【实验说明】
上一个实验是《使用ACL 来预防IP地址欺骗》,但是配置起来相对复杂,本实验我们将使用URPF(Unicast Reverse Path Forwarding)来轻松实现预防部分IP地址欺骗,URPF的知识请查看《Unicast RPF,单播逆向转发》 文章
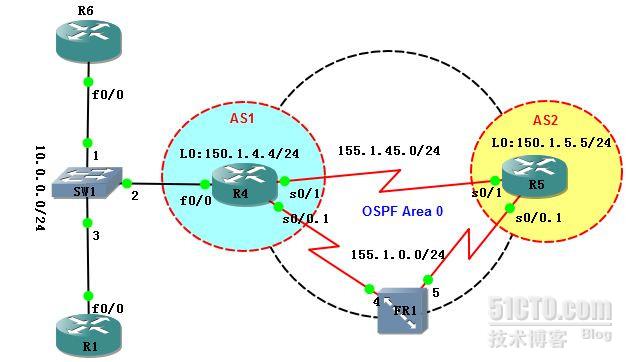
【实验拓扑】
I
OS:c2691-advsecurityk9-mz.124-11.T2.bin
【实验配置步骤】
- 配置上图网络为 IP service 中的“Common Configuration”
- 本实验将启用uRPF检查,但配置特定网络免受检查
- 所有的尝试欺骗都记录日志
- 在R5上创建Loopback1接口,IP地址为150.1.55.55/24,创建loopback2接口,IP地址为150.1.155.155/24
- 不通告上面两个loopback地址到路由协议
- 禁止R4上的BGP,以阻止其接收默认路由
- 在R4上创建 access-list 100 允许150.1.55.0/24网络. 拒绝其他并记录日志
- 在R4上外网口(串口)配置uRPF ,使access-list 100 作为uRPF ACL
【实验配置】
R5:
interface Loopback1
ip address 150.1.55.55 255.255.255.0
interface Loopback2
ip address 150.1.155.155 255.255.255.0
R4:
no router bgp 1
access-list 100 permit ip 150.1.55.0 0.0.0.255
any
access-list 100 deny ip any any log
!
int s0/1
ip verify unicast reverse-path 100
!
int s0/0.1
ip verify unicast reverse-path 100
【
Common Configuration 配置】
|
R1:
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 10.0.0.4
R6:
interface FastEthernet0/0
ip address 10.0.0.6 255.255.255.0
ip route 0.0.0.0 0.0.0.0 10.0.0.4
R4:
interface Loopback0
ip address 150.1.4.4 255.255.255.0
ip ospf network point-to-point
!
interface FastEthernet0/0
ip address 10.0.0.4 255.255.255.0
!
interface Serial0/0
en fram
no sh
!
interface Serial0/0.1 point-to-point
ip address 155.1.0.4 255.255.255.0
frame-relay interface-dlci 405
!
interface Serial0/1
ip address 155.1.45.4 255.255.255.0
clock rate 2000000
!
router ospf 1
router-id 150.1.4.4
network 150.1.4.4 0.0.0.0 area 0
network 155.1.0.4 0.0.0.0 area 0
network 155.1.45.4 0.0.0.0 area 0
!
router bgp 1
bgp router-id 150.1.4.4
neighbor 150.1.5.5 remote-as 2
neighbor 150.1.5.5 ebgp-multihop 255
neighbor 150.1.5.5 update-source Loopback0
|
R5:
interface Loopback0
ip address 150.1.5.5 255.255.255.0
ip ospf network point-to-point
!
interface Serial0/0
encapsulation frame-relay
!
interface Serial0/0.1 point-to-point
ip address 155.1.0.5 255.255.255.0
frame-relay interface-dlci 504
!
interface Serial0/1
ip address 155.1.45.5 255.255.255.0
clock rate 2000000
!
router ospf 1
router-id 150.1.5.5
network 150.1.5.5 0.0.0.0 area 0
network 155.1.0.5 0.0.0.0 area 0
network 155.1.45.5 0.0.0.0 area 0
!
router bgp 2
bgp router-id 150.1.5.5
neighbor 150.1.4.4 remote-as 1
neighbor 150.1.4.4 ebgp-multihop 255
neighbor 150.1.4.4 update-source Loopback0
neighbor 150.1.4.4 default-originate
|
【实验验证】
R5#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
155.1.0.0/24 is subnetted, 2 subnets
C 155.1.0.0 is directly connected, Serial0/0.1
C 155.1.45.0 is directly connected, Serial0/1
150.1.0.0/24 is subnetted, 4 subnets
C 150.1.155.0 is directly connected, Loopback2
C 150.1.5.0 is directly connected, Loopback0
O 150.1.4.0 [110/65] via 155.1.45.4, 00:18:39, Serial0/1
[110/65] via 155.1.0.4, 00:18:39, Serial0/0.1
C 150.1.55.0 is directly connected, Loopback1
R5#ping 150.1.4.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 150.1.4.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/22/52 ms
R5#ping 150.1.4.4 source loopback1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 150.1.4.4, timeout is 2 seconds:
Packet sent with a source address of 150.1.55.55
.....
R4#show ip access-list
*Mar 1 00:17:57.727: %SYS-5-CONFIG_I: Configured from console by console
R4#show ip access
R4#show ip access-lists
Extended IP access list 100
10 permit ip 150.1.55.0 0.0.0.255 any (5 matches)
20 deny ip any any log
R4#show ip int s0/0.1
Serial0/0.1 is up, line protocol is up
Internet address is 155.1.0.4/24
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 1500 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.5
Outgoing access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP fast switching on the same interface is enabled
IP Flow switching is disabled
IP CEF switching is enabled
IP CEF Feature Fast switching turbo vector
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Policy routing is disabled
Network address translation is disabled
BGP Policy Mapping is disabled
WCCP Redirect outbound is disabled
WCCP Redirect inbound is disabled
WCCP Redirect exclude is disabled
IP verify source reachable-via RX, allow default, ACL 100
0 verification drops
5 suppressed verification drops
R5#ping 150.1.4.4 source l2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 150.1.4.4, timeout is 2 seconds:
Packet sent with a source address of 150.1.155.155
.....
R4#show ip access 100
Extended IP access list 100
10 permit ip 150.1.55.0 0.0.0.255 any (5 matches)
20 deny ip any any log (5 matches)
R4#
*Mar 1 00:24:14.719: %SEC-6-IPACCESSLOGDP: list 100 denied icmp 150.1.155.155 -> 150.1.4.4 (0/0), 4 packets
R4#show ip int s0/0.1
Serial0/0.1 is up, line protocol is up
Internet address is 155.1.0.4/24
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 1500 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.5
Outgoing access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP fast switching on the same interface is enabled
IP Flow switching is disabled
IP CEF switching is enabled
IP CEF Feature Fast switching turbo vector
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Policy routing is disabled
Network address translation is disabled
BGP Policy Mapping is disabled
WCCP Redirect outbound is disabled
WCCP Redirect inbound is disabled
WCCP Redirect exclude is disabled
IP verify source reachable-via RX, allow default, ACL 100
5 verification drops
5 suppressed verification drops
转载于:https://blog.51cto.com/haolun/991664





















 328
328











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








