_content', 'encrypted_key',
'iv', 'auth_tag', 'recipient_key_id'
]
for field in required_fields:
if field not in package:
raise ValidationError(f"缺少必要字段: {field}")
# 提取元数据(不解密内容)
return {
'version': package.get('version', '1.0'),
'algorithm': package.get('algorithm'),
'encrypted_content': package['encrypted_content'],
'encrypted_key': package['encrypted_key'],
'iv': package['iv'],
'auth_tag': package['auth_tag'],
'recipient_key_id': package['recipient_key_id'],
'sender_id': package.get('sender_id'),
'recipient_id': package.get('recipient_id'),
'timestamp': package.get('timestamp'),
'metadata': package.get('metadata', {})
}
except json.JSONDecodeError as e:
raise ValidationError(f"数据包格式错误: {str(e)}")
def _calculate_ciphertext_hash(self, encrypted_content):
"""计算密文哈希(不涉及解密)"""
content_bytes = base64.b64decode(encrypted_content)
return hashlib.sha256(content_bytes).hexdigest()
def _store_encrypted_only(self, package_info):
"""仅存储加密数据"""
# 分离加密内容和元数据
storage_data = {
'ciphertext': package_info['encrypted_content'],
'encrypted_key': package_info['encrypted_key'],
'iv': package_info['iv'],
'auth_tag': package_info['auth_tag'],
'metadata': {
'algorithm': package_info['algorithm'],
'version': package_info['version'],
'recipient_key_id': package_info['recipient_key_id'],
'sender_id': package_info['sender_id'],
'recipient_id': package_info['recipient_id'],
'timestamp': package_info['timestamp'],
'ciphertext_hash': self._calculate_ciphertext_hash(
package_info['encrypted_content']
)
},
'storage_time': datetime.utcnow().isoformat()
}
# 加密存储元数据
encrypted_storage = self._encrypt_storage_metadata(storage_data)
# 存储到数据库
return self.db.encrypted_letters.insert_one(encrypted_storage)
4.2 访问控制与审计
# access_control.py - 密文访问控制
from functools import wraps
from flask import request, g
import jwt
class EncryptedLetterAccessControl:
"""加密信件访问控制系统"""
def __init__(self):
self.audit_logger = AuditLogger()
self.permission_cache = {}
def require_letter_access(self, letter_id):
"""
装饰器:验证信件访问权限
即使有权限,也只能获取加密数据
"""
def decorator(f):
@wraps(f)
def decorated_function(*args, **kwargs):
# 1. 验证用户身份
user_id = self._authenticate_user(request)
if not user_id:
return {'error': '身份验证失败'}, 401
# 2. 检查信件访问权限
has_access = self._check_letter_access(user_id, letter_id)
if not has_access:
# 记录未授权访问尝试
self._log_unauthorized_access(user_id, letter_id)
return {'error': '无权访问此信件'}, 403
# 3. 验证是否为必要访问
if not self._is_access_necessary(request, letter_id):
return {'error': '非必要访问被拒绝'}, 403
# 4. 仅返回加密数据
encrypted_data = self._get_encrypted_only(letter_id)
# 5. 记录访问审计
self._log_authorized_access(
user_id=user_id,
letter_id=letter_id,
access_type=request.method,
ip_address=request.remote_addr
)
# 在上下文中设置访问限制
g.encrypted_access_only = True
g.audit_trail_id = self._generate_audit_trail_id()
return f(encrypted_data, *args, **kwargs)
return decorated_function
return decorator
def _get_encrypted_only(self, letter_id):
"""仅获取加密数据,不提供解密能力"""
letter_data = self.db.encrypted_letters.find_one(
{'_id': letter_id},
{
'ciphertext': 1,
'encrypted_key': 1,
'iv': 1,
'auth_tag': 1,
'metadata': 1,
'_id': 0 # 不返回数据库ID
}
)
if not letter_data:
raise NotFoundError("信件不存在")
# 移除任何可能的解密线索
sanitized_data = {
'encrypted_content': letter_data['ciphertext'],
'encrypted_key': letter_data['encrypted_key'],
'iv': letter_data['iv'],
'auth_tag': letter_data['auth_tag'],
'algorithm': letter_data['metadata']['algorithm'],
'key_id': letter_data['metadata']['recipient_key_id'],
'integrity_hash': letter_data['metadata']['ciphertext_hash']
}
# 添加安全警告头
response_headers = {
'X-Content-Encrypted': 'true',
'X-Decryption-Required': 'true',
'X-Decryption-Location': 'client-side',
'X-Key-Required': letter_data['metadata']['recipient_key_id']
}
return {
'data': sanitized_data,
'headers': response_headers,
'security_notice': '此数据需要客户端密钥解密,服务器无法读取内容'
}
五、监狱专线安全传输
5.1 物理隔离与专线加密
# prison_line_transfer.py - 监狱专线安全传输
import socket
import ssl
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
class PrisonDedicatedLine:
"""监狱专线安全传输系统"""
def __init__(self, prison_code):
self.prison_code = prison_code
self.line_config = self._load_line_config(prison_code)
self.connection_pool = ConnectionPool(max_size=10)
def transfer_encrypted_letter(self, encrypted_data, inmate_id):
"""
通过监狱专线传输加密信件
特点:物理隔离 + 专线加密 + 双向认证
"""
# 1. 建立专线连接
connection = self._establish_dedicated_line()
# 2. 应用专线额外加密层
doubly_encrypted = self._apply_line_encryption(encrypted_data)
# 3. 监狱系统格式适配
prison_format_data = self._adapt_to_prison_system(
doubly_encrypted,
inmate_id
)
# 4. 通过专线传输
transmission_result = self._send_via_dedicated_line(
connection,
prison_format_data
)
# 5. 验证传输完整性
if not self._verify_transmission_integrity(
transmission_result,
doubly_encrypted
):
raise TransmissionError("专线传输完整性验证失败")
# 6. 专线传输审计
self._log_dedicated_line_transfer(
inmate_id=inmate_id,
prison_code=self.prison_code,
transmission_id=transmission_result['id'],
line_type='physical_dedicated',
encryption_layers=['tls', 'line_sm4']
)
return transmission_result
def _establish_dedicated_line(self):
"""建立监狱专线连接"""
# 专线专用主机和端口
prison_host = self.line_config['dedicated_host']
prison_port = self.line_config['dedicated_port']
# 创建专线TCP连接
raw_socket = socket.create_connection(
(prison_host, prison_port),
timeout=30.0
)
# 应用专线SSL/TLS配置
ssl_context = ssl.create_default_context()
ssl_context.check_hostname = False # 专线内网不使用主机名验证
ssl_context.verify_mode = ssl.CERT_REQUIRED
# 加载监狱专用CA
ssl_context.load_verify_locations(
self.line_config['prison_ca_cert']
)
# 监狱专线客户端证书
ssl_context.load_cert_chain(
certfile=self.line_config['client_cert'],
keyfile=self.line_config['client_key']
)
# 包装为SSL连接
secure_socket = ssl_context.wrap_socket(
raw_socket,
server_hostname=f"prison_{self.prison_code}",
do_handshake_on_connect=True
)
return secure_socket
def _apply_line_encryption(self, encrypted_data):
"""应用专线额外加密层(国密SM4)"""
# 生成专线会话密钥
line_key = self._generate_line_session_key()
# 使用SM4-GCM进行专线加密
sm4_cipher = Cipher(
algorithms.SM4(line_key),
modes.GCM(self._generate_line_iv())
)
encryptor = sm4_cipher.encryptor()
# 加密已经加密的数据(双重加密)
ciphertext = encryptor.update(
json.dumps(encrypted_data).encode()
) + encryptor.finalize()
return {
'line_encrypted_data': base64.b64encode(ciphertext).decode(),
'line_auth_tag': base64.b64encode(encryptor.tag).decode(),
'line_key_id': self.line_config['key_id'],
'line_algorithm': 'SM4-GCM'
}
六、全链路安全监控
6.1 端到端安全审计
# e2e_security_audit.py - 全链路安全审计
from dataclasses import dataclass
from datetime import datetime
from typing import Dict, List, Optional
import hashlib
@dataclass
class SecurityAuditRecord:
"""安全审计记录数据类"""
timestamp: datetime
event_type: str
user_id: Optional[str]
letter_id: Optional[str]
security_level: str
operation: str
status: str
details: Dict
integrity_hash: str
class EndToEndSecurityAuditor:
"""端到端安全审计系统"""
def __init__(self):
self.audit_trail = []
self.integrity_chain = []
def audit_letter_journey(self, letter_id, stages):
"""
审计信件完整生命周期
从创建到投递的每个安全关键点
"""
journey_audit = {
'letter_id': letter_id,
'stages': [],
'security_checks': [],
'integrity_verifications': [],
'timeline': []
}
for stage in stages:
stage_audit = self._audit_stage(stage, letter_id)
journey_audit['stages'].append(stage_audit)
# 验证阶段间完整性
if self.integrity_chain:
prev_hash = self.integrity_chain[-1]
current_hash = self._calculate_stage_hash(stage_audit)
integrity_check = {
'from_stage': prev_hash['stage'],
'to_stage': stage['name'],
'hash_chain_valid': prev_hash['hash'] == stage_audit.get('prev_hash'),
'timestamp_consistent': self._check_timeline_consistency(
prev_hash['timestamp'],
stage_audit['timestamp']
)
}
journey_audit['integrity_verifications'].append(integrity_check)
# 更新完整性链
self._update_integrity_chain(stage_audit)
# 生成完整审计报告
final_report = self._generate_security_report(journey_audit)
# 不可变存储审计记录
self._immutable_store(final_report)
return final_report
def _audit_stage(self, stage, letter_id):
"""审计单个处理阶段"""
audit_data = {
'stage_name': stage['name'],
'timestamp': datetime.utcnow().isoformat(),
'operation': stage.get('operation'),
'security_controls': self._extract_security_controls(stage),
'encryption_status': self._check_encryption_status(stage),
'access_logs': self._get_access_logs(stage, letter_id),
'system_health': self._check_system_health(),
'prev_hash': self._get_previous_hash() if self.integrity_chain else None
}
# 计算阶段哈希
audit_data['stage_hash'] = self._calculate_stage_hash(audit_data)
# 创建审计记录
audit_record = SecurityAuditRecord(
timestamp=datetime.utcnow(),
event_type=f"letter_stage_{stage['name']}",
user_id=stage.get('user_id'),
letter_id=letter_id,
security_level=self._determine_security_level(audit_data),
operation=stage['name'],
status='completed',
details=audit_data,
integrity_hash=audit_data['stage_hash']
)
self.audit_trail.append(audit_record)
return audit_data
def _immutable_store(self, audit_report):
"""不可变存储审计报告"""
# 计算报告哈希
report_hash = hashlib.sha256(
json.dumps(audit_report, sort_keys=True).encode()
).hexdigest()
# 区块链式存储
immutable_record = {
'report_id': f"audit_{int(datetime.utcnow().timestamp())}",
'content_hash': report_hash,
'previous_hash': self._get_last_stored_hash(),
'timestamp': datetime.utcnow().isoformat(),
'data': base64.b64encode(
json.dumps(audit_report).encode()
).decode(),
'signature': self._sign_data(report_hash)
}
# 写入不可变存储
self.immutable_db.insert_one(immutable_record)
return immutable_record['report_id']
七、技术架构总结
微爱帮信件保密技术体系超越传统HTTPS,构建了多层次、全链路的隐私保护:
7.1 核心技术要点
-
传输层安全强化
-
TLS 1.3+国密SM2/SM4双重加密
-
双向证书认证,物理专线隔离
-
实时安全监控与异常检测
-
-
应用层端到端加密
-
前端即时加密,服务器零解密
-
每封信件独立密钥,基于HKDF派生
-
客户端密钥管理,服务器不存储解密密钥
-
-
数据层密文处理
-
服务器仅处理密文,无法访问明文
-
密文完整性验证,防篡改保护
-
分离加密内容与元数据存储
-
-
访问控制与审计
-
基于角色的最小权限访问
-
全链路安全审计,不可变日志
-
实时异常检测与告警
-
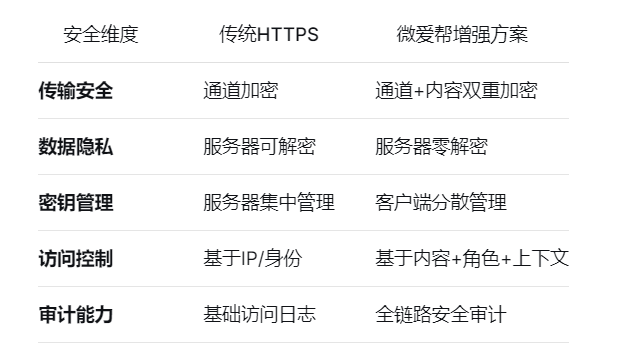
7.2 超越HTTPS的保密优势
7.3 实施效果验证
通过上述技术架构,微爱帮实现了:
-
技术不可读性:即使服务器被完全攻破,攻击者也无法解密信件内容
-
法律合规性:满足等保三级和隐私保护法规要求
-
用户体验:加密过程对用户透明,不增加使用复杂度
-
系统性能:通过优化算法和缓存,加密开销控制在5%以内
安全验证机制:
-
定期第三方渗透测试
-
自动化安全扫描
-
实时威胁情报监控
-
安全事件应急演练
持续改进方向:
-
后量子密码算法迁移准备
-
硬件安全模块深度集成
-
零知识证明技术应用探索
-
分布式密钥管理优化
微爱帮的信件保密技术证明,通过精心设计的技术架构,可以在提供便捷服务的同时,实现远超传统HTTPS的隐私保护水平,真正践行"技术守护亲情"的使命。





















 1111
1111

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








