linux sshd是什么
SSH, or Secure Shell, is a network protocol that allows one computer to securely connect to another computer over an unsecured network, like the internet, by having a shared agreement of how to communicate. SSH is an application layer protocol, which is the 7th layer of the OSI model.
SSH或Secure Shell是一种网络协议,它允许一台计算机通过共享通信方式协议,通过不安全的网络(例如Internet)安全地连接到另一台计算机。 SSH是应用程序层协议,它是OSI模型的第七层。
SSH is really useful because you do not have to have physical access to another machine; you can simply connect to it over the internet. This allows us to control servers remotely.
SSH非常有用,因为您不必物理访问另一台计算机。 您可以简单地通过Internet连接到它。 这使我们可以远程控制服务器。
SSH first appeared in the mid 90s and was designed as a replacement for Telnet, which is also an application layer protocol that transferred data without encryption. Without encryption, data travels over the internet in plain text. Anyone with a packet sniffer between you and the remote machine could see all the data you were transferring and everything you were doing.
SSH最早出现于90年代中期,被设计为Telnet的替代,后者也是一种无需加密即可传输数据的应用层协议。 如果不加密,数据将以纯文本格式在Internet上传输。 任何人在您与远程计算机之间使用数据包嗅探器时,都可以看到您正在传输的所有数据以及正在执行的所有操作。
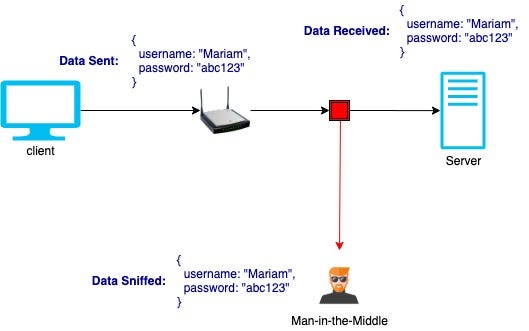
Encryption is a way to hide a piece of data so that it is unreadable unless you know how to decode or decrypt the data. SSH was created as a secure way of communication which encrypts data through a tunnel, so that bad actors cannot retrieve the data during transfer. With SSH, you can still see that data is being transferred and how much data is being transferred, but you cannot see what the data is.
加密是一种隐藏数据的方法,除非您知道如何解码或解密数据,否则它是不可读的。 SSH被创建为一种安全的通信方式,可以通过隧道对数据进行加密,因此不良行为者无法在传输过程中检索数据。 使用SSH,您仍然可以看到正在传输数据以及正在传输多少数据,但是看不到数据是什么。
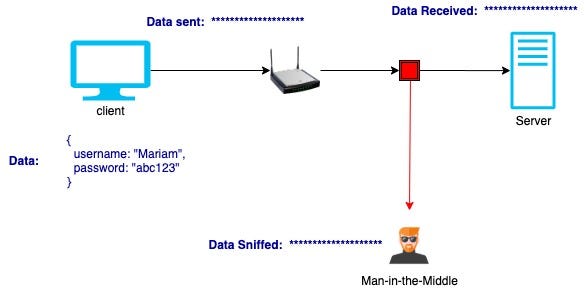
SSH is commonly implemented using the client-server model. One computer is called the SSH client and another machine acts as the SSH server, or host.
SSH通常使用客户端-服务器模型来实现 。 一台计算机称为SSH客户端 ,另一台计算机称为SSH服务器或主机 。
HTTPS, or Hyper Text Transfer Protocol Secure, is also another protocol that encrypts data. So what is the difference between SSH and HTTPS? HTTPS allows web browsers to communicate with servers to display websites. SSH allows for shells to enable data exchange or communication between two devices, not just browsers and a server. Shells allow you to talk to operating systems.
HTTPS或安全的超文本传输协议也是另一种加密数据的协议。 那么SSH和HTTPS有什么区别? HTTPS允许Web浏览器与服务器通信以显示网站。 SSH允许外壳程序启用两个设备之间的数据交换或通信,而不仅仅是浏览器和服务器。 Shell使您可以与操作系统对话。
When you connect to an SSH server, you are dropped into a shell. This shell can be a Linux terminal shell or a Windows command prompt shell where you can execute commands on the machine you are connected to. When you use terminal or command line, you are talking to your operating system. With SSH, you can talk to remote operating systems too.
连接到SSH服务器时,您将进入外壳。 该外壳可以是Linux终端外壳,也可以是Windows命令提示符外壳,您可以在其中连接的计算机上执行命令。 当您使用终端或命令行时,您正在与操作系统进行通信。 使用SSH,您也可以与远程操作系统通信。
我们可以通过SSH传输什么? (What Can We Transfer With SSH?)
SSH can be used to transmit:
SSH可用于传输:
- Data 数据
- Commands 指令
- Text 文本
- Files (Using SFTP: Secure File Transfer Protocol, basically an encrypted version of FTP that makes it that man-in-the-middle attacks are not possible) 文件(使用SFTP:安全文件传输协议,基本上是FTP的加密版本,无法进行中间人攻击)
SSH如何工作? (How does SSH work?)
SSH breaks data down into a series of packets. Like any packet transfer, there are a few fields at the beginning.
SSH将数据分解为一系列数据包。 像任何数据包传输一样,开头有一些字段。

At the top, the Packet Length tells you how big the packet is. After that, you have another byte, Padding Amount, tells you how much padding there is. Then you have your data, the Payload. Following the payload, you have Padding. That padding is random bytes that don’t mean anything but are encrypted along with the payload to make it even harder to detect the data because you’ve thrown in this random extra data. Finally, you have a Message Authentication Code so that you can be sure the data has not been tampered with.
在顶部, 数据包长度告诉您数据包的大小。 之后,您还有另一个字节, Padding Amount ,告诉您有多少填充。 然后,您有了数据,即Payload 。 在有效负载之后,您具有Padding 。 填充是随机字节,它什么都没有,但是会与有效负载一起加密,从而使检测数据变得更加困难,因为您已经抛出了这个随机的额外数据。 最后,您有一个消息身份验证代码,以便可以确保数据未被篡改。
The payload can also be compressed using standard compression algorithms. The whole packet, excluding the length and authentication code, is then encrypted.
有效载荷也可以使用标准压缩算法进行压缩。 然后对整个数据包(不包括长度和验证码)进行加密。

The packet is then sent to the server. The server decrypts the packet and decompresses the payload to extract the data. The same process is done for every packet sent over the connection.
然后将数据包发送到服务器。 服务器解密该数据包并解压缩有效负载以提取数据。 对于通过连接发送的每个数据包都执行相同的过程。
To keep SSH secure, SSH uses three different types of data manipulation techniques at various points during a transmission. The three techniques used in SSH are:
为了保持SSH的安全性,SSH在传输过程中的各个时间点使用三种不同类型的数据处理技术。 SSH中使用的三种技术是:
- Symmetrical Encryption 对称加密
- Asymmetrical Encryption 非对称加密
- Hashing 散列
对称加密 (Symmetrical Encryption)
Symmetric encryption is the type of encryption where one key can be used to encrypt messages sent to the destination and also decrypt messages received at the destination. This encryption scheme is also known as a shared secret encryption, or a shared key encryption.
对称加密是一种加密类型,其中一个密钥可用于加密发送到目的地的消息,也可以解密在目的地接收的消息。 此加密方案也称为共享秘密加密或共享密钥加密 。

Both devices use the same key to encrypt data they are sending over and decrypt data they receive. A secret key is specific to each SSH session. This is the type of encryption that is used to encrypt the entire SSH connection to stop man-in-the-middle attacks from being able to read the data because they do not have this secret key.
两种设备都使用相同的密钥来加密正在发送的数据和解密所接收的数据。 密钥是每个SSH会话专用的。 这是一种加密类型,用于加密整个SSH连接,以阻止中间人攻击能够读取数据,因为它们没有此密钥。
One problem that arises is the initial key exchange. If a third party is listening during the key exchange, they would now know the key and be able to decrypt all our messages. One way to prevent this is by using a Key Exchange Algorithm.
出现的一个问题是初始密钥交换。 如果第三方在密钥交换期间正在侦听,他们现在将知道密钥并能够解密我们的所有消息。 一种防止这种情况的方法是使用密钥交换算法。
A Key Exchange Algorithm is a secure way to exchange secret keys without interception. This is done by two computers exchanging public data and then manipulating that data independently to derive the secret key. In order to implement a key exchange algorithm, we need Asymmetrical Encryption.
密钥交换算法是一种无需拦截即可交换秘密密钥的安全方法。 这是通过两台计算机交换公共数据,然后独立地处理该数据以导出密钥来完成的。 为了实现密钥交换算法,我们需要非对称加密。
非对称加密 (Asymmetrical Encryption)
Asymmetrical encryption is encryption through the use of two separate keys for encryption and decryption, a public key and a private key. The public key can be can be shared with anyone but the private key is never shared. A public key and a private key form a key pair. A message that is encrypted with a machine’s public key can only be decrypted by its private key. The public key is stored on the SSH server and the private key is stored locally on the SSH client.
非对称加密是通过使用两个单独的密钥进行加密和解密来进行加密,即公共密钥和私有密钥。 可以与任何人共享公共密钥,但永远不会共享私有密钥。 公钥和私钥构成密钥对 。 用机器的公钥加密的消息只能用其私钥解密。 公钥存储在SSH服务器上,私钥存储在SSH客户端本地。
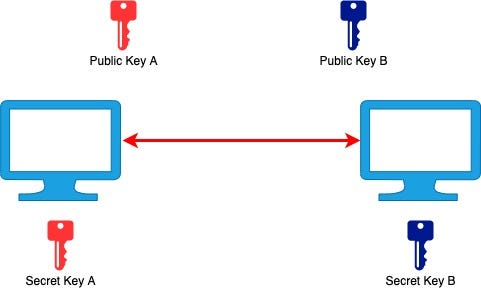
If I give you my public key, you can send me a message by encrypting it with my public key. I will then be able to read it by decrypting it using my private key.
如果我给您我的公共密钥,您可以通过使用我的公共密钥加密它来向我发送消息。 然后,我将可以通过使用我的私钥对其解密来读取它。
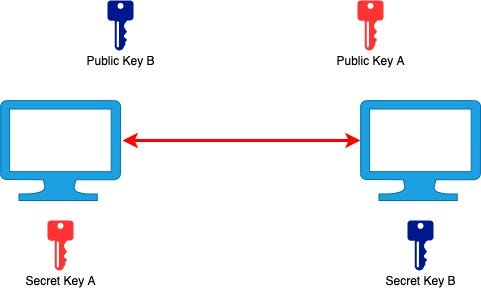
Even if a third party manages to obtain a public key, they will not be able to decrypt any messages because they don’t have the private key. So long as the private key is never sent over and is secure on your device, your messages can’t be decrypted.
即使第三方设法获取了公共密钥,他们也将无法解密任何消息,因为它们没有私有密钥。 只要私钥永远不会发送出去并且在您的设备上是安全的,您的消息就不会被解密。
SSH uses asymmetrical encryption in a few places such as the key exchange algorithm used to set up the symmetrical encryption. Asymmetrical encryption is also used as the key that can be used to SSH into a server without the use of a password. We exchange the algorithm to generate the keys (the yellow keys in diagram 1) used to encrypt and decrypt messages.
SSH在一些地方使用非对称加密,例如用于建立对称加密的密钥交换算法。 非对称加密还用作密钥,可用于在不使用密码的情况下SSH进入服务器。 我们交换算法以生成用于加密和解密消息的密钥(图1中的黄色密钥)。
Both devices generate temporary public and private keys and share their respective public keys. They then independently generate a new symmetric key that both devices will use to encrypt and decrypt messages. This generation is done using the Diffie Hellman key exchange.
这两个设备都生成临时的公共和私有密钥,并共享它们各自的公共密钥。 然后,它们独立生成一个新的对称密钥,两个设备都将使用该对称密钥来加密和解密消息。 这一生成是使用Diffie Hellman密钥交换完成的 。
At the start of a Diffie Hellman key exchange, the two devices need to agree on a few parameters that they will use for the key exchange:
在Diffie Hellman密钥交换开始时,这两个设备需要就它们将用于密钥交换的一些参数达成一致:
Generator
g发电机
gPrime number
n素数
n
Each device will use g along with their private keys to generate a public key.
每个设备将使用g及其私钥来生成公钥。
If you want to know the math behind the Diffie Hellman, watch this video.
如果您想了解Diffie Hellman背后的数学原理,请观看此视频 。
Once a secure symmetric communication has been established, the server uses the client’s public key to generate a challenge and transmits it to the client for authentication. If the client can successfully decrypt the challenge, which means that it holds the private key required for a connection, the SSH session begins.
一旦建立了安全的对称通信,服务器就会使用客户端的公共密钥来生成质询 ,并将其发送给客户端以进行身份验证。 如果客户端可以成功解密挑战,这意味着它拥有连接所需的私钥,则SSH会话将开始。
散列 (Hashing)
Hashing is another form of cryptography used it secure shell connections. Hashing allows you to create a signature or summary of a set of information. It is a one-way process and hashed data is never meant to be decrypted. But how is this useful?
散列是用于保护外壳连接的另一种加密形式。 散列使您可以创建一组信息的签名或摘要。 这是一个单向过程,散列数据绝不打算解密。 但这有什么用?
If a third party manages to dupe the client and the host, they can tamper with messages. SSH uses HMAC (Hash-based Message Authentication Codes). HMACs ensure that the messages sent are received in a complete and unmodified form.
如果第三方设法欺骗客户端和主机,则它们可能会篡改消息。 SSH使用HMAC ( 基于哈希的消息身份验证代码 )。 HMAC确保以完整且未修改的形式接收发送的消息。
Using a hash function, each message that is transmitted must contain something called a MAC. This MAC is a hash generated from the symmetric key, the packet sequence number and the message contents that were sent. Using these three elements combined as inputs into a hash function and this hash function will output some piece of string that has no meaning. This string, or signature, is sent to the host.
使用散列函数,传输的每个消息都必须包含称为MAC的内容。 该MAC是根据对称密钥,数据包序列号和已发送的消息内容生成的哈希。 使用这三个元素组合作为哈希函数的输入,此哈希函数将输出一些没有意义的字符串。 该字符串或签名被发送到主机。
Now, how does the host check if the message has been tampered with?
现在,主机如何检查邮件是否已被篡改?
Because the host has the same information (the symmetric key, the packet sequence number, and the message content), they can use the same hash function to generate a hash too. If the generated hash matches the one received, this verifies the signature of the client.
因为主机具有相同的信息(对称密钥,数据包序列号和消息内容),所以它们也可以使用相同的哈希函数来生成哈希。 如果生成的哈希与接收到的哈希匹配,则这将验证客户端的签名 。
This works because if the data is changed in any way, even something as small as capitalizing a letter, the hash will be completely different.
之所以可行,是因为如果以任何方式更改数据,即使是大小写字母大小的更改,哈希也将完全不同。
I hope this quick overview leaves you with a better understanding of SSH. I’ve listed the following references to use to delve deeper into SSH if you are interested.
我希望本文能使您对SSH有更好的了解。 如果您感兴趣,我列出了以下参考资料,可用于更深入地研究SSH。
Thanks for reading!
谢谢阅读!
翻译自: https://levelup.gitconnected.com/what-is-ssh-103f89e3e4b8
linux sshd是什么























 1170
1170

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








