aes256位加密
AES (Advanced Encryption Standard) is the most widely used symmetric encryption algorithm. AES is used in a wide array of applications that include the encryption of data at rest, and secure file transfer protocols like HTTPS.
AES(高级加密标准)是使用最广泛的对称加密算法。 AES用于各种各样的应用程序中,包括静态数据的加密以及安全文件传输协议(例如HTTPS)。
AES is the successor to DES. The Data Encryption Standard (DES) is a symmetric encryption algorithm that was developed at IBM. Back in the day, DES used to be the de facto encryption algorithm. However, it used a 56-bit key, and as technology progressed attacks against it started to become more plausible. Eventually, DES was deemed too insecure for continued use. The community transitioned to triple DES (which is still around today). In essence, triple DES is DES performed 3 times consecutively. As one might expect, triple DES is 3 times more secure than just plain DES. However, it’s also 3 times slower.
AES是DES的后继产品。 的 数据加密标准(DES)是IBM开发的对称加密算法。 过去,DES曾经是事实上的加密算法。 但是,它使用了56位密钥,并且随着技术的进步,针对它的攻击开始变得更加合理。 最终,DES被认为过于安全,无法继续使用。 社区过渡到三重DES (至今仍然存在)。 本质上,三重DES是连续执行3次的DES。 如人们所料,三重DES的安全性是普通DES的3倍。 但是,它也慢了3倍。
The US government held a competition to come up with an alternative to triple DES. In the end, Rijndael, written by the two Belgian cryptologists Vincent Rijmen and Joan Daemen, was chosen for its performance and its ease of implementation on both hardware and software, as well as its level of security. Rijndael became the Advanced Encryption Standard for the US, and ultimately for the rest of the world as well.
美国政府举行了一场竞赛,提出了替代三重DES的替代方案。 最后,由两位比利时密码学家Vincent Rijmen和Joan Daemen撰写的Rijndael,由于其性能以及在硬件和软件上的易于实现性以及安全级别而被选中。 Rijndael成为美国乃至世界其他地区的高级加密标准 。
AES加密算法 (AES Encryption Algorithm)
Suppose Bob wanted to send a message to Alice. Bob’s unencrypted message is first broken down into 128-bit chunks. The bytes (16 in all) in a given chunk are then organized as a 4x4 matrix.
假设鲍勃想向爱丽丝发送一条消息。 Bob的未加密消息首先被分解为128位块。 然后将给定块中的字节(总共16个)组织为4x4矩阵。
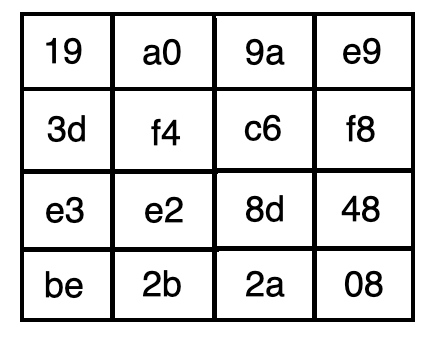
The block is passed through the following sequence of steps a total of x times, where x depends on the size of the cypher key.
该块总共经过x次以下步骤序列,其中x取决于密码密钥的大小。
- Substitute Bytes 替代字节
- Shift Rows 排行
- Mix Columns 混合列
- Add Round Key 添加回合密钥
替代字节 (Substitute Bytes)
In this step, each element in the matrix is mapped to the corresponding byte in the Rijndael S-box.
在此步骤中,矩阵中的每个元素都映射到Rijndael S-box中的相应字节。
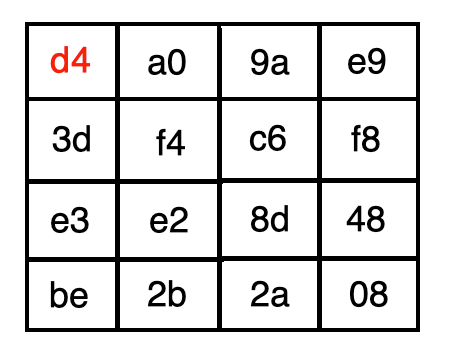
For example, the element in the top left corner is mapped to d4 since the first hexadecimal is 1 and the other hexadecimal is 9.
例如,左上角的元素映射到d4因为第一个十六进制为1 ,另一个十六进制为9 。

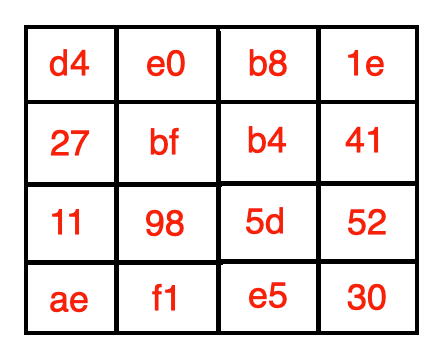
Repeating the process for every element, we obtain the following matrix:
对每个元素重复该过程,我们获得以下矩阵:
排行 (Shift Rows)
In the second step, we rotate each element x elements (bytes) to the left, where x is the index of the row.
在第二步中,我们将每个元素向左旋转x个元素(字节),其中x是该行的索引。
- Row 0 — Shift left 0 bytes (i.e. don’t shift) 第0行-向左移位0个字节(即不移位)

- Row 1 — Shift left 1 byte 第1行-左移1个字节


- Row 2 — Shift left 2 bytes 第2行-左移2个字节
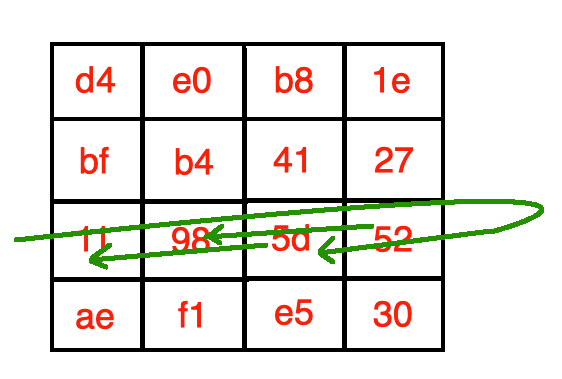
- Row 3 — Shift left 3 bytes 第3行-左移3个字节

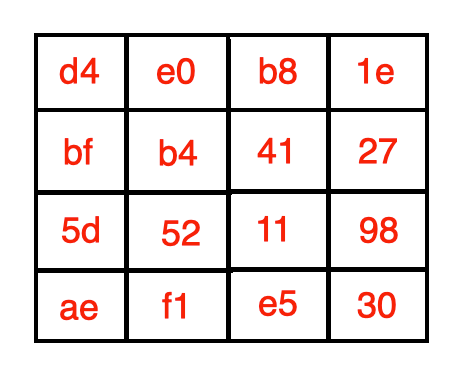
We finish with the following matrix:
我们完成以下矩阵:

混合列 (Mix Columns)
We multiply every column by a predefined matrix.
我们将每列乘以预定义的矩阵。



It’s important to note that this is not regular matrix multiplication. If any term is greater than 2 to the power of 8, we divide the polynomial by the Galois irreducible polynomial:
重要的是要注意,这不是规则的矩阵乘法。 如果任何一项大于2的8的幂,我们将多项式除以Galois不可约多项式:

Let’s walk through how we’d go about calculating the multiplication of d4 and 02. We start off by converting every bit into its binary arithmetic equivalent (polynomial form).
让我们来看一下如何计算d4和02的乘法。 我们首先将每个位转换为其等效的二进制算术形式(多项式形式)。


We multiply the two.
我们将两者相乘。


Since the product is greater than 2 to the power of 8, we divide it by the irreducible polynomial.
由于乘积大于2乘以8的幂,我们将其除以不可约的多项式。


We repeat the process for every element, and obtain the following matrix:
我们对每个元素重复此过程,并获得以下矩阵:

添加回合密钥 (Add Round Key)
In this step, we perform a bitwise XOR operation between the columns of the matrix we obtained in the preceding step and the Round Key. In the first iteration, the Round Key is the first 128 bits of the cypher key.
在这一步中,我们在上一步中获得的矩阵的列与Round Key之间执行按位XOR运算。 在第一次迭代中,“ 回合密钥”是密码密钥的前128位。




Repeating the process for the remaining columns gives us:
对其余的列重复该过程将为我们提供:

The preceding matrix is used as the input to the next round, and the process itself is repeated for another x rounds.
前面的矩阵用作下一个回合的输入,并且过程本身又重复了x个回合。
Note: The final round excludes the Mix Columns step.
注意 :最后一轮不包括“ 混合列”步骤。
AES密钥时间表 (AES Key Schedule)
The process of computing a new key for the following rounds is known as the Key Schedule. As we mentioned previously, the number of rounds depends on the length of the initial cypher key.
在接下来的回合中计算新密钥的过程称为密钥时间表 。 如前所述,轮数取决于初始密码密钥的长度。
- 128 bit key = 10 rounds 128位密钥= 10轮
- 192 bit key = 12 rounds 192位密钥= 12发
- 256 bit key = 14 rounds 256位密钥= 14轮
Note: In all other regards, the algorithm is exactly the same.
注意 :在所有其他方面,算法完全相同。
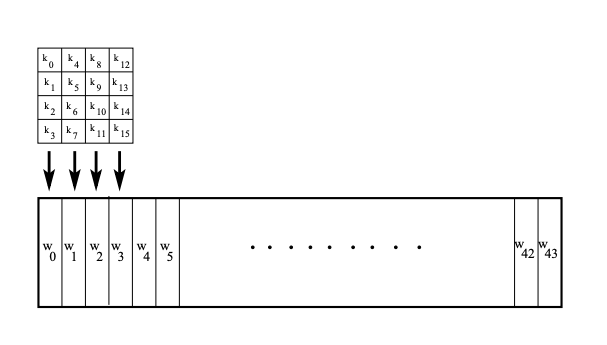
In the same manner as the 128-bit input block is arranged in the form of a state array, the algorithm arranges the first 16 bytes of the encryption key in the form of a 4 × 4 matrix of bytes. The following figure shows the four words of the original 128-bit key being expanded into a key schedule consisting of 4 x 11 = 44 words. The first four bytes of the encryption key constitute the word w0, the next four bytes the word w1, and so on up to w3.
与以状态数组的形式排列128位输入块的方式相同,该算法以4×4字节矩阵的形式排列加密密钥的前16个字节。 下图显示了将原始128位密钥的四个单词扩展为一个包含4 x 11 = 44个单词的密钥时间表。 加密密钥的前四个字节构成单词w0,后四个字节构成单词w1,依此类推,直到w3。
Let’s say that we have the four words of the round key for the ith round.
假设我们有第四个回合的回合密钥的四个单词。

We need to determine the words that will be used in the next round.
我们需要确定将在下一轮中使用的单词。

The first word in this sequence is computed as follows:
该序列中的第一个单词的计算如下:
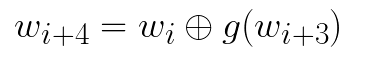
where the function g consists of the following three steps:
其中函数g包含以下三个步骤:
- Perform a one-byte circular rotation on the 4-byte word. 对4字节字执行一字节循环旋转。
- Substitute each byte in the word using the 16 × 16 lookup table 使用16×16查找表替换单词中的每个字节
XOR the bytes obtained from the previous step with what is known as a round constant.
将上一步获得的字节与舍入常量进行 XOR运算。
The round constant for the jth round is denoted Rcon[j].
第j轮的轮常数 t表示为Rcon [j] 。

where
哪里


Note: The addition of round constants ruins any symmetries that may have been introduced by the other steps in the algorithm, thus making it harder to crack.
注意 :舍入常数的添加会破坏算法中其他步骤可能引入的任何对称性,从而使其更难破解。

The first operation consists of rotating the bytes.
第一个操作包括旋转字节。


Then, we perform byte substitution using the lookup table.
然后,我们使用查找表执行字节替换。


After substituting the remaining bytes, we obtain the following vector.
替换剩余字节后,我们获得以下向量。

Finally, we perform a bitwise XOR operation between the vector, the first word and Rcon[1] to obtain the new word.
最后,我们在向量,第一个单词和Rcon [1]之间执行按位XOR运算以获得新单词。
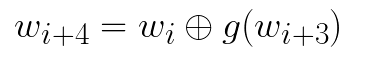

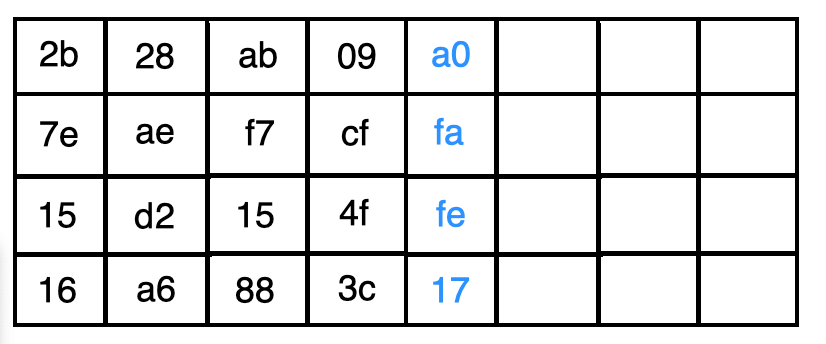
We then proceed to compute the remaining words in the Round Key.
然后,我们继续计算Round Key中的剩余单词。

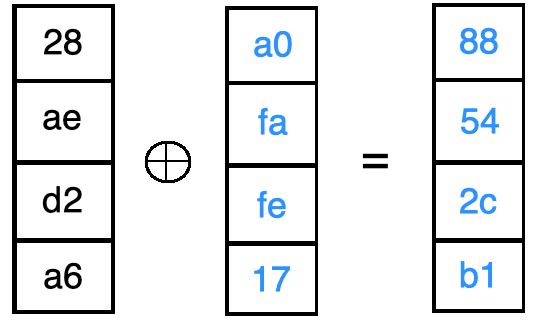






The new 4x4 matrix (Round Key) is used for the Add Key step of the proceeding round.
新的4x4矩阵(圆键)用于进行下一轮的“ 添加键”步骤。
The process is repeated for each of the 10 rounds.
每十回合重复该过程。
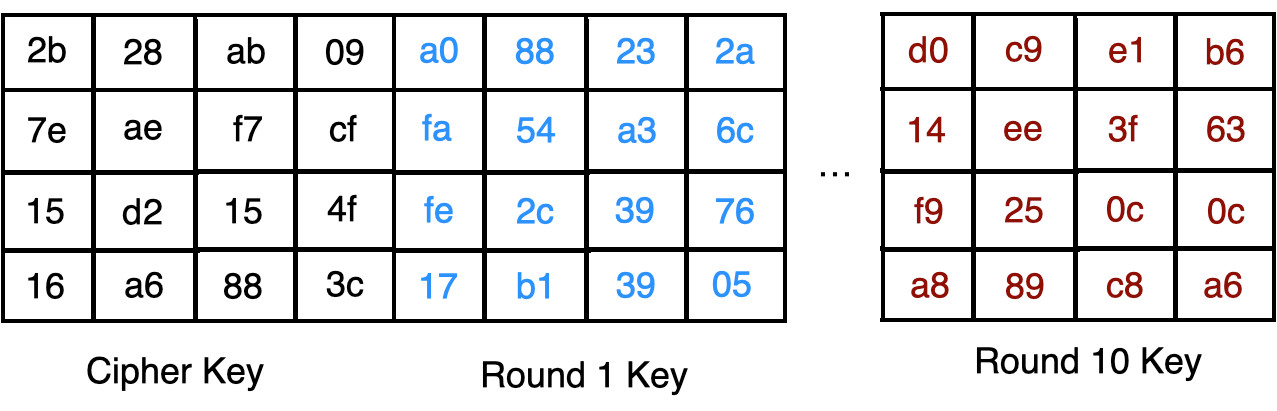
翻译自: https://towardsdatascience.com/aes-encryption-256-bit-a9ae49cde0b6
aes256位加密





















 5363
5363











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








