渗透测试和黑客攻击的区别
A hacker is a highly skilled computer operator who uses bugs and exploits to break into computer systems and networks. An ethical hacker, on the other hand, identifies vulnerabilities in computer systems and networks, and plugs these holes. Here’s a round-up of the ten best operating systems for ethical hackers and penetration testers.
黑客是技术娴熟的计算机操作员,他们使用错误和漏洞侵入计算机系统和网络。 另一方面,道德黑客会识别计算机系统和网络中的漏洞,并填补这些漏洞。 这是针对道德黑客和渗透测试人员的十种最佳操作系统的综述。
If you want to Gain In-depth Knowledge on Hacking, please go through this link Ethical Hacking Online Training
如果您想获得有关黑客的深入知识,请通过此链接进行道德黑客在线培训
Hacking has been part of computing for over five decades and is a very broad area, covering a range of tasks. The term hacker originated in 1960 at MIT. Hacking is regarded as a process of locating all possible back doors that exist in a computer system or network and, finally, intruding into it. In simple terms, it is regarded as an unauthorized activity to gain access to a computer system or network, to harm it or prevent its normal functions and to steal sensitive information available on computing systems.
黑客入侵已成为计算领域的五十多年,涉及面很广,涉及一系列任务。 黑客一词起源于1960年的麻省理工学院。 黑客被认为是定位计算机系统或网络中存在的所有可能后门,并最终侵入其中的过程。 简单来说,获得对计算机系统或网络的访问,损害或阻止其正常功能以及窃取计算系统上可用的敏感信息被视为未经授权的活动。
On the other hand, hacking can also be a legal activity when it is used to discover back doors and weaknesses in computer systems in order to patch them. This is called ethical hacking.
另一方面,当黑客用于发现后门和计算机系统中的漏洞以修补它们时,黑客也可能是合法活动。 这被称为道德黑客。
In today’s cyber world, lots of varied attacks occur every hour and are achieved by professional hackers, virus writers and crackers. The most basic tool required by every hacker is a hacking operating system. Usually, the operating systems specializing in hacking are based on the Linux kernel. These operating systems are regarded as advanced working systems, which include lots of ethical hacking and penetration testing tools.
在当今的网络世界中,每小时都会发生各种各样的攻击,并且都是由专业的黑客,病毒作者和破解者来实现的。 每个黑客都需要的最基本工具是黑客操作系统。 通常,专门从事黑客攻击的操作系统基于Linux内核。 这些操作系统被视为高级操作系统,其中包括许多道德黑客和渗透测试工具。
In this article, the ten best operating systems used by ethical hackers and penetration testers are featured. All of them are free, open source, are based on the Linux kernel and are bundled with many hacking tools.
在本文中,将介绍道德黑客和渗透测试人员使用的十种最佳操作系统。 所有这些都是免费的,开源的,基于Linux内核的,并且捆绑了许多黑客工具。
1. Kali LinuxKali Linux is based on the Debian-Linux distribution, and is especially designed for digital forensics and penetration testing. It is maintained and updated on a regular basis by Offensive Security Ltd, under the leadership of Mati Aharoni, Devon Kearns, and Raphael Hertzog who are core developers. Kali comes pre-installed with more than 300 penetration testing programs and can be installed as a primary operating system on the hard disk, live CD/USB and can even run as a virtual machine using some virtualization software.
1. Kali Linux Kali Linux基于Debian-Linux发行版,是专门为数字取证和渗透测试而设计的。 它是由Offensive Security Ltd在核心开发人员Mati Aharoni,Devon Kearns和Raphael Hertzog的领导下定期维护和更新的。 Kali预先安装了300多个渗透测试程序,可以作为主要操作系统安装在硬盘,实时CD / USB上,甚至可以使用某些虚拟化软件作为虚拟机运行。
Kali Linux supports both 32-bit and 64-bit images for use with x86 machines, and even supports various development boards like Raspberry Pi, BeagleBone, Odroid, CuBox, etc.
Kali Linux支持与x86机器一起使用的32位和64位映像,甚至还支持Raspberry Pi,BeagleBone,Odroid,CuBox等各种开发板。
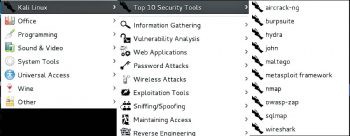
Tool categories
工具类别
Information gathering: These tools are used to gather information regarding DNS, IDS/IPS, network scanning, operating system, routing, SSL, SMB, VPN, VOPI, SNMP, email and VPN.
信息收集:这些工具用于收集有关DNS,IDS / IPS,网络扫描,操作系统,路由,SSL,SMB,VPN,VOPI,SNMP,电子邮件和VPN的信息。
Vulnerability assessment: These tools access the CISCO network and discover vulnerabilities in several database servers.
漏洞评估:这些工具访问CISCO网络并发现多个数据库服务器中的漏洞。
Web applications: These tools are related to Web applications like content management systems, database exploitation, application proxies, Web vulnerability scanners, etc.
Web应用程序:这些工具与Web应用程序相关,例如内容管理系统,数据库利用,应用程序代理,Web漏洞扫描程序等。
Password attacks: These tools perform password attacks via brute force, dictionary attacks, etc.
密码攻击:这些工具通过蛮力,字典攻击等执行密码攻击。
Exploitation tools: These exploit vulnerabilities in target systems for networks, the Web and databases, and to perform social engineering attacks.
利用工具:这些工具利用目标系统中的网络,Web和数据库漏洞,并执行社会工程学攻击。
Sniffing and spoofing: These tools sniff the network and Web traffic.
嗅探和欺骗:这些工具嗅探网络和Web流量。
Maintaining access: These tools maintain access to the target machine, to assess operating system back doors and for tunnelling.
维护访问权限:这些工具可维护对目标计算机的访问权限,以评估操作系统的后门和隧道连接。
Reporting tools: These document the penetration testing process.
报告工具:这些工具记录了渗透测试过程。
System services: These tools contain various pen-testing services like Apache, MySQL, SSH and Metasploit services.
系统服务:这些工具包含各种笔测试服务,例如Apache,MySQL,SSH和Metasploit服务。
Kali Linux is bundled with several tools that perform wireless attacks, reverse engineering, stress testing, hardware hacking and forensics.
Kali Linux捆绑有执行无线攻击,逆向工程,压力测试,硬件黑客和取证的多种工具。
Key features:
主要特点:
- Bundled with more than 600 penetration testing tools as compared to Backtrack OS. 与Backtrack OS相比,捆绑了600多种渗透测试工具。
- Completely free and open source and committed to GitHub, with the source code of each package being available. 完全免费和开源,并致力于GitHub,每个软件包的源代码都可用。
- Kali Linux is FHS (Filesystem Hierarchy Standard) compliant to locate binaries, and support files and libraries. Kali Linux符合FHS(文件系统层次结构标准),可查找二进制文件并支持文件和库。
- Kali Linux offers a custom kernel for customised coding and patching up the latest updates. Kali Linux提供了一个定制内核,用于定制编码和修补最新更新。
- Every package in it is GPG signed and, hence, committed to high quality standards by developers. 其中的每个程序包均经过GPG签名,因此开发人员致力于达到高质量标准。
- ARMEL and ARMHF support allows Kali Linux to be installed on various other devices like Pi, Odroid, Chromebook, etc. 通过ARMEL和ARMHF支持,Kali Linux可以安装在其他各种设备上,例如Pi,Odroid,Chromebook等。
2. BackBoxBackBox is an Ubuntu-based Linux distribution aimed at assisting ethical hackers and penetration testers in security assessments. BackBox OS is designed with the objective of being faster, easily operable and having a minimal desktop environment. The key advantage of BackBox is that its own software repositories are updated at regular intervals to keep the distribution stable and popular for real-world operations.The BackBox distribution consists of more than 70 tools for tasks ranging from Web analysis and network analysis to stress testing, sniffing, vulnerability assessment, forensics and exploitation.
2. BackBox BackBox是基于Ubuntu的Linux发行版,旨在帮助道德黑客和渗透测试人员进行安全评估。 BackBox OS的设计目标是更快,更容易操作并且具有最小的桌面环境。 BackBox的主要优势在于它自己的软件存储库会定期更新,以保持发行版稳定并在实际操作中广受欢迎.BackBox发行版包含70多种工具,可用于从Web分析和网络分析到压力测试的任务,嗅探,漏洞评估,取证和利用。
Key features:
主要特点:
- BackBox Linux is one of the first platforms supporting the cloud for penetration testing. BackBox Linux是最早支持云进行渗透测试的平台之一。
- It is fully automated and non-intrusive, with no agents or network configuration changes required to achieve regular automated configuration backups. 它是完全自动化且非侵入式的,无需进行代理或网络配置更改即可实现常规的自动配置备份。
- Saves time and eliminates the requirement of tracking individual network devices. 节省时间并消除了跟踪单个网络设备的需求。
- With support of the XFCE desktop, BackBox is regarded as fast in operations and suitable even for old configuration systems. 借助XFCE桌面的支持,BackBox被认为运行速度很快,甚至适用于旧的配置系统。
- Completely hacker friendly due to the support it receives for creating its own Launchpad PPA and sending the package to developers who, in turn, contribute instantly to BackBox Linux. 由于获得了创建自己的Launchpad PPA并将软件包发送给开发人员的支持,因此对黑客完全友好,而开发人员又直接为BackBox Linux做出了贡献。
3. Parrot Security Operating SystemParrot Security OS is based on Debian GNU/Linux combined with the Frozenbox OS and Kali Linux to provide ethical hackers the best-in-class experience of penetration and security testing in real-world environments. It is also designed to provide vulnerability assessment and mitigation, computer forensics and anonymous Web browsing, by the Frozenbox team.Parrot Security OS makes use of Kali repositories for all sorts of package updates and to integrate new tools. It makes use of the MATE desktop environment using the LightDM display manager to provide an easy-to-use GUI and lightweight environment for computer system analysts to perform all sorts of forensics, vulnerability assessment and cryptography. This OS is known for being highly customisable and for its strong community support.
3. Parrot Security操作系统 Parrot Security操作系统基于Debian GNU / Linux,Frozenbox OS和Kali Linux的组合,为道德黑客提供了在真实环境中进行渗透和安全测试的一流体验。 它还被设计为由Frozenbox团队提供漏洞评估和缓解,计算机取证和匿名Web浏览。ParrotSecurity OS使用Kali存储库进行各种软件包更新并集成新工具。 它利用LightDM显示管理器利用MATE桌面环境,为计算机系统分析人员提供易于使用的GUI和轻量级环境,以执行各种取证,漏洞评估和加密。 该操作系统以高度可定制性和强大的社区支持而闻名。
Key features:
主要特点:
- Equipped with the highly customisable kernel version 4.5, it is currently under rolling release upgrade line and based on Debian 9. 配备了高度可定制的内核版本4.5,它目前处于滚动发布升级线下,并且基于Debian 9。
- Has custom anti-forensic tools, interfaces for GPG, Cryptsetup, and support for LUKS, Truecrypt and VeraCrypt. 具有自定义的取证工具,用于GPG,Cryptsetup的界面,并支持LUKS,Truecrypt和VeraCrypt。
- It supports FALCON 1.0 programming language, multiple compilers, debuggers and the Qt5 and .NET/mono frameworks. 它支持FALCON 1.0编程语言,多种编译器,调试器以及Qt5和.NET / mono框架。
- Supports Anonsurf including anonymisation of the entire OS, TOR, I2P anonymous networks and beyond. 支持Anonsurf,包括整个OS,TOR,I2P匿名网络以及其他范围的匿名化。
A special edition of Parrot Cloud, designed for servers, comprises lightweight Parrot OS distributions without graphics, wireless and forensics tools, and acts as a VPS or dedicated server with only useful security tools. To get in-depth knowledge on Cyber Security Online Training
专门为服务器设计的Parrot Cloud特殊版本包括轻量级的Parrot OS发行版,不包含图形,无线和取证工具,并且充当VPS或仅具有有用安全工具的专用服务器。 深入了解网络安全在线培训
4. DEFT LinuxDEFT (Digital Evidence and Forensics Toolkit) is based on GNU Linux and DART (Digital Advanced Response Toolkit), a forensics system comprising some of the best tools for forensics and incident response. DEFT Linux is especially designed for carrying out forensics tasks and runs live on systems without tampering with the hard disk or any other storage media. It consists of more than 100 highly-rated forensics and hacking tools.It is currently developed and maintained by Stefano Fratepietro along with other developers, and is available free of charge. It is used actively by ethical hackers, pen testers, government officers, IT auditors and even the military for carrying out various forensics based systems analysis.
4. DEFT Linux DEFT(数字证据和取证工具包)基于GNU Linux和DART(数字高级响应工具包),DART是一个包括一些用于取证和事件响应的最佳工具的取证系统。 DEFT Linux专为执行取证任务而设计,可在系统上实时运行,而不会篡改硬盘或任何其他存储介质。 它由100多种高度评价的取证和黑客工具组成,目前由Stefano Fratepietro和其他开发人员共同开发和维护,可免费获得。 道德黑客,钢笔测试人员,政府官员,IT审计人员甚至军方都积极使用它来执行各种基于法医的系统分析。
Key features:
主要特点:
- It is based on the Lubuntu distribution comprising open source digital forensics and penetration testing tools. 它基于Lubuntu发行版,该发行版包含开源数字取证和渗透测试工具。
- Full support for Bitlocker encrypted disks, Android and iOS 7.1 logical acquisitions. 完全支持Bitlocker加密磁盘,Android和iOS 7.1逻辑采集。
- Consists of Digital Forensics Framework 1.3. 包含数字取证框架1.3。
5.Samurai Web Testing FrameworkSamurai Web Testing Framework primarily focuses on testing the security of Web applications and comprises lots of Web assessment and exploitation tools. The credit for developing the Samurai Web Testing Framework goes to Kevin Johnson, Justin Searle and Frank DiMaggio. The Samurai Framework provides ethical hackers and pen testers with a live Linux environment that is preconfigured to run as a virtual machine to perform Web penetration testing.The Samurai Web Testing Framework includes popular testing tools like Fierce Domain Scanner and Maltego for Reconnaissance, WebScarab and Ratproxy for mapping, w3af and Burp for discovery, and BeEF and AJAXShell for exploitation.The framework is based on Ubuntu 9.04, is fully open source and receives regular updates with regard to products.
5.Samurai Web测试框架 Samurai Web测试框架主要侧重于测试Web应用程序的安全性,并且包含许多Web评估和开发工具。 开发Samurai Web测试框架的功劳归于Kevin Johnson,Justin Searle和Frank DiMaggio。 Samurai框架为道德的黑客和笔测试人员提供了一个实时Linux环境,该环境已预先配置为可以作为虚拟机运行以执行Web渗透测试.Samurai Web测试框架包括流行的测试工具,例如用于侦察的Fierce Domain Scanner和Maltego,WebScarab和Ratproxy该框架基于Ubuntu 9.04,是完全开源的,并且会定期接收有关产品的更新。
Key features:
主要特点:
- Contains many tools for reconnaissance, mapping, discovery and exploitation, especially focusing on Web penetration testing. 包含许多用于侦察,映射,发现和利用的工具,尤其着重于Web渗透测试。
- Equipped with SVN to provide updated security tools, and syncs with active development tools. 配备SVN以提供更新的安全工具,并与活动的开发工具同步。
6. Network Security ToolkitThe Network Security Toolkit (NST), based on Fedora, is a live bootable DVD/USB Flash drive consisting of the top 125 open source security tools provided by insecure.org to perform network security, penetration testing, network diagnostics and monitoring of day-to-day tasks. The main objective behind the development of NST is to provide network/systems administrators a combined set of open source security tools to carry out operations like network traffic analysis, intrusion detection, network scanning and security patching.NST has been developed by Ronald W. Henderson and Paul Blankenbaker. It provides a Web interface known as NST WUI and all the tools can be accessed via the Web page. NST is equipped with intelligent package management capabilities based on Fedora and maintains its own repositories of additional packages.
6.网络安全工具包基于Fedora的网络安全工具包(NST)是可启动的DVD / USB闪存驱动器,由insecure.org提供的排名前125位的开源安全工具组成,用于执行网络安全,渗透测试,网络诊断。并监控日常任务。 NST开发的主要目标是为网络/系统管理员提供一套组合的开源安全工具,以执行网络流量分析,入侵检测,网络扫描和安全修补等操作。NST由Ronald W. Henderson开发和保罗·布兰肯贝克(Paul Blankenbaker)。 它提供了一个称为NST WUI的Web界面,并且可以通过该网页访问所有工具。 NST具备基于Fedora的智能软件包管理功能,并维护自己的附加软件包存储库。
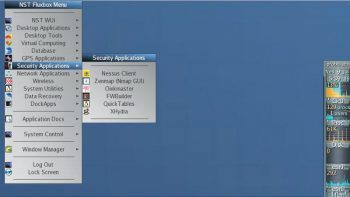
Key features:
主要特点:
- Provides visualisation of ntopng, ntop, Wireshark, traceroute, NetFlow and Kismet data. 提供ntopng,ntop,Wireshark,traceroute,NetFlow和Kismet数据的可视化。
- JavaScript console with built-in object library helps in the development of dynamic Web pages. 带有内置对象库JavaScript控制台有助于动态网页的开发。
- Other features include network intrusion detection, Web-based Snort IDS integration, active connections monitor, VNC/RDP desktop session management, host/IPv4 address geolocation and network segment ARP scanner. 其他功能包括网络入侵检测,基于Web的Snort IDS集成,活动连接监控器,VNC / RDP桌面会话管理,主机/ IPv4地址地理位置和网段ARP扫描器。
7. BlackArch LinuxBlackArch is an Arch Linux-based security and penetration testing distribution, which consists of more than 1600 tools and is regarded as the first choice distribution among security researchers to do Web and applications based security testing. It is a strong alternative to Kali Linux and Backbox in terms of the variety of its tools and ease of use.BlackArch is basically a lightweight extension to Arch Linux for security researchers, as the tool set within the former is distributed as the Arch Linux unofficial user repository and can even be installed on top of existing Arch Linux.Arch Linux can be installed on 32-bit and 64-bit machines including ARM based development boards like Raspberry Pi, BeagleBone, etc.
7. BlackArch Linux BlackArch是基于Arch Linux的安全性和渗透性测试发行版,它包含1600多种工具,被视为安全研究人员中进行基于Web和应用程序的安全性测试的首选发行版。 就其工具的多样性和易用性而言,它是Kali Linux和Backbox的有力替代品。BlackArch本质上是安全研究人员对Arch Linux的轻量级扩展,因为前者中的工具集是作为非官方的Arch Linux发布的用户存储库,甚至可以安装在现有的Arch Linux之上.Arch Linux可以安装在32位和64位计算机上,包括基于ARM的开发板,如Raspberry Pi,BeagleBone等。
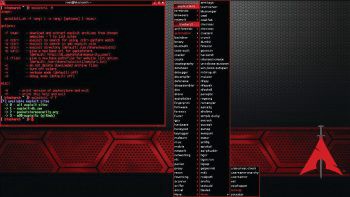
Key features:
主要特点:
- GUI interface is powered by Fluxbox and includes i3, WMii, Spectrwm, Awesome, dwm and Openbox window managers. GUI界面由Fluxbox提供支持,包括i3,WMii,Spectrwm,Awesome,dwm和Openbox窗口管理器。
- Has modular package groups. 具有模块化的包装组。
- Installation can be performed from source. 可以从源执行安装。
8. Cyborg Hawk LinuxCyborg Hawk Linux is regarded as the most advanced, powerful and well-managed Ubuntu based penetration testing Linux distribution created by Ztrela Knowledge Solutions Pvt Ltd. The distribution consists of more than 700 tools dedicated to penetration testing, and more than 300 tools for mobile security and malware analysis.Cyborg Hawk Linux is completely open source and free to use, and the latest version comes with its own repository. The distribution is highly reliable and stable in the eyes of ethical hackers and pen testers for real-world stress testing of networks, malware analysis and finding out back doors.
8. Cyborg Hawk Linux Cyborg Hawk Linux被视为由Ztrela Knowledge Solutions Pvt Ltd创建的最先进,功能强大且管理良好的基于Ubuntu的渗透测试Linux发行版。该发行版包含700多个专用于渗透测试的工具,而300种用于移动安全和恶意软件分析的工具。CyborgHawk Linux是完全开源的,可以免费使用,最新版本带有其自己的存储库。 在道德黑客和笔测试人员的眼中,该发行版高度可靠且稳定,可用于现实世界中的网络压力测试,恶意软件分析和查找后门。
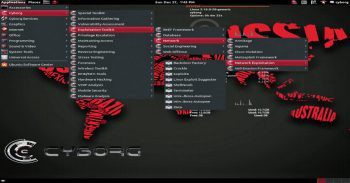
Key features:
主要特点:
- Full support for wireless devices. 全面支持无线设备。
- Can be installed as a virtual machine. 可以安装为虚拟机。
- Managed and well-sorted menus in the distribution. 分发中托管和分类良好的菜单。
- Bundles tools for exploitation, stress testing, reverse engineering, forensics, mobile security and wireless security. 捆绑了用于开发,压力测试,逆向工程,取证,移动安全和无线安全的工具。
- Secured and well patched kernel. 安全且修补良好的内核。
- Has full capability to run as Live OS. 具有作为Live OS运行的完整功能。
9. GnackTrackGnackTrack is an Ubuntu based penetration testing Linux distribution which includes lots of utilities for penetration testing. It has a GUI based GNOME desktop for easy interfacing. GnackTrack is an open source and free project, and contains various significant penetration testing tools like Metaspoilt, Armitage, wa3f and many more.
9. GnackTrack GnackTrack是一个基于Ubuntu的渗透测试Linux发行版,其中包含许多用于渗透测试的实用程序。 它具有基于GUI的GNOME桌面,可轻松进行接口连接。 GnackTrack是一个开源免费项目,包含各种重要的渗透测试工具,例如Metaspoilt,Armitage,wa3f等。

Key features:
主要特点:
- Supports both 32-bit and 64-bit hardware platforms for installation and running live OSs. 支持用于安装和运行实时操作系统的32位和64位硬件平台。
- Standard boot menu for booting up live DVD OS. 用于启动实时DVD OS的标准启动菜单。
- Inspired by Backtrack and the most useful choice for starters to learn and research penetration testing. 受Backtrack启发,是初学者学习和研究渗透测试的最有用选择。
Take your career to new heights of success by enroll for live free demo on Ethical Hacking Training
通过参加免费的Ethical Hacking Training演示免费注册演示,将您的职业提升到新的高度
10. NodeZeroNodeZero is an open source Ubuntu based penetration testing Linux distro, which makes use of Ubuntu repositories for updates. It consists of more than 300 penetration testing tools as well as a set of basic services that are required for carrying out all sorts of operations. The Linux distribution is available for download as a dual-arch live DVD ISO image, and can run on both 32-bit and 64-bit computing architectures.
10. NodeZero NodeZero是一个基于Ubuntu的开源渗透测试Linux发行版,该发行版使用Ubuntu存储库进行更新。 它包含300多种渗透测试工具以及执行各种操作所需的一组基本服务。 Linux发行版可作为双体系结构实时DVD ISO映像下载,并且可以在32位和64位计算体系结构上运行。
The live OS supports various other features like system memory diagnostic tests, hard disk booting, install direct, safe mode booting, text mode or debug mode.
实时操作系统还支持其他各种功能,例如系统内存诊断测试,硬盘启动,直接安装,安全模式启动,文本模式或调试模式。
渗透测试和黑客攻击的区别




















 4415
4415











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








