新建用户表——users,并完成数据库增删查改
一、新建表
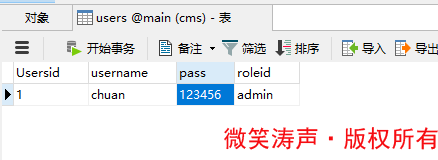
二、持久化映射,建立模型类,添加主键生成器
//指定生成器名称
@GeneratedValue(generator = "uuid2" )
@GenericGenerator(name = "uuid2", strategy = "org.hibernate.id.UUIDGenerator" )
三、建立Dao层
package edu.ynmd.cms.dao;
import edu.ynmd.cms.model.Users;
import org.springframework.data.jpa.repository.JpaRepository;
import org.springframework.data.jpa.repository.Query;
import org.springframework.data.repository.query.Param;
import javax.websocket.server.PathParam;
import java.util.List;
public interface UsersDao extends JpaRepository {
@Query("select u from Users u where u.username=:username and u.pass=:pass")
List getUsersByUsernameAndPass(@Param("username")String username, @Param("pass") String pass);
}
四、配置service层
在ManageService添加方法
//用户表
Users saveUser(Users users);
boolean deleteUser(String id);
Users getUser(String id);
Users getUserByUserNameAndPass(String username,String pass);
在ManageServiceImpl添加方法具体实现
//*****************************用户表增删查改开始*********************************
@Override
public Users saveUser(Users users) {
try {
return usersDao.save(users);
} catch (Exception e) {
e.printStackTrace();
return null;
}
}
@Override
public boolean deleteUser(String id) {
try {
usersDao.deleteById(id);
return true;
} catch (Exception e) {
e.printStackTrace();
}
return false;
}
@Override
public Users getUser(String id) {
Optional temp=usersDao.findById(id);
return temp.isPresent()?temp.get():null;
}
@Override
public Users getUserByUserNameAndPass(String username, String pass) {
List ul=usersDao.getUsersByUsernameAndPass(username,pass);
if(ul.size()>0){
return ul.get(0);
}
return null;
}
JWT框架的搭建
一、添加Maven依赖
org.springframework.boot
spring-boot-starter-security
io.jsonwebtoken
jjwt
0.7.0
二、编写JwtUtil工具类(生成token,解析token,校验token)
package edu.ynmd.cms.tools;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.SignatureAlgorithm;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import javax.servlet.http.HttpServletRequest;
import java.util.Date;
import java.util.HashMap;
import java.util.Map;
public class JwtUtil {
private static final Logger logger= LoggerFactory.getLogger(JwtUtil.class);
public static final long EXPIRATION_TIME=60*60*1000;// 令牌环有效期








 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章















 166
166











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








