本文是SSH端口转发功能的学习笔记,以备后续复习
ssh所有参数如下:
$ ssh -h
usage: ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-B bind_interface]
[-b bind_address] [-c cipher_spec] [-D [bind_address:]port]
[-E log_file] [-e escape_char] [-F configfile] [-I pkcs11]
[-i identity_file] [-J [user@]host[:port]] [-L address]
[-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port]
[-Q query_option] [-R address] [-S ctl_path] [-W host:port]
[-w local_tun[:remote_tun]] destination [command]
-
ssh端口转发相关的的常用参数:
-f 后台执行ssh指令
-C 允许压缩数据
-N 不执行远程指令
-R 将远程主机(服务器)的某个端口转发到本地端指定机器的指定端口
详细说明:
-R [bind_address:]port:host:hostport
-R [bind_address:]port:local_socket
-R remote_socket:host:hostport
-R remote_socket:local_socket
-R [bind_address:]port
Specifies that connections to the given TCP port or Unix socket on the remote (server) host are to be forwarded to the local side.
This works by allocating a socket to listen to either a TCP port or to a Unix socket on the remote side. When‐ever a connection is made to this port or Unix socket, the connection is forwarded over the secure channel, and a connection is made from the local machine to either an explicit destination specified by host port hostport, or local_socket, or, if no explicit destination was specified, ssh will act as a SOCKS 4/5 proxy and forward connections to the destinations requested by the remote SOCKS client.
Port forwardings can also be specified in the configuration file. Privileged ports can be forwarded only when logging in as root on the remote machine. IPv6 addresses can be specified by enclosing the address in square brackets.
By default, TCP listening sockets on the server will be bound to the loopback interface only. This may be overridden by specifying a bind_address. An empty bind_address, or the address ‘*’, indicates that the remote socket should listen on all interfaces. Specifying a remote bind_address will only succeed if the server's
GatewayPorts option is enabled (see sshd_config(5)).
If the port argument is ‘0’, the listen port will be dynamically allocated on the server and reported to the client at run time. When used together with -O forward the allocated port will be printed to the standard out‐put.
-L 本地端口转发
详细说明
-L [bind_address:]port:host:hostport
-L [bind_address:]port:remote_socket
-L local_socket:host:hostport
-L local_socket:remote_socket
Specifies that connections to the given TCP port or Unix socket on the local (client) host are to be forwarded to the given host and port, or Unix socket, on the remote side. This works by allocating a socket to listen to either a TCP port on the local side, optionally bound to the specified bind_address, or to a Unix socket.
Whenever a connection is made to the local port or socket, the connection is forwarded over the secure channel, and a connection is made to either host port hostport, or the Unix socket remote_socket, from the remote machine.
Port forwardings can also be specified in the configuration file. Only the superuser can forward privileged ports. IPv6 addresses can be specified by enclosing the address in square brackets.
By default, the local port is bound in accordance with the GatewayPorts setting. However, an explicit bind_address may be used to bind the connection to a specific address. The bind_address of “localhost” indi‐cates that the listening port be bound for local use only, while an empty address or ‘*’ indicates that the port should be available from all interfaces.
-D 动态端口转发
详细说明:
-D [bind_address:]port
Specifies a local “dynamic” application-level port forwarding. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to deter‐mine where to connect to from the remote machine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be specified in the configuration file.
IPv6 addresses can be specified by enclosing the address in square brackets. Only the superuser can forward privileged ports. By default, the local port is bound in accordance with the GatewayPorts setting. However, an explicit bind_address may be used to bind the connection to a specific address. The bind_address of “localhost” indicates that the listening port be bound for local use only, while an empty address or ‘*’ indi‐cates that the port should be available from all interfaces.
-
本地转发
远程的端口转发到本地的端口,
对于使用者"Local Clients"来说,入口在本机IP
ssh -N -L [My Computer Port]:[Remote Server IP]:[Remote Port] [SSH Server User Name]@[SSH Server IP]
本地转发是将 [Remote Server IP]:[Remote Port] 映射到 127.0.0.1:[My Computer Port]
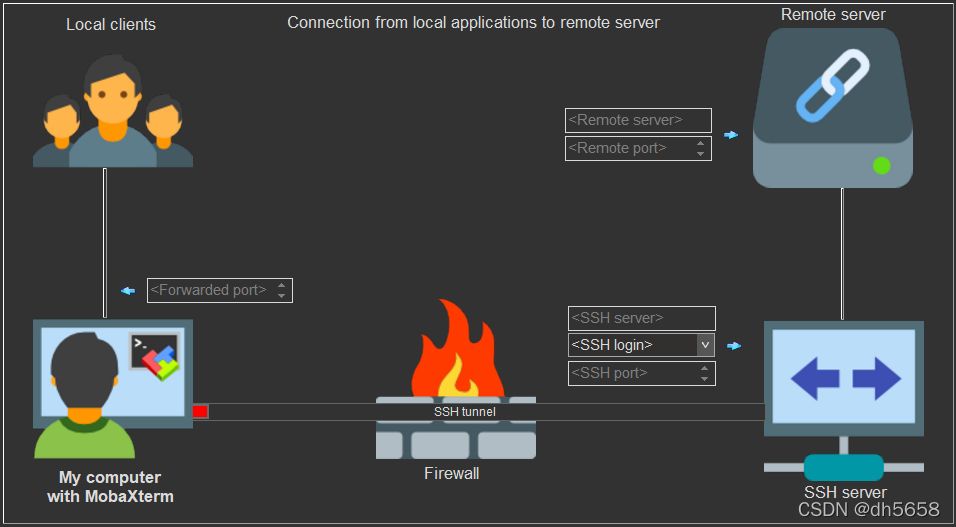
(配图来自MobaXterm截屏)
典型的使用场景:
VNC server 因为安全性原因,配置为只接受 127.0.0.1的接入, 而服务器对外只提供ssh登录,就可以通过ssh隧道来承载VNC的访问。
先SSH连上vnc server主机,将vnc server端口映射到本地,再连接vnc。
功能类似路由器的端口映射,区别:
路由器的端口映射后,vnc viewer的ip是客户端的IP,
SSH本地转发映射端口后,vnc viewer的ip是vnc server的127.0.0.1
举例:
ssh -NL 13306:aliyuncs.com:3306 root@39.23.80.6
# 访问 127.0.0.1:13306 -> aliyuncs.com:3306
-
远端转发
本地的端口转发到远程的端口,远程的服务器相当于提供DNAT、反向代理服务器的功能
对于使用者"Remote Clients"来说,入口在"SSH Server IP"
ssh -N -R [Local Server]:[Local Port]:[SSH Server IP]:[SSH Server Port] [SSH User Name]@[SSH Server IP]
注意:
1. sshd_config里要打开AllowTcpForwarding选项,否则-R远程端口转发会失败。
默认转发到远程主机上的端口绑定的是127.0.0.1,
2. 如要绑定0.0.0.0需要配置sshd_config里的GatewayPorts选项为yes。

文档:
1、是否允许远程主机连接本地的转发端口。默认值是"no"。
2、sshd(8) 默认将远程端口转发绑定到loopback地址。这样将阻止其它远程主机连接到转发端口。
3、GatewayPorts 指令可以让 sshd 将远程端口转发绑定到非loopback地址,这样就可以允许远程主机连接了。
4、"no"表示仅允许本地连接,"yes"表示强制将远程端口转发绑定到统配地址(wildcard address),
"clientspecified"表示允许客户端选择将远程端口转发绑定到哪个地址。
这个选项如果由于权限没法打开也有办法,可配合ssh -L多转发一次
典型的使用场景:
内网的服务器通过跳板机为互联网的用户提供接入服务。
类似frp等内网穿透功能
举例:
ssh -NR 8080:47.104.164.235:80 root@8.136.136.247
# 访问8.136.136.247:8080 -> 47.104.164.235:80
ssh -NR 8000:8.136.136.247:80 root@47.104.164.235
# 访问47.104.164.235:8000 -> 8.136.136.247:80
-
动态转发
相当于SNAT。对使用者“Local Clients”来说,可以理解为代理服务器上网
ssh -N -D [LocaHost Port] [SSH Server User Name]@[SSh Server IP]
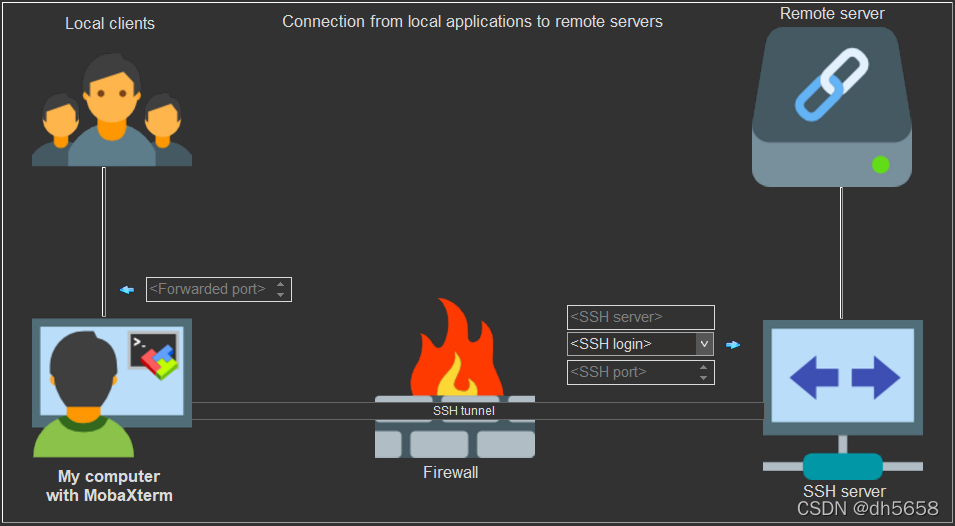
举例:
ssh -ND 2000 root@47.104.164.235
# 在浏览器或系统设置中将设置socks代理: 127.0.0.1:2000
然后本地所有的上网出口全部通过47.104.164.235进行转发。
动态端口转发则只是绑定了一个本地端口,而目标地址:目标端口则是不固定的
目标地址:目标端口是由本地发起的请求决定的
比如访问baidu.com 则相当于把这个请求首先发送到了47.104.164.235,然后由47.104.164.235进行访问后将数据转发回至本地
即: 访问百度流程变成 本地 -> 47.104.164.235 -> 百度







 本文详细介绍了SSH的端口转发功能,包括本地端口转发(-L)、远程端口转发(-R)和动态端口转发(-D)。本地转发将远程主机端口映射到本地,适用于访问受限服务;远程转发则让本地端口转发到远程主机,实现内网穿透;动态转发创建一个SOCKS代理,可用于代理上网。文章还提及了配置参数和使用场景,例如VNC服务器的安全访问和内网服务的外部访问。
本文详细介绍了SSH的端口转发功能,包括本地端口转发(-L)、远程端口转发(-R)和动态端口转发(-D)。本地转发将远程主机端口映射到本地,适用于访问受限服务;远程转发则让本地端口转发到远程主机,实现内网穿透;动态转发创建一个SOCKS代理,可用于代理上网。文章还提及了配置参数和使用场景,例如VNC服务器的安全访问和内网服务的外部访问。
















 1014
1014

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








