内存越界检测工具kasan
KASAN简介
Kasan 是 Kernel Address Sanitizer 的缩写,它是一个动态检测内存错误的工具,主要功能是检查内存越界访问和使用已释放的内存等问题。在Linux-4.0中Kasan 集成在 Linux 内核中,随 Linux 内核代码一起发布,并由内核社区维护和发展。但知道Linux-4.4版本才开始之初ARM64。此次采用的是Linux-4.9版本做实验。
KASAN原理
Kasan 的原理是利用“额外”的内存来标记那些可以被使用的内存的状态。这些做标记的区域被称为影子区域(shadow region)。了解 Linux 内存管理的读者知道,内存中的每个物理页在内存中都会有一个 struct page 这样的结构体来表示,即每 4KB 的页需要 40B 的结构体,大约 1% 的内存用来表示内存本身。Kasan 与其类似但“浪费”更为严重,影子区域的比例是 1:8,即总内存的九分之一会被“浪费”。用官方文档中的例子,如果有 128TB 的可用内存,需要有额外 16TB 的内存用来做标记。
做标记的方法比较简单,将可用内存按照 8 子节的大小分组,如果每组中所有 8 个字节都可以访问,则影子内存中相应的地方用全零(0x00)表示;如果可用内存的前 N(1 到 7 范围之间)个字节可用,则影子内存中响应的位置用 N 表示;其它情况影子内存用负数表示该内存不可用。
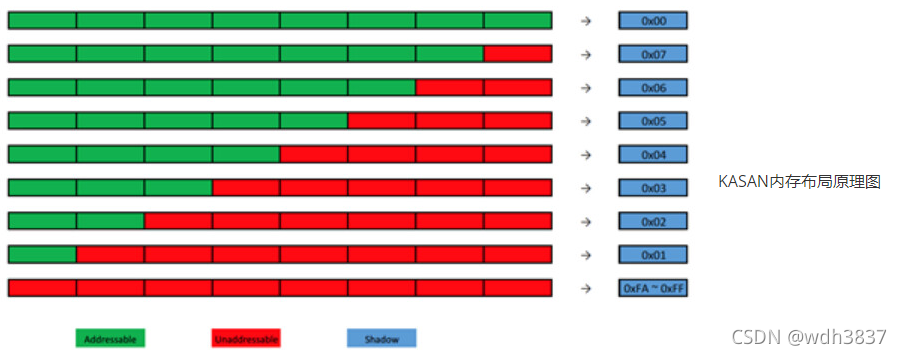
填充值定义
#define KASAN_FREE_PAGE 0xFF /* page was freed */
#define KASAN_PAGE_REDZONE 0xFE /* redzone for kmalloc_large allocations */
#define KASAN_KMALLOC_REDZONE 0xFC /* redzone inside slub object */
#define KASAN_KMALLOC_FREE 0xFB /* object was freed (kmem_cache_free/kfree) */
#define KASAN_GLOBAL_REDZONE 0xFA /* redzone for global variable */
内核配置选项
CONFIG_HAVE_ARCH_KASAN=y
CONFIG_KASAN=y
KASAN实例分析
- 在内存访问中有很多种错误类型:
- 越界访问(out-of-bounds)。
- 访问已经释放的内存(use-after-free)。
- 重复释放。(double-free)。
越界访问(out-of-bounds)
实例源码
- 实例包括
- kmalloc_oob_right:右侧数组越界访问。
- kmalloc_oob_left:左侧数组越界访问。
- kmalloc_node_oob_right:右侧节点越界访问。
- kmalloc_pagealloc_oob_right:右侧页越界访问。
- kmalloc_large_oob_right:右侧kmalloc最大分配越界访问。
- kmalloc_oob_krealloc_more:krealloc扩大后越界访问。
- kmalloc_oob_krealloc_less:krealloc缩小后越界访问。
- kmalloc_oob_16:申请小于赋值内存块导致越界访问。
- kmalloc_oob_memset_2:memset越界访问。
- kmalloc_oob_memset_4:memset越界访问。
- kmalloc_oob_memset_8:memset越界访问。
- kmalloc_oob_memset_16:memset越界访问。
- kmalloc_oob_in_memset:memset越界访问。
- kmem_cache_oob:其他cache域赋值导致越界访问。
- kasan_global_oob:全局变量越界访问。
- kasan_stack_oob:堆栈越界访问。
- ksize_unpoisons_memory:ksize后右侧越界访问。
- copy_user_test:内核态与用户态传递类越界访问。
- kasan_alloca_oob_left:左侧alloca越界访问。
- kasan_alloca_oob_right:右侧alloca越界访问。
#define pr_fmt(fmt) "kasan test: %s " fmt, __func__
#include <linux/kernel.h>
#include <linux/mman.h>
#include <linux/mm.h>
#include <linux/printk.h>
#include <linux/slab.h>
#include <linux/string.h>
#include <linux/uaccess.h>
#include <linux/module.h>
#include <linux/kasan.h>
static noinline void __init kmalloc_oob_right(void)
{
char *ptr;
size_t size = 123;
pr_info("out-of-bounds to right\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
ptr[size] = 'x';
kfree(ptr);
}
static noinline void __init kmalloc_oob_left(void)
{
char *ptr;
size_t size = 15;
pr_info("out-of-bounds to left\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
*ptr = *(ptr - 1);
kfree(ptr);
}
static noinline void __init kmalloc_node_oob_right(void)
{
char *ptr;
size_t size = 4096;
pr_info("kmalloc_node(): out-of-bounds to right\n");
ptr = kmalloc_node(size, GFP_KERNEL, 0);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
ptr[size] = 0;
kfree(ptr);
}
#ifdef CONFIG_SLUB
static noinline void __init kmalloc_pagealloc_oob_right(void)
{
char *ptr;
size_t size = KMALLOC_MAX_CACHE_SIZE + 10;
/* Allocate a chunk that does not fit into a SLUB cache to trigger
* the page allocator fallback.
*/
pr_info("kmalloc pagealloc allocation: out-of-bounds to right\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
ptr[size] = 0;
kfree(ptr);
}
#endif
static noinline void __init kmalloc_large_oob_right(void)
{
char *ptr;
size_t size = KMALLOC_MAX_CACHE_SIZE - 256;
/* Allocate a chunk that is large enough, but still fits into a slab
* and does not trigger the page allocator fallback in SLUB.
*/
pr_info("kmalloc large allocation: out-of-bounds to right\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
ptr[size] = 0;
kfree(ptr);
}
static noinline void __init kmalloc_oob_krealloc_more(void)
{
char *ptr1, *ptr2;
size_t size1 = 17;
size_t size2 = 19;
pr_info("out-of-bounds after krealloc more\n");
ptr1 = kmalloc(size1, GFP_KERNEL);
ptr2 = krealloc(ptr1, size2, GFP_KERNEL);
if (!ptr1 || !ptr2) {
pr_err("Allocation failed\n");
kfree(ptr1);
return;
}
ptr2[size2] = 'x';
kfree(ptr2);
}
static noinline void __init kmalloc_oob_krealloc_less(void)
{
char *ptr1, *ptr2;
size_t size1 = 17;
size_t size2 = 15;
pr_info("out-of-bounds after krealloc less\n");
ptr1 = kmalloc(size1, GFP_KERNEL);
ptr2 = krealloc(ptr1, size2, GFP_KERNEL);
if (!ptr1 || !ptr2) {
pr_err("Allocation failed\n");
kfree(ptr1);
return;
}
ptr2[size2] = 'x';
kfree(ptr2);
}
static noinline void __init kmalloc_oob_16(void)
{
struct {
u64 words[2];
} *ptr1, *ptr2;
pr_info("kmalloc out-of-bounds for 16-bytes access\n");
ptr1 = kmalloc(sizeof(*ptr1) - 3, GFP_KERNEL);
ptr2 = kmalloc(sizeof(*ptr2), GFP_KERNEL);
if (!ptr1 || !ptr2) {
pr_err("Allocation failed\n");
kfree(ptr1);
kfree(ptr2);
return;
}
*ptr1 = *ptr2;
kfree(ptr1);
kfree(ptr2);
}
static noinline void __init kmalloc_oob_memset_2(void)
{
char *ptr;
size_t size = 8;
pr_info("out-of-bounds in memset2\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
memset(ptr+7, 0, 2);
kfree(ptr);
}
static noinline void __init kmalloc_oob_memset_4(void)
{
char *ptr;
size_t size = 8;
pr_info("out-of-bounds in memset4\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
memset(ptr+5, 0, 4);
kfree(ptr);
}
static noinline void __init kmalloc_oob_memset_8(void)
{
char *ptr;
size_t size = 8;
pr_info("out-of-bounds in memset8\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
memset(ptr+1, 0, 8);
kfree(ptr);
}
static noinline void __init kmalloc_oob_memset_16(void)
{
char *ptr;
size_t size = 16;
pr_info("out-of-bounds in memset16\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
memset(ptr+1, 0, 16);
kfree(ptr);
}
static noinline void __init kmalloc_oob_in_memset(void)
{
char *ptr;
size_t size = 666;
pr_info("out-of-bounds in memset\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
memset(ptr, 0, size+5);
kfree(ptr);
}
static int __init kmalloc_tests_init(void)
{
/*
* Temporarily enable multi-shot mode. Otherwise, we'd only get a
* report for the first case.
*/
bool multishot = kasan_save_enable_multi_shot();
kmalloc_oob_right();
kmalloc_oob_left();
kmalloc_node_oob_right();
#ifdef CONFIG_SLUB
kmalloc_pagealloc_oob_right();
#endif
kmalloc_large_oob_right();
kmalloc_oob_krealloc_more();
kmalloc_oob_krealloc_less();
kmalloc_oob_16();
kmalloc_oob_in_memset();
kmalloc_oob_memset_2();
kmalloc_oob_memset_4();
kmalloc_oob_memset_8();
kmalloc_oob_memset_16();
kasan_restore_multi_shot(multishot);
return -EAGAIN;
}
module_init(kmalloc_tests_init);
MODULE_LICENSE("GPL");
输出log
/ # insmod lib/modules/4.9.191/test_kasan.ko
[ 105.429081] kasan test: kmalloc_oob_right out-of-bounds to right
[ 105.437243] ==================================================================
[ 105.445390] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_right+0x7c/0xb8 [test_kasan]
[ 105.454244] Write of size 1 at addr ffffffc0335a00fb by task insmod/1204
[ 105.461731]
[ 105.463412] CPU: 0 PID: 1204 Comm: insmod Not tainted 4.9.191 #4
[ 105.470130] Hardware name: sun50iw10 (DT)
[ 105.474613] Call trace:
[ 105.477371] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 105.483419] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 105.489085] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 105.494753] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 105.501968] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 105.508014] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 105.514002] [<ffffff90007b83d4>] kmalloc_oob_right+0x7c/0xb8 [test_kasan]
[ 105.521644] [<ffffff90007b9528>] kmalloc_tests_init+0x18/0x90 [test_kasan]
[ 105.529345] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 105.535592] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 105.541740] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 105.547884] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 105.554220] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 105.560164]
[ 105.561838] Allocated by task 1204:
[ 105.565753] save_stack_trace_tsk+0x0/0x1f4
[ 105.570440] save_stack_trace+0x18/0x20
[ 105.574741] kasan_kmalloc.part.1+0x44/0xec
[ 105.579429] kasan_kmalloc+0x88/0x9c
[ 105.583475] kmalloc_oob_right+0x60/0xb8 [test_kasan]
[ 105.589175] kmalloc_tests_init+0x18/0x90 [test_kasan]
[ 105.594930] do_one_initcall+0xe4/0x1b0
[ 105.599233] do_init_module+0xf0/0x2ac
[ 105.603438] load_module+0x2690/0x2dcc
[ 105.607640] SyS_init_module+0x198/0x224
[ 105.612033] el0_svc_naked+0x34/0x38
[ 105.616030]
[ 105.617699] Freed by task 0:
[ 105.620922] (stack is not available)
[ 105.624922]
[ 105.626600] The buggy address belongs to the object at ffffffc0335a0080
[ 105.626600] which belongs to the cache kmalloc-128 of size 128
[ 105.640607] The buggy address is located 123 bytes inside of
[ 105.640607] 128-byte region [ffffffc0335a0080, ffffffc0335a0100)
[ 105.653737] The buggy address belongs to the page:
[ 105.659104] page:ffffffbf00cd6800 count:1 mapcount:0 mapping: (null) index:0xffffffc0335a3c80 compound_mapcount: 0
[ 105.671574] flags: 0x10200(slab|head)
[ 105.675672] page dumped because: kasan: bad access detected
[ 105.681901]
[ 105.683572] Memory state around the buggy address:
[ 105.688936] ffffffc03359ff80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 105.697019] ffffffc0335a0000: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 105.705104] >ffffffc0335a0080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 03
[ 105.713179] ^
[ 105.721165] ffffffc0335a0100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 105.729248] ffffffc0335a0180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 105.737324] ==================================================================
[ 105.745398] Disabling lock debugging due to kernel taint
[ 105.760245] kasan test: kmalloc_oob_left out-of-bounds to left
[ 105.783074] ==================================================================
[ 105.791219] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_left+0x7c/0xc0 [test_kasan]
[ 105.799978] Read of size 1 at addr ffffffc0335a057f by task insmod/1204
[ 105.807371]
[ 105.809052] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 105.817126] Hardware name: sun50iw10 (DT)
[ 105.821611] Call trace:
[ 105.824366] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 105.830415] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 105.836080] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 105.841746] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 105.848959] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 105.855006] [<ffffff90081f6910>] __asan_load1+0x44/0x4c
[ 105.860897] [<ffffff90007b848c>] kmalloc_oob_left+0x7c/0xc0 [test_kasan]
[ 105.868438] [<ffffff90007b952c>] kmalloc_tests_init+0x1c/0x90 [test_kasan]
[ 105.876134] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 105.882382] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 105.888529] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 105.894674] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 105.901012] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 105.906948]
[ 105.908622] Allocated by task 1204:
[ 105.912527] save_stack_trace_tsk+0x0/0x1f4
[ 105.917215] save_stack_trace+0x18/0x20
[ 105.921515] kasan_kmalloc.part.1+0x44/0xec
[ 105.926202] kasan_kmalloc+0x88/0x9c
[ 105.930245] kmalloc_oob_left+0x60/0xc0 [test_kasan]
[ 105.935841] kmalloc_tests_init+0x1c/0x90 [test_kasan]
[ 105.941594] do_one_initcall+0xe4/0x1b0
[ 105.945894] do_init_module+0xf0/0x2ac
[ 105.950098] load_module+0x2690/0x2dcc
[ 105.954297] SyS_init_module+0x198/0x224
[ 105.958692] el0_svc_naked+0x34/0x38
[ 105.962691]
[ 105.964362] Freed by task 0:
[ 105.967584] (stack is not available)
[ 105.971581]
[ 105.973256] The buggy address belongs to the object at ffffffc0335a0580
[ 105.973256] which belongs to the cache kmalloc-128 of size 128
[ 105.987264] The buggy address is located 1 bytes to the left of
[ 105.987264] 128-byte region [ffffffc0335a0580, ffffffc0335a0600)
[ 106.000683] The buggy address belongs to the page:
[ 106.006050] page:ffffffbf00cd6800 count:1 mapcount:0 mapping: (null) index:0xffffffc0335a3780 compound_mapcount: 0
[ 106.018517] flags: 0x10200(slab|head)
[ 106.022615] page dumped because: kasan: bad access detected
[ 106.028840]
[ 106.030509] Memory state around the buggy address:
[ 106.035876] ffffffc0335a0400: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.043959] ffffffc0335a0480: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.052043] >ffffffc0335a0500: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.060118] ^
[ 106.068105] ffffffc0335a0580: 00 07 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.076185] ffffffc0335a0600: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.084260] ==================================================================
[ 106.159446] kasan test: kmalloc_node_oob_right kmalloc_node(): out-of-bounds to right
[ 106.168480] ==================================================================
[ 106.176619] BUG: KASAN: slab-out-of-bounds in kmalloc_node_oob_right+0x80/0xb8 [test_kasan]
[ 106.185962] Write of size 1 at addr ffffffc0305d2280 by task insmod/1204
[ 106.193449]
[ 106.195135] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 106.203210] Hardware name: sun50iw10 (DT)
[ 106.207694] Call trace:
[ 106.210449] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 106.216500] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 106.222162] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 106.227830] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 106.235043] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 106.241091] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 106.247080] [<ffffff90007b8550>] kmalloc_node_oob_right+0x80/0xb8 [test_kasan]
[ 106.255204] [<ffffff90007b9530>] kmalloc_tests_init+0x20/0x90 [test_kasan]
[ 106.262899] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 106.269146] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 106.275291] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 106.281437] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 106.287776] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 106.293713]
[ 106.295386] Allocated by task 1204:
[ 106.299300] save_stack_trace_tsk+0x0/0x1f4
[ 106.303985] save_stack_trace+0x18/0x20
[ 106.308284] kasan_kmalloc.part.1+0x44/0xec
[ 106.312971] kasan_kmalloc+0x88/0x9c
[ 106.317016] kmalloc_node_oob_right+0x60/0xb8 [test_kasan]
[ 106.323197] kmalloc_tests_init+0x20/0x90 [test_kasan]
[ 106.328948] do_one_initcall+0xe4/0x1b0
[ 106.333248] do_init_module+0xf0/0x2ac
[ 106.337449] load_module+0x2690/0x2dcc
[ 106.341649] SyS_init_module+0x198/0x224
[ 106.346042] el0_svc_naked+0x34/0x38
[ 106.350039]
[ 106.351709] Freed by task 772:
[ 106.355135] save_stack_trace_tsk+0x0/0x1f4
[ 106.359824] save_stack_trace+0x18/0x20
[ 106.364124] kasan_slab_free+0x90/0x15c
[ 106.368418] kfree+0xc8/0x258
[ 106.371748] cleanup_uevent_env+0x20/0x2c
[ 106.376242] call_usermodehelper_freeinfo+0x28/0x3c
[ 106.381703] umh_complete+0x38/0x40
[ 106.385617] call_usermodehelper_exec_async+0x184/0x1b0
[ 106.391466] ret_from_fork+0x10/0x50
[ 106.395461]
[ 106.397136] The buggy address belongs to the object at ffffffc0305d1280
[ 106.397136] which belongs to the cache kmalloc-4096 of size 4096
[ 106.411335] The buggy address is located 0 bytes to the right of
[ 106.411335] 4096-byte region [ffffffc0305d1280, ffffffc0305d2280)
[ 106.424941] The buggy address belongs to the page:
[ 106.430308] page:ffffffbf00c17400 count:1 mapcount:0 mapping: (null) index:0xffffffc0305d2480 compound_mapcount: 0
[ 106.442771] flags: 0x10200(slab|head)
[ 106.446866] page dumped because: kasan: bad access detected
[ 106.453095]
[ 106.454763] Memory state around the buggy address:
[ 106.460131] ffffffc0305d2180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 106.468213] ffffffc0305d2200: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 106.476295] >ffffffc0305d2280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.484369] ^
[ 106.487987] ffffffc0305d2300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.496067] ffffffc0305d2380: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 106.504139] ==================================================================
[ 106.517246] kasan test: kmalloc_pagealloc_oob_right kmalloc pagealloc allocation: out-of-bounds to right
[ 106.537092] ==================================================================
[ 106.545230] BUG: KASAN: slab-out-of-bounds in kmalloc_pagealloc_oob_right+0x5c/0x88 [test_kasan]
[ 106.555059] Write of size 1 at addr ffffffc03263a00a by task insmod/1204
[ 106.562551]
[ 106.564231] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 106.572306] Hardware name: sun50iw10 (DT)
[ 106.576792] Call trace:
[ 106.579550] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 106.585601] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 106.591263] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 106.596929] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 106.604145] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 106.610195] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 106.616185] [<ffffff90007b832c>] kmalloc_pagealloc_oob_right+0x5c/0x88 [test_kasan]
[ 106.624791] [<ffffff90007b9534>] kmalloc_tests_init+0x24/0x90 [test_kasan]
[ 106.632487] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 106.638734] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 106.644878] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 106.651025] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 106.657362] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 106.663301]
[ 106.664972] The buggy address belongs to the page:
[ 106.670332] page:ffffffbf00c98e00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 106.681339] flags: 0x10000(head)
[ 106.684950] page dumped because: kasan: bad access detected
[ 106.691181]
[ 106.692846] Memory state around the buggy address:
[ 106.698213] ffffffc032639f00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 106.706298] ffffffc032639f80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 106.714380] >ffffffc03263a000: 00 02 fe fe fe fe fe fe fe fe fe fe fe fe fe fe
[ 106.722456] ^
[ 106.726365] ffffffc03263a080: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
[ 106.734449] ffffffc03263a100: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
[ 106.742524] ==================================================================
[ 106.755409] kasan test: kmalloc_large_oob_right kmalloc large allocation: out-of-bounds to right
[ 106.767882] ==================================================================
[ 106.776012] BUG: KASAN: slab-out-of-bounds in kmalloc_large_oob_right+0x80/0xb8 [test_kasan]
[ 106.785453] Write of size 1 at addr ffffffc03066c180 by task insmod/1204
[ 106.792941]
[ 106.794625] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 106.802702] Hardware name: sun50iw10 (DT)
[ 106.807189] Call trace:
[ 106.809946] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 106.815997] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 106.821660] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 106.827325] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 106.834540] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 106.840587] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 106.846576] [<ffffff90007b8608>] kmalloc_large_oob_right+0x80/0xb8 [test_kasan]
[ 106.854796] [<ffffff90007b9538>] kmalloc_tests_init+0x28/0x90 [test_kasan]
[ 106.862491] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 106.868736] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 106.874881] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 106.881028] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 106.887365] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 106.893304]
[ 106.894977] Allocated by task 1204:
[ 106.898889] save_stack_trace_tsk+0x0/0x1f4
[ 106.903573] save_stack_trace+0x18/0x20
[ 106.907874] kasan_kmalloc.part.1+0x44/0xec
[ 106.912561] kasan_kmalloc+0x88/0x9c
[ 106.916607] kmalloc_large_oob_right+0x60/0xb8 [test_kasan]
[ 106.922884] kmalloc_tests_init+0x28/0x90 [test_kasan]
[ 106.928638] do_one_initcall+0xe4/0x1b0
[ 106.932940] do_init_module+0xf0/0x2ac
[ 106.937142] load_module+0x2690/0x2dcc
[ 106.941344] SyS_init_module+0x198/0x224
[ 106.945737] el0_svc_naked+0x34/0x38
[ 106.949736]
[ 106.951407] Freed by task 0:
[ 106.954628] (stack is not available)
[ 106.958625]
[ 106.960301] The buggy address belongs to the object at ffffffc03066a280
[ 106.960301] which belongs to the cache kmalloc-8192 of size 8192
[ 106.974500] The buggy address is located 7936 bytes inside of
[ 106.974500] 8192-byte region [ffffffc03066a280, ffffffc03066c280)
[ 106.987817] The buggy address belongs to the page:
[ 106.993180] page:ffffffbf00c19a00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 107.004191] flags: 0x10200(slab|head)
[ 107.008289] page dumped because: kasan: bad access detected
[ 107.014520]
[ 107.016191] Memory state around the buggy address:
[ 107.021556] ffffffc03066c080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 107.029636] ffffffc03066c100: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 107.037720] >ffffffc03066c180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.045793] ^
[ 107.049411] ffffffc03066c200: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.057491] ffffffc03066c280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.065565] ==================================================================
[ 107.078711] kasan test: kmalloc_oob_krealloc_more out-of-bounds after krealloc more
[ 107.094689] ==================================================================
[ 107.102826] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_krealloc_more+0xa0/0xd8 [test_kasan]
[ 107.112464] Write of size 1 at addr ffffffc0335a1213 by task insmod/1204
[ 107.119954]
[ 107.121635] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 107.129710] Hardware name: sun50iw10 (DT)
[ 107.134195] Call trace:
[ 107.136951] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 107.143002] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 107.148663] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 107.154328] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 107.161539] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 107.167588] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 107.173578] [<ffffff90007b89c0>] kmalloc_oob_krealloc_more+0xa0/0xd8 [test_kasan]
[ 107.181994] [<ffffff90007b953c>] kmalloc_tests_init+0x2c/0x90 [test_kasan]
[ 107.189691] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 107.195938] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 107.202084] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 107.208226] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 107.214564] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 107.220502]
[ 107.222175] Allocated by task 1204:
[ 107.226089] save_stack_trace_tsk+0x0/0x1f4
[ 107.230776] save_stack_trace+0x18/0x20
[ 107.235075] kasan_kmalloc.part.1+0x44/0xec
[ 107.239763] kasan_kmalloc+0x88/0x9c
[ 107.243769] kasan_krealloc+0x64/0x70
[ 107.247873] krealloc+0x5c/0xd4
[ 107.251433] kmalloc_oob_krealloc_more+0x74/0xd8 [test_kasan]
[ 107.257902] kmalloc_tests_init+0x2c/0x90 [test_kasan]
[ 107.263657] do_one_initcall+0xe4/0x1b0
[ 107.267953] do_init_module+0xf0/0x2ac
[ 107.272153] load_module+0x2690/0x2dcc
[ 107.276353] SyS_init_module+0x198/0x224
[ 107.280744] el0_svc_naked+0x34/0x38
[ 107.284739]
[ 107.286409] Freed by task 0:
[ 107.289630] (stack is not available)
[ 107.293625]
[ 107.295301] The buggy address belongs to the object at ffffffc0335a1200
[ 107.295301] which belongs to the cache kmalloc-128 of size 128
[ 107.309307] The buggy address is located 19 bytes inside of
[ 107.309307] 128-byte region [ffffffc0335a1200, ffffffc0335a1280)
[ 107.322332] The buggy address belongs to the page:
[ 107.327697] page:ffffffbf00cd6800 count:1 mapcount:0 mapping: (null) index:0xffffffc0335a2b00 compound_mapcount: 0
[ 107.340163] flags: 0x10200(slab|head)
[ 107.344260] page dumped because: kasan: bad access detected
[ 107.350488]
[ 107.352160] Memory state around the buggy address:
[ 107.357525] ffffffc0335a1100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.365607] ffffffc0335a1180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.373686] >ffffffc0335a1200: 00 00 03 fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.381755] ^
[ 107.385956] ffffffc0335a1280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.394037] ffffffc0335a1300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.402111] ==================================================================
[ 107.419927] kasan test: kmalloc_oob_krealloc_less out-of-bounds after krealloc less
[ 107.445756] ==================================================================
[ 107.453906] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_krealloc_less+0xa0/0xd8 [test_kasan]
[ 107.463537] Write of size 1 at addr ffffffc0335a170f by task insmod/1204
[ 107.471027]
[ 107.472712] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 107.480788] Hardware name: sun50iw10 (DT)
[ 107.485272] Call trace:
[ 107.488031] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 107.494080] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 107.499747] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 107.505415] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 107.512626] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 107.518674] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 107.524662] [<ffffff90007b8a98>] kmalloc_oob_krealloc_less+0xa0/0xd8 [test_kasan]
[ 107.533075] [<ffffff90007b9540>] kmalloc_tests_init+0x30/0x90 [test_kasan]
[ 107.540770] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 107.547018] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 107.553165] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 107.559311] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 107.565647] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 107.571586]
[ 107.573260] Allocated by task 1204:
[ 107.577174] save_stack_trace_tsk+0x0/0x1f4
[ 107.581861] save_stack_trace+0x18/0x20
[ 107.586161] kasan_kmalloc.part.1+0x44/0xec
[ 107.590848] kasan_kmalloc+0x88/0x9c
[ 107.594856] kasan_krealloc+0x64/0x70
[ 107.598959] krealloc+0x5c/0xd4
[ 107.602518] kmalloc_oob_krealloc_less+0x74/0xd8 [test_kasan]
[ 107.608988] kmalloc_tests_init+0x30/0x90 [test_kasan]
[ 107.614741] do_one_initcall+0xe4/0x1b0
[ 107.619042] do_init_module+0xf0/0x2ac
[ 107.623240] load_module+0x2690/0x2dcc
[ 107.627440] SyS_init_module+0x198/0x224
[ 107.631834] el0_svc_naked+0x34/0x38
[ 107.635832]
[ 107.637502] Freed by task 0:
[ 107.640725] (stack is not available)
[ 107.644722]
[ 107.646399] The buggy address belongs to the object at ffffffc0335a1700
[ 107.646399] which belongs to the cache kmalloc-128 of size 128
[ 107.660408] The buggy address is located 15 bytes inside of
[ 107.660408] 128-byte region [ffffffc0335a1700, ffffffc0335a1780)
[ 107.673434] The buggy address belongs to the page:
[ 107.678803] page:ffffffbf00cd6800 count:1 mapcount:0 mapping: (null) index:0xffffffc0335a2600 compound_mapcount: 0
[ 107.691271] flags: 0x10200(slab|head)
[ 107.695367] page dumped because: kasan: bad access detected
[ 107.701598]
[ 107.703268] Memory state around the buggy address:
[ 107.708635] ffffffc0335a1600: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.716717] ffffffc0335a1680: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.724800] >ffffffc0335a1700: 00 07 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.732874] ^
[ 107.736783] ffffffc0335a1780: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.744867] ffffffc0335a1800: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 107.752987] ==================================================================
[ 107.817694] kasan test: kmalloc_oob_16 kmalloc out-of-bounds for 16-bytes access
[ 107.833892] ==================================================================
[ 107.842039] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_16+0xc4/0x110 [test_kasan]
[ 107.850702] Write of size 16 at addr ffffffc0319fe100 by task insmod/1204
[ 107.858291]
[ 107.859974] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 107.868053] Hardware name: sun50iw10 (DT)
[ 107.872539] Call trace:
[ 107.875297] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 107.881342] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 107.887004] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 107.892669] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 107.899882] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 107.905929] [<ffffff90081f6d64>] __asan_store16+0x78/0x80
[ 107.912016] [<ffffff90007b8704>] kmalloc_oob_16+0xc4/0x110 [test_kasan]
[ 107.919460] [<ffffff90007b9544>] kmalloc_tests_init+0x34/0x90 [test_kasan]
[ 107.927156] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 107.933404] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 107.939550] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 107.945693] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 107.952031] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 107.957973]
[ 107.959646] Allocated by task 1204:
[ 107.963562] save_stack_trace_tsk+0x0/0x1f4
[ 107.968250] save_stack_trace+0x18/0x20
[ 107.972548] kasan_kmalloc.part.1+0x44/0xec
[ 107.977235] kasan_kmalloc+0x88/0x9c
[ 107.981278] kmalloc_oob_16+0x68/0x110 [test_kasan]
[ 107.986778] kmalloc_tests_init+0x34/0x90 [test_kasan]
[ 107.992531] do_one_initcall+0xe4/0x1b0
[ 107.996830] do_init_module+0xf0/0x2ac
[ 108.001031] load_module+0x2690/0x2dcc
[ 108.005232] SyS_init_module+0x198/0x224
[ 108.009625] el0_svc_naked+0x34/0x38
[ 108.013620]
[ 108.015292] Freed by task 1036:
[ 108.018814] save_stack_trace_tsk+0x0/0x1f4
[ 108.023505] save_stack_trace+0x18/0x20
[ 108.027803] kasan_slab_free+0x90/0x15c
[ 108.032099] kfree+0xc8/0x258
[ 108.035428] kvfree+0x34/0x3c
[ 108.038758] default_file_splice_read+0x3ac/0x40c
[ 108.044022] do_splice_to+0xa0/0xbc
[ 108.047930] splice_direct_to_actor+0x170/0x2f8
[ 108.053001] do_splice_direct+0xf8/0x148
[ 108.057398] do_sendfile+0x264/0x434
[ 108.061407] SyS_sendfile64+0xe8/0x1a0
[ 108.065609] el0_svc_naked+0x34/0x38
[ 108.069606]
[ 108.071283] The buggy address belongs to the object at ffffffc0319fe100
[ 108.071283] which belongs to the cache kmalloc-128 of size 128
[ 108.085289] The buggy address is located 0 bytes inside of
[ 108.085289] 128-byte region [ffffffc0319fe100, ffffffc0319fe180)
[ 108.098220] The buggy address belongs to the page:
[ 108.103586] page:ffffffbf00c67f00 count:1 mapcount:0 mapping: (null) index:0xffffffc0319fdc00 compound_mapcount: 0
[ 108.116051] flags: 0x10200(slab|head)
[ 108.120148] page dumped because: kasan: bad access detected
[ 108.126378]
[ 108.128046] Memory state around the buggy address:
[ 108.133415] ffffffc0319fe000: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.141499] ffffffc0319fe080: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.149586] >ffffffc0319fe100: 00 05 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.157662] ^
[ 108.161573] ffffffc0319fe180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.169656] ffffffc0319fe200: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.177731] ==================================================================
[ 108.192928] kasan test: kmalloc_oob_in_memset out-of-bounds in memset
[ 108.214416] ==================================================================
[ 108.222560] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_in_memset+0x84/0xb8 [test_kasan]
[ 108.231805] Write of size 671 at addr ffffffc03243ce80 by task insmod/1204
[ 108.239490]
[ 108.241170] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 108.249245] Hardware name: sun50iw10 (DT)
[ 108.253731] Call trace:
[ 108.256489] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 108.262540] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 108.268201] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 108.273867] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 108.281078] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 108.287126] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 108.293757] [<ffffff90081f72f0>] memset+0x2c/0x4c
[ 108.299067] [<ffffff90007b8b54>] kmalloc_oob_in_memset+0x84/0xb8 [test_kasan]
[ 108.307094] [<ffffff90007b9548>] kmalloc_tests_init+0x38/0x90 [test_kasan]
[ 108.314792] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 108.321041] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 108.327188] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 108.333332] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 108.339669] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 108.345608]
[ 108.347279] Allocated by task 1204:
[ 108.351193] save_stack_trace_tsk+0x0/0x1f4
[ 108.355878] save_stack_trace+0x18/0x20
[ 108.360176] kasan_kmalloc.part.1+0x44/0xec
[ 108.364858] kasan_kmalloc+0x88/0x9c
[ 108.368904] kmalloc_oob_in_memset+0x60/0xb8 [test_kasan]
[ 108.374985] kmalloc_tests_init+0x38/0x90 [test_kasan]
[ 108.380736] do_one_initcall+0xe4/0x1b0
[ 108.385038] do_init_module+0xf0/0x2ac
[ 108.389236] load_module+0x2690/0x2dcc
[ 108.393434] SyS_init_module+0x198/0x224
[ 108.397827] el0_svc_naked+0x34/0x38
[ 108.401824]
[ 108.403494] Freed by task 0:
[ 108.406715] (stack is not available)
[ 108.410712]
[ 108.412387] The buggy address belongs to the object at ffffffc03243ce80
[ 108.412387] which belongs to the cache kmalloc-1024 of size 1024
[ 108.426586] The buggy address is located 0 bytes inside of
[ 108.426586] 1024-byte region [ffffffc03243ce80, ffffffc03243d280)
[ 108.439610] The buggy address belongs to the page:
[ 108.444973] page:ffffffbf00c90e00 count:1 mapcount:0 mapping: (null) index:0xffffffc03243b080 compound_mapcount: 0
[ 108.457446] flags: 0x10200(slab|head)
[ 108.461545] page dumped because: kasan: bad access detected
[ 108.467774]
[ 108.469445] Memory state around the buggy address:
[ 108.474814] ffffffc03243d000: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 108.482896] ffffffc03243d080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 108.490980] >ffffffc03243d100: 00 00 00 02 fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.499050] ^
[ 108.503544] ffffffc03243d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.511627] ffffffc03243d200: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.519700] ==================================================================
[ 108.532700] kasan test: kmalloc_oob_memset_2 out-of-bounds in memset2
[ 108.548444] ==================================================================
[ 108.556578] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_memset_2+0x84/0xb8 [test_kasan]
[ 108.565724] Write of size 2 at addr ffffffc032eb8307 by task insmod/1204
[ 108.573213]
[ 108.574896] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 108.582971] Hardware name: sun50iw10 (DT)
[ 108.587457] Call trace:
[ 108.590213] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 108.596263] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 108.601924] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 108.607589] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 108.614802] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 108.620851] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 108.627482] [<ffffff90081f72f0>] memset+0x2c/0x4c
[ 108.632786] [<ffffff90007b8c0c>] kmalloc_oob_memset_2+0x84/0xb8 [test_kasan]
[ 108.640713] [<ffffff90007b954c>] kmalloc_tests_init+0x3c/0x90 [test_kasan]
[ 108.648408] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 108.654654] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 108.660795] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 108.666938] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 108.673275] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 108.679213]
[ 108.680886] Allocated by task 1204:
[ 108.684799] save_stack_trace_tsk+0x0/0x1f4
[ 108.689488] save_stack_trace+0x18/0x20
[ 108.693788] kasan_kmalloc.part.1+0x44/0xec
[ 108.698477] kasan_kmalloc+0x88/0x9c
[ 108.702522] kmalloc_oob_memset_2+0x60/0xb8 [test_kasan]
[ 108.708503] kmalloc_tests_init+0x3c/0x90 [test_kasan]
[ 108.714258] do_one_initcall+0xe4/0x1b0
[ 108.718558] do_init_module+0xf0/0x2ac
[ 108.722757] load_module+0x2690/0x2dcc
[ 108.726957] SyS_init_module+0x198/0x224
[ 108.731350] el0_svc_naked+0x34/0x38
[ 108.735347]
[ 108.737018] Freed by task 1041:
[ 108.740545] save_stack_trace_tsk+0x0/0x1f4
[ 108.745233] save_stack_trace+0x18/0x20
[ 108.749533] kasan_slab_free+0x90/0x15c
[ 108.753831] kfree+0xc8/0x258
[ 108.757163] cpufreq_task_times_exit+0x60/0x70
[ 108.762141] free_task+0x14/0x68
[ 108.765762] __put_task_struct+0x168/0x17c
[ 108.770358] delayed_put_task_struct+0x44/0x50
[ 108.775341] rcu_process_callbacks+0x52c/0x740
[ 108.780316] __do_softirq+0x1bc/0x35c
[ 108.784409]
[ 108.786085] The buggy address belongs to the object at ffffffc032eb8300
[ 108.786085] which belongs to the cache kmalloc-128 of size 128
[ 108.800089] The buggy address is located 7 bytes inside of
[ 108.800089] 128-byte region [ffffffc032eb8300, ffffffc032eb8380)
[ 108.813017] The buggy address belongs to the page:
[ 108.818382] page:ffffffbf00cbae00 count:1 mapcount:0 mapping: (null) index:0xffffffc032eba600 compound_mapcount: 0
[ 108.830852] flags: 0x10200(slab|head)
[ 108.834950] page dumped because: kasan: bad access detected
[ 108.841182]
[ 108.842850] Memory state around the buggy address:
[ 108.848217] ffffffc032eb8200: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.856299] ffffffc032eb8280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.864383] >ffffffc032eb8300: 00 fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.872458] ^
[ 108.876366] ffffffc032eb8380: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.884449] ffffffc032eb8400: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 108.892524] ==================================================================
[ 108.910034] kasan test: kmalloc_oob_memset_4 out-of-bounds in memset4
[ 108.937830] ==================================================================
[ 108.945977] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_memset_4+0x84/0xb8 [test_kasan]
[ 108.955124] Write of size 4 at addr ffffffc0336d8d05 by task insmod/1204
[ 108.962614]
[ 108.964298] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 108.972374] Hardware name: sun50iw10 (DT)
[ 108.976860] Call trace:
[ 108.979617] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 108.985667] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 108.991327] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 108.996995] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 109.004210] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 109.010259] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 109.016887] [<ffffff90081f72f0>] memset+0x2c/0x4c
[ 109.022199] [<ffffff90007b8cc4>] kmalloc_oob_memset_4+0x84/0xb8 [test_kasan]
[ 109.030129] [<ffffff90007b9550>] kmalloc_tests_init+0x40/0x90 [test_kasan]
[ 109.037825] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 109.044071] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 109.050218] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 109.056364] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 109.062703] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 109.068642]
[ 109.070315] Allocated by task 1204:
[ 109.074229] save_stack_trace_tsk+0x0/0x1f4
[ 109.078917] save_stack_trace+0x18/0x20
[ 109.083216] kasan_kmalloc.part.1+0x44/0xec
[ 109.087902] kasan_kmalloc+0x88/0x9c
[ 109.091948] kmalloc_oob_memset_4+0x60/0xb8 [test_kasan]
[ 109.097938] kmalloc_tests_init+0x40/0x90 [test_kasan]
[ 109.103692] do_one_initcall+0xe4/0x1b0
[ 109.107990] do_init_module+0xf0/0x2ac
[ 109.112192] load_module+0x2690/0x2dcc
[ 109.116394] SyS_init_module+0x198/0x224
[ 109.120787] el0_svc_naked+0x34/0x38
[ 109.124784]
[ 109.126453] Freed by task 1045:
[ 109.129978] save_stack_trace_tsk+0x0/0x1f4
[ 109.134667] save_stack_trace+0x18/0x20
[ 109.138967] kasan_slab_free+0x90/0x15c
[ 109.143264] kfree+0xc8/0x258
[ 109.146593] kvfree+0x34/0x3c
[ 109.149923] default_file_splice_read+0x3ac/0x40c
[ 109.155191] do_splice_to+0xa0/0xbc
[ 109.159099] splice_direct_to_actor+0x170/0x2f8
[ 109.164173] do_splice_direct+0xf8/0x148
[ 109.168567] do_sendfile+0x264/0x434
[ 109.172577] SyS_sendfile64+0xe8/0x1a0
[ 109.176777] el0_svc_naked+0x34/0x38
[ 109.180774]
[ 109.182451] The buggy address belongs to the object at ffffffc0336d8d00
[ 109.182451] which belongs to the cache kmalloc-128 of size 128
[ 109.196455] The buggy address is located 5 bytes inside of
[ 109.196455] 128-byte region [ffffffc0336d8d00, ffffffc0336d8d80)
[ 109.209386] The buggy address belongs to the page:
[ 109.214750] page:ffffffbf00cdb600 count:1 mapcount:0 mapping: (null) index:0xffffffc0336d9480 compound_mapcount: 0
[ 109.227218] flags: 0x10200(slab|head)
[ 109.231316] page dumped because: kasan: bad access detected
[ 109.237544]
[ 109.239214] Memory state around the buggy address:
[ 109.244581] ffffffc0336d8c00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.252665] ffffffc0336d8c80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.260745] >ffffffc0336d8d00: 00 fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.268819] ^
[ 109.272730] ffffffc0336d8d80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.280810] ffffffc0336d8e00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.288885] ==================================================================
[ 109.333769] kasan test: kmalloc_oob_memset_8 out-of-bounds in memset8
[ 109.349685] ==================================================================
[ 109.357834] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_memset_8+0x84/0xb8 [test_kasan]
[ 109.366985] Write of size 8 at addr ffffffc0336d8a81 by task insmod/1204
[ 109.374476]
[ 109.376159] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 109.384236] Hardware name: sun50iw10 (DT)
[ 109.388722] Call trace:
[ 109.391483] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 109.397532] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 109.403194] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 109.408854] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 109.416068] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 109.422119] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 109.428749] [<ffffff90081f72f0>] memset+0x2c/0x4c
[ 109.434057] [<ffffff90007b8d7c>] kmalloc_oob_memset_8+0x84/0xb8 [test_kasan]
[ 109.441986] [<ffffff90007b9554>] kmalloc_tests_init+0x44/0x90 [test_kasan]
[ 109.449684] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 109.455928] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 109.462072] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 109.468217] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 109.474552] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 109.480491]
[ 109.482164] Allocated by task 1204:
[ 109.486078] save_stack_trace_tsk+0x0/0x1f4
[ 109.490767] save_stack_trace+0x18/0x20
[ 109.495069] kasan_kmalloc.part.1+0x44/0xec
[ 109.499756] kasan_kmalloc+0x88/0x9c
[ 109.503803] kmalloc_oob_memset_8+0x60/0xb8 [test_kasan]
[ 109.509789] kmalloc_tests_init+0x44/0x90 [test_kasan]
[ 109.515542] do_one_initcall+0xe4/0x1b0
[ 109.519845] do_init_module+0xf0/0x2ac
[ 109.524047] load_module+0x2690/0x2dcc
[ 109.528246] SyS_init_module+0x198/0x224
[ 109.532640] el0_svc_naked+0x34/0x38
[ 109.536637]
[ 109.538309] Freed by task 1044:
[ 109.541832] save_stack_trace_tsk+0x0/0x1f4
[ 109.546519] save_stack_trace+0x18/0x20
[ 109.550821] kasan_slab_free+0x90/0x15c
[ 109.555120] kfree+0xc8/0x258
[ 109.558452] load_elf_binary+0xcbc/0x182c
[ 109.562946] search_binary_handler+0xc8/0x264
[ 109.567827] do_execveat_common.isra.14+0x8a4/0xa34
[ 109.573290] do_execve+0x28/0x30
[ 109.576909] SyS_execve+0x24/0x34
[ 109.580623] el0_svc_naked+0x34/0x38
[ 109.584621]
[ 109.586298] The buggy address belongs to the object at ffffffc0336d8a80
[ 109.586298] which belongs to the cache kmalloc-128 of size 128
[ 109.600305] The buggy address is located 1 bytes inside of
[ 109.600305] 128-byte region [ffffffc0336d8a80, ffffffc0336d8b00)
[ 109.613236] The buggy address belongs to the page:
[ 109.618597] page:ffffffbf00cdb600 count:1 mapcount:0 mapping: (null) index:0xffffffc0336d8300 compound_mapcount: 0
[ 109.631068] flags: 0x10200(slab|head)
[ 109.635162] page dumped because: kasan: bad access detected
[ 109.641387]
[ 109.643057] Memory state around the buggy address:
[ 109.648419] ffffffc0336d8980: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.656501] ffffffc0336d8a00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.664583] >ffffffc0336d8a80: 00 fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.672655] ^
[ 109.676565] ffffffc0336d8b00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.684646] ffffffc0336d8b80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 109.692719] ==================================================================
[ 109.736756] kasan test: kmalloc_oob_memset_16 out-of-bounds in memset16
[ 109.744483] ==================================================================
[ 109.752621] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_memset_16+0x84/0xb8 [test_kasan]
[ 109.761866] Write of size 16 at addr ffffffc0336d8301 by task insmod/1204
[ 109.769453]
[ 109.771137] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 109.779214] Hardware name: sun50iw10 (DT)
[ 109.783698] Call trace:
[ 109.786456] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 109.792508] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 109.798173] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 109.803838] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 109.811049] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 109.817099] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 109.823725] [<ffffff90081f72f0>] memset+0x2c/0x4c
[ 109.829034] [<ffffff90007b8e34>] kmalloc_oob_memset_16+0x84/0xb8 [test_kasan]
[ 109.837061] [<ffffff90007b9558>] kmalloc_tests_init+0x48/0x90 [test_kasan]
[ 109.844763] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 109.851011] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 109.857160] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 109.863303] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 109.869641] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 109.875578]
[ 109.877251] Allocated by task 1204:
[ 109.881164] save_stack_trace_tsk+0x0/0x1f4
[ 109.885854] save_stack_trace+0x18/0x20
[ 109.890154] kasan_kmalloc.part.1+0x44/0xec
[ 109.894839] kasan_kmalloc+0x88/0x9c
[ 109.898886] kmalloc_oob_memset_16+0x60/0xb8 [test_kasan]
[ 109.904971] kmalloc_tests_init+0x48/0x90 [test_kasan]
[ 109.910723] do_one_initcall+0xe4/0x1b0
[ 109.915025] do_init_module+0xf0/0x2ac
[ 109.919222] load_module+0x2690/0x2dcc
[ 109.923422] SyS_init_module+0x198/0x224
[ 109.927819] el0_svc_naked+0x34/0x38
[ 109.931818]
[ 109.933490] Freed by task 1042:
[ 109.937013] save_stack_trace_tsk+0x0/0x1f4
[ 109.941702] save_stack_trace+0x18/0x20
[ 109.946001] kasan_slab_free+0x90/0x15c
[ 109.950300] kfree+0xc8/0x258
[ 109.953629] kvfree+0x34/0x3c
[ 109.956961] default_file_splice_read+0x3ac/0x40c
[ 109.962227] do_splice_to+0xa0/0xbc
[ 109.966139] splice_direct_to_actor+0x170/0x2f8
[ 109.971214] do_splice_direct+0xf8/0x148
[ 109.975611] do_sendfile+0x264/0x434
[ 109.979619] SyS_sendfile64+0xe8/0x1a0
[ 109.983819] el0_svc_naked+0x34/0x38
[ 109.987816]
[ 109.989491] The buggy address belongs to the object at ffffffc0336d8300
[ 109.989491] which belongs to the cache kmalloc-128 of size 128
[ 110.003496] The buggy address is located 1 bytes inside of
[ 110.003496] 128-byte region [ffffffc0336d8300, ffffffc0336d8380)
[ 110.016428] The buggy address belongs to the page:
[ 110.021796] page:ffffffbf00cdb600 count:1 mapcount:0 mapping: (null) index:0xffffffc0336d9200 compound_mapcount: 0
[ 110.034261] flags: 0x10200(slab|head)
[ 110.038356] page dumped because: kasan: bad access detected
[ 110.044586]
[ 110.046256] Memory state around the buggy address:
[ 110.051626] ffffffc0336d8200: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.059710] ffffffc0336d8280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.067790] >ffffffc0336d8300: 00 00 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.075862] ^
[ 110.080063] ffffffc0336d8380: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.088145] ffffffc0336d8400: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.096219] ==================================================================
[ 111.313213] kasan test: kmem_cache_oob out-of-bounds in kmem_cache_alloc
[ 111.321336] ==================================================================
[ 111.329474] BUG: KASAN: slab-out-of-bounds in kmem_cache_oob+0x84/0xc0 [test_kasan]
[ 111.338039] Read of size 1 at addr ffffffc0335280d0 by task insmod/1204
[ 111.345432]
[ 111.347115] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 111.355191] Hardware name: sun50iw10 (DT)
[ 111.359677] Call trace:
[ 111.362434] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 111.368480] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 111.374142] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 111.379806] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 111.387021] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 111.393069] [<ffffff90081f6910>] __asan_load1+0x44/0x4c
[ 111.398962] [<ffffff90007b8fa4>] kmem_cache_oob+0x84/0xc0 [test_kasan]
[ 111.406309] [<ffffff90007b9568>] kmalloc_tests_init+0x58/0x90 [test_kasan]
[ 111.414006] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 111.420256] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 111.426398] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 111.432546] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 111.438878] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 111.444819]
[ 111.446492] Allocated by task 1204:
[ 111.450406] save_stack_trace_tsk+0x0/0x1f4
[ 111.455095] save_stack_trace+0x18/0x20
[ 111.459394] kasan_kmalloc.part.1+0x44/0xec
[ 111.464083] kasan_kmalloc+0x88/0x9c
[ 111.468089] kasan_slab_alloc+0x14/0x1c
[ 111.472388] kmem_cache_alloc+0x16c/0x194
[ 111.476915] kmem_cache_oob+0x64/0xc0 [test_kasan]
[ 111.482319] kmalloc_tests_init+0x58/0x90 [test_kasan]
[ 111.488073] do_one_initcall+0xe4/0x1b0
[ 111.492374] do_init_module+0xf0/0x2ac
[ 111.496576] load_module+0x2690/0x2dcc
[ 111.500777] SyS_init_module+0x198/0x224
[ 111.505172] el0_svc_naked+0x34/0x38
[ 111.509169]
[ 111.510839] Freed by task 0:
[ 111.514061] (stack is not available)
[ 111.518056]
[ 111.519730] The buggy address belongs to the object at ffffffc033528008
[ 111.519730] which belongs to the cache test_cache of size 200
[ 111.533639] The buggy address is located 0 bytes to the right of
[ 111.533639] 200-byte region [ffffffc033528008, ffffffc0335280d0)
[ 111.547151] The buggy address belongs to the page:
[ 111.552516] page:ffffffbf00cd4a00 count:1 mapcount:0 mapping: (null) index:0xffffffc03352bc68 compound_mapcount: 0
[ 111.564981] flags: 0x10200(slab|head)
[ 111.569079] page dumped because: kasan: bad access detected
[ 111.575309]
[ 111.576980] Memory state around the buggy address:
[ 111.582348] ffffffc033527f80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 111.590424] ffffffc033528000: fc 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 111.598504] >ffffffc033528080: 00 00 00 00 00 00 00 00 00 00 fc fc fc fc fc fc
[ 111.606583] ^
[ 111.613111] ffffffc033528100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 111.621193] ffffffc033528180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 111.629268] ==================================================================
[ 111.659883] kasan test: kasan_stack_oob out-of-bounds on stack
[ 111.666977] ==================================================================
[ 111.675115] BUG: KASAN: stack-out-of-bounds in kasan_stack_oob+0x9c/0xd0 [test_kasan]
[ 111.683875] Read of size 1 at addr ffffffc03248f97a by task insmod/1204
[ 111.691268]
[ 111.692950] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 111.701024] Hardware name: sun50iw10 (DT)
[ 111.705508] Call trace:
[ 111.708266] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 111.714318] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 111.719979] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 111.725645] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 111.732858] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 111.738908] [<ffffff90081f6910>] __asan_load1+0x44/0x4c
[ 111.744800] [<ffffff90007b809c>] kasan_stack_oob+0x9c/0xd0 [test_kasan]
[ 111.752242] [<ffffff90007b956c>] kmalloc_tests_init+0x5c/0x90 [test_kasan]
[ 111.759941] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 111.766188] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 111.772338] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 111.778481] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 111.784817] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 111.790757]
[ 111.792429] The buggy address belongs to the page:
[ 111.797792] page:ffffffbf00c923c0 count:0 mapcount:0 mapping: (null) index:0x0
[ 111.806750] flags: 0x0()
[ 111.809583] page dumped because: kasan: bad access detected
[ 111.815808]
[ 111.817479] Memory state around the buggy address:
[ 111.822847] ffffffc03248f800: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 111.830931] ffffffc03248f880: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 111.839014] >ffffffc03248f900: 00 00 f1 f1 f1 f1 04 f4 f4 f4 f2 f2 f2 f2 00 02
[ 111.847088] ^
[ 111.855072] ffffffc03248f980: f4 f4 f3 f3 f3 f3 00 00 00 00 00 00 00 00 00 00
[ 111.863150] ffffffc03248fa00: 00 00 00 00 f1 f1 f1 f1 00 00 00 00 00 00 00 00
[ 111.871221] ==================================================================
[ 111.884645] kasan test: kasan_global_oob out-of-bounds global variable
[ 111.895041] ==================================================================
[ 111.903174] BUG: KASAN: global-out-of-bounds in kasan_global_oob+0x90/0xd0 [test_kasan]
[ 111.912130] Read of size 1 at addr ffffff90007b288d by task insmod/1204
[ 111.919526]
[ 111.921208] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 111.929283] Hardware name: sun50iw10 (DT)
[ 111.933765] Call trace:
[ 111.936521] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 111.942570] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 111.948235] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 111.953899] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 111.961114] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 111.967160] [<ffffff90081f6910>] __asan_load1+0x44/0x4c
[ 111.973054] [<ffffff90007b8160>] kasan_global_oob+0x90/0xd0 [test_kasan]
[ 111.980597] [<ffffff90007b9570>] kmalloc_tests_init+0x60/0x90 [test_kasan]
[ 111.988292] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 111.994541] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 112.000684] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 112.006830] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 112.013165] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 112.019103]
[ 112.020773] The buggy address belongs to the variable:
[ 112.026562] global_array+0xd/0xffffffffffffd7d0 [test_kasan]
[ 112.032984]
[ 112.034655] Memory state around the buggy address:
[ 112.040022] ffffff90007b2780: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 112.048104] ffffff90007b2800: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 112.056187] >ffffff90007b2880: 00 02 fa fa fa fa fa fa 00 00 00 00 00 00 00 00
[ 112.064259] ^
[ 112.068169] ffffff90007b2900: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 112.076248] ffffff90007b2980: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 112.084323] ==================================================================
[ 112.097127] kasan test: kasan_alloca_oob_left out-of-bounds to left on alloca
[ 112.107198] kasan test: kasan_alloca_oob_right out-of-bounds to right on alloca
[ 112.115763] kasan test: ksize_unpoisons_memory ksize() unpoisons the whole allocated chunk
[ 112.125481] ==================================================================
[ 112.133608] BUG: KASAN: slab-out-of-bounds in ksize_unpoisons_memory+0x9c/0xe0 [test_kasan]
[ 112.142953] Write of size 1 at addr ffffffc032ecfa80 by task insmod/1204
[ 112.150441]
[ 112.152123] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 112.160199] Hardware name: sun50iw10 (DT)
[ 112.164685] Call trace:
[ 112.167437] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 112.173487] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 112.179147] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 112.184810] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 112.192027] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 112.198077] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 112.204064] [<ffffff90007b9224>] ksize_unpoisons_memory+0x9c/0xe0 [test_kasan]
[ 112.212188] [<ffffff90007b957c>] kmalloc_tests_init+0x6c/0x90 [test_kasan]
[ 112.219884] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 112.226127] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 112.232271] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 112.238415] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 112.244750] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 112.250690]
[ 112.252362] Allocated by task 1204:
[ 112.256276] save_stack_trace_tsk+0x0/0x1f4
[ 112.260962] save_stack_trace+0x18/0x20
[ 112.265260] kasan_kmalloc.part.1+0x44/0xec
[ 112.269945] kasan_kmalloc+0x88/0x9c
[ 112.273992] ksize_unpoisons_memory+0x64/0xe0 [test_kasan]
[ 112.280171] kmalloc_tests_init+0x6c/0x90 [test_kasan]
[ 112.285926] do_one_initcall+0xe4/0x1b0
[ 112.290228] do_init_module+0xf0/0x2ac
[ 112.294429] load_module+0x2690/0x2dcc
[ 112.298633] SyS_init_module+0x198/0x224
[ 112.303026] el0_svc_naked+0x34/0x38
[ 112.307023]
[ 112.308697] Freed by task 1051:
[ 112.312222] save_stack_trace_tsk+0x0/0x1f4
[ 112.316910] save_stack_trace+0x18/0x20
[ 112.321213] kasan_slab_free+0x90/0x15c
[ 112.325509] kfree+0xc8/0x258
[ 112.328842] load_elf_binary+0xcbc/0x182c
[ 112.333337] search_binary_handler+0xc8/0x264
[ 112.338216] do_execveat_common.isra.14+0x8a4/0xa34
[ 112.343672] do_execve+0x28/0x30
[ 112.347289] SyS_execve+0x24/0x34
[ 112.351005] el0_svc_naked+0x34/0x38
[ 112.355002]
[ 112.356676] The buggy address belongs to the object at ffffffc032ecfa00
[ 112.356676] which belongs to the cache kmalloc-128 of size 128
[ 112.370670] The buggy address is located 0 bytes to the right of
[ 112.370670] 128-byte region [ffffffc032ecfa00, ffffffc032ecfa80)
[ 112.384183] The buggy address belongs to the page:
[ 112.389547] page:ffffffbf00cbb300 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 112.400558] flags: 0x10200(slab|head)
[ 112.404656] page dumped because: kasan: bad access detected
[ 112.410887]
[ 112.412555] Memory state around the buggy address:
[ 112.417923] ffffffc032ecf980: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.426004] ffffffc032ecfa00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 112.434084] >ffffffc032ecfa80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.442160] ^
[ 112.445778] ffffffc032ecfb00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.453861] ffffffc032ecfb80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.461934] ==================================================================
[ 112.479913] kasan test: copy_user_test out-of-bounds in copy_from_user()
[ 112.505686] ==================================================================
[ 112.513842] BUG: KASAN: slab-out-of-bounds in copy_user_test+0xa8/0x2a8 [test_kasan]
[ 112.522506] Write of size 11 at addr ffffffc032e2d200 by task insmod/1204
[ 112.530097]
[ 112.531781] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 112.539857] Hardware name: sun50iw10 (DT)
[ 112.544344] Call trace:
[ 112.547101] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 112.553151] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 112.558816] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 112.564484] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 112.571697] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 112.577750] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 112.584381] [<ffffff90081f6ee8>] kasan_check_write+0x18/0x20
[ 112.590755] [<ffffff90007b9310>] copy_user_test+0xa8/0x2a8 [test_kasan]
[ 112.598194] [<ffffff90007b9580>] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 112.605891] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 112.612138] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 112.618280] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 112.624425] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 112.630763] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 112.636701]
[ 112.638373] Allocated by task 1204:
[ 112.642287] save_stack_trace_tsk+0x0/0x1f4
[ 112.646973] save_stack_trace+0x18/0x20
[ 112.651273] kasan_kmalloc.part.1+0x44/0xec
[ 112.655962] kasan_kmalloc+0x88/0x9c
[ 112.660010] copy_user_test+0x50/0x2a8 [test_kasan]
[ 112.665510] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 112.671264] do_one_initcall+0xe4/0x1b0
[ 112.675567] do_init_module+0xf0/0x2ac
[ 112.679759] load_module+0x2690/0x2dcc
[ 112.683961] SyS_init_module+0x198/0x224
[ 112.688356] el0_svc_naked+0x34/0x38
[ 112.692352]
[ 112.694023] Freed by task 1051:
[ 112.697544] save_stack_trace_tsk+0x0/0x1f4
[ 112.702232] save_stack_trace+0x18/0x20
[ 112.706532] kasan_slab_free+0x90/0x15c
[ 112.710829] kfree+0xc8/0x258
[ 112.714158] kvfree+0x34/0x3c
[ 112.717486] default_file_splice_read+0x3ac/0x40c
[ 112.722754] do_splice_to+0xa0/0xbc
[ 112.726664] splice_direct_to_actor+0x170/0x2f8
[ 112.731739] do_splice_direct+0xf8/0x148
[ 112.736135] do_sendfile+0x264/0x434
[ 112.740143] SyS_sendfile64+0xe8/0x1a0
[ 112.744343] el0_svc_naked+0x34/0x38
[ 112.748350]
[ 112.750039] The buggy address belongs to the object at ffffffc032e2d200
[ 112.750039] which belongs to the cache kmalloc-128 of size 128
[ 112.764139] The buggy address is located 0 bytes inside of
[ 112.764139] 128-byte region [ffffffc032e2d200, ffffffc032e2d280)
[ 112.777067] The buggy address belongs to the page:
[ 112.782429] page:ffffffbf00cb8b00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 112.793439] flags: 0x10200(slab|head)
[ 112.797535] page dumped because: kasan: bad access detected
[ 112.803763]
[ 112.805433] Memory state around the buggy address:
[ 112.810801] ffffffc032e2d100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.818877] ffffffc032e2d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.826955] >ffffffc032e2d200: 00 02 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.835024] ^
[ 112.838931] ffffffc032e2d280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.847009] ffffffc032e2d300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 112.855094] ==================================================================
[ 112.901800] kasan test: copy_user_test out-of-bounds in copy_to_user()
[ 112.917653] ==================================================================
[ 112.925798] BUG: KASAN: slab-out-of-bounds in copy_user_test+0x114/0x2a8 [test_kasan]
[ 112.934558] Read of size 11 at addr ffffffc032e2d200 by task insmod/1204
[ 112.942053]
[ 112.943738] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 112.951808] Hardware name: sun50iw10 (DT)
[ 112.956292] Call trace:
[ 112.959049] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 112.965099] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 112.970760] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 112.976421] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 112.983632] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 112.989682] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 112.996309] [<ffffff90081f6ec8>] kasan_check_read+0x18/0x20
[ 113.002588] [<ffffff90007b937c>] copy_user_test+0x114/0x2a8 [test_kasan]
[ 113.010128] [<ffffff90007b9580>] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 113.017825] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 113.024070] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 113.030214] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 113.036354] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 113.042686] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 113.048623]
[ 113.050294] Allocated by task 1204:
[ 113.054207] save_stack_trace_tsk+0x0/0x1f4
[ 113.058895] save_stack_trace+0x18/0x20
[ 113.063193] kasan_kmalloc.part.1+0x44/0xec
[ 113.067879] kasan_kmalloc+0x88/0x9c
[ 113.071926] copy_user_test+0x50/0x2a8 [test_kasan]
[ 113.077425] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 113.083176] do_one_initcall+0xe4/0x1b0
[ 113.087476] do_init_module+0xf0/0x2ac
[ 113.091678] load_module+0x2690/0x2dcc
[ 113.095878] SyS_init_module+0x198/0x224
[ 113.100271] el0_svc_naked+0x34/0x38
[ 113.104271]
[ 113.105941] Freed by task 1051:
[ 113.109466] save_stack_trace_tsk+0x0/0x1f4
[ 113.114153] save_stack_trace+0x18/0x20
[ 113.118455] kasan_slab_free+0x90/0x15c
[ 113.122753] kfree+0xc8/0x258
[ 113.126082] kvfree+0x34/0x3c
[ 113.129412] default_file_splice_read+0x3ac/0x40c
[ 113.134678] do_splice_to+0xa0/0xbc
[ 113.138587] splice_direct_to_actor+0x170/0x2f8
[ 113.143658] do_splice_direct+0xf8/0x148
[ 113.148054] do_sendfile+0x264/0x434
[ 113.152066] SyS_sendfile64+0xe8/0x1a0
[ 113.156266] el0_svc_naked+0x34/0x38
[ 113.160263]
[ 113.161939] The buggy address belongs to the object at ffffffc032e2d200
[ 113.161939] which belongs to the cache kmalloc-128 of size 128
[ 113.175936] The buggy address is located 0 bytes inside of
[ 113.175936] 128-byte region [ffffffc032e2d200, ffffffc032e2d280)
[ 113.188867] The buggy address belongs to the page:
[ 113.194227] page:ffffffbf00cb8b00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 113.205233] flags: 0x10200(slab|head)
[ 113.209331] page dumped because: kasan: bad access detected
[ 113.215560]
[ 113.217228] Memory state around the buggy address:
[ 113.222596] ffffffc032e2d100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.230681] ffffffc032e2d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.238759] >ffffffc032e2d200: 00 02 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.246830] ^
[ 113.250741] ffffffc032e2d280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.258821] ffffffc032e2d300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.266892] ==================================================================
[ 113.311514] kasan test: copy_user_test out-of-bounds in __copy_from_user()
[ 113.319459] ==================================================================
[ 113.327593] BUG: KASAN: slab-out-of-bounds in copy_user_test+0x170/0x2a8 [test_kasan]
[ 113.336350] Write of size 11 at addr ffffffc032e2d200 by task insmod/1204
[ 113.343937]
[ 113.345622] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 113.353692] Hardware name: sun50iw10 (DT)
[ 113.358177] Call trace:
[ 113.360934] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 113.366984] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 113.372645] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 113.378310] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 113.385520] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 113.391568] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 113.398197] [<ffffff90081f6ee8>] kasan_check_write+0x18/0x20
[ 113.404573] [<ffffff90007b93d8>] copy_user_test+0x170/0x2a8 [test_kasan]
[ 113.412115] [<ffffff90007b9580>] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 113.419814] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 113.426062] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 113.432209] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 113.438352] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 113.444686] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 113.450623]
[ 113.452295] Allocated by task 1204:
[ 113.456208] save_stack_trace_tsk+0x0/0x1f4
[ 113.460894] save_stack_trace+0x18/0x20
[ 113.465193] kasan_kmalloc.part.1+0x44/0xec
[ 113.469879] kasan_kmalloc+0x88/0x9c
[ 113.473922] copy_user_test+0x50/0x2a8 [test_kasan]
[ 113.479421] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 113.485174] do_one_initcall+0xe4/0x1b0
[ 113.489472] do_init_module+0xf0/0x2ac
[ 113.493672] load_module+0x2690/0x2dcc
[ 113.497870] SyS_init_module+0x198/0x224
[ 113.502261] el0_svc_naked+0x34/0x38
[ 113.506260]
[ 113.507932] Freed by task 1051:
[ 113.511456] save_stack_trace_tsk+0x0/0x1f4
[ 113.516143] save_stack_trace+0x18/0x20
[ 113.520445] kasan_slab_free+0x90/0x15c
[ 113.524740] kfree+0xc8/0x258
[ 113.528071] kvfree+0x34/0x3c
[ 113.531401] default_file_splice_read+0x3ac/0x40c
[ 113.536667] do_splice_to+0xa0/0xbc
[ 113.540576] splice_direct_to_actor+0x170/0x2f8
[ 113.545649] do_splice_direct+0xf8/0x148
[ 113.550048] do_sendfile+0x264/0x434
[ 113.554057] SyS_sendfile64+0xe8/0x1a0
[ 113.558257] el0_svc_naked+0x34/0x38
[ 113.562254]
[ 113.563929] The buggy address belongs to the object at ffffffc032e2d200
[ 113.563929] which belongs to the cache kmalloc-128 of size 128
[ 113.577940] The buggy address is located 0 bytes inside of
[ 113.577940] 128-byte region [ffffffc032e2d200, ffffffc032e2d280)
[ 113.590869] The buggy address belongs to the page:
[ 113.596229] page:ffffffbf00cb8b00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 113.607235] flags: 0x10200(slab|head)
[ 113.611329] page dumped because: kasan: bad access detected
[ 113.617555]
[ 113.619226] Memory state around the buggy address:
[ 113.624590] ffffffc032e2d100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.632673] ffffffc032e2d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.640756] >ffffffc032e2d200: 00 02 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.648830] ^
[ 113.652737] ffffffc032e2d280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.660817] ffffffc032e2d300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 113.668887] ==================================================================
[ 113.681967] kasan test: copy_user_test out-of-bounds in __copy_to_user()
[ 113.699836] ==================================================================
[ 113.707971] BUG: KASAN: slab-out-of-bounds in copy_user_test+0x1ac/0x2a8 [test_kasan]
[ 113.716727] Read of size 11 at addr ffffffc032e2d200 by task insmod/1204
[ 113.724216]
[ 113.725899] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 113.733969] Hardware name: sun50iw10 (DT)
[ 113.738452] Call trace:
[ 113.741207] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 113.747256] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 113.752917] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 113.758579] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 113.765792] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 113.771842] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 113.778471] [<ffffff90081f6ec8>] kasan_check_read+0x18/0x20
[ 113.784747] [<ffffff90007b9414>] copy_user_test+0x1ac/0x2a8 [test_kasan]
[ 113.792284] [<ffffff90007b9580>] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 113.799979] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 113.806224] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 113.812370] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 113.818512] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 113.824849] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 113.830786]
[ 113.832460] Allocated by task 1204:
[ 113.836372] save_stack_trace_tsk+0x0/0x1f4
[ 113.841063] save_stack_trace+0x18/0x20
[ 113.845364] kasan_kmalloc.part.1+0x44/0xec
[ 113.850049] kasan_kmalloc+0x88/0x9c
[ 113.854098] copy_user_test+0x50/0x2a8 [test_kasan]
[ 113.859598] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 113.865352] do_one_initcall+0xe4/0x1b0
[ 113.869652] do_init_module+0xf0/0x2ac
[ 113.873855] load_module+0x2690/0x2dcc
[ 113.878059] SyS_init_module+0x198/0x224
[ 113.882452] el0_svc_naked+0x34/0x38
[ 113.886452]
[ 113.888123] Freed by task 1051:
[ 113.891650] save_stack_trace_tsk+0x0/0x1f4
[ 113.896339] save_stack_trace+0x18/0x20
[ 113.900637] kasan_slab_free+0x90/0x15c
[ 113.904932] kfree+0xc8/0x258
[ 113.908263] kvfree+0x34/0x3c
[ 113.911595] default_file_splice_read+0x3ac/0x40c
[ 113.916862] do_splice_to+0xa0/0xbc
[ 113.920772] splice_direct_to_actor+0x170/0x2f8
[ 113.925844] do_splice_direct+0xf8/0x148
[ 113.930238] do_sendfile+0x264/0x434
[ 113.934249] SyS_sendfile64+0xe8/0x1a0
[ 113.938448] el0_svc_naked+0x34/0x38
[ 113.942446]
[ 113.944122] The buggy address belongs to the object at ffffffc032e2d200
[ 113.944122] which belongs to the cache kmalloc-128 of size 128
[ 113.958124] The buggy address is located 0 bytes inside of
[ 113.958124] 128-byte region [ffffffc032e2d200, ffffffc032e2d280)
[ 113.971051] The buggy address belongs to the page:
[ 113.976415] page:ffffffbf00cb8b00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 113.987435] flags: 0x10200(slab|head)
[ 113.991529] page dumped because: kasan: bad access detected
[ 113.997756]
[ 113.999425] Memory state around the buggy address:
[ 114.004792] ffffffc032e2d100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.012870] ffffffc032e2d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.020953] >ffffffc032e2d200: 00 02 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.029024] ^
[ 114.032931] ffffffc032e2d280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.041012] ffffffc032e2d300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.049083] ==================================================================
[ 114.062173] kasan test: copy_user_test out-of-bounds in __copy_from_user_inatomic()
[ 114.081086] ==================================================================
[ 114.089222] BUG: KASAN: slab-out-of-bounds in copy_user_test+0x1e8/0x2a8 [test_kasan]
[ 114.097978] Write of size 11 at addr ffffffc032e2d200 by task insmod/1204
[ 114.105562]
[ 114.107245] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 114.115326] Hardware name: sun50iw10 (DT)
[ 114.119811] Call trace:
[ 114.122568] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 114.128615] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 114.134276] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 114.139940] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 114.147152] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 114.153205] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 114.159832] [<ffffff90081f6ee8>] kasan_check_write+0x18/0x20
[ 114.166206] [<ffffff90007b9450>] copy_user_test+0x1e8/0x2a8 [test_kasan]
[ 114.173748] [<ffffff90007b9580>] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 114.181441] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 114.187683] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 114.193826] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 114.199968] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 114.206300] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 114.212238]
[ 114.213908] Allocated by task 1204:
[ 114.217819] save_stack_trace_tsk+0x0/0x1f4
[ 114.222506] save_stack_trace+0x18/0x20
[ 114.226806] kasan_kmalloc.part.1+0x44/0xec
[ 114.231493] kasan_kmalloc+0x88/0x9c
[ 114.235538] copy_user_test+0x50/0x2a8 [test_kasan]
[ 114.241037] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 114.246788] do_one_initcall+0xe4/0x1b0
[ 114.251088] do_init_module+0xf0/0x2ac
[ 114.255287] load_module+0x2690/0x2dcc
[ 114.259488] SyS_init_module+0x198/0x224
[ 114.263880] el0_svc_naked+0x34/0x38
[ 114.267877]
[ 114.269549] Freed by task 1051:
[ 114.273077] save_stack_trace_tsk+0x0/0x1f4
[ 114.277766] save_stack_trace+0x18/0x20
[ 114.282066] kasan_slab_free+0x90/0x15c
[ 114.286362] kfree+0xc8/0x258
[ 114.289691] kvfree+0x34/0x3c
[ 114.293020] default_file_splice_read+0x3ac/0x40c
[ 114.298290] do_splice_to+0xa0/0xbc
[ 114.302199] splice_direct_to_actor+0x170/0x2f8
[ 114.307275] do_splice_direct+0xf8/0x148
[ 114.311672] do_sendfile+0x264/0x434
[ 114.315682] SyS_sendfile64+0xe8/0x1a0
[ 114.319883] el0_svc_naked+0x34/0x38
[ 114.323880]
[ 114.325553] The buggy address belongs to the object at ffffffc032e2d200
[ 114.325553] which belongs to the cache kmalloc-128 of size 128
[ 114.339554] The buggy address is located 0 bytes inside of
[ 114.339554] 128-byte region [ffffffc032e2d200, ffffffc032e2d280)
[ 114.352484] The buggy address belongs to the page:
[ 114.357845] page:ffffffbf00cb8b00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 114.368852] flags: 0x10200(slab|head)
[ 114.372946] page dumped because: kasan: bad access detected
[ 114.379174]
[ 114.380841] Memory state around the buggy address:
[ 114.386215] ffffffc032e2d100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.394297] ffffffc032e2d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.402379] >ffffffc032e2d200: 00 02 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.410449] ^
[ 114.414358] ffffffc032e2d280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.422437] ffffffc032e2d300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.430505] ==================================================================
[ 114.448292] kasan test: copy_user_test out-of-bounds in __copy_to_user_inatomic()
[ 114.477216] ==================================================================
[ 114.485366] BUG: KASAN: slab-out-of-bounds in copy_user_test+0x224/0x2a8 [test_kasan]
[ 114.494127] Read of size 11 at addr ffffffc032e2d200 by task insmod/1204
[ 114.501616]
[ 114.503301] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 114.511372] Hardware name: sun50iw10 (DT)
[ 114.515855] Call trace:
[ 114.518613] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 114.524663] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 114.530324] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 114.535987] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 114.543205] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 114.549254] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 114.555890] [<ffffff90081f6ec8>] kasan_check_read+0x18/0x20
[ 114.562171] [<ffffff90007b948c>] copy_user_test+0x224/0x2a8 [test_kasan]
[ 114.569706] [<ffffff90007b9580>] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 114.577403] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 114.583644] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 114.589790] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 114.595932] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 114.602268] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 114.608206]
[ 114.609880] Allocated by task 1204:
[ 114.613794] save_stack_trace_tsk+0x0/0x1f4
[ 114.618479] save_stack_trace+0x18/0x20
[ 114.622779] kasan_kmalloc.part.1+0x44/0xec
[ 114.627466] kasan_kmalloc+0x88/0x9c
[ 114.631511] copy_user_test+0x50/0x2a8 [test_kasan]
[ 114.637014] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 114.642762] do_one_initcall+0xe4/0x1b0
[ 114.647064] do_init_module+0xf0/0x2ac
[ 114.651262] load_module+0x2690/0x2dcc
[ 114.655464] SyS_init_module+0x198/0x224
[ 114.659859] el0_svc_naked+0x34/0x38
[ 114.663856]
[ 114.665526] Freed by task 1051:
[ 114.669053] save_stack_trace_tsk+0x0/0x1f4
[ 114.673740] save_stack_trace+0x18/0x20
[ 114.678040] kasan_slab_free+0x90/0x15c
[ 114.682337] kfree+0xc8/0x258
[ 114.685665] kvfree+0x34/0x3c
[ 114.688999] default_file_splice_read+0x3ac/0x40c
[ 114.694265] do_splice_to+0xa0/0xbc
[ 114.698175] splice_direct_to_actor+0x170/0x2f8
[ 114.703246] do_splice_direct+0xf8/0x148
[ 114.707642] do_sendfile+0x264/0x434
[ 114.711650] SyS_sendfile64+0xe8/0x1a0
[ 114.715852] el0_svc_naked+0x34/0x38
[ 114.719849]
[ 114.721526] The buggy address belongs to the object at ffffffc032e2d200
[ 114.721526] which belongs to the cache kmalloc-128 of size 128
[ 114.735531] The buggy address is located 0 bytes inside of
[ 114.735531] 128-byte region [ffffffc032e2d200, ffffffc032e2d280)
[ 114.748456] The buggy address belongs to the page:
[ 114.753817] page:ffffffbf00cb8b00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 114.764831] flags: 0x10200(slab|head)
[ 114.768928] page dumped because: kasan: bad access detected
[ 114.775153]
[ 114.776821] Memory state around the buggy address:
[ 114.782187] ffffffc032e2d100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.790268] ffffffc032e2d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.798345] >ffffffc032e2d200: 00 02 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.806417] ^
[ 114.810327] ffffffc032e2d280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.818406] ffffffc032e2d300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 114.826479] ==================================================================
[ 114.873765] kasan test: copy_user_test out-of-bounds in strncpy_from_user()
[ 114.889592] ==================================================================
[ 114.897701] BUG: KASAN: slab-out-of-bounds in strncpy_from_user+0x70/0x214
[ 114.905395] Write of size 11 at addr ffffffc032e2d200 by task insmod/1204
[ 114.912978]
[ 114.914662] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 114.922739] Hardware name: sun50iw10 (DT)
[ 114.927222] Call trace:
[ 114.929977] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 114.936022] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 114.941681] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 114.947343] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 114.954554] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 114.960602] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 114.967231] [<ffffff90081f6ee8>] kasan_check_write+0x18/0x20
[ 114.973568] [<ffffff90083e0f6c>] strncpy_from_user+0x70/0x214
[ 114.980046] [<ffffff90007b94cc>] copy_user_test+0x264/0x2a8 [test_kasan]
[ 114.987587] [<ffffff90007b9580>] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 114.995281] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 115.001534] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 115.007675] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 115.013819] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 115.020155] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 115.026094]
[ 115.027767] Allocated by task 1204:
[ 115.031677] save_stack_trace_tsk+0x0/0x1f4
[ 115.036366] save_stack_trace+0x18/0x20
[ 115.040668] kasan_kmalloc.part.1+0x44/0xec
[ 115.045345] kasan_kmalloc+0x88/0x9c
[ 115.049390] copy_user_test+0x50/0x2a8 [test_kasan]
[ 115.054890] kmalloc_tests_init+0x70/0x90 [test_kasan]
[ 115.060642] do_one_initcall+0xe4/0x1b0
[ 115.064940] do_init_module+0xf0/0x2ac
[ 115.069138] load_module+0x2690/0x2dcc
[ 115.073339] SyS_init_module+0x198/0x224
[ 115.077734] el0_svc_naked+0x34/0x38
[ 115.081731]
[ 115.083402] Freed by task 1051:
[ 115.086925] save_stack_trace_tsk+0x0/0x1f4
[ 115.091612] save_stack_trace+0x18/0x20
[ 115.095910] kasan_slab_free+0x90/0x15c
[ 115.100207] kfree+0xc8/0x258
[ 115.103537] kvfree+0x34/0x3c
[ 115.106867] default_file_splice_read+0x3ac/0x40c
[ 115.112135] do_splice_to+0xa0/0xbc
[ 115.116047] splice_direct_to_actor+0x170/0x2f8
[ 115.121119] do_splice_direct+0xf8/0x148
[ 115.125513] do_sendfile+0x264/0x434
[ 115.129520] SyS_sendfile64+0xe8/0x1a0
[ 115.133722] el0_svc_naked+0x34/0x38
[ 115.137721]
[ 115.139396] The buggy address belongs to the object at ffffffc032e2d200
[ 115.139396] which belongs to the cache kmalloc-128 of size 128
[ 115.153396] The buggy address is located 0 bytes inside of
[ 115.153396] 128-byte region [ffffffc032e2d200, ffffffc032e2d280)
[ 115.166322] The buggy address belongs to the page:
[ 115.171684] page:ffffffbf00cb8b00 count:1 mapcount:0 mapping: (null) index:0x0 compound_mapcount: 0
[ 115.182689] flags: 0x10200(slab|head)
[ 115.186787] page dumped because: kasan: bad access detected
[ 115.193013]
[ 115.194682] Memory state around the buggy address:
[ 115.200049] ffffffc032e2d100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 115.208128] ffffffc032e2d180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 115.216205] >ffffffc032e2d200: 00 02 fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 115.224279] ^
[ 115.228187] ffffffc032e2d280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 115.236263] ffffffc032e2d300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 115.244332] ==================================================================
分析
- 从上述log,kasan提示这时一个越界访问的错误类型(BUG: KASAN: slab-out-of-bounds in xxxx),并显示出错的函数名称,出错信息提示,出错附近内存状况和出错位置。可以利用gdb+符号表查看源码,以kmalloc_oob_right 为例:
$ ./out/gcc-linaro-5.3.1-2016.05-x86_64_aarch64-linux-gnu/bin/aarch64-linux-gnu-gdb ~/link/kernel/linux-4.9/lib/test_kasan.ko
GNU gdb (Linaro_GDB-2016.05) 7.11.1.20160702-git
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "--host=x86_64-unknown-linux-gnu --target=aarch64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from /home1/weidonghui/link/kernel/linux-4.9/lib/test_kasan.ko...done.
(gdb) list *kmalloc_oob_right+0x7c
0x3d4 is in kmalloc_oob_right (lib/test_kasan.c:41).
36 if (!ptr) {
37 pr_err("Allocation failed\n");
38 return;
39 }
40
41 ptr[size] = 'x';
42 kfree(ptr);
43 }
44
(gdb)
访问已经释放的内存(use-after-free)
实例源码
- 实例包括
- kmalloc_uaf:向释放已内存赋值。
- kmalloc_uaf_memset:用memset向释放已内存赋值。
- kmalloc_uaf2:向释放已内存赋值。
#define pr_fmt(fmt) "kasan test: %s " fmt, __func__
#include <linux/kernel.h>
#include <linux/mman.h>
#include <linux/mm.h>
#include <linux/printk.h>
#include <linux/slab.h>
#include <linux/string.h>
#include <linux/uaccess.h>
#include <linux/module.h>
#include <linux/kasan.h>
static noinline void __init kmalloc_uaf(void)
{
char *ptr;
size_t size = 10;
pr_info("use-after-free\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
kfree(ptr);
*(ptr + 8) = 'x';
}
static noinline void __init kmalloc_uaf_memset(void)
{
char *ptr;
size_t size = 33;
pr_info("use-after-free in memset\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
kfree(ptr);
memset(ptr, 0, size);
}
static noinline void __init kmalloc_uaf2(void)
{
char *ptr1, *ptr2;
size_t size = 43;
pr_info("use-after-free after another kmalloc\n");
ptr1 = kmalloc(size, GFP_KERNEL);
if (!ptr1) {
pr_err("Allocation failed\n");
return;
}
kfree(ptr1);
ptr2 = kmalloc(size, GFP_KERNEL);
if (!ptr2) {
pr_err("Allocation failed\n");
return;
}
ptr1[40] = 'x';
if (ptr1 == ptr2)
pr_err("Could not detect use-after-free: ptr1 == ptr2\n");
kfree(ptr2);
}
static int __init kmalloc_tests_init(void)
{
/*
* Temporarily enable multi-shot mode. Otherwise, we'd only get a
* report for the first case.
*/
bool multishot = kasan_save_enable_multi_shot();
kmalloc_uaf();
kmalloc_uaf_memset();
kmalloc_uaf2();
kasan_restore_multi_shot(multishot);
return -EAGAIN;
}
module_init(kmalloc_tests_init);
MODULE_LICENSE("GPL");
输出log
/ # insmod lib/modules/4.9.191/test_kasan.ko
[ 110.109605] kasan test: kmalloc_uaf use-after-free
[ 110.124350] ==================================================================
[ 110.132481] BUG: KASAN: use-after-free in kmalloc_uaf+0x84/0xb8 [test_kasan]
[ 110.140365] Write of size 1 at addr ffffffc0336d9208 by task insmod/1204
[ 110.147856]
[ 110.149540] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 110.157613] Hardware name: sun50iw10 (DT)
[ 110.162098] Call trace:
[ 110.164853] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 110.170900] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 110.176563] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 110.182225] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 110.189436] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 110.195485] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 110.201473] [<ffffff90007b87d4>] kmalloc_uaf+0x84/0xb8 [test_kasan]
[ 110.208528] [<ffffff90007b955c>] kmalloc_tests_init+0x4c/0x90 [test_kasan]
[ 110.216227] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 110.222471] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 110.228615] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 110.234762] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 110.241095] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 110.247032]
[ 110.248704] Allocated by task 1204:
[ 110.252619] save_stack_trace_tsk+0x0/0x1f4
[ 110.257307] save_stack_trace+0x18/0x20
[ 110.261607] kasan_kmalloc.part.1+0x44/0xec
[ 110.266295] kasan_kmalloc+0x88/0x9c
[ 110.270338] kmalloc_uaf+0x60/0xb8 [test_kasan]
[ 110.275450] kmalloc_tests_init+0x4c/0x90 [test_kasan]
[ 110.281204] do_one_initcall+0xe4/0x1b0
[ 110.285504] do_init_module+0xf0/0x2ac
[ 110.289701] load_module+0x2690/0x2dcc
[ 110.293902] SyS_init_module+0x198/0x224
[ 110.298294] el0_svc_naked+0x34/0x38
[ 110.302293]
[ 110.303962] Freed by task 1204:
[ 110.307486] save_stack_trace_tsk+0x0/0x1f4
[ 110.312173] save_stack_trace+0x18/0x20
[ 110.316470] kasan_slab_free+0x90/0x15c
[ 110.320767] kfree+0xc8/0x258
[ 110.324133] kmalloc_uaf+0x7c/0xb8 [test_kasan]
[ 110.329245] kmalloc_tests_init+0x4c/0x90 [test_kasan]
[ 110.334999] do_one_initcall+0xe4/0x1b0
[ 110.339304] do_init_module+0xf0/0x2ac
[ 110.343503] load_module+0x2690/0x2dcc
[ 110.347702] SyS_init_module+0x198/0x224
[ 110.352098] el0_svc_naked+0x34/0x38
[ 110.356096]
[ 110.357773] The buggy address belongs to the object at ffffffc0336d9200
[ 110.357773] which belongs to the cache kmalloc-128 of size 128
[ 110.371780] The buggy address is located 8 bytes inside of
[ 110.371780] 128-byte region [ffffffc0336d9200, ffffffc0336d9280)
[ 110.384708] The buggy address belongs to the page:
[ 110.390073] page:ffffffbf00cdb600 count:1 mapcount:0 mapping: (null) index:0xffffffc0336dab00 compound_mapcount: 0
[ 110.402539] flags: 0x10200(slab|head)
[ 110.406635] page dumped because: kasan: bad access detected
[ 110.412860]
[ 110.414530] Memory state around the buggy address:
[ 110.419901] ffffffc0336d9100: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.427984] ffffffc0336d9180: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.436064] >ffffffc0336d9200: fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb
[ 110.444138] ^
[ 110.448045] ffffffc0336d9280: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.456125] ffffffc0336d9300: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.464202] ==================================================================
[ 110.489110] kasan test: kmalloc_uaf_memset use-after-free in memset
[ 110.496258] ==================================================================
[ 110.504390] BUG: KASAN: use-after-free in kmalloc_uaf_memset+0x8c/0xb8 [test_kasan]
[ 110.512953] Write of size 33 at addr ffffffc0336dab00 by task insmod/1204
[ 110.520540]
[ 110.522221] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 110.530298] Hardware name: sun50iw10 (DT)
[ 110.534783] Call trace:
[ 110.537541] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 110.543590] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 110.549252] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 110.554917] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 110.562131] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 110.568182] [<ffffff90081f6d8c>] check_memory_region+0x20/0x144
[ 110.574812] [<ffffff90081f72f0>] memset+0x2c/0x4c
[ 110.580118] [<ffffff90007b8ef4>] kmalloc_uaf_memset+0x8c/0xb8 [test_kasan]
[ 110.587853] [<ffffff90007b9560>] kmalloc_tests_init+0x50/0x90 [test_kasan]
[ 110.595550] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 110.601794] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 110.607937] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 110.614080] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 110.620417] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 110.626354]
[ 110.628027] Allocated by task 1204:
[ 110.631940] save_stack_trace_tsk+0x0/0x1f4
[ 110.636628] save_stack_trace+0x18/0x20
[ 110.640930] kasan_kmalloc.part.1+0x44/0xec
[ 110.645617] kasan_kmalloc+0x88/0x9c
[ 110.649661] kmalloc_uaf_memset+0x60/0xb8 [test_kasan]
[ 110.655454] kmalloc_tests_init+0x50/0x90 [test_kasan]
[ 110.661209] do_one_initcall+0xe4/0x1b0
[ 110.665506] do_init_module+0xf0/0x2ac
[ 110.669708] load_module+0x2690/0x2dcc
[ 110.673909] SyS_init_module+0x198/0x224
[ 110.678304] el0_svc_naked+0x34/0x38
[ 110.682303]
[ 110.683975] Freed by task 1204:
[ 110.687500] save_stack_trace_tsk+0x0/0x1f4
[ 110.692189] save_stack_trace+0x18/0x20
[ 110.696489] kasan_slab_free+0x90/0x15c
[ 110.700784] kfree+0xc8/0x258
[ 110.704152] kmalloc_uaf_memset+0x7c/0xb8 [test_kasan]
[ 110.709943] kmalloc_tests_init+0x50/0x90 [test_kasan]
[ 110.715694] do_one_initcall+0xe4/0x1b0
[ 110.719995] do_init_module+0xf0/0x2ac
[ 110.724198] load_module+0x2690/0x2dcc
[ 110.728398] SyS_init_module+0x198/0x224
[ 110.732793] el0_svc_naked+0x34/0x38
[ 110.736791]
[ 110.738468] The buggy address belongs to the object at ffffffc0336dab00
[ 110.738468] which belongs to the cache kmalloc-128 of size 128
[ 110.752478] The buggy address is located 0 bytes inside of
[ 110.752478] 128-byte region [ffffffc0336dab00, ffffffc0336dab80)
[ 110.765407] The buggy address belongs to the page:
[ 110.770772] page:ffffffbf00cdb600 count:1 mapcount:0 mapping: (null) index:0xffffffc0336dbc80 compound_mapcount: 0
[ 110.783238] flags: 0x10200(slab|head)
[ 110.787334] page dumped because: kasan: bad access detected
[ 110.793561]
[ 110.795231] Memory state around the buggy address:
[ 110.800602] ffffffc0336daa00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.808687] ffffffc0336daa80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.816769] >ffffffc0336dab00: fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb
[ 110.824845] ^
[ 110.828463] ffffffc0336dab80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.836546] ffffffc0336dac00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 110.844621] ==================================================================
[ 110.861989] kasan test: kmalloc_uaf2 use-after-free after another kmalloc
[ 110.889739] ==================================================================
[ 110.897890] BUG: KASAN: use-after-free in kmalloc_uaf2+0xc8/0x118 [test_kasan]
[ 110.905972] Write of size 1 at addr ffffffc02fc52da8 by task insmod/1204
[ 110.913462]
[ 110.915144] CPU: 0 PID: 1204 Comm: insmod Tainted: G B 4.9.191 #4
[ 110.923218] Hardware name: sun50iw10 (DT)
[ 110.927702] Call trace:
[ 110.930462] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[ 110.936512] [<ffffff900808bda0>] show_stack+0x14/0x1c
[ 110.942174] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[ 110.947840] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[ 110.955057] [<ffffff90081f8140>] kasan_report+0x250/0x27c
[ 110.961103] [<ffffff90081f695c>] __asan_store1+0x44/0x4c
[ 110.967092] [<ffffff90007b88d0>] kmalloc_uaf2+0xc8/0x118 [test_kasan]
[ 110.974341] [<ffffff90007b9564>] kmalloc_tests_init+0x54/0x90 [test_kasan]
[ 110.982040] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[ 110.988286] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[ 110.994435] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[ 111.000578] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[ 111.006916] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[ 111.012854]
[ 111.014524] Allocated by task 1204:
[ 111.018433] save_stack_trace_tsk+0x0/0x1f4
[ 111.023119] save_stack_trace+0x18/0x20
[ 111.027419] kasan_kmalloc.part.1+0x44/0xec
[ 111.032106] kasan_kmalloc+0x88/0x9c
[ 111.036152] kmalloc_uaf2+0x68/0x118 [test_kasan]
[ 111.041463] kmalloc_tests_init+0x54/0x90 [test_kasan]
[ 111.047214] do_one_initcall+0xe4/0x1b0
[ 111.051516] do_init_module+0xf0/0x2ac
[ 111.055717] load_module+0x2690/0x2dcc
[ 111.059917] SyS_init_module+0x198/0x224
[ 111.064312] el0_svc_naked+0x34/0x38
[ 111.068309]
[ 111.069981] Freed by task 1204:
[ 111.073505] save_stack_trace_tsk+0x0/0x1f4
[ 111.078191] save_stack_trace+0x18/0x20
[ 111.082490] kasan_slab_free+0x90/0x15c
[ 111.086790] kfree+0xc8/0x258
[ 111.090157] kmalloc_uaf2+0x84/0x118 [test_kasan]
[ 111.095465] kmalloc_tests_init+0x54/0x90 [test_kasan]
[ 111.101217] do_one_initcall+0xe4/0x1b0
[ 111.105518] do_init_module+0xf0/0x2ac
[ 111.109716] load_module+0x2690/0x2dcc
[ 111.113918] SyS_init_module+0x198/0x224
[ 111.118311] el0_svc_naked+0x34/0x38
[ 111.122307]
[ 111.123984] The buggy address belongs to the object at ffffffc02fc52d80
[ 111.123984] which belongs to the cache kmalloc-128 of size 128
[ 111.137989] The buggy address is located 40 bytes inside of
[ 111.137989] 128-byte region [ffffffc02fc52d80, ffffffc02fc52e00)
[ 111.151016] The buggy address belongs to the page:
[ 111.156383] page:ffffffbf00bf1400 count:1 mapcount:0 mapping: (null) index:0xffffffc02fc53c80 compound_mapcount: 0
[ 111.168852] flags: 0x10200(slab|head)
[ 111.172950] page dumped because: kasan: bad access detected
[ 111.179177]
[ 111.180848] Memory state around the buggy address:
[ 111.186217] ffffffc02fc52c80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 111.194301] ffffffc02fc52d00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 111.202384] >ffffffc02fc52d80: fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb
[ 111.210459] ^
[ 111.215532] ffffffc02fc52e00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 111.223610] ffffffc02fc52e80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[ 111.231683] ==================================================================
分析
- 从上述log,kasan提示这时一个访问已释放内存的错误类型(BUG: KASAN: use-after-free xxx),并显示出错的函数名称,出错信息提示,出错附近内存状况和出错位置。可以利用gdb+符号表查看源码,以kmalloc_uaf为例:
$ ./out/gcc-linaro-5.3.1-2016.05-x86_64_aarch64-linux-gnu/bin/aarch64-linux-gnu-gdb ~/link/kernel/linux-4.9/lib/test_kasan.ko
GNU gdb (Linaro_GDB-2016.05) 7.11.1.20160702-git
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "--host=x86_64-unknown-linux-gnu --target=aarch64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from /home1/weidonghui/link/kernel/linux-4.9/lib/test_kasan.ko...done.
(gdb) list *kmalloc_uaf+0x84
0x7d4 is in kmalloc_uaf (lib/test_kasan.c:267).
warning: Source file is more recent than executable.
262 pr_err("Allocation failed\n");
263 return;
264 }
265
266 kfree(ptr);
267 *(ptr + 8) = 'x';
268 }
269
270 static noinline void __init kmalloc_uaf_memset(void)
271 {
(gdb)
重复释放(double-free)
实例源码
- 实例包括
- kmalloc_double_free_test:重复释放内存。
#define pr_fmt(fmt) "kasan test: %s " fmt, __func__
#include <linux/kernel.h>
#include <linux/mman.h>
#include <linux/mm.h>
#include <linux/printk.h>
#include <linux/slab.h>
#include <linux/string.h>
#include <linux/uaccess.h>
#include <linux/module.h>
#include <linux/kasan.h>
static noinline void __init kmalloc_double_free_test(void)
{
char *ptr;
size_t size = 123;
pr_info("double-free\n");
ptr = kmalloc(size, GFP_KERNEL);
if (!ptr) {
pr_err("Allocation failed\n");
return;
}
kfree(ptr);
kfree(ptr);
}
static int __init kmalloc_tests_init(void)
{
/*
* Temporarily enable multi-shot mode. Otherwise, we'd only get a
* report for the first case.
*/
bool multishot = kasan_save_enable_multi_shot();
kmalloc_double_free_test();
kasan_restore_multi_shot(multishot);
return -EAGAIN;
}
module_init(kmalloc_tests_init);
MODULE_LICENSE("GPL");
输出log
[159003.489404] kasan test: kmalloc_double_free_test double-free
[159003.496364] ==================================================================
[159003.504599] BUG: KASAN: double-free or invalid-free in (null)
[159003.512152]
[159003.513943] CPU: 0 PID: 17631 Comm: insmod Tainted: G B 4.9.191 #4
[159003.522265] Hardware name: sun50iw10 (DT)
[159003.526886] Call trace:
[159003.529769] [<ffffff900808ba74>] dump_backtrace+0x0/0x318
[159003.535965] [<ffffff900808bda0>] show_stack+0x14/0x1c
[159003.541771] [<ffffff90083ae758>] dump_stack+0xb0/0xe8
[159003.547579] [<ffffff90081f7ad4>] print_address_description+0x60/0x228
[159003.554950] [<ffffff90081f7ec8>] kasan_report_double_free+0x64/0x8c
[159003.562124] [<ffffff90081f7694>] kasan_slab_free+0x44/0x15c
[159003.568511] [<ffffff90081f4b50>] kfree+0xc8/0x258
[159003.573964] [<ffffff90008289a4>] kmalloc_double_free_test+0x84/0xb0 [test_kasan]
[159003.582443] [<ffffff9000829640>] kmalloc_tests_init+0x78/0x90 [test_kasan]
[159003.590302] [<ffffff9008083a8c>] do_one_initcall+0xe4/0x1b0
[159003.596695] [<ffffff9008190ce4>] do_init_module+0xf0/0x2ac
[159003.602987] [<ffffff900815bd40>] load_module+0x2690/0x2dcc
[159003.609277] [<ffffff900815c614>] SyS_init_module+0x198/0x224
[159003.615761] [<ffffff9008083200>] el0_svc_naked+0x34/0x38
[159003.621846]
[159003.623630] Allocated by task 17631:
[159003.627772] save_stack_trace_tsk+0x0/0x1f4
[159003.632596] save_stack_trace+0x18/0x20
[159003.637035] kasan_kmalloc.part.1+0x44/0xec
[159003.641856] kasan_kmalloc+0x88/0x9c
[159003.646030] kmalloc_double_free_test+0x60/0xb0 [test_kasan]
[159003.652552] kmalloc_tests_init+0x78/0x90 [test_kasan]
[159003.658446] do_one_initcall+0xe4/0x1b0
[159003.662882] do_init_module+0xf0/0x2ac
[159003.667210] load_module+0x2690/0x2dcc
[159003.671544] SyS_init_module+0x198/0x224
[159003.676073] el0_svc_naked+0x34/0x38
[159003.680197]
[159003.681980] Freed by task 17631:
[159003.685733] save_stack_trace_tsk+0x0/0x1f4
[159003.690558] save_stack_trace+0x18/0x20
[159003.694987] kasan_slab_free+0x90/0x15c
[159003.699417] kfree+0xc8/0x258
[159003.702911] kmalloc_double_free_test+0x7c/0xb0 [test_kasan]
[159003.709435] kmalloc_tests_init+0x78/0x90 [test_kasan]
[159003.715328] do_one_initcall+0xe4/0x1b0
[159003.719759] do_init_module+0xf0/0x2ac
[159003.724089] load_module+0x2690/0x2dcc
[159003.728418] SyS_init_module+0x198/0x224
[159003.732945] el0_svc_naked+0x34/0x38
[159003.737071]
[159003.738858] The buggy address belongs to the object at ffffffc031810d00
[159003.738858] which belongs to the cache kmalloc-128 of size 128
[159003.753164] The buggy address is located 0 bytes inside of
[159003.753164] 128-byte region [ffffffc031810d00, ffffffc031810d80)
[159003.766389] The buggy address belongs to the page:
[159003.771893] page:ffffffbf00c60400 count:1 mapcount:0 mapping: (null) index:0xffffffc031813a00 compound_mapcount: 0
[159003.784561] flags: 0x10200(slab|head)
[159003.788786] page dumped because: kasan: bad access detected
[159003.795161]
[159003.796939] Memory state around the buggy address:
[159003.802443] ffffffc031810c00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[159003.810680] ffffffc031810c80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[159003.818920] >ffffffc031810d00: fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb
[159003.827150] ^
[159003.830892] ffffffc031810d80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[159003.839142] ffffffc031810e00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[159003.847379] ==================================================================
分析
- 从上述log,kasan提示这是一个重复释放内存的错误类型(BUG: KASAN: double-free or invalid-free xxx),并显示出错的函数名称,出错信息提示,出错附近内存状况和出错位置。可以利用gdb+符号表查看源码,以kmalloc_double_free_test为例:
$ ./out/gcc-linaro-5.3.1-2016.05-x86_64_aarch64-linux-gnu/bin/aarch64-linux-gnu-gdb ~/link/kernel/linux-4.9/lib/test_kasan.ko
GNU gdb (Linaro_GDB-2016.05) 7.11.1.20160702-git
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "--host=x86_64-unknown-linux-gnu --target=aarch64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from /home1/weidonghui/link/kernel/linux-4.9/lib/test_kasan.ko...done.
(gdb) list *kmalloc_double_free_test+0x84
0x9a4 is in kmalloc_double_free_test (lib/test_kasan.c:477).
472 return;
473 }
474
475 kfree(ptr);
476 kfree(ptr);
477 }
478
479 static int __init kmalloc_tests_init(void)
480 {
481 /*
(gdb)





















 749
749











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








