“1、网页查看,2、有道翻译简单实现源码,3、JS解密(详解),4、python实现JS解密后的完整代码,4.1、实现效果,5、JS解密后完整代码升级版,5.1、实现效果!”

1、网页查看
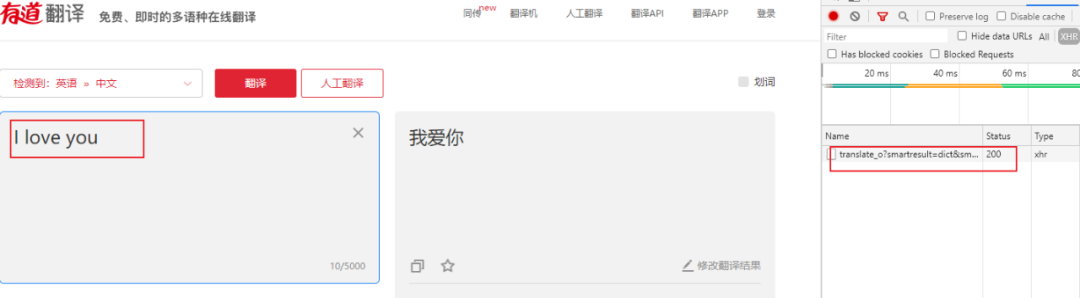
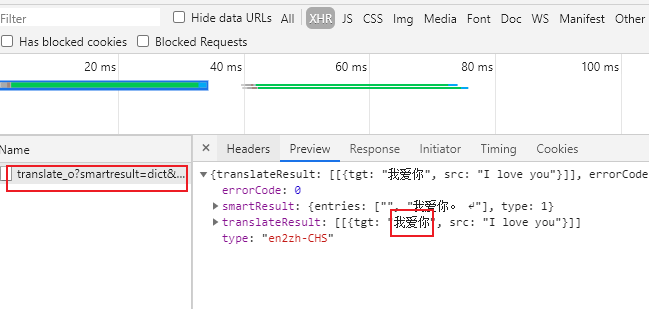
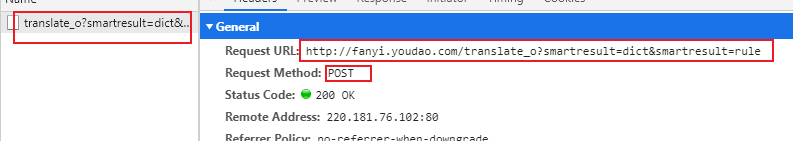
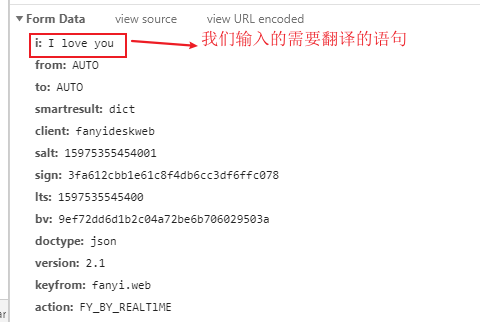
2、有道翻译简单实现源码
import requests#请求头#headers不能只有一个User-Agent,因为有道翻译是有一定的反扒机制的,所以我们直接全部带上headers = { "Accept": "application/json, text/javascript, */*; q=0.01", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "keep-alive", "Content-Length": "244", "Content-Type": "application/x-www-form-urlencoded; charset=UTF-8", "Cookie": "OUTFOX_SEARCH_USER_ID=-1506602845@10.169.0.82; JSESSIONID=aaaUggpd8kfhja1AIJYpx; OUTFOX_SEARCH_USER_ID_NCOO=108436537.92676207; ___rl__test__cookies=1597502296408", "Host": "fanyi.youdao.com", "Origin": "http://fanyi.youdao.com", "Referer": "http://fanyi.youdao.com/", "user-agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36", "X-Requested-With": "XMLHttpRequest",}#提交参数params = { "i": "I love you", "from": "UTO", "to": "AUTO", "smartresult": "dict", "client": "fanyideskweb", "salt": "15975022964104", "sign": "7b7db70e0d1a786a43a6905c0daec508", "lts": "1597502296410", "bv": "9ef72dd6d1b2c04a72be6b706029503a", "doctype": "json", "version": "2.1", "keyfrom": "fanyi.web", "action": "FY_BY_REALTlME",}url = "http://fanyi.youdao.com/translate_o?smartresult=dict&smartresult=rule"#发起POST请求response = requests.post(url=url,headers=headers,data=params).json()print(response)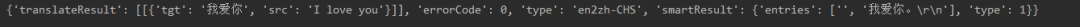
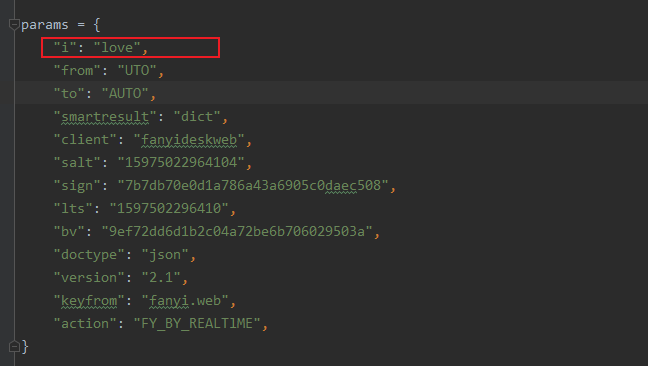

原因
我们在有道翻译重新翻译,会发起新的POST请求,而每次请求所带的参数值会有所不同,如果想要真正实现有道翻译功能,就要找到这四个参数值的生成方式,然后用python 实现同样的功能才行。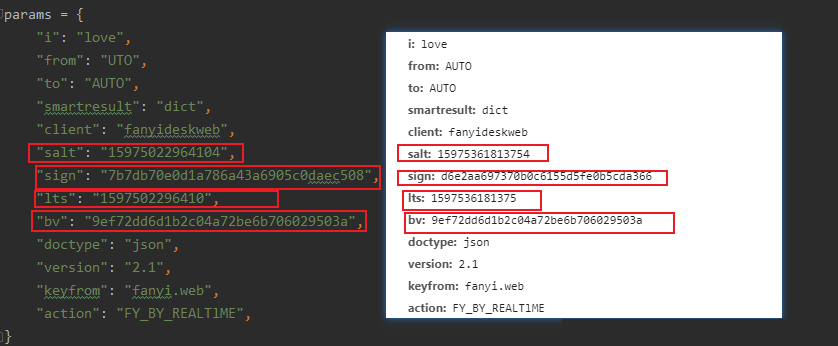
3、JS解密(详解)
Ctrl+Shift+f进行搜索,输入sign

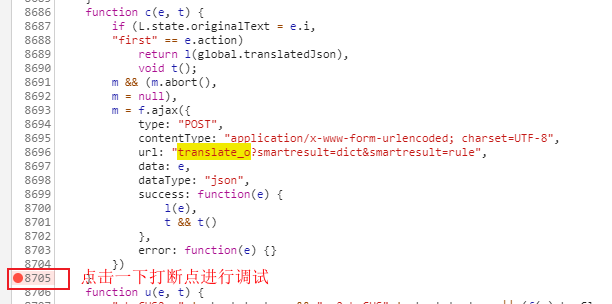
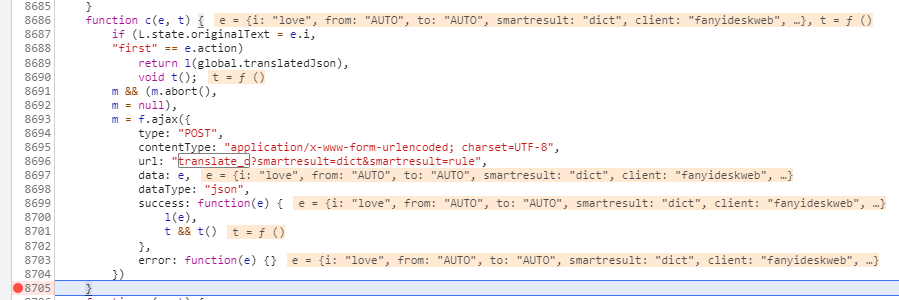
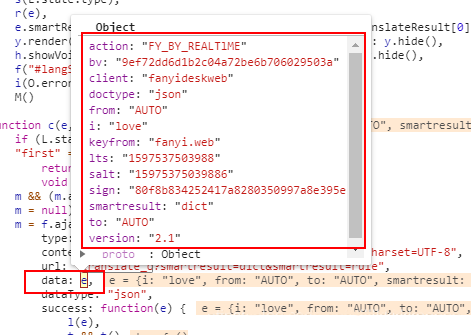
但由于我们是调试模式,可以返回到上一步,点击如下按钮。
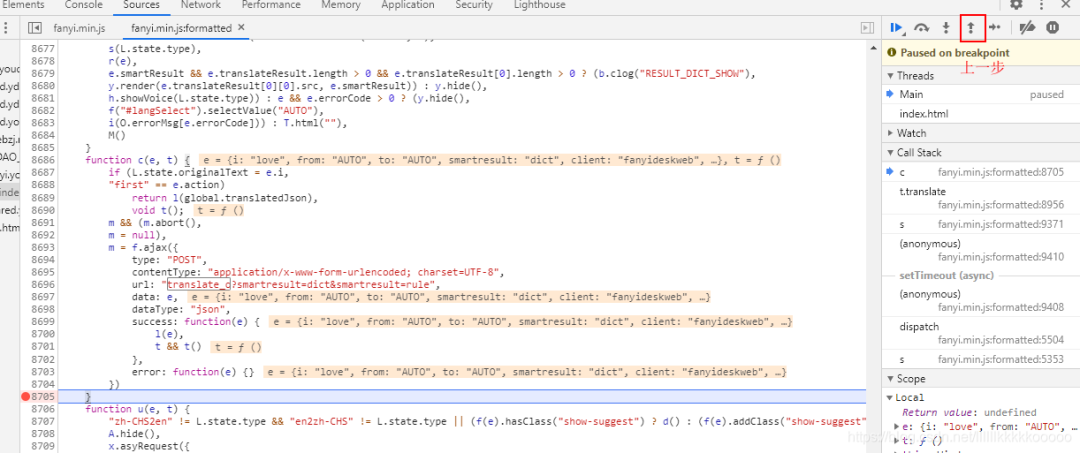
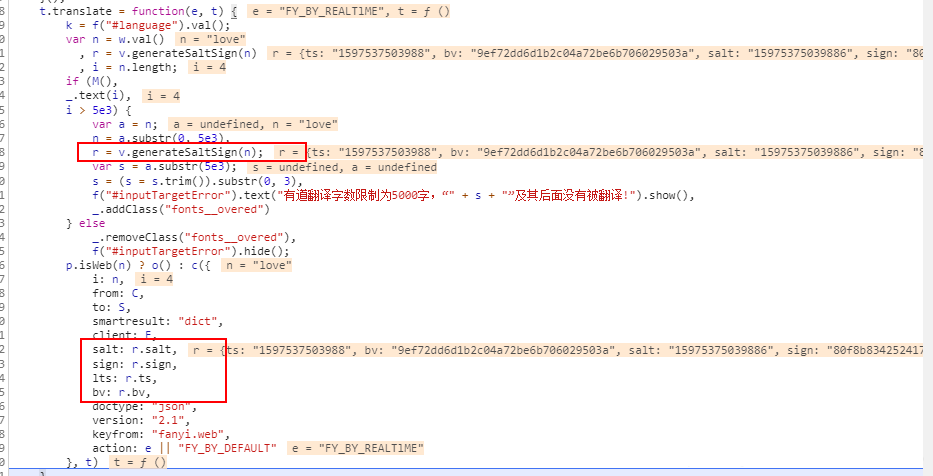
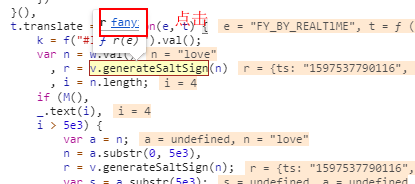
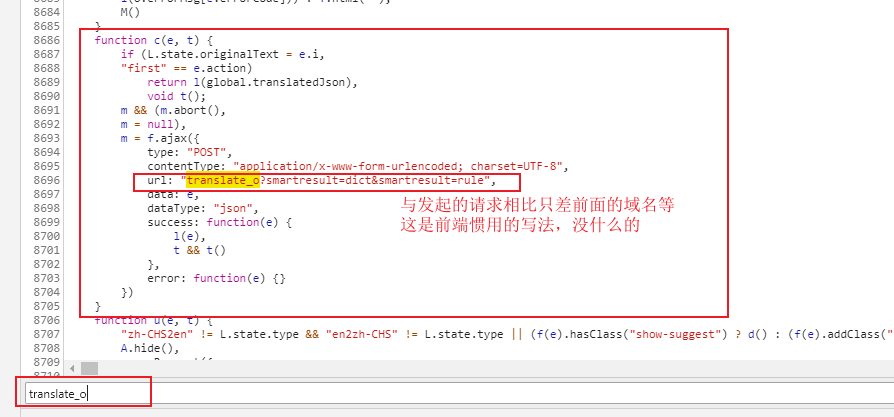
可以发现这里就是加密的地方
复制这段js代码,我们需要使用python代码来实现。
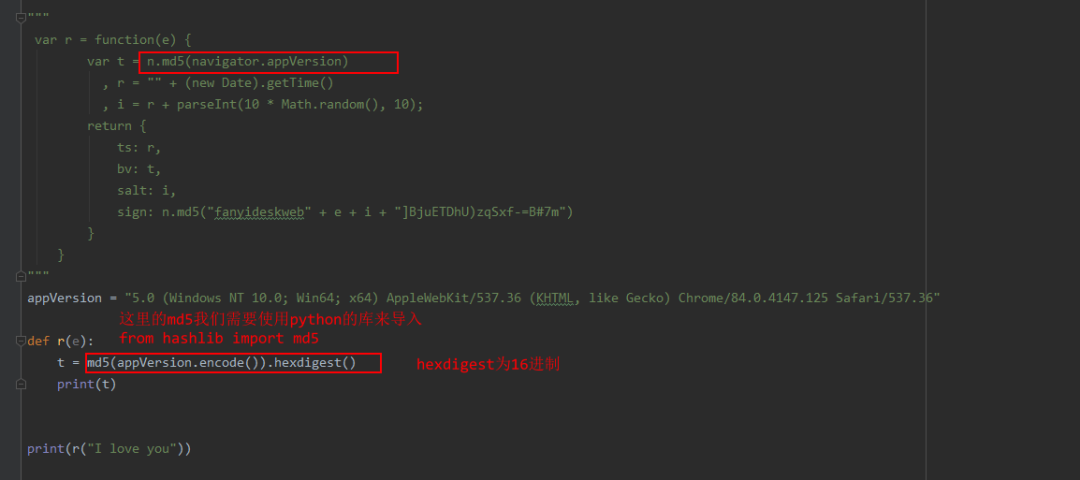
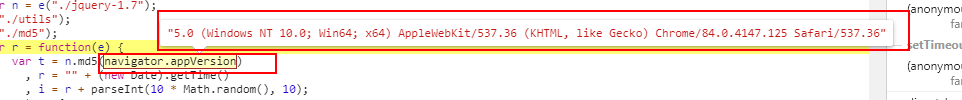
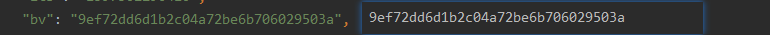
注意这里翻译内容不同其bv也是不同的。
接下来看its,用Python实现
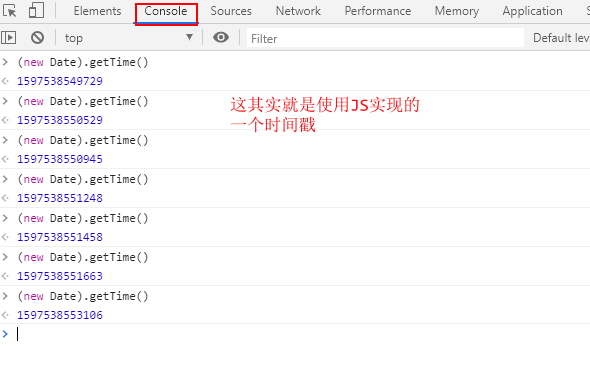

这就ok了!
乘以1000转化为int舍弃小数位再转化为字符串,因为JS里是字符串
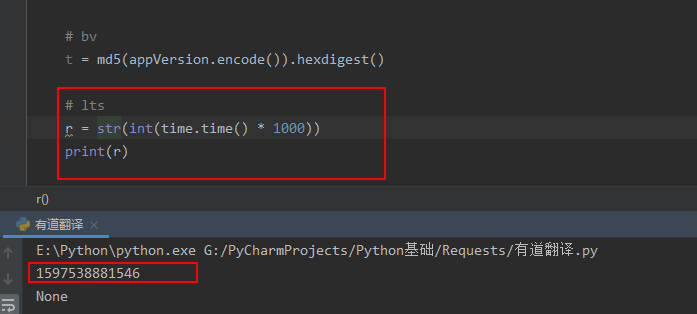

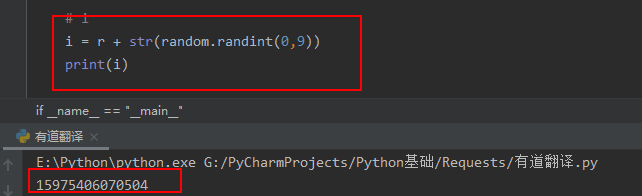

温馨提示:
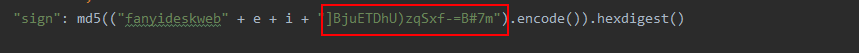
4、python实现JS解密后的完整代码
import requestsfrom hashlib import md5import timeimport random#请求地址url = "http://fanyi.youdao.com/translate_o?smartresult=dict&smartresult=rule"appVersion = "5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36"headers = { "Accept": "application/json, text/javascript, */*; q=0.01", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "keep-alive", "Content-Length": "244", "Content-Type": "application/x-www-form-urlencoded; charset=UTF-8", "Cookie": "OUTFOX_SEARCH_USER_ID=-1506602845@10.169.0.82; JSESSIONID=aaaUggpd8kfhja1AIJYpx; OUTFOX_SEARCH_USER_ID_NCOO=108436537.92676207; ___rl__test__cookies=1597502296408", "Host": "fanyi.youdao.com", "Origin": "http://fanyi.youdao.com", "Referer": "http://fanyi.youdao.com/", "user-agent": appVersion, "X-Requested-With": "XMLHttpRequest",}def r(e): # bv t = md5(appVersion.encode()).hexdigest() # lts r = str(int(time.time() * 1000)) # i i = r + str(random.randint(0,9)) return { "ts": r, "bv": t, "salt": i, "sign": md5(("fanyideskweb" + e + i + "]BjuETDhU)zqSxf-=B#7m").encode()).hexdigest() }def fanyi(word): data = r(word) params = { "i": word, "from": "UTO", "to": "AUTO", "smartresult": "dict", "client": "fanyideskweb", "salt": data["salt"], "sign": data["sign"], "lts": data["ts"], "bv": data["bv"], "doctype": "json", "version": "2.1", "keyfrom": "fanyi.web", "action": "FY_BY_REALTlME", } response = requests.post(url=url,headers=headers,data=params) #返回json数据 return response.json()if __name__ == "__main__": while True: word = input("请输入要翻译的语句:") result = fanyi(word) #对返回的json数据进行提取,提取出我们需要的数据 r_data = result["translateResult"][0] print(r_data[0]["src"]) print(r_data[0]["tgt"])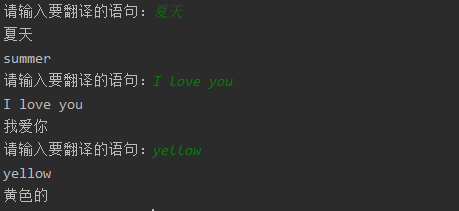
import requestsfrom hashlib import md5import timeimport random#请求地址url = "http://fanyi.youdao.com/translate_o?smartresult=dict&smartresult=rule"appVersion = "5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36"headers = { "Accept": "application/json, text/javascript, */*; q=0.01", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "keep-alive", "Content-Length": "244", "Content-Type": "application/x-www-form-urlencoded; charset=UTF-8", "Cookie": "OUTFOX_SEARCH_USER_ID=-1506602845@10.169.0.82; JSESSIONID=aaaUggpd8kfhja1AIJYpx; OUTFOX_SEARCH_USER_ID_NCOO=108436537.92676207; ___rl__test__cookies=1597502296408", "Host": "fanyi.youdao.com", "Origin": "http://fanyi.youdao.com", "Referer": "http://fanyi.youdao.com/", "user-agent": appVersion, "X-Requested-With": "XMLHttpRequest",}def r(e): # bv t = md5(appVersion.encode()).hexdigest() # lts r = str(int(time.time() * 1000)) # i i = r + str(random.randint(0,9)) return { "ts": r, "bv": t, "salt": i, "sign": md5(("fanyideskweb" + e + i + "]BjuETDhU)zqSxf-=B#7m").encode()).hexdigest() }def fanyi(word): data = r(word) params = { "i": word, "from": "UTO", "to": "AUTO", "smartresult": "dict", "client": "fanyideskweb", "salt": data["salt"], "sign": data["sign"], "lts": data["ts"], "bv": data["bv"], "doctype": "json", "version": "2.1", "keyfrom": "fanyi.web", "action": "FY_BY_REALTlME", } response = requests.post(url=url,headers=headers,data=params) return response.json()if __name__ == "__main__": #打开需要翻译的文章 with open("文章.txt",mode="r",encoding="utf-8") as f: #获取文章全部内容 text = f.read() result = fanyi(text) r_data = result["translateResult"] #翻译结果保存 with open("test.txt",mode="w",encoding="utf-8") as f: for data in r_data: f.write(data[0]["tgt"]) f.write('\n') f.write(data[0]["src"]) f.write('\n') print(data[0]["tgt"]) print(data[0]["src"])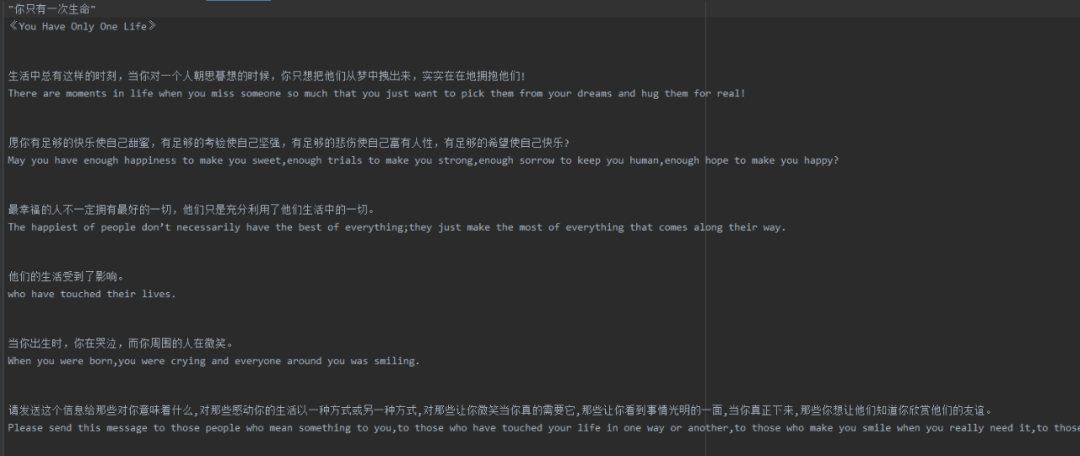
这是保存下来的JS解密代码以上为我Python爬虫JS解密详解用到的手段,如有不足之处或更多技巧,欢迎指教补充。愿本文的分享对您之后爬虫JS解密有所帮助。谢谢~
编辑排版:筱筱 原创:Code皮皮虾






















 644
644











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








