学习地址:
https://www.majiaxueyuan.com/uc/play/65
Oauth2.0的一些简单介绍:
https://blog.csdn.net/qq_28198181/article/details/100523474
如果要处理使用授权码模式
需要配置两个地方:
1.将授权码模式放进去
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.http.HttpMethod;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.AuthenticationProvider;
import org.springframework.security.authentication.dao.DaoAuthenticationProvider;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerSecurityConfigurer;
import org.springframework.security.provisioning.InMemoryUserDetailsManager;
/**
* @author : HYXT_ZouQiJun
* @createTime : 2019/9/3 15:33
* @descrption :
*/
@Configuration
@EnableAuthorizationServer
public class AuthorizationServerConfig extends AuthorizationServerConfigurerAdapter {
//accessToken 过期
private int accessTokenValiditySecond = 60 * 60 * 2; //2小时
private int refreshTokenValiditySecond = 60 * 60 * 24 * 7; // 7 天
//添加商户信息
public void configure(ClientDetailsServiceConfigurer configurer) throws Exception {
//withClient Appid
configurer.inMemory().withClient("yyy_client").secret(passwordEncoder().encode("yyy_secret")) //设置用户 和密码
//这里放入了授权码模式
.authorizedGrantTypes("password","authorization_code","client_credentials","refresh_token").scopes("all") //设置权限类型,用密码,客户端,刷新的token 权限为所有人
.accessTokenValiditySeconds(accessTokenValiditySecond)
.refreshTokenValiditySeconds(refreshTokenValiditySecond);
}
//定义授权和令牌端点和令牌服务
public void configure(AuthorizationServerEndpointsConfigurer endpointsConfigurer){
//刷新令牌时需要的认证管理和用户信息来源
endpointsConfigurer.authenticationManager(authenticationManager()).allowedTokenEndpointRequestMethods(HttpMethod.GET,HttpMethod.POST);
endpointsConfigurer.authenticationManager(authenticationManager());
endpointsConfigurer.userDetailsService(userDetailsService());
}
@Override
public void configure(AuthorizationServerSecurityConfigurer oauthServer) throws Exception {
//允许表单认证
oauthServer.allowFormAuthenticationForClients();
//允许 check_token 访问
oauthServer.checkTokenAccess("permitAll()");
}
@Bean
AuthenticationManager authenticationManager() {
AuthenticationManager authenticationManager = new AuthenticationManager() {
public Authentication authenticate(Authentication authentication) throws AuthenticationException {
return daoAuhthenticationProvider().authenticate(authentication);
}
};
return authenticationManager;
}
@Bean
public AuthenticationProvider daoAuhthenticationProvider() {
DaoAuthenticationProvider daoAuthenticationProvider = new DaoAuthenticationProvider();
daoAuthenticationProvider.setUserDetailsService(userDetailsService());
daoAuthenticationProvider.setHideUserNotFoundExceptions(false);
daoAuthenticationProvider.setPasswordEncoder(passwordEncoder());
return daoAuthenticationProvider;
}
// 设置添加用户信息,正常应该从数据库中读取
@Bean
UserDetailsService userDetailsService() {
InMemoryUserDetailsManager userDetailsService = new InMemoryUserDetailsManager();
userDetailsService.createUser(User.withUsername("user_1").password(passwordEncoder().encode("123456"))
.authorities("ROLE_USER").build());
userDetailsService.createUser(User.withUsername("user_2").password(passwordEncoder().encode("123456"))
.authorities("ROLE_USER").build());
return userDetailsService;
}
@Bean
PasswordEncoder passwordEncoder() {
// 加密方式
PasswordEncoder passwordEncoder = new BCryptPasswordEncoder();
return passwordEncoder;
}
}
2.需要配置一个security,不然会报错
@Component
public class SecurityConfig extends WebSecurityConfigurerAdapter {
//暂时什么都没写
}
3.测试一下
首先需要获取到认证的code 才能通过code 得到token
将程序类启动:
@SpringBootApplication
public class SSOApplication {
public static void main(String[] args) {
SpringApplication.run(SSOApplication.class, args);
}
}
这个连接是自己写了个路径
http://localhost:8080/oauth/authorize?response_type=code&client_id=yyy_client&redirect_uri=http://www.4399.com
访问路径 Security会先让你输入用户名和密码
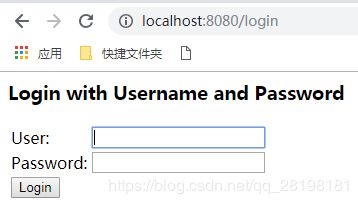
我们将后台写死的user和password
会跳转到我们原来进入的路径。选择允许
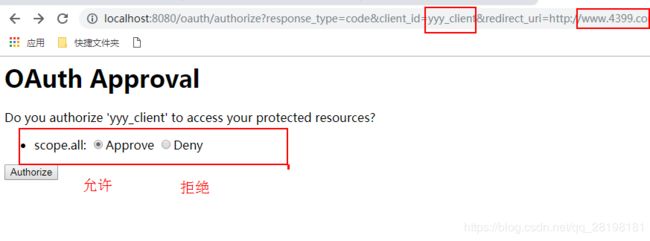
点击认证后会跳转到4399页面 地址栏会附带code
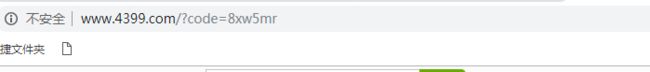
我们通过postman 去访问oauth下的token
http://localhost:8080/oauth/token
如下:
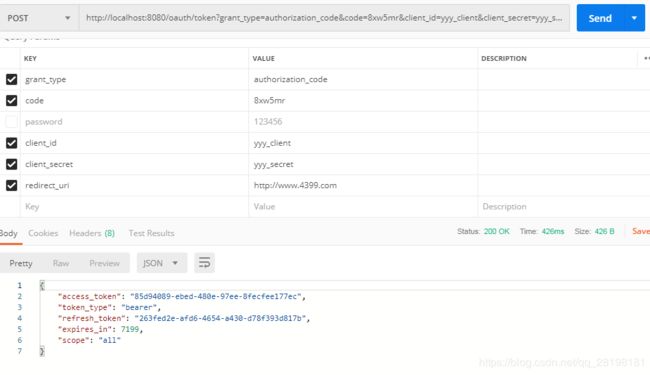
如下得到了token值
注意:token只有一次 如果要下一次的话得重新获取code码
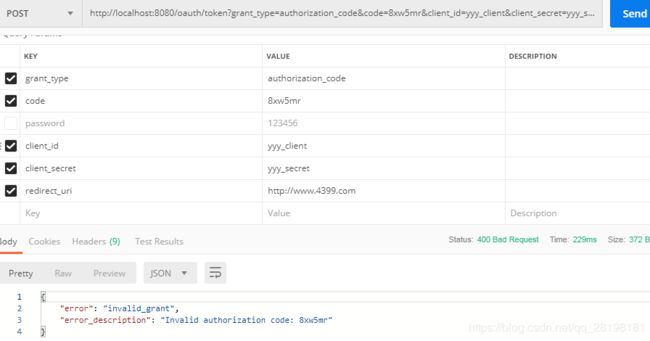
重新从authorize中获取

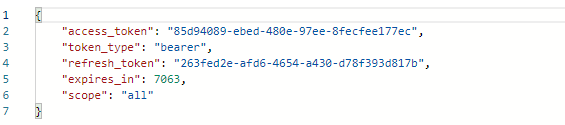
可以看到即便code不一致但是token是一致的
简单记录一下 以后补充现在不会的





















 511
511











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








