工控 恶意软件
病毒 (VIRUS)
During my undergraduate career, I had the opportunity to volunteer as a research assistant in the Pharmacology and Toxicology department, studying the adverse effects of inflammation induced by viruses in rodents.
在我的大学生涯中,我有机会自愿担任药理毒理学系的研究助理,研究啮齿动物中病毒引起的炎症的不良影响。
I was enamored by virology and infectious diseases — when I decided to change my career trajectory, the infatuation never went away. I’ve tend to see myself gravitate towards malware research by reading books, reverse engineering samples of malware and reading blogs. The similarities I’ve found between the two may be a coincidence or a natural formation of bio-mimicry. Humans are a lot like computers, we have functions and underlying code that can be tampered with or exploited by things outside of our reach.
我被病毒学和传染病迷住了。当我决定改变自己的职业道路时,痴情从未消失。 我倾向于通过阅读书籍,对恶意软件进行反向工程样本以及阅读博客来发现自己倾向于进行恶意软件研究。 我发现两者之间的相似之处可能是巧合或自然模仿。 人类就像计算机一样,我们拥有可以被我们无法企及的东西篡改或利用的功能和底层代码。
In Biology, viruses are simple-celled organisms that contain nucleic acids surrounded by a protein coat. In computers, they are an artificial life-form that corrupts a system and destroys data.
在生物学中,病毒是单细胞生物,其包含被蛋白质外壳包裹的核酸。 在计算机中,它们是人为破坏的生命形式,会破坏系统并破坏数据。
Some scientists even believe they are the key to the origin of life, but are viruses even alive? An accurate depiction of what it means to be “living“ is outlined in Computer Viruses, Artificial Life, and Evolution by Mark Ludwig
一些科学家甚至认为它们是生命起源的关键,但是病毒是否还活着? 马克·路德维格(Mark Ludwig)在“ 计算机病毒,人工生命和进化 ”中概述了“活着”的含义的准确描述。
The assertion is made that a living organism is simply a highly complex machine built of organic molecules… The question of what life is becomes merely a question of function. Design a machine with proper functions, and it will be alive.
有人断言,生命有机体只是由有机分子构成的高度复杂的机器……关于什么是生命的问题仅是功能的问题。 设计一台具有适当功能的机器,它就会恢复活力。
He states that in order to understand whether an organism is living or not is to look at the function of what that thing does.
他指出,为了了解生物体是否居住与否看的那个东西做什么功能。
Computer instructions uses 0s and 1s which translate to functions that it will execute. Living organisms contain carbon structures and proteins programmed with amino acids: Adenine, Cytosine, Thymine, and Guanine. These nucleotides chain together using a process called transcription and translation to form a structure. This structure is then used for a type of function in the body.
计算机指令使用0 s和1 s转换为它将执行的功能。 生物体含有碳结构和与氨基酸编程蛋白质: 甲丹尼恩,C ytosine,T hymine和G uanine。 这些核苷酸通过称为转录和翻译的过程连接在一起,形成一个结构。 然后将此结构用于体内的一种功能。

Here is a simple program I wrote in C that prints “Hello, World” the function of the program prints text (ASCII). For a computer to understand what to do, it translates to opcode — an instruction for a computer to execute. Its own version of transcription and translation.
这是我用C语言编写的一个简单程序,可以打印“ Hello,World”,该程序的功能可以打印文本( ASCII )。 对于计算机应采取何种措施,将其转换为操作码 -对计算机执行的指令。 自己的转录和翻译版本。

The program is then compiled and instructs the computer processing unit (CPU) like so.
然后,该程序将被编译,并像这样指示计算机处理单元(CPU)。

For the purposes of this example, the concepts were heavily simplified. To learn more about computer architecture take a look here.
出于本示例的目的,概念被大大简化。 要了解有关计算机体系结构的更多信息,请 在这里查看 。
This article will not get into the nuances of biology, computer science, quantum theory, or the meaning of life but will highlight the inner workings of malware to conceptualize overlapping properties in biology.
本文将不涉及生物学,计算机科学,量子理论或生命意义的细微差别,而是将重点介绍恶意软件的内部工作原理,以概念化生物学中的重叠特性。
是机器还是动物 (Is It Machine or Animal)
It wasn’t until the invention of the Electron Microscope in the 1930s that equipped us with the capability to visualize viral structures for the first very time. The commonly illustrated Bacteriophage was one of the first organisms seen by the naked eye.
直到1930年代电子显微镜的发明首次使我们具备可视化病毒结构的能力。 常见的噬菌体是用肉眼看到的最早的生物之一。
While the origins of viruses are a mystery, the study of viral structure, reproduction, and disease may lead to the origins of human life. They are everywhere, whether parasitic in nature or symbiotic, viruses embody life in it’s simplest form, a construct of patterns carved by forces of evolution and mother nature.
尽管病毒的起源是个谜,但对病毒结构,繁殖和疾病的研究可能会导致人类生命的起源。 它们无处不在,无论是自然的还是共生的,病毒都以最简单的形式体现生命,这种生命是由进化力和大自然所刻划而成的。
The head is the helical structure seen in the image, it contains viral DNA ready to be injected into a cell, instructing it to function in a way it was not supposed to, this is the DNA payload.
头部是图像中看到的螺旋结构,它包含准备注入细胞中的病毒DNA,指示其以一种不应有的方式发挥作用,这就是DNA 负载 。

The kill-switch mechanism is the spring-like structure within the tail region, consisting of proteins that forms the mounting and injection mechanism of the virus. There are forms of viruses that are different shapes also, the Bacteriophage is an example of a rod-like virus, while Hepatitis is spherical virus. The shell that gives their shape is called a Capsid, a protein shell which surrounds and protects the nucleic genome. A key structure in preventing detection from white blood cells.
杀灭开关机制是尾部区域内的弹簧状结构,由形成病毒安装和注射机制的蛋白质组成。 各种形式的病毒也具有不同的形状,噬菌体是杆状病毒的一个例子,而肝炎是球形病毒。 赋予其形状的壳称为衣壳 ,一种围绕并保护核酸基因组的蛋白质壳。 防止白细胞检测的关键结构。

Proteins are the basic building block of any living organism, it is a chain of four nucleic acids with multiple permutations. Similarily, in computer programs — there are only 0s and 1s, these come together not to form a protein, but to execute instructions on a computer.
蛋白质是任何生物的基本组成部分,它是由四个具有多个排列的核酸组成的链。 类似地,在计算机程序中-只有0和1,它们在一起不是形成蛋白质,而是在计算机上执行指令。
多态机器 (The Polymorphic Machine)

Biological viruses can have multiple genetic mutations that result in viral variants, this is a reason why we can be infected with influenza every year, it’s a virus that constantly mutates, essentially changing it’s DNA to infect hosts over and over again.
生物病毒可以具有多种遗传突变,从而导致病毒变异。这就是为什么我们每年都会感染流感的原因,这是一种不断变异的病毒,本质上是改变其DNA来一次又一次地感染宿主。
Malware is similar, it’s common for malware authors to use other pieces of source code, and modify it to make a new type of malware. There’s even malware written called polymorphic malware that has an ability to change it’s viral signature, consistently infecting the system. It also has an ability to stay hidden from anti-virus software to infect the device repeatedly.
恶意软件与此类似,对于恶意软件作者来说,使用其他源代码并对其进行修改以生成新型恶意软件是很常见的。 甚至有一种被称为多态恶意软件的恶意软件 ,可以改变其病毒特征,从而持续感染系统。 它还具有对防病毒软件隐藏的功能,从而可以反复感染设备。
“留下了赎金记录” (“A ransom note was left behind”)
The Dharma Ransomware was a variant of ransomware that evolved into 30 different variants used in many ransomware attacks seen today. Also known as CrySIS, Dharma is a popular malware responsible for ransomware attacks in the first quarter of 2019.
Dharma勒索软件是勒索软件的一种变体,已演变成如今在许多勒索软件攻击中使用的30种不同变体 。 Dharma也被称为CrySIS ,它是一种流行的恶意软件,于2019年第一季度负责勒索软件攻击。
The malware sample we’ll use for this comparison is called Stuxnet. A malicious program that infected nuclear power plants. This malware is particularly interesting because it used four zero-day vulnerabilities to infect hosts.
我们将用于此比较的恶意软件样本称为Stuxnet 。 感染核电站的恶意程序。 该恶意软件特别有趣,因为它使用了四个零日漏洞来感染主机。

A zero-day is an computer vulnerability that is unknown to any party, essentially a secret weapon only used by those who know or have information about it.
零日 是一个计算机漏洞,它是未知的任何一方,基本上是一个秘密武器仅用于那些谁知道或有关于它的信息。
It was transmitted through USB, once it finds an environment that checks all the boxes, it will drop a vulnerable library and malicious code to hide itself, propagate, and damage it’s target device. A sophisticated program also known as a worm.
它是通过USB传输的,一旦找到可以检查所有框的环境,它将丢弃易受攻击的库和恶意代码以隐藏自身,传播并损坏其目标设备。 一个复杂的程序,也称为蠕虫。
A worm is a malicious, self-replicating program that does not require human assistance once started.
蠕虫 是一种恶意的,自我复制的程序一旦启动,不需要人的帮助。
Stuxnet的目标-核电站 (The Target of Stuxnet — Nuclear Power Plants)
SCADA systems to be specific. Systems responsible for industrial processes and literally airgapped from the internet because of how critical these systems are.
具体的SCADA系统。 由于这些系统的重要性 ,因此负责工业过程并实际上与Internet 隔离的系统。

This malware is highly complex, the mechanisms it used for the infection resembled behavior of biological viruses. This includes:
该恶意软件非常复杂,其用于感染的机制类似于生物病毒的行为。 这包括:
- Transmission (Vulnerable DLL) 传输(易受攻击的DLL)
- Dormancy (Rootkit) Hibernate(Rootkit)
- Evasion from immunity (Packing and Obfuscation) 逃避免疫力(包装和混淆)
- Specificity of host environment (Windows 7 and older) 主机环境的特殊性(Windows 7和更低版本)
We’ll reverse engineer the executable to provide a deeper understanding of these mechanisms and how they correlate.
我们将对可执行文件进行反向工程,以更深入地了解这些机制以及它们之间的关系。
功能特点 (Functional Characteristics)
We start by using a technique called basic static analysis to break open the dropper. The dropper contains all the functions Stuxnet required to run when executed on a target computer.
我们首先使用一种称为“ 基本静态分析”的技术来打开吸管。 删除程序包含Stuxnet在目标计算机上执行时需要运行的所有功能。
滴管和有效载荷 (The Dropper and Payload)
Computer malware is dynamic, it uses a variety of attack vectors to run it’s payload, a common technique is with a dropper, this is used to inject it’s instructions onto a host. To compare, a virus will inject it’s DNA into a cell, it will then add itself to the host genome, masking itself, and tricking the cell to transcribe and translate viral proteins for replication. This worm-like process does not require human interaction, the viral components will naturally come together, bind to internal components and spread to other cells.
计算机的恶意软件是动态的,它采用了多种攻击向量的运行它的有效载荷,一个常用的方法是用滴管 ,这是用来 将其说明注入主机。 相比之下,病毒会将其DNA注入细胞,然后将其添加到宿主基因组中,掩盖自身,并诱使细胞转录和翻译病毒蛋白以进行复制。 这种蠕虫状的过程不需要人为干预,病毒成分自然会聚在一起,与内部成分结合并扩散到其他细胞。

Malware does this too, it can drop files onto the device and duplicate itself across different computers.
恶意软件也这样做,它可以将文件拖放到设备上并在不同计算机上复制自身。
This example shows the mechanism in which a type of spherical virus (Hepatitis) infects a cell by fusing through it’s membrane, it will then inject it’s DNA and use it to create protein components for replication.
这个例子说明了一种机制,其中一种球形病毒(肝炎)通过融合在细胞膜上来感染细胞,然后将其注射到DNA中,并使用它来创建蛋白质成分进行复制。
A key step in this process is the fact that the CEACAM-1 receptor protein binds to a spike protein on the hepatitis virus. This is a form of receptor that tells a virus to drop it’s payload and infect it’s target. Your cells has thousands of receptors on the outside of the cell that are unique to a type of function — Similar to how computers use ports to communicate information. Learn more about cell receptors here.
该过程中的关键步骤是CEACAM-1受体蛋白与肝炎病毒上的刺突蛋白结合的事实。 这是一种受体形式,它告诉病毒丢弃有效载荷并感染其目标。 您的细胞在细胞的外部具有成千上万种功能类型所特有的受体,类似于计算机如何使用端口来传递信息。 在此处 了解有关细胞受体的更多信息 。
滴管和有效载荷 (The Dropper and Payload)
Let’s take a look at the dropper executable in our Windows 7 environment.
让我们看一下Windows 7环境中的dropper可执行文件。
We’ll first start disassembling how the infection is dropped onto the machine, the mechanisms that scans for a specific host environment and how the virus hides the infection. The following function polls device data so it can understand the architecture the machine is running.
我们首先将开始分解感染如何掉到机器上,扫描特定主机环境的机制以及病毒如何隐藏感染。 以下函数可轮询设备数据,以便可以了解机器正在运行的体系结构。
“Is the victim computer running Windows XP, Windows 7, or older?”
“受害者计算机运行的是Windows XP,Windows 7或更早版本吗?”
If a target windows version is found, the malware will continue the execution, if it’s not compatible — will sterilize itself.
如果找到目标Windows版本,则恶意软件将继续执行(如果不兼容)-对其进行自我消毒。

The exact version of Windows Stuxnet targets is VER_PLATFORM_WIN32_NT 2. The documentation for the Windows API is seen below.
Windows Stuxnet目标的确切版本是VER_PLATFORM_WIN32_NT 2 。 Windows API的文档如下所示。
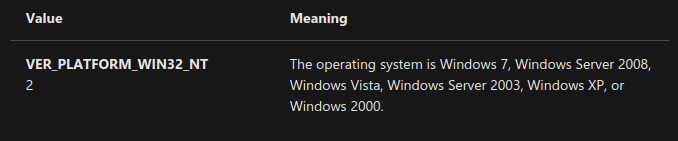
For malware to work, it needs the right environment, libraries, and versions of software for the infection to bear any fruit. An infection attacking Windows only devices via this mechanism will never work on MacOS, simply because their OS and architecture are completely different.
为了使恶意软件正常工作,需要正确的环境,库和软件版本,感染才能取得成果。 通过这种机制攻击仅Windows设备的感染将无法在MacOS上运行,仅因为它们的操作系统和体系结构完全不同。
Aside from packing and encrypting itself, Stuxnet also used a rootkit to hide it’s processes and avoid detection.
除了打包和加密本身之外,Stuxnet还使用rootkit隐藏其进程并避免检测。
捉迷藏 (Hide and Seek)
Packing and obfuscation is another common technique employed by malware writers to evade anti-virus software. It will encrypt itself to make it completely invisible from the immune response of windows anti-virus.
打包和混淆是恶意软件编写者用来逃避防病毒软件的另一种常用技术。 它将对其进行加密,使其完全不受Windows防病毒软件的免疫React影响。
Here’s an example of encrypted functions used by Stuxnet to avoid detection and disassembly.
这是Stuxnet用来避免检测和反汇编的加密函数的示例。

The following shows the entropy (overall chaos) of the file. The more inconsistent the data, the more “random” the file is, this helps reverse engineers understand if a file is encrypted or not.
下面显示了文件的熵(总体混乱)。 数据越不一致,文件越“随机”,这有助于反向工程师了解文件是否已加密。


In the human body, it’s tricky for your defenses to detect viruses depending on the type it’s put up against. There are some forms of deadly viruses that will constantly change their DNA. A mechanism used by malware writers also.
在人体中,根据防御类型来检测病毒是很困难的。 有些致命病毒会不断改变其DNA 。 恶意软件编写者还使用一种机制。
The human body is a product of millions and millions of years of evolution. Technology is constantly evolving and converging with the physical world, as they overlap, the question of what it means to be alive intensifies.
人体是数百万年进化的产物。 随着技术的不断交叠,技术在不断发展并与物理世界融合,人们对其生存的意义的问题愈演愈烈。
These observations may be a product of sheer coincidence, but there is always a small chance it might not be. We may never know.
这些观察结果可能是巧合的产物,但总有可能并非如此。 我们可能永远不会知道。
Computer Viruses, Artificial Life and Evolution by Mark Ludwig
Mark Ludwig的计算机病毒,人工生命与进化
Principles of Virology 4th Edition Volume 2 by Jane Flint, Vincent R. Racaniello, Glenn F. Rall, and Anna Marie Skalka
病毒学原理第四版第2卷,简·弗林特(Jane Flint),文森特·R·拉卡尼洛(Vincent R. Racaniello),格伦·F·拉尔(Glenn F. Rall)和安娜·玛丽·斯卡卡(Anna Marie Skalka)
Practical Malware Analysis The Hands-On Guide to Dissecting Malicious Software by Michael Sikorski and Andrew Honig
实用恶意软件分析Michael Sikorski和Andrew Honig编写的“剖析恶意软件动手指南”
Stuxnet Malware Analysis Paper by Amr Thabet
Amr Thabet的 Stuxnet恶意软件分析论文
工控 恶意软件





















 755
755

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








