2024-05-31
背景
功能
实际效果
自定义规则
规则xml
2024-06-06 更新
IP黑名单列表
背景:
客户多为小微公司,服务器因为业务需求要暴露在公网上
公司产品线全部是基于Windows 的环境开发,不能用linux的服务器
客户公司(少的五六个人,多的10几个人),不愿意支出专业的防火墙或者其它需要花钱的手段
被勒索病毒搞怕了,网上搜索中看到 EvlWatcher 这工具,用了一下效果还行,比较符合 小客户的Windows服务器的低成本 降低被爆破的风险,多多少少能有点用
EvlWatcher的github开源项目链接
项目链接中有具体的使用方法,我就不在这里啰嗦了
小工具的思路是读取服务器日志,抓取关键字,将正则匹配的IP加入到防火墙规则中
功能:
支持临时封禁和永久封禁IP,支持手动添加IP白名单
支持自定义拉黑规则,支持自定义触发规则的次数和时间段
支持拉黑RDP爆破和MSSQLSERVER爆破IP
放实际效果图:
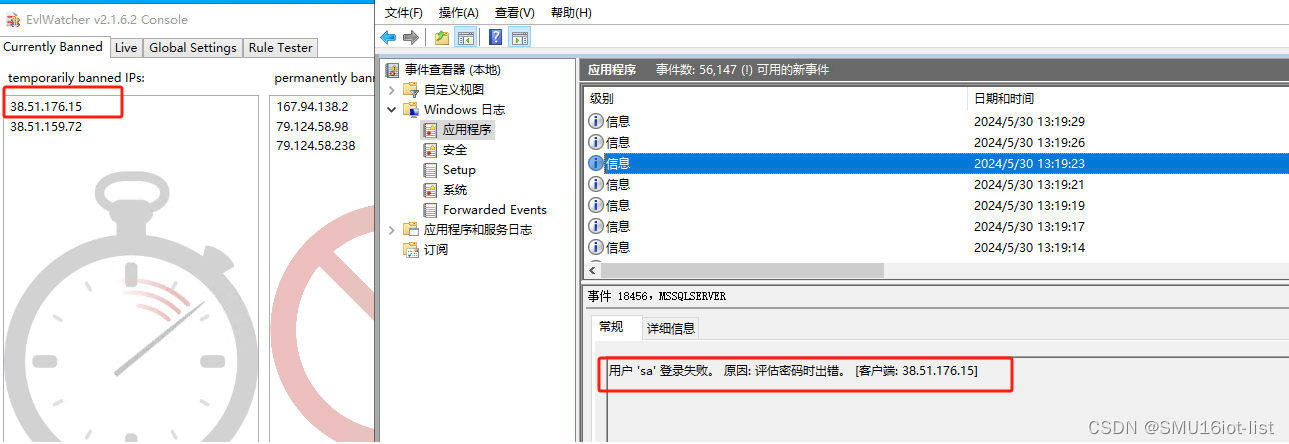
中文简体的windows服务器,如果是安装的MSSQL,还是中文版本的,需要再加自定义规则。分析后加了三条自定义规则
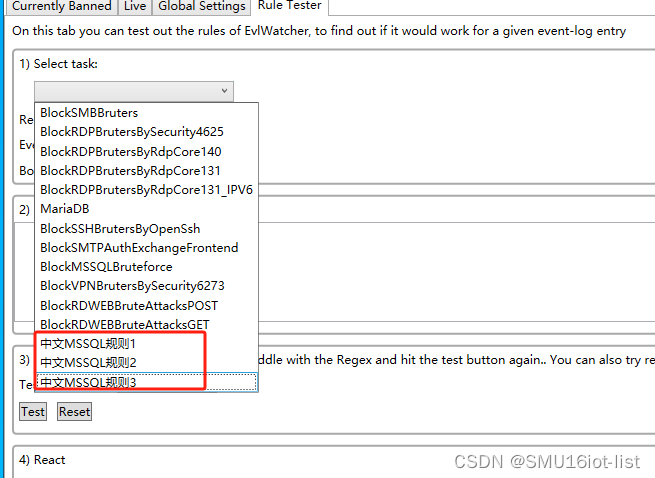
规则在这里添加
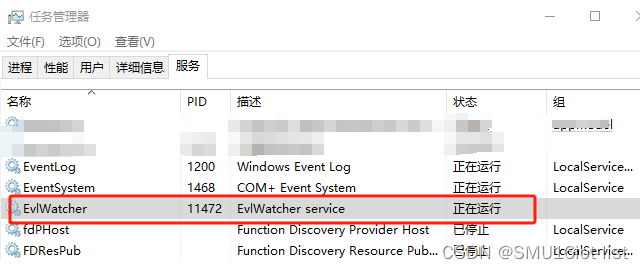
加完之后,重启服务
xml最后加入如下规则,其它规则看着自己自定义加吧
<Task Name="中文MSSQL规则1" Active="true">
<!-- the description ..-->
<Description>
This rule checks for failed SQL Server logins.
</Description>
<!-- this is the time a temporary ban is issued for, in seconds-->
<LockTime>
3600
</LockTime>
<!-- this is used for rules that only need new events for evaluating.
- If you dont know what this does, leave it set to false
- If you set this to true, it means that the task will only receive events it has not already received
- If you set this to false, it means that the task will receive all events of its timeframe, everytime it is polled
(e.g. task gets events provided until they fall out of the timeframe)-->
<OnlyNew>
False
</OnlyNew>
<!-- this is the timeframe (in seconds) to be inspected-->
<EventAge>
120
</EventAge>
<!-- this is the amount of times an entry must occure within the time frame to be considered a brute force attempt-->
<TriggerCount>
5
</TriggerCount>
<!-- after this amount of times temporarily banned, the ban will become permanent -->
<PermaBanCount>
3
</PermaBanCount>
<!-- This is the place where the rule looks for entries-->
<EventPath>
Application
</EventPath>
<!-- This was introduced because sole regex matching is too CPU intensive. it incredibly speeds up the filtering when you enter some (or at least one) words that MUST be contained in the LogEntry to undergo the regex inspection-->
<RegexBoosters>
<Booster>原因: 评估密码时出错。</Booster>
</RegexBoosters>
<!-- This is the regex that tries to extract an IP from the entries that contain the booster words for more infos see regex101.com-->
<Regex>
(\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b)
</Regex>
</Task>
<Task Name="中文MSSQL规则2" Active="true">
<!-- the description ..-->
<Description>
This rule checks for failed SQL Server logins.
</Description>
<!-- this is the time a temporary ban is issued for, in seconds-->
<LockTime>
3600
</LockTime>
<!-- this is used for rules that only need new events for evaluating.
- If you dont know what this does, leave it set to false
- If you set this to true, it means that the task will only receive events it has not already received
- If you set this to false, it means that the task will receive all events of its timeframe, everytime it is polled
(e.g. task gets events provided until they fall out of the timeframe)-->
<OnlyNew>
False
</OnlyNew>
<!-- this is the timeframe (in seconds) to be inspected-->
<EventAge>
120
</EventAge>
<!-- this is the amount of times an entry must occure within the time frame to be considered a brute force attempt-->
<TriggerCount>
5
</TriggerCount>
<!-- after this amount of times temporarily banned, the ban will become permanent -->
<PermaBanCount>
3
</PermaBanCount>
<!-- This is the place where the rule looks for entries-->
<EventPath>
Application
</EventPath>
<!-- This was introduced because sole regex matching is too CPU intensive. it incredibly speeds up the filtering when you enter some (or at least one) words that MUST be contained in the LogEntry to undergo the regex inspection-->
<RegexBoosters>
<Booster>原因: 密码与所提供的登录名不匹配。</Booster>
</RegexBoosters>
<!-- This is the regex that tries to extract an IP from the entries that contain the booster words for more infos see regex101.com-->
<Regex>
(\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b)
</Regex>
</Task>
<Task Name="中文MSSQL规则3" Active="true">
<!-- the description ..-->
<Description>
This rule checks for failed SQL Server logins.
</Description>
<!-- this is the time a temporary ban is issued for, in seconds-->
<LockTime>
3600
</LockTime>
<!-- this is used for rules that only need new events for evaluating.
- If you dont know what this does, leave it set to false
- If you set this to true, it means that the task will only receive events it has not already received
- If you set this to false, it means that the task will receive all events of its timeframe, everytime it is polled
(e.g. task gets events provided until they fall out of the timeframe)-->
<OnlyNew>
False
</OnlyNew>
<!-- this is the timeframe (in seconds) to be inspected-->
<EventAge>
120
</EventAge>
<!-- this is the amount of times an entry must occure within the time frame to be considered a brute force attempt-->
<TriggerCount>
5
</TriggerCount>
<!-- after this amount of times temporarily banned, the ban will become permanent -->
<PermaBanCount>
3
</PermaBanCount>
<!-- This is the place where the rule looks for entries-->
<EventPath>
Application
</EventPath>
<!-- This was introduced because sole regex matching is too CPU intensive. it incredibly speeds up the filtering when you enter some (or at least one) words that MUST be contained in the LogEntry to undergo the regex inspection-->
<RegexBoosters>
<Booster>原因: 找不到与提供的名称匹配的登录名。</Booster>
</RegexBoosters>
<!-- This is the regex that tries to extract an IP from the entries that contain the booster words for more infos see regex101.com-->
<Regex>
(\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b)
</Regex>
</Task>
如果有愿意把界面改个中文的好心老哥,麻烦把改后和我分享一下,谢谢大佬了,我是真不会改
2024-06-06 运行一个多周,永久拉黑的IP还挺多的
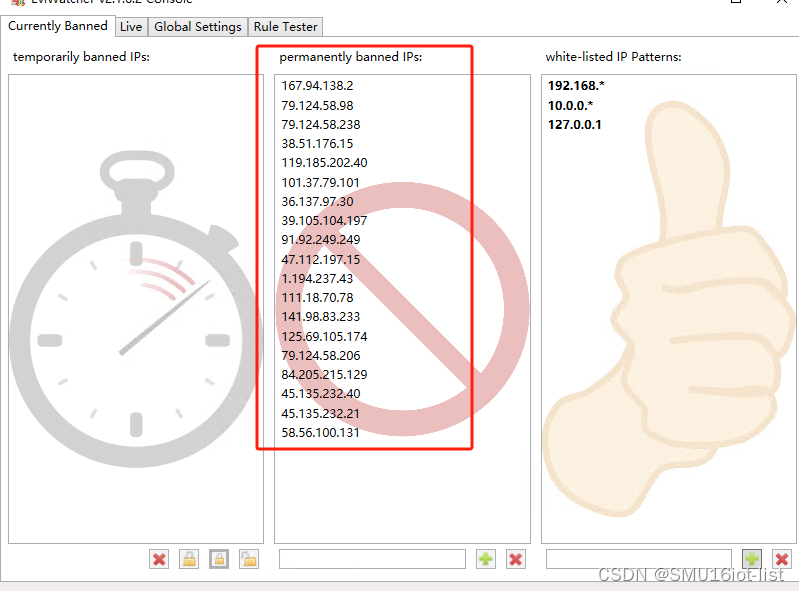
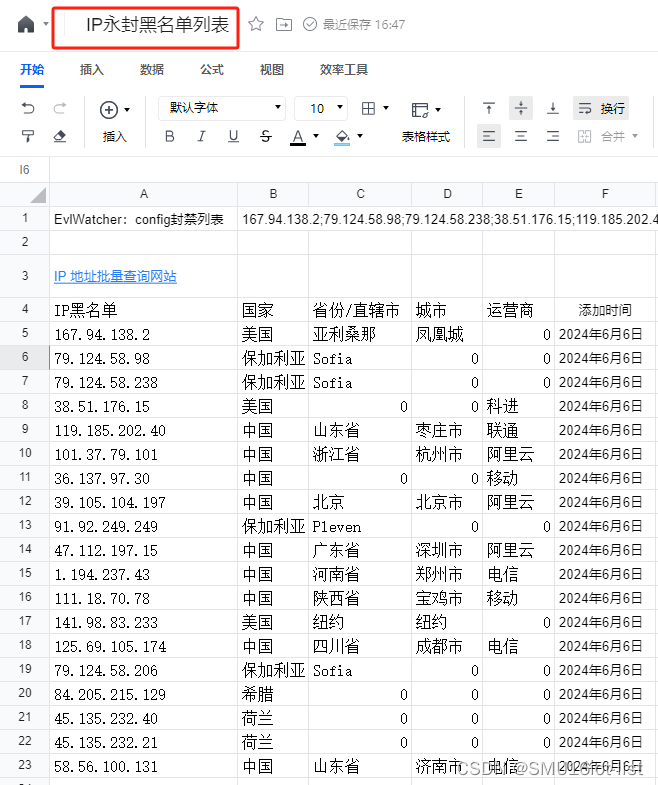
把永封的IP做一个列表分享吧,腾讯文档:IP永封黑名单列表,纯手工统计
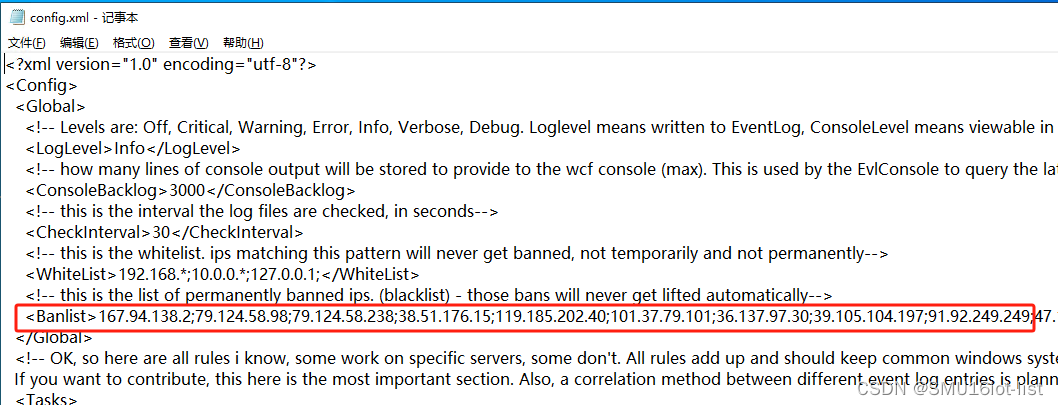
黑名单IP可以通过修改xml批量添加,保存之后,不要忘记重启服务






















 1087
1087

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








