一、背景简介
最近公司准备上个项目,然后使用的是私有云部署模式,我们这边是有总部和分支,总部和分支采用标准IPsec VPN,现在私有云也通过IPsec VPN接入总部相当于一个分支,但是由于我们分支比较多,因此这边各分支访问业务是通过总部进行中转的方式。最近一周都在折腾这个,一个小问题导致了一直有问题也是很无语。
二、概述
IPsec VPN是一种基于IPsec协议族构建的安全虚拟专用网络技术。它通过在公网上为两个或多个私有网络之间建立IPsec隧道,利用加密和验证算法来确保VPN连接的安全性。IPsec VPN可以保护点对点之间的通信,允许在主机和主机之间、主机和网络安全网关之间或网络安全网关(如路由器、防火墙)之间建立安全的隧道连接。
简单说就是在总部和分部间防火墙公网间建立一个隧道,识别到总部到分部间的流量就走隧道,怎样识别呢?通过ACL进行匹配,前面已经学习过了,感兴趣可以看下。今天这个只是大概记录下这周的踩坑经过,后面好像有专门的章节了解VPN是什么。
拓扑图:
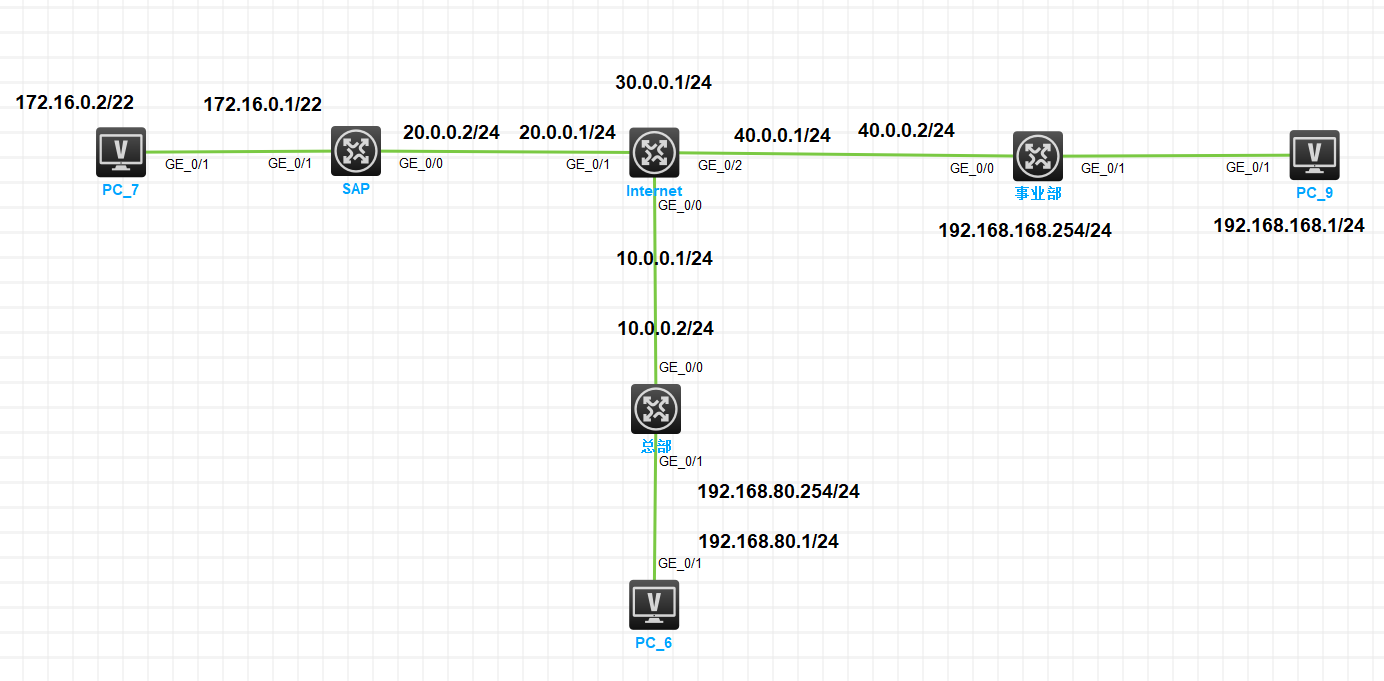
三、IPsec VPN基础
IPsec VPN建立包括两个阶段:阶段一和阶段二。
部署模式也有几种:主模式、野蛮模式等
VPN 基础配置步骤(V7):
-
基础IP和路由 -
ike proposal -
ipsec transform-set -
ike keychain -
ike profile -
ipsec policy
3.1 总部与分支建立VPN
总部:
# G0/0接口地址
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 10.0.0.2 255.255.255.0
nat outbound 3500
# 内网接口地址
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 192.168.80.254 255.255.255.0
# 默认路由
ip route-static 0.0.0.0 0 10.0.0.1
# 一阶段ike提议,定义加解密认证参数
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
# 二阶段提议,定义加解密认证参数
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
# ike对等体信息
ike keychain cj
pre-shared-key address 40.0.0.2 255.255.255.255 key simple 12345678
#
ike keychain SAP
pre-shared-key address 20.0.0.2 255.255.255.255 key simple 12345678
# 使用acl 3000匹配总部到SAP的感兴趣流量
acl advanced 3000
rule 0 permit ip source 192.168.80.0 0.0.0.255 destination 172.16.0.0 0.0.3.255
# 使用acl 3002匹配总部到事业部的感兴趣流量
acl advanced 3002
rule 0 permit ip source 192.168.80.0 0.0.0.255 destination 192.168.168.0 0.0.0.255
# 一般我这边是外网除了建立VPN还需要正常访问外网那就需要NAT转换,但是要禁止转换VPN流量,所有需要将上面两条ACL流量deny,然后peimit所有
acl advanced 3500
rule 0 deny ip source 192.168.80.0 0.0.0.255 destination 172.16.0.0 0.0.3.255
rule 1 deny ip source 192.168.168.0 0.0.0.255 destination 172.16.0.0 0.0.3.255
rule 2 deny ip source 172.16.0.0 0.0.3.255 destination 192.168.168.0 0.0.0.255 rule 1000 permit ip
# 事业部的一阶段profile调用
ike profile cj
keychain cj
local-identity address 10.0.0.2
match remote identity address 40.0.0.2 255.255.255.255
proposal 1
# SAP的一阶段profile调用
ike profile SAP
keychain SAP
local-identity address 10.0.0.2
match remote identity address 20.0.0.2 255.255.255.255
proposal 1
# 创建名称为zongbu的ipsec策略,一个设备只能创建一个策略,但是一条策略可以有多个链接,以序号区分,使用isakmp方式协商sa,所以这里1为到SAP
ipsec policy zongbu 1 isakmp
transform-set 1
security acl 3000
local-address 10.0.0.2
remote-address 20.0.0.2
ike-profile SAP
# 2为到事业部的策略
ipsec policy zongbu 3 isakmp
transform-set 1
security acl 3002
local-address 10.0.0.2
remote-address 40.0.0.2
ike-profile cj
# 最后在公网接口调用ipsec 策略zongbu
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 10.0.0.2 255.255.255.0
nat outbound 3500
ipsec apply policy zongbu
事业部:
事业部和SAP业务只需要分别和总部建立邻居即可。
# 配置接口地址
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 40.0.0.2 255.255.255.0
nat outbound 3500
ipsec apply policy cj
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 192.168.168.254 255.255.255.0
# 默认路由
ip route-static 0.0.0.0 0 40.0.0.1
# acl 3000匹配到总部的感兴趣流量
acl advanced 3000
rule 0 permit ip source 192.168.168.0 0.0.0.255 destination 192.168.80.0 0.0.0.255
#
acl advanced 3500
rule 0 deny ip source 192.168.168.0 0.0.0.255 destination 192.168.80.0 0.0.0.255
rule 1000 permit ip
# 一阶段协商,协商参数两端需要一致
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
# 二阶段协商,协商参数两端需要一致
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
# 创建cj策略,调用二阶段协商参数,定义两端地址
ipsec policy cj 1 isakmp
transform-set 1
security acl 3000
local-address 40.0.0.2
remote-address 10.0.0.2
ike-profile zongbu
# 调用keychain和ike提议
ike profile zongbu
keychain zongbu
local-identity address 40.0.0.2
match remote identity address 10.0.0.2 255.255.255.255
proposal 1
#
# 定义总部对等体信息,key必须两端一致
ike keychain zongbu
pre-shared-key address 10.0.0.2 255.255.255.255 key simple 12345678
SAP:与事业部原理一致,这里不重复了。
实现总部分别与两端通信。
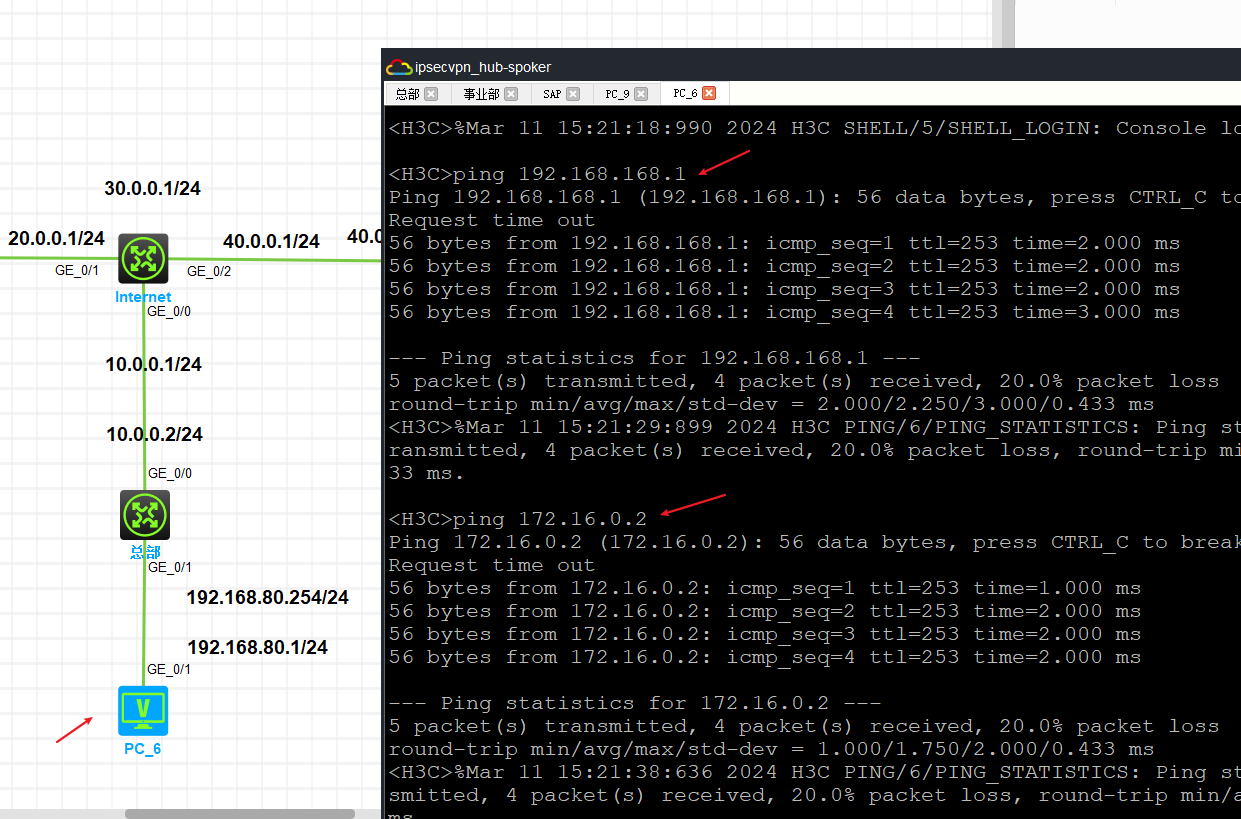
3.2 分支间通过总部互联
分支通过总部通信的原理就是感兴趣的匹配上,比如在分支到总部的acl中定义到SAP的感兴趣流,然后在SAP到总部的acl添加到事业部的感兴趣流,nat的acl也需要拒绝掉。
最终总部的acl为如下:
[zongbu]dis acl all
# acl 3000为匹配总部到SAP的感兴趣流,这里添加上事业部到SAP的感兴趣流,目的都为SAP网段
Advanced IPv4 ACL 3000, 3 rules,
ACL's step is 5
rule 0 permit ip source 192.168.80.0 0.0.0.255 destination 172.16.0.0 0.0.3.255 (6 times matched)
rule 10 permit ip source 192.168.168.0 0.0.0.255 destination 172.16.0.0 0.0.3.255 (5 times matched)
# acl 3002为总部到事业部的感兴趣流,这里添加SAP到事业部的感兴趣流
Advanced IPv4 ACL 3002, 2 rules,
ACL's step is 5
rule 0 permit ip source 192.168.80.0 0.0.0.255 destination 192.168.168.0 0.0.0.255 (6 times matched)
rule 5 permit ip source 172.16.0.0 0.0.3.255 destination 192.168.168.0 0.0.0.255 (5 times matched)
# acl 3500为nat的匹配,需要将上面的流量都先拒绝,然后允许其他所有流量以正常上网转换
Advanced IPv4 ACL 3500, 5 rules,
ACL's step is 5
rule 0 deny ip source 192.168.80.0 0.0.0.255 destination 172.16.0.0 0.0.3.255 (2 times matched)
rule 2 deny ip source 192.168.80.0 0.0.0.255 destination 192.168.168.0 0.0.0.255 (2 times matched)
rule 3 deny ip source 192.168.168.0 0.0.0.255 destination 172.16.0.0 0.0.3.255 (2 times matched)
rule 4 deny ip source 172.16.0.0 0.0.3.255 destination 192.168.168.0 0.0.0.255
rule 1000 permit ip
事业部:
[cj]dis acl all
# acl 3000 为事业部到总部的感兴趣,这里也需要加上到SAP的流量
Advanced IPv4 ACL 3000, 2 rules,
ACL's step is 5
rule 0 permit ip source 192.168.168.0 0.0.0.255 destination 192.168.80.0 0.0.0.255 (5 times matched)
rule 5 permit ip source 192.168.168.0 0.0.0.255 destination 172.16.0.0 0.0.3.255 (5 times matched)
# nat的acl,一样deny掉相应的流量,然后放通所有
Advanced IPv4 ACL 3500, 3 rules,
ACL's step is 5
rule 0 deny ip source 192.168.168.0 0.0.0.255 destination 192.168.80.0 0.0.0.255
rule 1 deny ip source 192.168.168.0 0.0.0.255 destination 172.16.0.0 0.0.3.255 (2 times matched)
rule 1000 permit ip
SAP:
[SAP]dis acl all
# SAP到总部流量,增加到达事业部流量
Advanced IPv4 ACL 3000, 2 rules,
ACL's step is 5
rule 0 permit ip source 172.16.0.0 0.0.3.255 destination 192.168.80.0 0.0.0.255 (5 times matched)
rule 15 permit ip source 172.16.0.0 0.0.3.255 destination 192.168.168.0 0.0.0.255 (4 times matched)
# NAT对应增加
Advanced IPv4 ACL 3500, 2 rules,
ACL's step is 5
rule 0 deny ip source 172.16.0.0 0.0.3.255 destination 192.168.0.0 0.0.255.255
rule 1000 permit ip
如果是使用防火墙配置,完成后一定要检查防火墙安全策略,我这里尝试是需要增加untrust-untrust区域的策略才行。然后ike看到是正常的,在ipsec sa能够看到对应的感兴趣流,如下:
# 事业部sa,能够看到192.168.80.0/24和172.16.0.0/22网段的匹配。
[cj]dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: cj
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Initiator
Path MTU: 1444
Tunnel:
local address: 40.0.0.2
remote address: 10.0.0.2
Flow:
sour addr: 192.168.168.0/255.255.255.0 port: 0 protocol: ip
dest addr: 172.16.0.0/255.255.252.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 519196545 (0x1ef24f81)
Connection ID: 21474836480
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1255
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3077448557 (0xb76e236d)
Connection ID: 21474836481
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1255
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
-----------------------------
IPsec policy: cj
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 1
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Responder
Path MTU: 1444
Tunnel:
local address: 40.0.0.2
remote address: 10.0.0.2
Flow:
sour addr: 192.168.168.0/255.255.255.0 port: 0 protocol: ip
dest addr: 192.168.80.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1044057413 (0x3e3b0d45)
Connection ID: 21474836482
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3044
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 1192130007 (0x470e75d7)
Connection ID: 21474836483
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3044
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: N
Status: Active
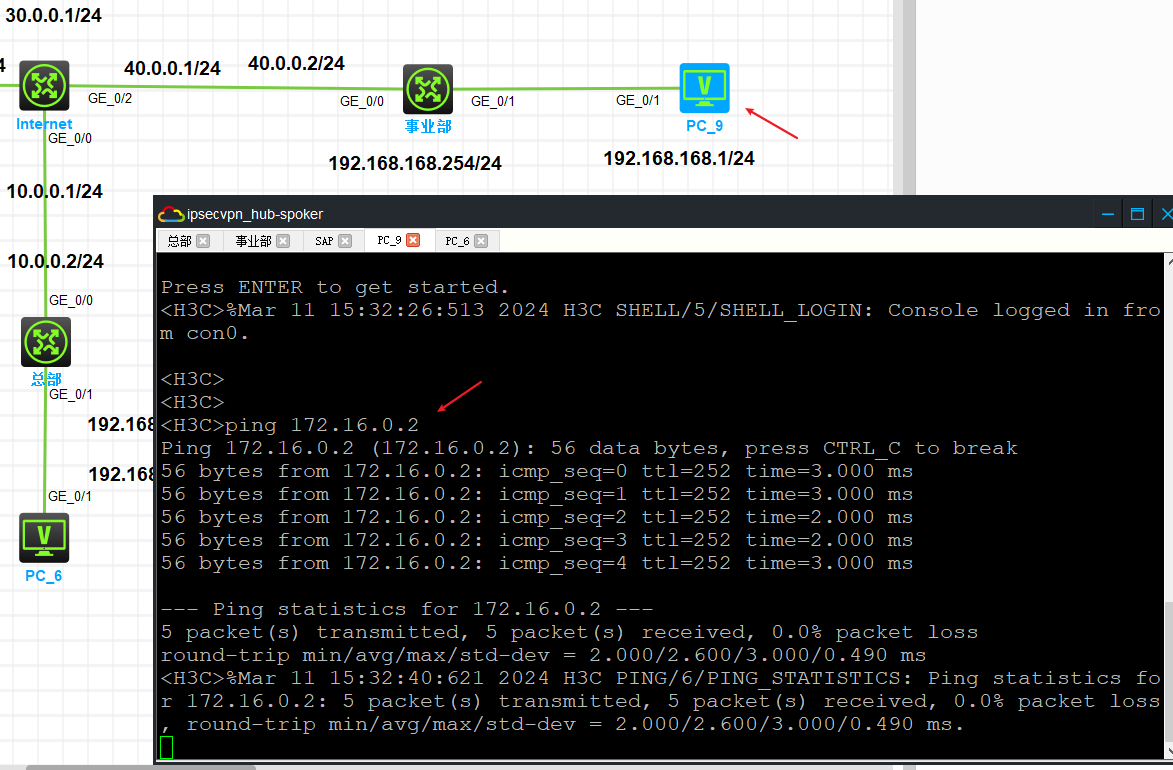
这周我就是在ACL里面多配置了几个rule导致一直不通,然后还有防火墙策略没有搞明白,折腾了好久。这样做的好处就是不需要每个事业部都和SAP建立连接,只需要修改目前的acl感兴趣流匹配即可。以此记录20240311.
本文由 mdnice 多平台发布























 581
581











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










