One of the biggest threats to modern online banking is a type of vulnerability called race conditions.
现代在线银行业务的最大威胁之一是一种称为竞赛条件的漏洞。
These vulnerabilities stem from simple programming mistakes that developers commonly make. And these mistakes have proved costly: race conditions have been used by hackers to steal money from online banks, stock brokerages, and cryptocurrency exchanges. (They have also been used by hackers to drink unlimited coffee at Starbucks, as you’ll soon see in this post!)
这些漏洞源于开发人员通常会犯的简单编程错误。 而且这些错误已被证明代价高昂:黑客利用种族条件从网上银行,股票经纪人和加密货币交易所偷钱。 (黑客还使用它们在星巴克喝无限量的咖啡,正如您将在本文中很快看到的那样!)
Today, let’s talk about how and why these vulnerabilities happen, how attackers have exploited it, and how to prevent it in your own applications.
今天,让我们讨论一下这些漏洞的发生方式和原因,攻击者如何利用它以及如何在您自己的应用程序中进行预防。
速成课程并发 (Crash Course Concurrency)
In computer science, concurrency is the ability for different parts of a program to be executed simultaneously without affecting the final outcome of the computation.
在计算机科学中,并发是指可以在不影响计算最终结果的情况下同时执行程序的不同部分的功能。
When a program is developed with concurrency in mind, it can take full advantage of modern multithreading and multiprocessing systems, and thus drastically improve its performance.
在考虑并发性的情况下开发程序时,它可以充分利用现代的多线程和多处理系统,从而极大地提高其性能。
Multithreading is the ability of a CPU to provide multiple threads of execution. These threads don’t all execute at the same time but take turns using the CPU’s computational power. With multithreading, other threads can continue taking advantage of the unused computing resources while they are idle. (For example, when the original thread is suspended while waiting for input or output to complete.)
多线程是CPU提供多个执行线程的能力。 这些线程并非全部同时执行,而是使用CPU的计算能力轮流执行。 使用多线程,其他线程可以在空闲时继续利用未使用的计算资源。 (例如,当原始线程在等待输入或输出完成时被挂起时。)
While multiprocessing refers to the usage of multiple CPUs for computation at the same time.
多处理是指同时使用多个CPU进行计算。
Arranging the sequence of execution of multiple threads is called scheduling. There are many different scheduling algorithms in use, each optimized for different performance priorities.
安排多个线程的执行顺序称为调度。 使用了许多不同的调度算法,每种算法都针对不同的性能优先级进行了优化。
什么是比赛条件? (What is a Race Condition?)
In computing, a race condition happens when two sections of code that are designed to be executed in a sequence were executed out of sequence.
在计算中,争用条件发生在设计为按顺序执行的两个代码段不按顺序执行时。
Since the scheduling algorithm can swap between the execution of two threads at any time, you can’t predict the sequence in which the threads execute each action.
由于调度算法可以随时在两个线程的执行之间进行交换,因此您无法预测线程执行每个动作的顺序。
For example, let’s say that two concurrent threads of execution are each trying to increase the value of a global variable by 1. So in the end, the global variable will have the value of 2. (The example is taken from the Wikipedia page: https://en.wikipedia.org/wiki/Race_condition)
例如,假设两个并发的执行线程都试图将全局变量的值增加1。因此,最后,全局变量的值将为2。(该示例摘自Wikipedia页面: https://zh.wikipedia.org/wiki/种族条件 )
Ideally, the threads would be executed as such:
理想情况下,线程将按以下方式执行:
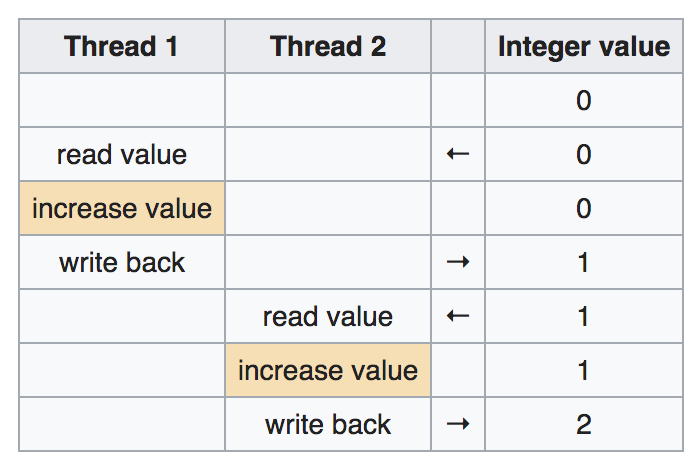
But, if the two threads are run simultaneously, without resource locks (a mechanism that blocks other threads from operating on the same resource) or synchronization (a mechanism that ensures that threads that utilize the same resources so not execute simultaneously), the execution could be scheduled like this:
但是,如果两个线程同时运行,而没有资源锁 (一种阻止其他线程在同一资源上运行的机制)或同步 (一种确保使用相同资源的线程不会同时执行的机制),则执行可能像这样预定:
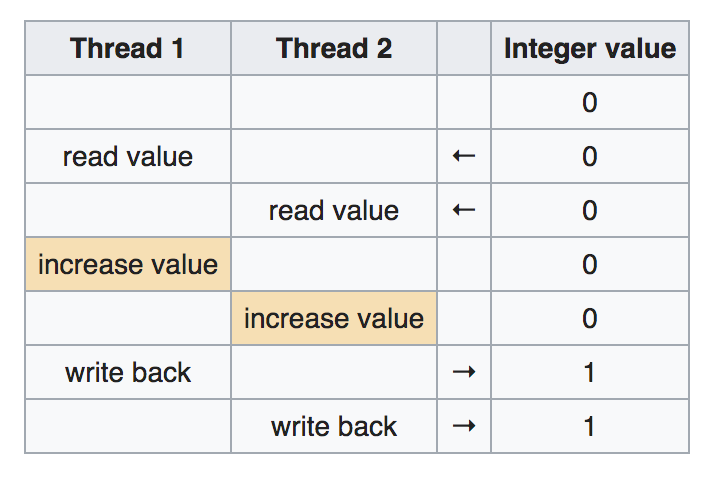
In this case, the final value of the global variable becomes 1, which is incorrect. (The expected value is 2.)
在这种情况下,全局变量的最终值为1,这是不正确的。 (预期值为2。)
This happens because the outcome of the execution of one thread depends on the outcome of another thread. When the two threads are executed simultaneously, unexpected outcomes can occur.
发生这种情况是因为一个线程的执行结果取决于另一个线程的结果。 当两个线程同时执行时,可能会发生意外结果。
什么是竞争条件漏洞? (What is a Race Condition Vulnerability?)
A race condition becomes a vulnerability when it affects a security control mechanism. Hackers can then induce a situation in which a sensitive action is executed before a security control is complete. For this reason, race condition vulnerabilities are also referred to as Time of Check/Time of Use vulnerabilities.
当竞争条件影响安全控制机制时,它就成为一个漏洞。 然后,黑客可能会导致在安全控制完成之前执行敏感操作的情况。 因此,竞争条件漏洞也称为检查时间/使用时间漏洞 。
Imagine if the two threads of the above example are executing something a little more sensitive: the transferring of money between bank accounts. The application would have to perform three subtasks to transfer the money correctly:
想象一下,如果上面的示例中的两个线程正在执行一些更敏感的操作:在银行帐户之间转移资金。 该应用程序将必须执行三个子任务才能正确转账:
- Check if account A has enough balance. 检查帐户A是否有足够的余额。
- Add the money to account B. 将钱添加到帐户B中。
- Deduct the money from account A. 从帐户A中扣除这笔钱。
Let’s say that you own two bank accounts, account A and account B. You have $500 in account A and $0 in account B. Now, you initiate two money transfers of $500 from account A to account B.
假设您拥有两个银行帐户, 帐户A和帐户B。 您在帐户A中有$ 500,在帐户B中有$ 0。现在,您要进行两次从帐户A到帐户B的$ 500汇款。
Ideally, when two money transfer requests were initiated, the program should behave like this.
理想情况下,当启动两个汇款请求时,程序应具有以下行为。
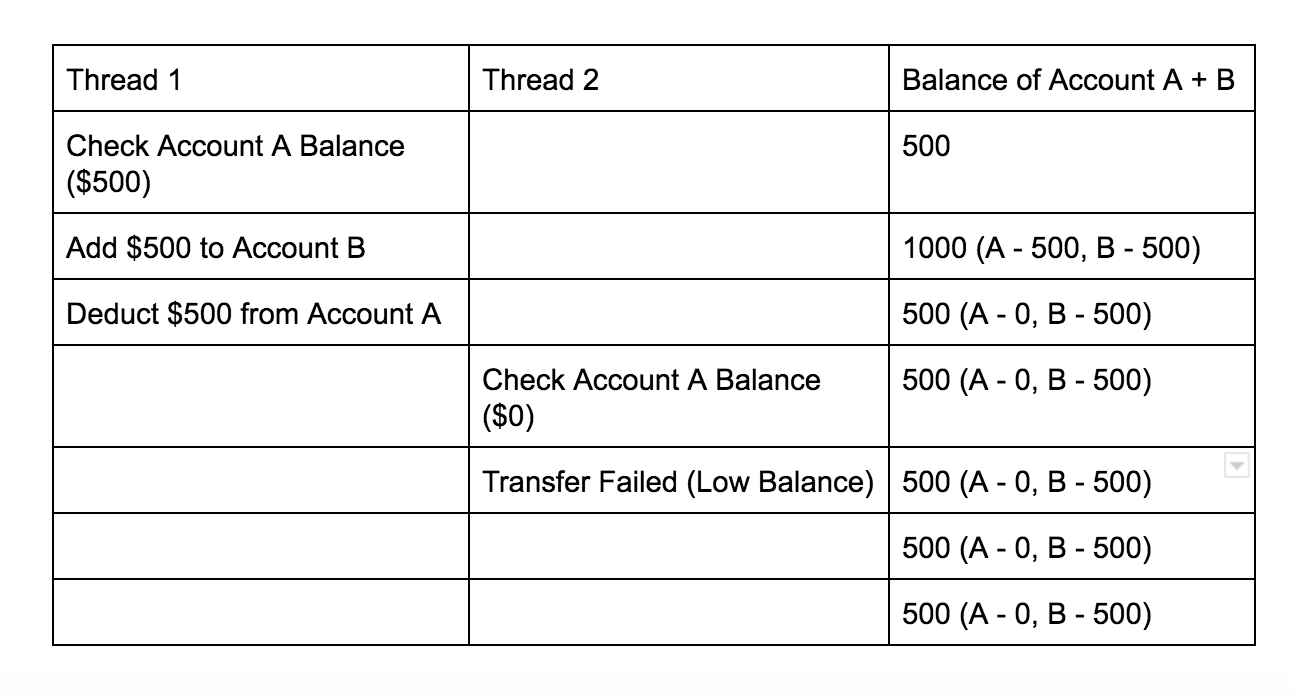
But if you can send the two request simultaneously, you might be able to induce a situation in which the execution of the threads become like this:
但是,如果您可以同时发送两个请求,则可能会导致线程执行如下所示的情况:
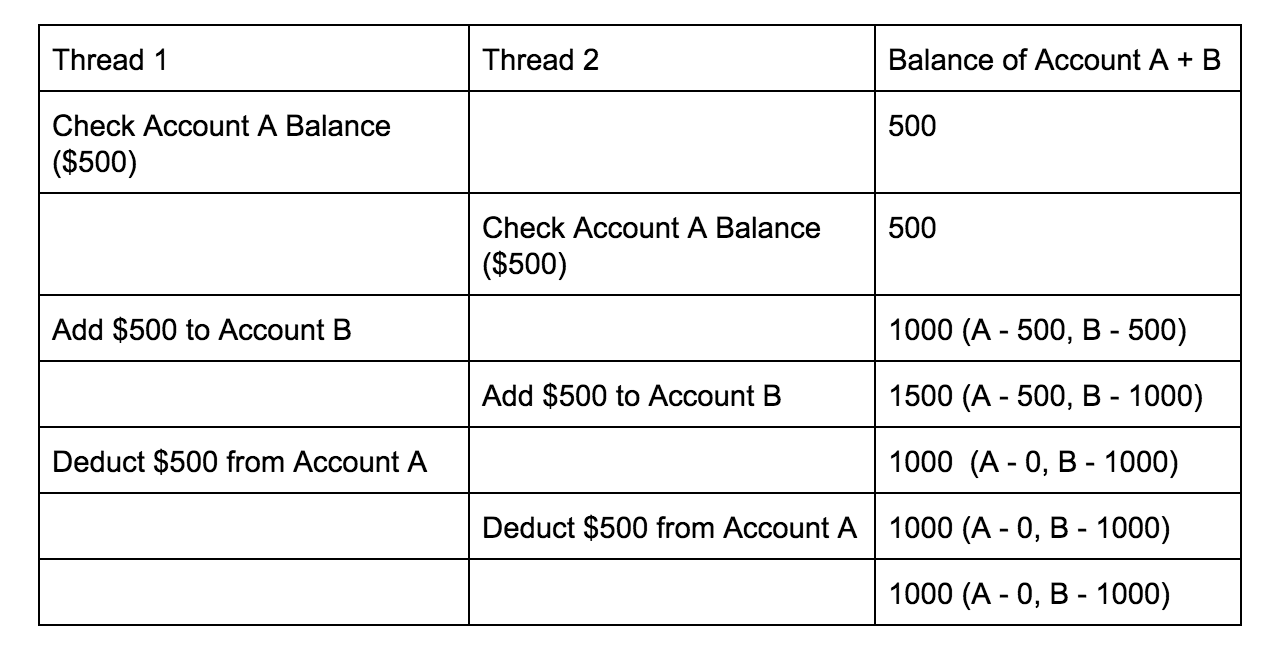
Note that in this scenario, you end up with more money than you started with! You essentially made an additional $500 appear out of thin air by exploiting a race condition vulnerability.
请注意,在这种情况下,最终获得的资金比开始时要多! 通过利用种族条件漏洞,您基本上可以凭空赚了500美元。
案例研究:无限星巴克咖啡 (Case Study: Unlimited Starbucks Coffee)
A cool example of how race conditions have been exploited in real life was the Starbucks hack by security researcher Egor Homakov.
安全研究员埃戈尔·霍马科夫(Egor Homakov)的星巴克黑客程序就是现实生活中如何利用种族条件的一个很酷的例子。
By exploiting a race condition on the gift card page, he found a way to generate an unlimited amount of credit on Starbucks gift cards for free.
通过利用礼品卡页面上的竞赛条件,他找到了一种免费生成星巴克礼品卡无限量信用额的方法。
This vulnerability lies in the functionality that transfers the gift card balance from one card to another. The website uses the following POST request to transfer credit:
此漏洞在于将礼品卡余额从一张卡转移到另一张卡的功能。 该网站使用以下POST请求来转移信用额:
POST /step1?amount=5&from=card_A&to=card_BWhen this request is sent multiple times within a small time frame, the hacker can induce a situation in which he can transfer more money into card B than the account balance that he has on card A. This means that when executed for many times, this attack generates unlimited amounts of money on card B for free.
当在短时间内多次发送此请求时,黑客可能会导致一种情况,即他可以将比他在卡A上的帐户余额多的钱转入卡B。这意味着当多次执行此操作时,攻击免费产生无限量的B卡金钱。
The root cause of this attack is a race condition between these three actions:
此攻击的根本原因是这三个动作之间的竞争状态:
- Check that card A has enough money to be transferred. 检查卡A是否有足够的钱可以转账。
- Transfer that amount to card B. 将该金额转入卡B。
- Deduct the balance of card A. 扣除卡A的余额。
This is the breakdown of the race condition that caused the vulnerability:
这是导致漏洞的竞争条件的细分:
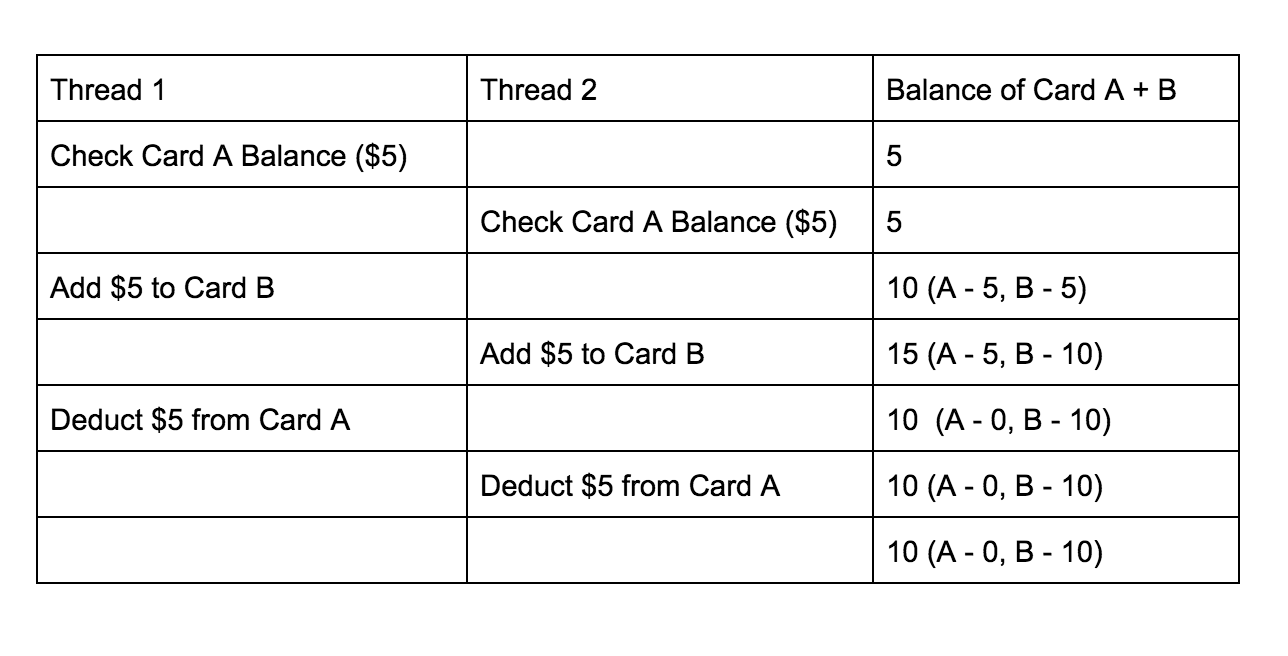
You can read more about the fun details of the exploit here.
您可以在此处详细了解该漏洞利用的有趣细节。
高风险应用 (High-Risk Applications)
Race conditions are used as a way to subvert access controls. So in theory, any application that has sensitive actions that rely on access control mechanisms could be vulnerable.
竞争条件被用作颠覆访问控制的一种方式。 因此,从理论上讲,任何具有依赖访问控制机制的敏感动作的应用程序都可能受到攻击。
Most of the time though, hackers target race conditions on the websites of financial institutions. Because if a race condition could be found on a critical functionality like cash withdrawal, fund transfer or credit card payment, it could lead to infinite financial gains for the hacker.
但是,在大多数情况下,黑客将种族条件瞄准了金融机构的网站。 因为如果在关键功能(例如现金提取,资金转帐或信用卡付款)上发现了竞争状况,那么这可能会为黑客带来无限的财务收益。
Other high-risk applications include e-commerce sites, online games, and online voting systems.
其他高风险应用程序包括电子商务网站,在线游戏和在线投票系统。
Additionally, if an exploitable race condition was ever found on a site, it is possible that the site does not follow secure programming practices and thus the likelihood of it being vulnerable again is high.
此外,如果在站点上发现了可利用的竞争条件,则该站点可能未遵循安全的编程惯例,因此再次受到攻击的可能性很高。
利用比赛条件 (Exploiting Race Conditions)
Most of the time, you can test for and exploit race conditions in web apps by sending multiple requests to the server simultaneously.
在大多数情况下,您可以通过同时向服务器发送多个请求来测试和利用Web应用程序中的竞争条件。
Bank Account balance: 3000For example, if you want to see if you can withdraw more money than you have in your bank account, you can simultaneously send multiple requests for withdrawal to the server via the curl command.
例如,如果要查看是否可以提取比银行帐户中更多的钱,则可以通过curl命令同时向服务器发送多个提款请求。
curl (withdraw 3000) & (withdraw 3000) & (withdraw 3000) & (withdraw 3000) & (withdraw 3000) & (withdraw 3000)Note that whether your attack succeeds or not would depend on the process scheduling algorithm of the server and is a matter of luck. However, the more requests you send within a short time frame, the better the odds that your attack will succeed.
请注意,您的攻击是否成功取决于服务器的进程调度算法,这很幸运。 但是,您在短时间内发送的请求越多,攻击成功的几率就越大。
防止比赛条件 (Preventing Race Conditions)
The key to preventing race conditions is to implement safe concurrency. And the best way to do this is by using resource locks. Most programming languages that have concurrency abilities will also have some sort of locking functionality built-in. Please refer to the documentation of your chosen language to learn how to do it!
防止竞争条件的关键是实现安全并发。 最好的方法是使用资源锁。 大多数具有并发功能的编程语言还将内置一些锁定功能。 请参考您选择的语言的文档以了解如何做!
Beyond that, following secure coding practices (like the least privilege principle) and auditing code on a regular basis will reduce the likelihood of your application being hacked!
除此之外,遵循安全编码惯例(如最低特权原则)并定期审核代码将减少您的应用程序被黑客入侵的可能性!
Thanks for reading. And remember: trying this on systems where you don’t have permission to test is illegal. If you’ve found a vulnerability, please disclose it responsibly to the vendor. Help make our Internet a safer place.
谢谢阅读。 请记住:在没有测试许可的系统上尝试这样做是非法的。 如果您发现了漏洞,请以负责任的方式向供应商披露。 帮助使我们的互联网更安全。
Is there anything I missed? Feel free to let me know on Twitter.
我有什么想念的吗? 随时在Twitter上让我知道。
翻译自: https://medium.com/swlh/hacking-banks-with-race-conditions-2f8d55b45a4b





















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








