目前在现有商密SM系列算法使用下:
依据GB/T38636-2020《信息安全技术传输层密码协议(TLCP)》相关技术规范,在使用ECC(SM2)进行密钥交换时,singed_params是服务端对双方随机数和服务端加密证书的签名。
以下为标准信息:
1. 打开国密算法算法的业务系统,并进行抓包
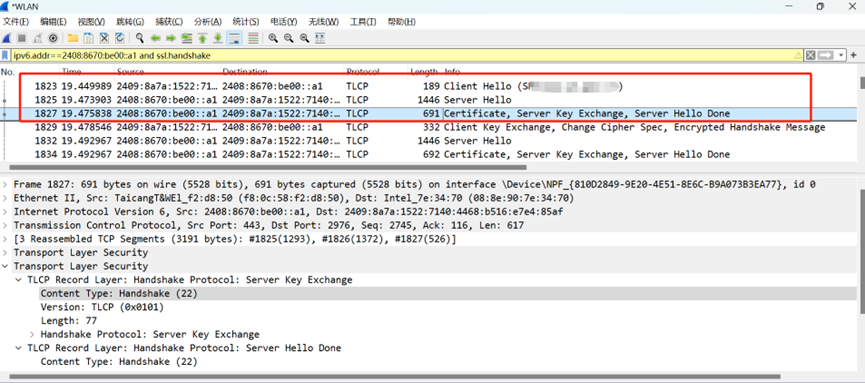
2. 抓包信息如下:
3. 在ClintHello包中查看并提取随机数
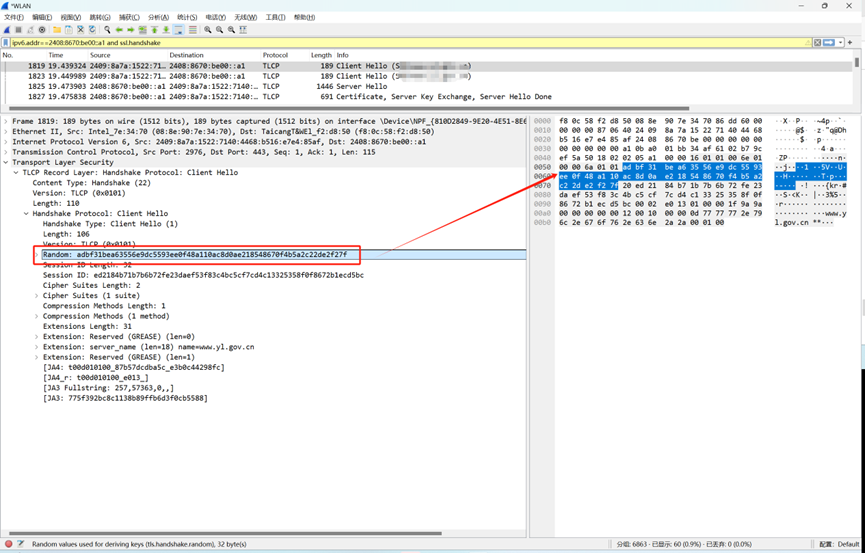
客户端随机数提取:
adbf31bea63556e9dc5593ee0f48a110ac8d0ae218548670f4b5a2c22de2f27f
4. 在ServerHello包中查看并提取随机数
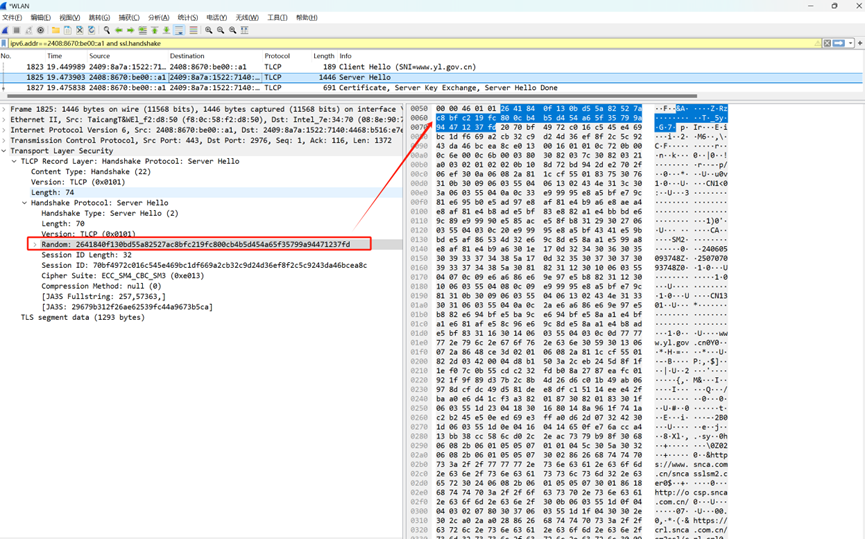
服务端随机数提取:
2641840f130bd55a82527ac8bfc219fc800cb4b5d454a65f35799a94471237fd
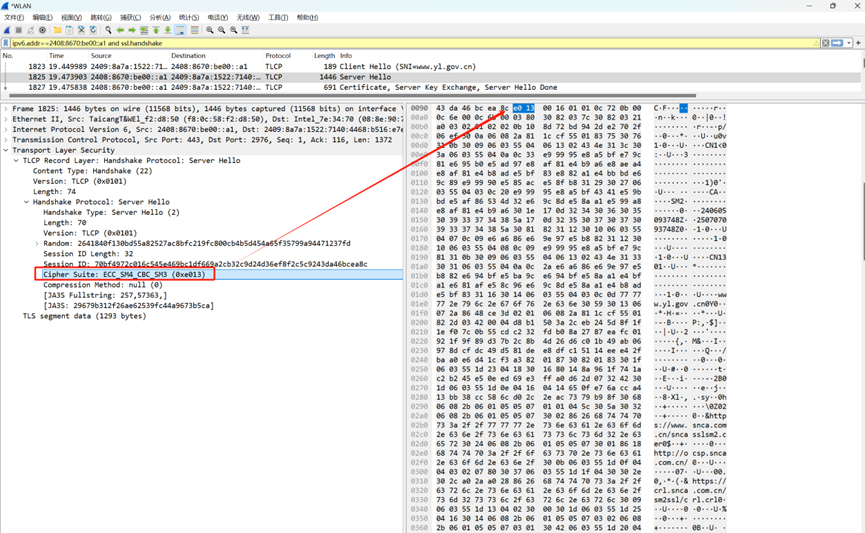
协商使用的密码套件
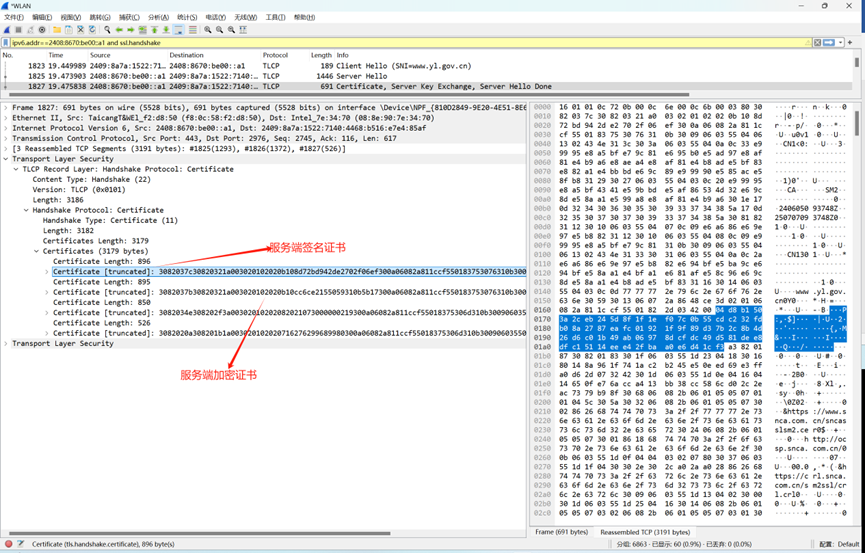
5. 提取服务端签名证书公钥
采用双证书体系,第一个为服务端签名证书、第二个为服务端加密证书
将服务端签名证书转化为.cer格式,提取公钥
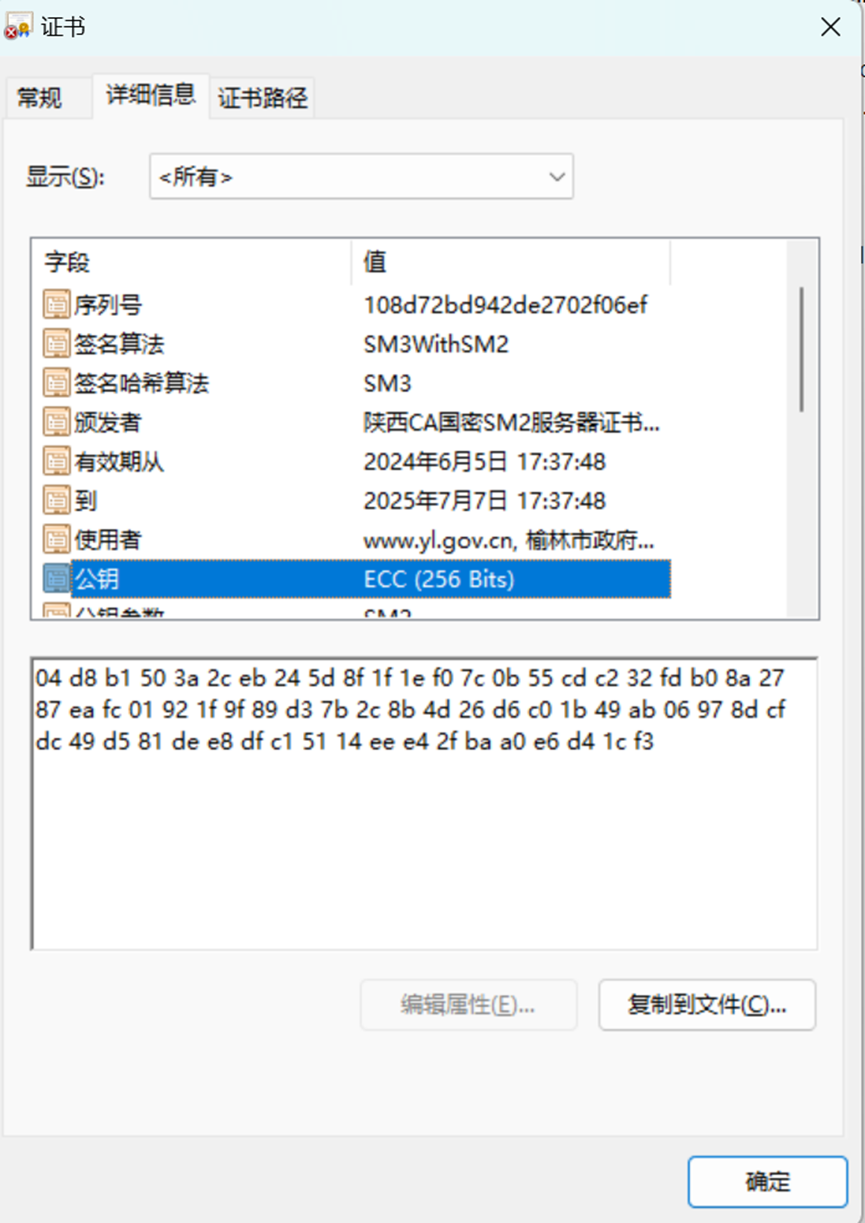
提取公钥
04d8b1503a2ceb245d8f1f1ef07c0b55cdc232fdb08a2787eafc01921f9f89d37b2c8b4d26d6c01b49ab06978dcfdc49d581dee8dfc15114eee42fbaa0e6d41cf3
6. 提取服务端加密证书
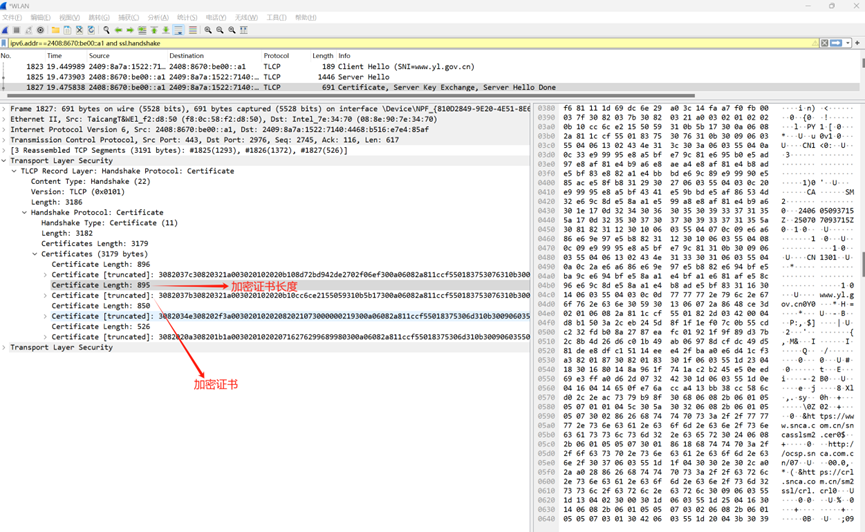
提取加密证书长度
00037f
提取加密证书值
3082037b30820321a003020102020b10cc6ce2155059310b5b17300a06082a811ccf550183753076310b300906035504061302434e313c303a060355040a0c33e99995e8a5bfe79c81e695b0e5ad97e8af81e4b9a6e8aea4e8af81e4b8ade5bf83e882a1e4bbbde69c89e99990e585ace58fb83129302706035504030c20e99995e8a5bf4341e59bbde5af86534d32e69c8de58aa1e599a8e8af81e4b9a6301e170d3234303630353039333731355a170d3235303730373039333731355a3081823112301006035504070c09e6a686e69e97e5b8823112301006035504080c09e99995e8a5bfe79c81310b300906035504061302434e31333031060355040a0c2ae6a686e69e97e5b882e694bfe5ba9ce694bfe58aa1e4bfa1e681afe58c96e69c8de58aa1e4b8ade5bf833116301406035504030c0d7777772e796c2e676f762e636e3059301306072a8648ce3d020106082a811ccf5501822d03420004d8b1503a2ceb245d8f1f1ef07c0b55cdc232fdb08a2787eafc01921f9f89d37b2c8b4d26d6c01b49ab06978dcfdc49d581dee8dfc15114eee42fbaa0e6d41cf3a382018730820183301f0603551d230418301680148a961f741ac2b245e50eed69e3ffa0d62d073242301d0603551d0e04160414650fe76acca413bb38cc586cd02c2eac7379b98f306806082b06010505070101045c305a303206082b06010505073002862668747470733a2f2f7777772e736e63612e636f6d2e636e2f736e636173736c736d322e636572302406082b060105050730018618687474703a2f2f6f6373702e736e63612e636f6d2e636e2f30370603551d1f0430302e302ca02aa028862668747470733a2f2f63726c2e736e63612e636f6d2e636e2f736d3273736c2f63726c2e63726c30090603551d1304023000301d0603551d250416301406082b0601050507030206082b0601050507030130420603551d20043b3039303706092a811c87842204010b302a302806082b06010505070201161c68747470733a2f2f7777772e736e63612e636f6d2e636e2f4350532f300b0603551d0f04040302052030230603551d11041c301a8209796c2e676f762e636e820d7777772e796c2e676f762e636e300a06082a811ccf550183750348003045022079add940bd65a6ec925b4520827fabad2bb80c19d826222971cf04d3725c904e022100de8a4a98e217188d13f311887cf710dfd6bda9e3f9fd78e8ae0c48ee82432a7c
7. 提取签名值
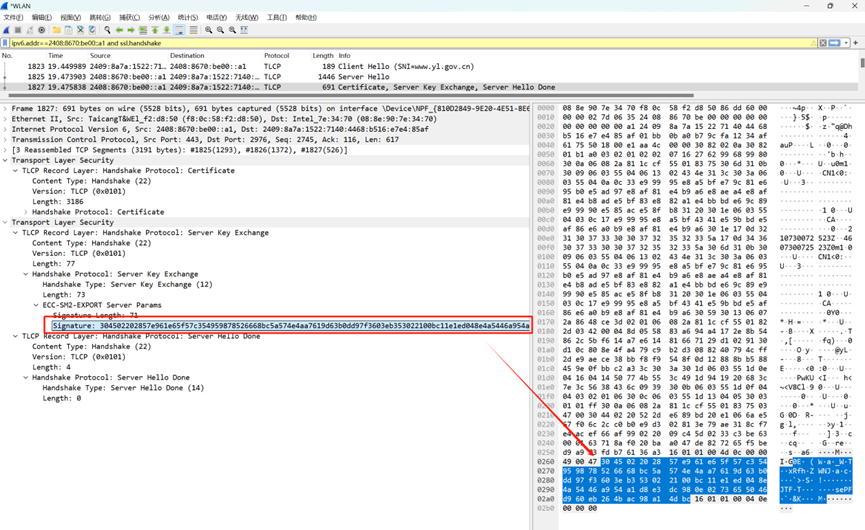
提取签名值:
304502202857e961e65f57c354959878526668bc5a574e4aa7619d63b0dd97f3603eb353022100bc11e1ed048e4a5446a954a1d8e3dc980e0273655046d960eb264bac98a14dbc
8. 验签
签名原文:客户端随机数+服务端随机数+服务端加密证书长度+服务度加密证书
adbf31bea63556e9dc5593ee0f48a110ac8d0ae218548670f4b5a2c22de2f27f2641840f130bd55a82527ac8bfc219fc800cb4b5d454a65f35799a94471237fd00037f3082037b30820321a003020102020b10cc6ce2155059310b5b17300a06082a811ccf550183753076310b300906035504061302434e313c303a060355040a0c33e99995e8a5bfe79c81e695b0e5ad97e8af81e4b9a6e8aea4e8af81e4b8ade5bf83e882a1e4bbbde69c89e99990e585ace58fb83129302706035504030c20e99995e8a5bf4341e59bbde5af86534d32e69c8de58aa1e599a8e8af81e4b9a6301e170d3234303630353039333731355a170d3235303730373039333731355a3081823112301006035504070c09e6a686e69e97e5b8823112301006035504080c09e99995e8a5bfe79c81310b300906035504061302434e31333031060355040a0c2ae6a686e69e97e5b882e694bfe5ba9ce694bfe58aa1e4bfa1e681afe58c96e69c8de58aa1e4b8ade5bf833116301406035504030c0d7777772e796c2e676f762e636e3059301306072a8648ce3d020106082a811ccf5501822d03420004d8b1503a2ceb245d8f1f1ef07c0b55cdc232fdb08a2787eafc01921f9f89d37b2c8b4d26d6c01b49ab06978dcfdc49d581dee8dfc15114eee42fbaa0e6d41cf3a382018730820183301f0603551d230418301680148a961f741ac2b245e50eed69e3ffa0d62d073242301d0603551d0e04160414650fe76acca413bb38cc586cd02c2eac7379b98f306806082b06010505070101045c305a303206082b06010505073002862668747470733a2f2f7777772e736e63612e636f6d2e636e2f736e636173736c736d322e636572302406082b060105050730018618687474703a2f2f6f6373702e736e63612e636f6d2e636e2f30370603551d1f0430302e302ca02aa028862668747470733a2f2f63726c2e736e63612e636f6d2e636e2f736d3273736c2f63726c2e63726c30090603551d1304023000301d0603551d250416301406082b0601050507030206082b0601050507030130420603551d20043b3039303706092a811c87842204010b302a302806082b06010505070201161c68747470733a2f2f7777772e736e63612e636f6d2e636e2f4350532f300b0603551d0f04040302052030230603551d11041c301a8209796c2e676f762e636e820d7777772e796c2e676f762e636e300a06082a811ccf550183750348003045022079add940bd65a6ec925b4520827fabad2bb80c19d826222971cf04d3725c904e022100de8a4a98e217188d13f311887cf710dfd6bda9e3f9fd78e8ae0c48ee82432a7c
服务端签名证书公钥:
04d8b1503a2ceb245d8f1f1ef07c0b55cdc232fdb08a2787eafc01921f9f89d37b2c8b4d26d6c01b49ab06978dcfdc49d581dee8dfc15114eee42fbaa0e6d41cf3
Px:d8b1503a2ceb245d8f1f1ef07c0b55cdc232fdb08a2787eafc01921f9f89d37b
Py:2c8b4d26d6c01b49ab06978dcfdc49d581dee8dfc15114eee42fbaa0e6d41cf3
签名值:
304502202857e961e65f57c354959878526668bc5a574e4aa7619d63b0dd97f3603eb353022100bc11e1ed048e4a5446a954a1d8e3dc980e0273655046d960eb264bac98a14dbc
R:2857e961e65f57c354959878526668bc5a574e4aa7619d63b0dd97f3603eb353
S:bc11e1ed048e4a5446a954a1d8e3dc980e0273655046d960eb264bac98a14dbc
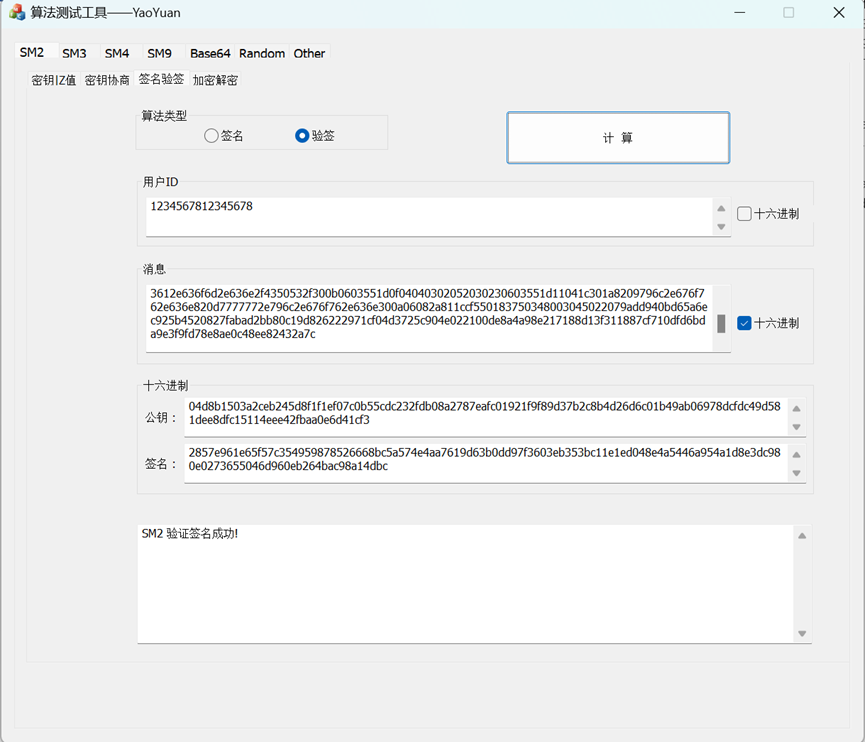
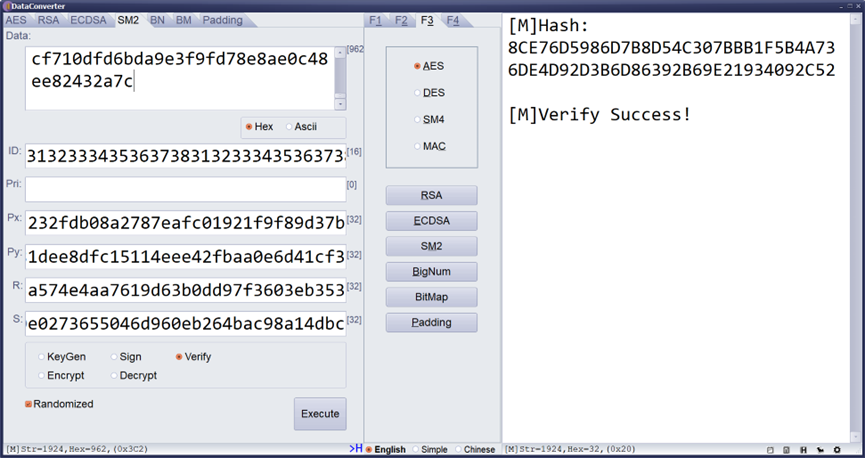
9. 使用算法工具验签
不同工具验签数据稍有不同





















 3665
3665

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








