声明:本案例中所有内容仅供个人学习交流,抓包内容、敏感网址、数据接口均已做脱敏处理,严禁用于商业用途和非法用途,否则由此产生的一切后果均与作者无关!
1.接口分析
1.1.load 包
请求类型:GET
说明:返回图片等数据
查询字符串(第一次请求):{
callback: geetest_1741679915326
captcha_id: 8b4a2bef633xxxxxxxxxxxxxx
challenge: 3349bf06-5857-4350-86d8-57ceac68380a
client_type: web
lang: zh-cn
},
查询字符串(验证错误刷新):{
callback: geetest_1741679915326
captcha_id: 8b4a2bef633xxxxxxxxxxxxxx
client_type: web
pt:1
lang: zho
}
响应:{
....
data:{
"lot_number": "8c407ed02e0b423597f51a3b605c9a7a",
"imgs": "",
"ques": [],
...
"gct_path": "/v4/gct/gct4.5axxxxxxxxxxxxx.js",
"pt": "1",
"language": "zh-cn",
"pow_detail": {
"version": "1",
"bits": 12,
"datetime": "2025-03-11T16:10:22.757715+08:00",
"hashfunc": "md5"
},
"payload": "",
"process_token": "",
"payload_protocol": 1
}
}
1.2.verify包
请求类型:GET
说明:验证接口
查询字符串:{
callback: geetest_1741769465581,
captcha_id: 8b4a2bef633xxxxxxxxxxxxxx,
client_type: web,
lot_number: 8c407ed02e0b423597f51a3b605c9a7a,
payload: "",
process_token: "",
payload_protocol: 1,
pt:1,
w:""
}
响应:{
data:{
"result": "success",
"fail_count": 0,
"seccode":{},
"score": "27",
"payload": "",
"process_token":"",
"payload_protocol": 1
}
}
2.w逆向分析
var _ᕸᖄᖗᕷ = {
"passtime": data.passtime,
"userresponse": data.userresponse,
"device_id": "",
"lot_number": options.lotNumber,
"pow_msg": pow.pow_msg,
"pow_sign": pow.pow_sign,
"geetest": "captcha",
"lang": "zh",
"ep": "123",
"biht": "",
"bJv3": "",
"em":[],
"10fb":{"c9c4":"917320"}
};
var _ᖘᖂᖄᕴ = _ᖙᕿᕹᕵ["default"](JSON.stringify(_ᕸᖄᖗᕷ),data);
说明:有个坑是pow_sign开头不是000就一直循环
3.效果
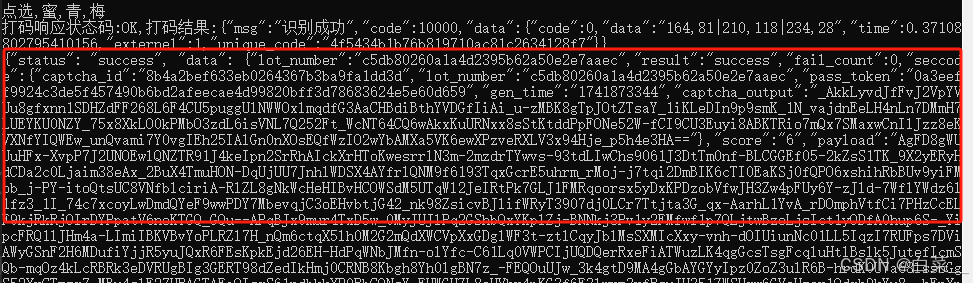





















 3万+
3万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








