一般收集信息,我们要对服务端语言、Web开发框架、Web应用CMS、前短库和第三方组件等进行识别收集信息。
相对而言,Web应用的指纹稍微负责一些,也可以自己实现工具来探测http头,waf,cms等。也可以借助whatweb/wafw00f,参考这些成熟的开源工具。下面主要还是说一下这两工具。
0x00 嘚啵
1. whatweb
whatweb是基于ruby语言开发的网站指纹识别软件,能识别网站的详细信息,CMS类型,博客平台,中间件,Web框架模块,网站服务器,脚本类型,JavaScript库,IP,Cookie等。
0x02 安装
debian/ubuntu系统下
apt install whatweb
简洁的使用如下:
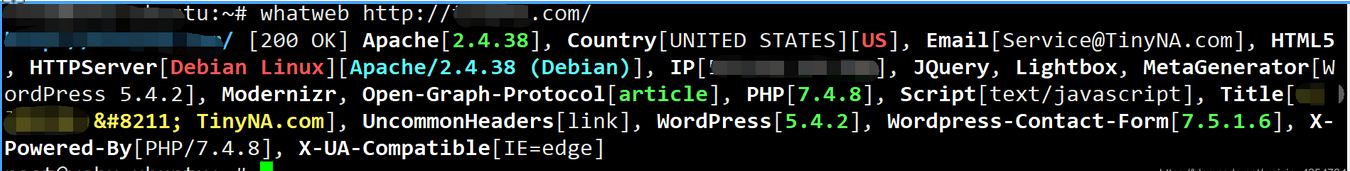
复杂的使用如下:whatweb --help
.$$$ $. .$$$ $.
$$$$ $$. .$$$ $$$ .$$$$$$. .$$$$$$$$$$. $$$$ $$. .$$$$$$$. .$$$$$$.
$ $$ $$$ $ $$ $$$ $ $$$$$$. $$$$$ $$$$$$ $ $$ $$$ $ $$ $$ $ $$$$$$.
$ `$ $$$ $ `$ $$$ $ `$ $$$ $$' $ `$ `$$ $ `$ $$$ $ `$ $ `$ $$$'
$. $ $$$ $. $$$$$$ $. $$$$$$ `$ $. $ :' $. $ $$$ $. $$$$ $. $$$$$.
$::$ . $$$ $::$ $$$ $::$ $$$ $::$ $::$ . $$$ $::$ $::$ $$$$
$;;$ $$$ $$$ $;;$ $$$ $;;$ $$$ $;;$ $;;$ $$$ $$$ $;;$ $;;$ $$$$
$$$$$$ $$$$$ $$$$ $$$ $$$$ $$$ $$$$ $$$$$$ $$$$$ $$$$$$$$$ $$$$$$$$$'
WhatWeb - Next generation web scanner version 0.4.9.
Developed by Andrew Horton aka urbanadventurer and Brendan Coles.
Homepage: http://www.morningstarsecurity.com/research/whatweb
Usage: whatweb [options] <URLs>
TARGET SELECTION:
<TARGETs> Enter URLs, hostnames, IP adddresses,
filenames, or nmap-format IP address ranges.
--input-file=FILE, -i Read targets from a file. You can pipe
hostnames or URLs directly with -i /dev/stdin.
TARGET MODIFICATION:
--url-prefix Add a prefix to target URLs.
--url-suffix Add a suffix to target URLs.
--url-pattern Insert the targets into a URL.
e.g. example.com/%insert%/robots.txt
AGGRESSION:
The aggression level controls the trade-off between speed/stealth and
reliability.
--aggression, -a=LEVEL Set the aggression level. Default: 1.
1. Stealthy Makes one HTTP request per target and also
follows redirects.
3. Aggressive If a level 1 plugin is matched, additional
requests will be made.
4. Heavy Makes a lot of HTTP requests per target. URLs
from all plugins are attempted.
HTTP OPTIONS:
--user-agent, -U=AGENT Identify as AGENT instead of WhatWeb/0.4.9.
--header, -H Add an HTTP header. eg "Foo:Bar". Specifying a
default header will replace it. Specifying an
empty value, e.g. "User-Agent:" will remove it.
--follow-redirect=WHEN Control when to follow redirects. WHEN may be
`never', `http-only', `meta-only', `same-site',
`same-domain' or `always'. Default: always.
--max-redirects=NUM Maximum number of redirects. Default: 10.
AUTHENTICATION:
--user, -u=<user:password> HTTP basic authentication.
--cookie, -c=COOKIES Use cookies, e.g. 'name=value; name2=value2'.
PROXY:
--proxy <hostname[:port]> Set proxy hostname and port.
Default: 8080.
--proxy-user <username:password> Set proxy user and password.
PLUGINS:
--list-plugins, -l List all plugins.
--info-plugins, -I=[SEARCH] List all plugins with detailed information.
Optionally search with keywords in a comma
delimited list.
--search-plugins=STRING Search plugins for a keyword.
--plugins, -p=LIST Select plugins. LIST is a comma delimited set
of selected plugins. Default is all.
Each element can be a directory, file or plugin
name and can optionally have a modifier, +/-.
Examples: +/tmp/moo.rb,+/tmp/foo.rb
title,md5,+./plugins-disabled/
./plugins-disabled,-md5
-p + is a shortcut for -p +plugins-disabled.
--grep, -g=STRING Search for STRING in HTTP responses. Reports
with a plugin named Grep.
--custom-plugin=DEFINITION Define a custom plugin named Custom-Plugin,
Examples: ":text=>'powered by abc'"
":version=>/powered[ ]?by ab[0-9]/"
":ghdb=>'intitle:abc \"powered by abc\"'"
":md5=>'8666257030b94d3bdb46e05945f60b42'"
"{:text=>'powered by abc'}"
--dorks=PLUGIN List Google dorks for the selected plugin.
OUTPUT:
--verbose, -v Verbose output includes plugin descriptions.
Use twice for debugging.
--colour,--color=WHEN control whether colour is used. WHEN may be
`never', `always', or `auto'.
--quiet, -q Do not display brief logging to STDOUT.
--no-errors Suppress error messages.
LOGGING:
--log-brief=FILE Log brief, one-line output.
--log-verbose=FILE Log verbose output.
--log-errors=FILE Log errors.
--log-xml=FILE Log XML format.
--log-json=FILE Log JSON format.
--log-sql=FILE Log SQL INSERT statements.
--log-sql-create=FILE Create SQL database tables.
--log-json-verbose=FILE Log JSON Verbose format.
--log-magictree=FILE Log MagicTree XML format.
--log-object=FILE Log Ruby object inspection format.
--log-mongo-database Name of the MongoDB database.
--log-mongo-collection Name of the MongoDB collection.
Default: whatweb.
--log-mongo-host MongoDB hostname or IP address.
Default: 0.0.0.0.
--log-mongo-username MongoDB username. Default: nil.
--log-mongo-password MongoDB password. Default: nil.
--log-elastic-index Name of the index to store results. Default: whatweb
--log-elastic-host Host:port of the elastic http interface. Default: 127.0.0.1:9200
PERFORMANCE & STABILITY:
--max-threads, -t Number of simultaneous threads. Default: 25.
--open-timeout Time in seconds. Default: 15.
--read-timeout Time in seconds. Default: 30.
--wait=SECONDS Wait SECONDS between connections.
This is useful when using a single thread.
HELP & MISCELLANEOUS:
--short-help Short usage help.
--help, -h Complete usage help.
--debug Raise errors in plugins.
--version Display version information.
EXAMPLE USAGE:
* Scan example.com.
./whatweb example.com
* Scan reddit.com slashdot.org with verbose plugin descriptions.
./whatweb -v reddit.com slashdot.org
* An aggressive scan of wired.com detects the exact version of WordPress.
./whatweb -a 3 www.wired.com
* Scan the local network quickly and suppress errors.
whatweb --no-errors 192.168.0.0/24
* Scan the local network for https websites.
whatweb --no-errors --url-prefix https:// 192.168.0.0/24
* Scan for crossdomain policies in the Alexa Top 1000.
./whatweb -i plugin-development/alexa-top-100.txt \
--url-suffix /crossdomain.xml -p crossdomain_xml
OPTIONAL DEPENDENCIES
--------------------------------------------------------------------------------
To enable MongoDB logging install the mongo gem.
2. wafw00f
wafw00f是Python开发的用于检测网络服务器是否处于网络应用的防火墙(WAF)保护状态。PS: (0是数字)
wafw00f其工作原理是通过发送一个正常的http请求,然后观察其返回有没有一些特殊字符,如果没有则通过发送一个恶意的请求出发WAF拦截来获取其返回的特征来判断所使用的WAF。
0x03安装
debian/ubuntu系统下
apt install wafw00f
简洁的使用如下:

复杂的使用如下:
root@w-ubuntu:~# wafw00f --help
^ ^
_ __ _ ____ _ __ _ _ ____
///7/ /.' \ / __////7/ /,' \ ,' \ / __/
| V V // o // _/ | V V // 0 // 0 // _/
|_n_,'/_n_//_/ |_n_,' \_,' \_,'/_/
<
...'
WAFW00F - Web Application Firewall Detection Tool
By Sandro Gauci && Wendel G. Henrique
Usage: wafw00f url1 [url2 [url3 ... ]]
example: wafw00f http://www.victim.org/
Options:
-h, --help show this help message and exit
-v, --verbose enable verbosity - multiple -v options increase
verbosity
-a, --findall Find all WAFs, do not stop testing on the first one
-r, --disableredirect
Do not follow redirections given by 3xx responses
-t TEST, --test=TEST Test for one specific WAF
-l, --list List all WAFs that we are able to detect
-p PROXY, --proxy=PROXY
Use an HTTP proxy to perform requests, example:
http://hostname:8080, socks5://hostname:1080
-V, --version Print out the version
-H HEADERSFILE, --headersfile=HEADERSFILE
Pass custom headers, for example to overwrite the
default User-Agent string
这俩工具真不赖,大家有空分析分析他的源码,肯定有不少收获
goodlucky!





 本文介绍如何使用whatweb和wafw00f工具进行Web应用指纹识别及WAF检测,涵盖安装、基本与高级用法。whatweb可识别网站详细信息,包括CMS、Web框架等;wafw00f用于检测Web应用防火墙。
本文介绍如何使用whatweb和wafw00f工具进行Web应用指纹识别及WAF检测,涵盖安装、基本与高级用法。whatweb可识别网站详细信息,包括CMS、Web框架等;wafw00f用于检测Web应用防火墙。
















 1305
1305

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








